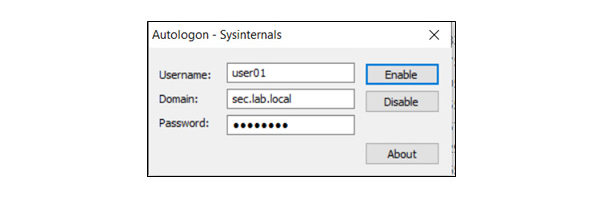
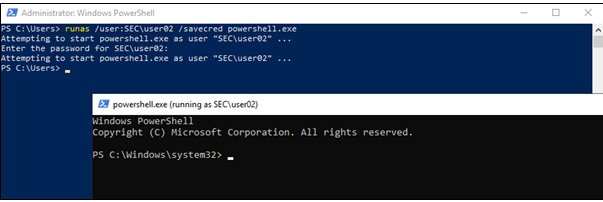
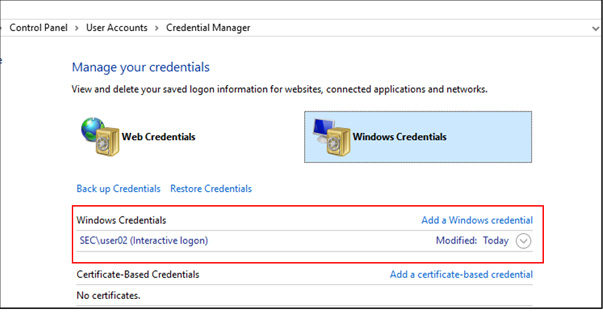
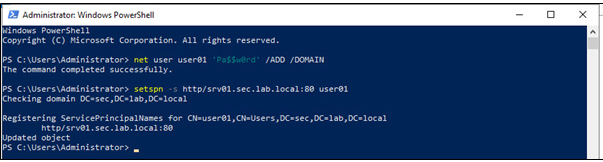
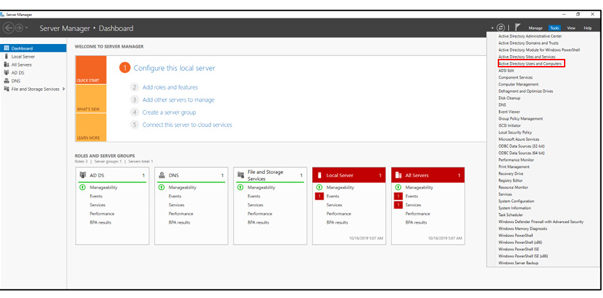
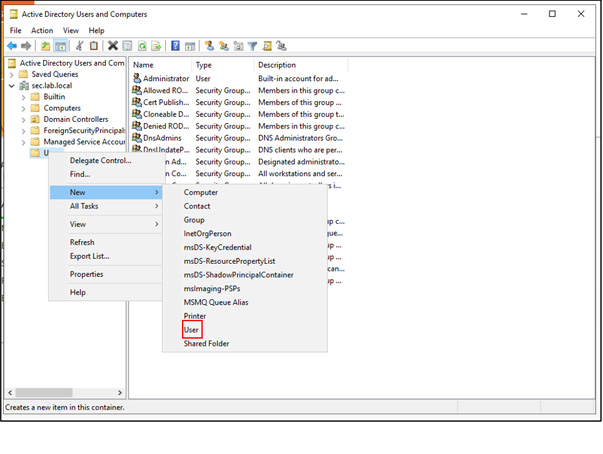
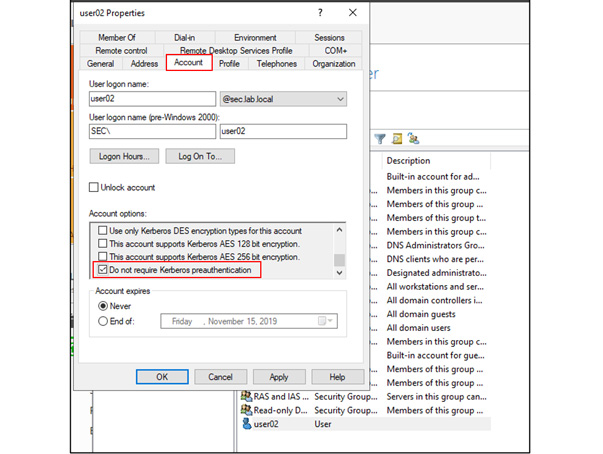
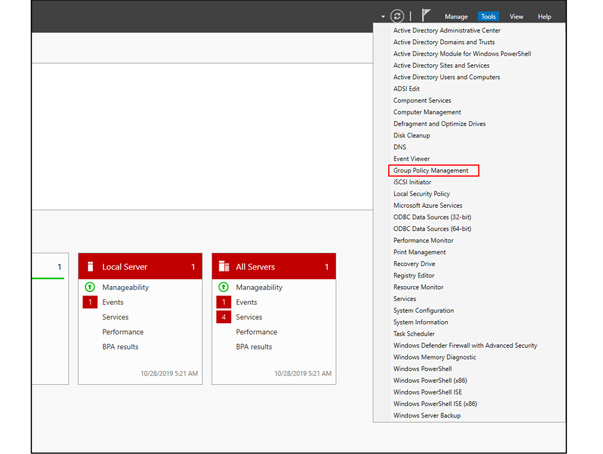
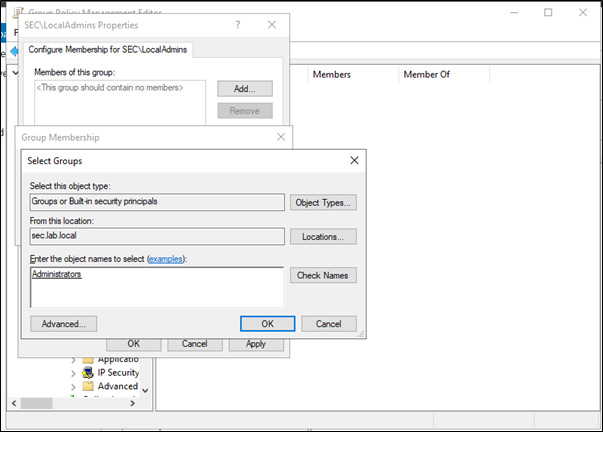
