One of the most significant threats are root exploits that can compromise the security of an Android device. In a research project, SEC Consult wanted to find out, if current root detection libraries, used by applications dealing with highly sensitive information like banking applications, would detect if a device is compromised during runtime by a malicious application using a root exploit. The aim is to question the usefulness of root detection in general and discuss the different implementation possibilities.
In order to better understand this topic, our mobile security experts Hussam Cheaib and Fabian Densborn, will start by describing what rooting actually is, what different types of root exist and how or whether root detection actually works.
What is Rooting?
Rooting is the process of gaining administrative privileges or "root access" on an Android device. By default, Android devices are set up with restricted user accounts that have limited permissions. These restrictions prevent users from accessing certain system files and settings, which can help improve the security and stability of the device. Once a device has been rooted, the user has full control over the device, including the ability to install custom software, modify system settings, and access system files that were previously restricted. While rooting can provide users with greater control over their device, it can also come with risks. Rooting can potentially make the device more vulnerable to security threats, such as malware and other malicious software. There exist two different types of rooting that have to be distinguished:
User Root - Users rooting their own devices
For users who want more control over their device, rooting can provide a way to bypass these restrictions and gain full control over the operating system. Rooting essentially involves modifying the device's firmware or software in order to allow privileged access to the system files and settings. Rooting can be done through various methods, such as using a rooting tool or flashing a custom ROM (modified version of the Android operating system). Most of the time a gatekeeper application like Magisk will be installed to supervise access to those elevated privileges. In this scenario, users are aware of the rooted device because they have taken steps such as flashing the device themselves. They want to take advantage of the flexibility they get from rooting their own device. There exist a lot of artifacts on the device that can be used to detect that such a device is rooted, but as this root is intentional, most of the custom ROMs do not even try to hide such artifacts.
Malicious Root – An attacker compromising a victim’s device
Malicious root is often used by malware to get elevated root privileges without modifying the system in a way that it is easy to detect. Most of the times a kernel exploit is abused to escalate the privileges and the malware executes its malicious actions. Only a few artifacts, which could indicate the compromise of the system, are placed on the device as the malware tries to hide its malicious intention. This makes it almost impossible to detect malicious root, as with its high privileges, the malware can hide all of its tracks. Most malicious root exploits are temporary, i.e., they last only until the next reboot (but smartphones are not frequently rebooted anyways). However, there are also malicious root exploits that are able to reach persistence, some of them even surviving a factory reset of the smartphone.
Root exploits are essentially vulnerabilities that allow attackers to obtain root privileges on a device. Once attackers have gained root access, they can do anything on the device, including modifying system files, stealing data, and installing malware.
Most of the root exploits abuse a kernel vulnerability to get elevated privileges on the device. But for a successful exploitation many security features like SECCOMP or SELinux have to be circumvented first. Additionally, most of the root exploits need to be tailored to a specific device in order to work.
Root Detection
What is Root Detection?
Root detection is a technique used by some Android apps to determine if a device has been rooted. When an app is installed, it checks for signs of rooting, such as the presence of specific files or folders created during the process. If rooting is detected, the app may disable certain features that could be exploited by an attacker with root access or refuse to run entirely. The purpose of this process is to ensure the app runs on a device that hasn't been compromised, maintaining the default security measures of the operating system, such as keeping the private directory of an application only accessible to the app itself and preventing other apps from accessing its sensitive data.
How does Root Detection Work?
Root detection can work in a variety of ways, depending on the app and the specific techniques used. Some apps may simply check for the existence of certain files or folders that are created when a device is rooted. Others may use more advanced techniques, such as checking the device's kernel for modifications or analyzing the device's file system for signs of tampering. Some apps may also use a combination of different techniques to improve the accuracy of their root detection.
