Security for SAP Services
SAP® systems are amongst the most important systems of a company. Yet, the security point of view is often neglected. SEC Consult helps detecting severe vulnerabilities before malicious people do.
What you need to know about Security for SAP®
Leading in Research
The experts of SEC Consult contribute to improving the security of all SAP systems by identifying vulnerabilities in the SAP core applications. With the Vulnerability Lab we operate an internal security laboratory and develop our own security tool framework. The in-depth research of our specialists allows us to be one step ahead of cybercriminals in the search for security gaps.
Deep Technical Expertise & Pentesting Background
SAP security is not only about users and roles, although that is an important aspect. Different vulnerabilities might exist due to insecure connections, configurations or missing security features. All our security experts are knowledgeable not only about SAP, but also about web application, network and infrastructure security.
Experience at your Service
SEC Consult realizes more than 60 SAP security projects per year. Our customers come from a wide range of industries and cover a spectrum of mid-sized companies up to major SAP customers. For instance, our experts are conducting continuous SAP assessments for one of the biggest SAP clients in the world.
Sharing Knowledge
SAP systems are at the heart of many companies and organizations. Staff from all business units needs to collaborate safely in this environment, therefore teamwork is essential. SEC Consult collaborates with other SAP partners with other SAP partners in the development of SAP security tools and knowledge.

Objectives of our SAP Security Assessment
- Discovering both obvious and subtle SAP vulnerabilities
- Understanding the root causes of these problems
- Providing an overview of the security of your system landscape
- Increasing SAP security awareness in your organization
Security for SAP® Services in Action
To ensure a secure design of your entire system landscape the SAP security specialists of SEC Consult start with an assessment of the current state of your SAP infrastructure. By testing settings of basic systems, interfaces, applications and databases for insecure configurations, vulnerabilities as well as violations of best practice our experts can uncover potential attack vectors.
They also check your internal security guidelines for the configuration and in-house developments for consistency and correct use. With the combination of automated and manual checks, SEC Consult ensures the coverage of the largest possible scope of topics. The results of the assessment will provide you with an extensive overview about the security of your system landscape.
The wide range of possible vulnerabilities proves that SAP is no secure black box, its security depends to a great extent on quality of the implementation and security awareness. Therefore our SAP specialists in the DACH region offer customer trainings in SAP security awareness to support in implementing security strengthening measures.
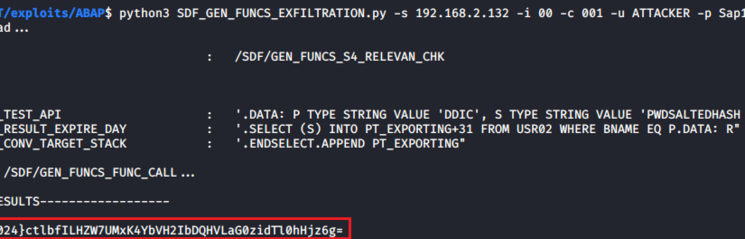
What exactly are we looking at?
- Authentication and authorization security
- Users and authorizations
- Standard users including user and role management
- Network security
- SAP relevant OS security
- Communication security
- Client security
- Message server
- Gateway and RFC connections (including RFC hopping)
- System trust relationships and configuration
- Patch levels
- Protocols / Audit logs
- Custom and Standard Web services
- Custom Code Review