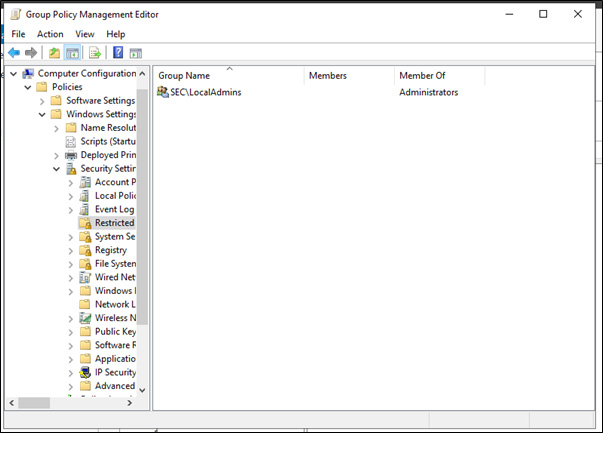
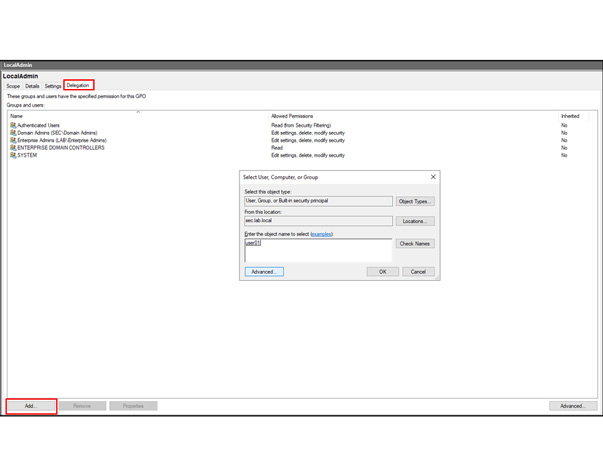
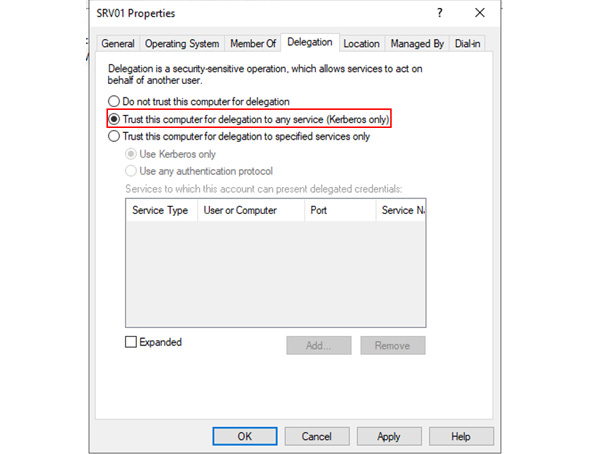
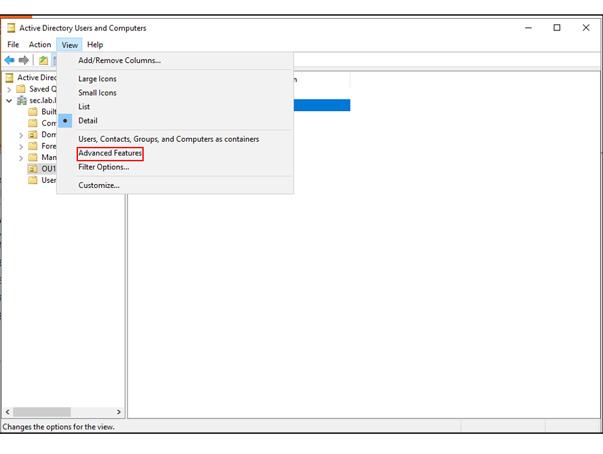
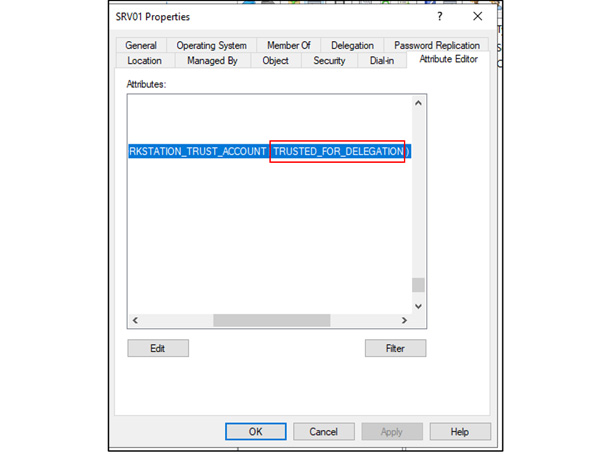
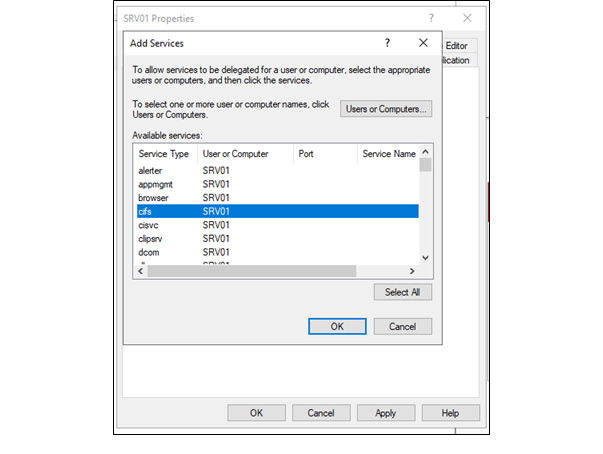
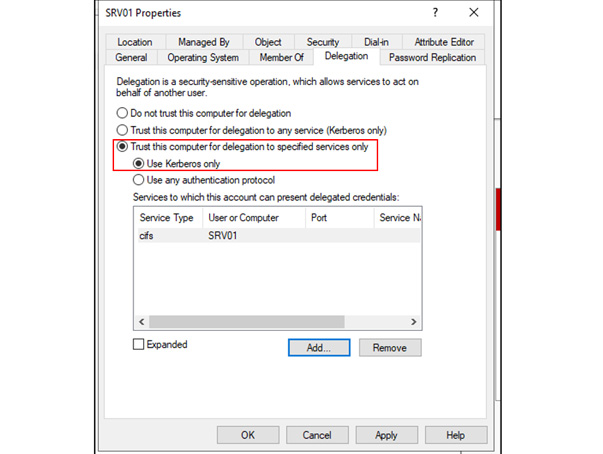
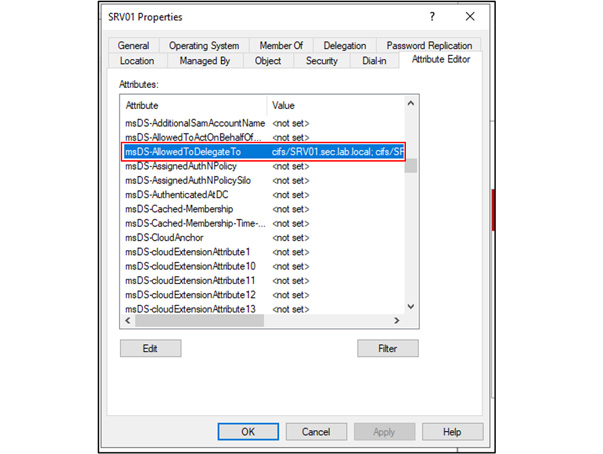
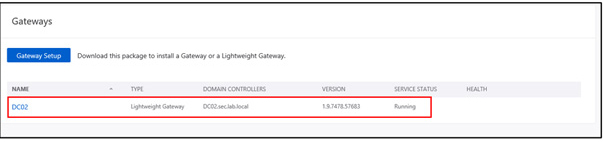
In this article, Sven Bernhard will describe how Blue and Red Teams can create Active Directory Labs for training and testing purposes. He explains how to set up the Active Directory environment as well as how to introduce common misconfigurations / vulnerabilities on purpose. Furthermore, a monitoring server setup using Microsoft ATA is described.