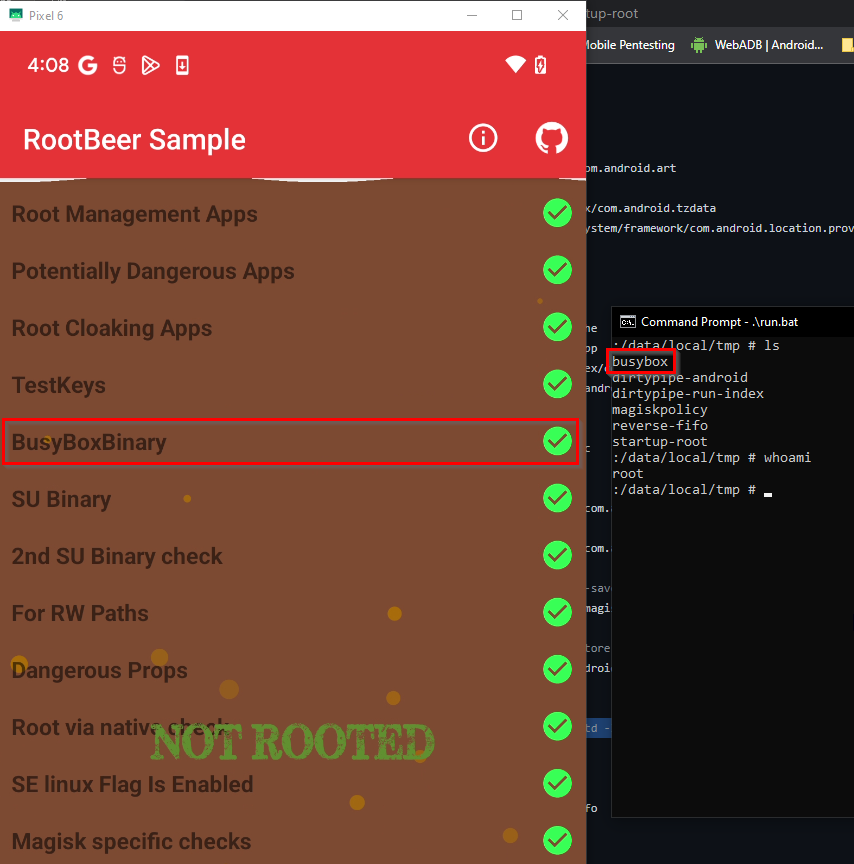
Most of the root detection libraries check the following things:
- Are root management apps (e.g. like Magisk) installed on the device?
- Are other potentially malicious applications installed?
- Does the build tag contain test keys?
- Has the device set dangerous device properties?
- Is the busybox binary installed on the device?
- Is the su binary installed on the device?
- Is the system partition mounted as read write and not read-only?
Some applications even try to get the current SELinux mode the device is running in, but without special permissions, which are only accessible to system applications, this is not possible in modern Android versions.
How applications deal with Root Detection?
When an app detects that the device it is running on is compromised, there are different ways apps respond:
- Warning the User: Some apps may simply warn the user that they are operating on a rooted device, informing them about the potential risks.
- Restrict Functionality: Some apps may choose to restrict certain features if they detect that the device is rooted. For instance, a banking app may disallow transactions on a rooted device.
- Deny Access: In more extreme cases, an app may refuse to run altogether on a rooted device. This is common for applications that deal with highly sensitive data or transactions, such as banking or financial apps, certain games to prevent cheating, or streaming services to prevent piracy.
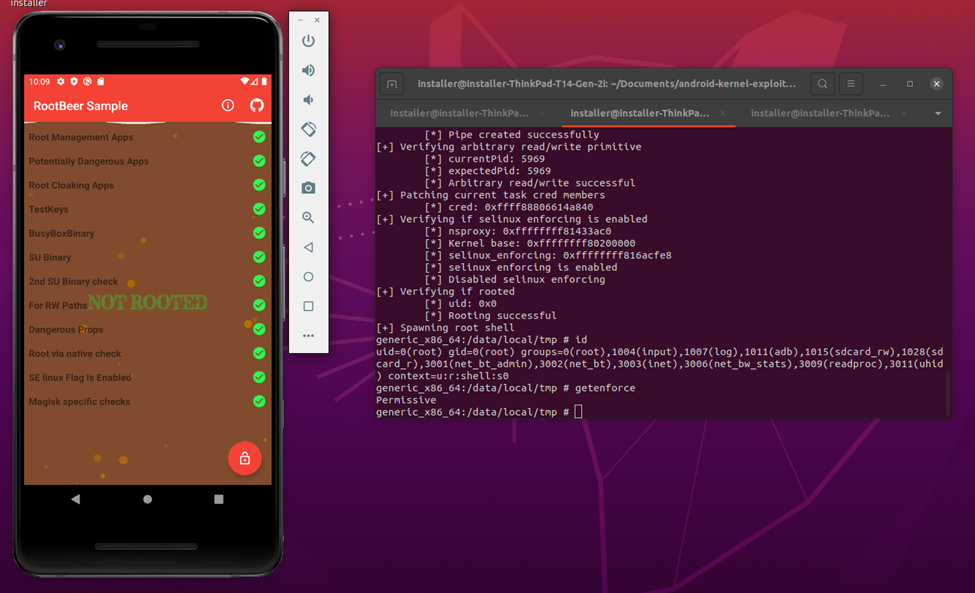
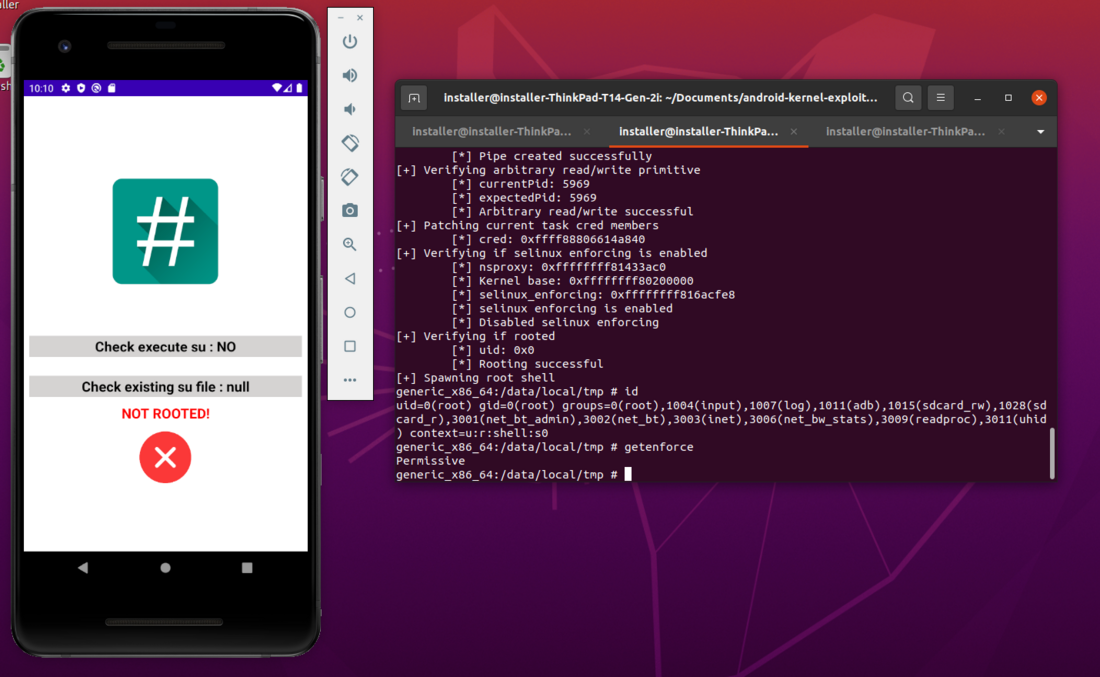
Proof of Concept: Do Root Detection Libraries detect Malicious Root?
To check whether applications that implement root detection mechanisms also detect malicious root exploits at runtime, we first had to identify possible exploit candidates for which a public Proof-of-Concept (PoC) exists.
During the research, the vulnerabilities with identifiers CVE-2019-2215 and CVE-2020-0847 turned out to be the most documented ones. For both vulnerabilities a PoC already exists, which allows us to exploit the kernel vulnerability and create a shell with root privileges at runtime.