The evaluation is based on the OWASP MASTG and MASVS that are being used actively by SEC Consult for conducting standardized and thorough security assessments of mobile applications. Thus, this blog post will first give a brief introduction into the key facts of the OWASP MASTG and MASVS followed by a short evaluation of selected mobile messengers.1
OWASP Mobile Application Security Testing Guide (MASTG) & Mobile Application Security Verification Standard (MASVS)
What is the MASTG?
The OWASP Mobile Application Security Testing Guide is a security standard for mobile apps and a comprehensive testing guide. It covers the processes, techniques and tools used during a mobile app security test. It is also in use as a comprehensive set of test cases that enables testers to deliver consistent and complete results.
What is the MASVS?
The overall goal of the MASVS is to provide a foundation for mobile application security (MASVS-L1), while also enabling the inclusion of defense-in-depth measures (MASVS-L2) and protection against client-side threats (MASVS-R).
The MASVS is meant to achieve the following:
Provide requirements for software architects and developers seeking to develop secure mobile applications,
Offer an industry standard, which can be used as a checklist in mobile app security reviews for verifying the security maturity,
Clarify the role of software protection mechanisms in mobile security and provide requirements to verify their effectiveness,
Provide specific recommendations on what level of security is recommended for different use-cases.
Whom is it for?
Security Consultants, Security Engineers, Administrators, DevOps Engineers, Developers
Why do we use it?
We as SEC Consult have chosen to use the OWASP MASTG for our mobile penetration assessments, because this standard is publicly accessible for everyone and well renowned in the mobile application security community. This means that customers, colleagues and even other companies, can use a common terminology when communicating about vulnerabilities and ways to mitigate them.
MASTG Checklist
There is a checklist available for use in security assessments.2 It is based on the MASVS and the MASTG standards, and it contains links to the MASTG test cases for each requirement.
Sponsorship
The Open Web Application Security Project® (OWASP) is a non-profit foundation that is community-led with tens of thousands of members. It is widely known for the OWASP Top 10 Vulnerabilities and a variety of open-source projects. We want to support their efforts in these great projects and have decided to support them both financially and by applying their mobile standard for our Mobile Security Product.
Results of the Analysis
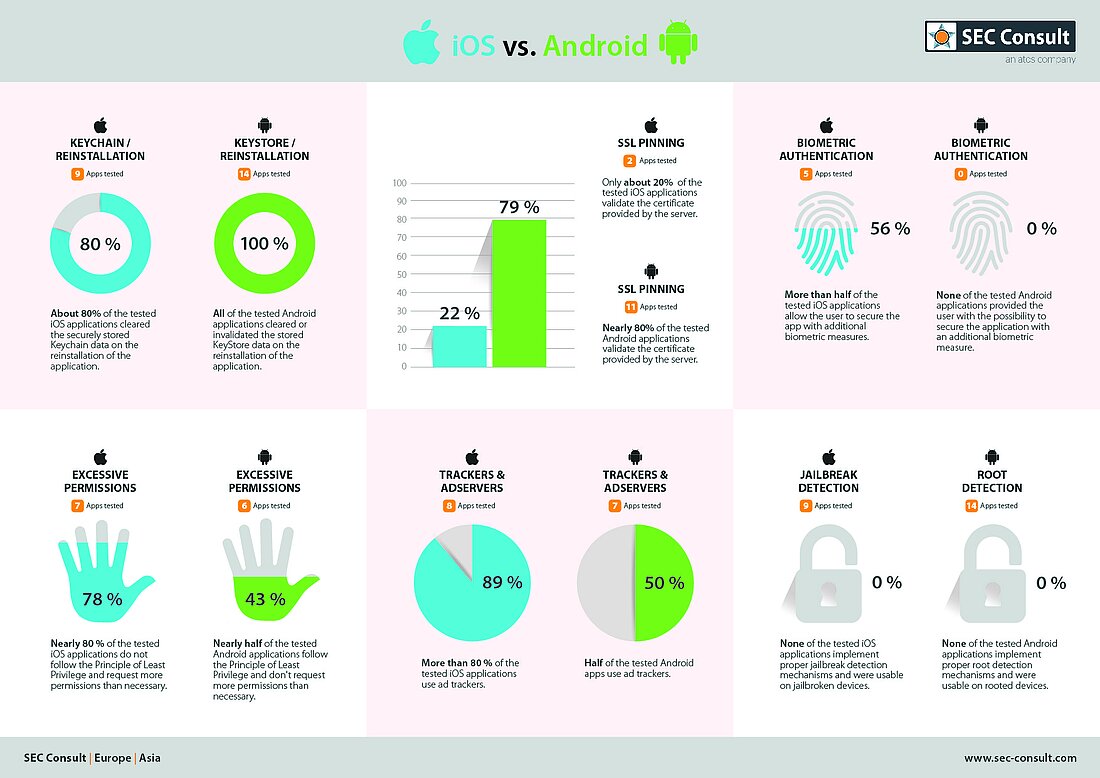
The results of the analysis are summarized in the following table.
Some interesting key facts are that 78% of the iOS and 43% of the Android applications request 20 or more application permissions. Of course, some permissions are necessary for the operation of an application. However, an excessive request for permissions allows them to access more data than they actually need to operate.
Furthermore, only 22% of iOS applications use SSL pinning to ensure that the communication between app and server is further secured. Especially when it comes to messaging apps, making sure that only the expected server is communicating with the app to ensure the confidentiality of messages is something that one would expect. However, to actually exploit such an issue, the attacker would face some obstacles, such as being in a man-in-the-middle position between the victim's device and the server.
Interestingly enough, 78% of the iOS applications clear the Keychain upon re-installation. In case a user sells their phone and forgets to wipe the whole device, the new owner could access the previously stored data (e.g., user credentials) in the Keychain and thus access the user account of the previous user. In Android, all data belonging to a specific app and stored in the Keystore is automatically wiped upon uninstallation of the app, making sure that the mentioned scenario would not be applicable.
Conclusion
During our research we focused on some of the OWASP MASTG test cases. Our research showed that there are quite a few differences between how the messenger applications integrate into the iOS or Android operating system. Perhaps the most interesting result from the analysis is that there is quite a big difference between the apps protecting their client to server communication with SSL Pinning based on the operating system. This communication might very well include sensitive information, which one might hope would be secure during transit. It is important to note, however, that during the analysis the applications were not further investigated into whether the communication between two parties using an app was encrypted or even end-to-end encrypted or that data being sent between the parties was stored securely on the device. For future research this would be interesting to analyze, and to verify whether especially those messengers that want to provide a high level of security can really stand up to their claim.
This blog post has been published on behalf of the SEC Consult Vulnerability Lab.
1 This research have been conducted in 2022. Some of the evaluated apps as well as the guide might have changed since that time.
2 The current version is v1.6.0 but an older version was used for the short evaluation.