Prerequisites
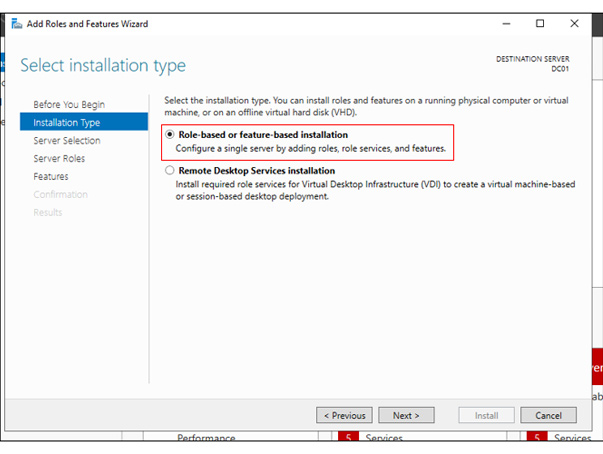
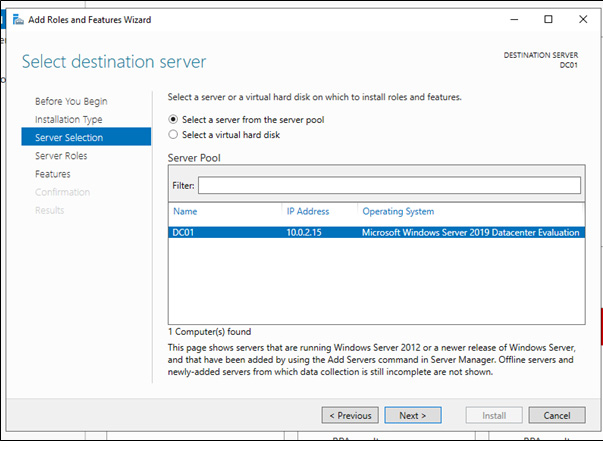
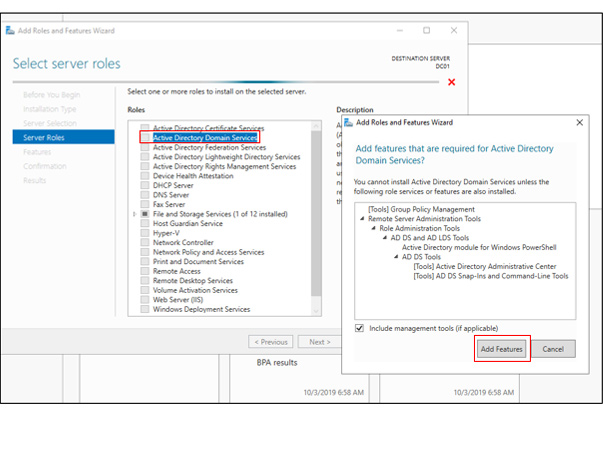
Think about how you like to set up your lab environment:
- Cloud
- Hardware
Cloud
Setup of the lab environment on one of the different cloud hosting providers like AWS, Azure or Google Cloud.
Advantages:
- Unlimited resources
- Easily accessible from anywhere
- You pay only if the lab is running
Disadvantages:
Can be very expensive (7 Machines with 2 CPU, 4GB RAM and 80 Gigs of storage will cost around 300-400 USD per month – if they are running 24/7)
Hardware
The easiest way is to build a lab just on your personal computer is with a virtualization software like VirtualBox, VMware Workstation or Hyper-V, but a lot of resources are needed to have all machines up and running. Therefore, I recommend building a dedicated lab server.
Used server hardware is cheap nowadays. Following an example configuration: