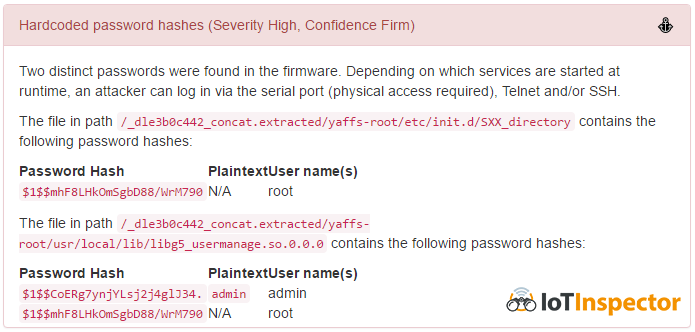
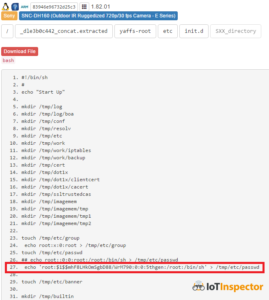
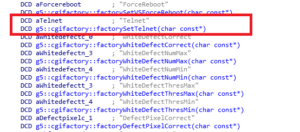
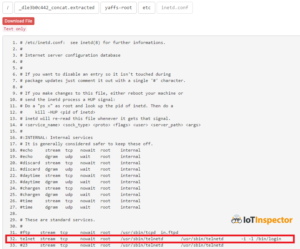
Now we have all ingredients to craft an attack that looks like this:
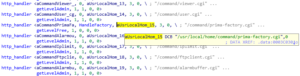
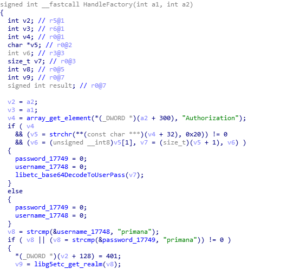
- Send HTTP requests to /command/prima-factory.cgi containing the “secret” request values cPoq2fi4cFk and zKw2hEr9 and use primana:primana for HTTP authentication. This starts the Telnet service on the device.
- Login using the cracked root credentials via Telnet. Note: We have not cracked the root password, but it’s only a matter of time until someone will.
The user primana has access to other functionality intended for device testing or factory calibration (?). There is another user named debug with the password popeyeConnection that has access to other CGI functionality we didn’t analyze further.
We believe that this backdoor was introduced by Sony developers on purpose (maybe as a way to debug the device during development or factory functional testing) and not an “unauthorized third party” like in other cases (e.g. the Juniper ScreenOS Backdoor, CVE-2015-7755).
We have asked Sony some questions regarding the nature of the backdoor, intended purpose, when it was introduced and how it was fixed, but they did not answer.
For further information regarding affected devices and patched firmware, see our advisory. IoT Inspector now comes with a plugin that detects this vulnerability.