The growing electrification of transportation not only brings ecological benefits but also new cybersecurity challenges for public charging infrastructure. In this blog post, we take a detailed look at potential cyber threats that could impact not only charge point operators but also EV owners and public trust in e-mobility. We highlight the role of penetration testing (pentests) in effectively countering these threats and meeting regulatory requirements.
Cyber Threats to EV Charging Infrastructure: Risks and Protection through Penetration Testing
news
Threats to EV Charging Infrastructure
Let’s explore the most pressing threats to EV charging infrastructure and the potential consequences they carry for users and operators alike.
1. Infrastructure Outage
A targeted attack on availability can lead to long queues, stranded vehicles, revenue losses, and significant damage to the operator’s reputation. Reliable charging infrastructure is crucial for EV drivers. Such outages can undermine public trust in the technology and hinder progress toward sustainable mobility.
2. Manipulation of Consumption Data
Tampered data can lead to billing problems and violations of legal regulations, such as the Measurement and Verification Act. Billing and roaming with partner networks may be disrupted, potentially causing significant financial losses for operators.
3. Duplication of Charging Cards and Authentication Bypass
Attacks on card-based authentication systems can harm customers and cause revenue losses for operators. This underscores the importance of robust and thoroughly tested authentication mechanisms.
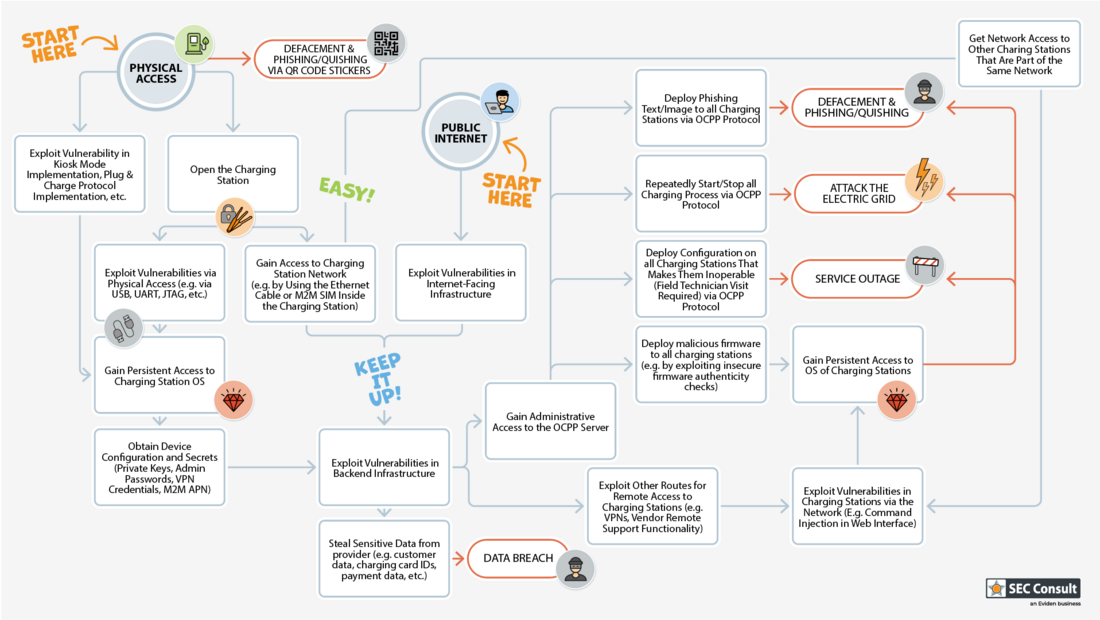
4. Attacks on Backend and Cloud Systems
An attack on backend systems—such as those processing consumption data, authenticating users, and managing billing—or cloud portals used by customers can result in massive data breaches. This allows attackers to manipulate charging sessions or alter the configuration of charging stations. Vulnerabilities in backend systems often serve as entry points for more extensive attacks within the infrastructure.
5. Defacement and Phishing (Quishing)
Inappropriate content displayed on charging station screens or fraudulent QR codes can mislead customers, redirect them to fake billing sites, and damage the operator’s image. "Quishing" attacks via QR codes pose a significant risk to end-users.
6. Ransomware
Ransomware attacks on operators can lock down all charging stations until a ransom is paid. These attacks not only cause financial losses but also undermine trust in the operator and the critical charging infrastructure.
7. Attacks on the Power Grid
Attackers may exploit simultaneous manipulation of multiple charging stations to destabilize the grid through load peaks or drops, potentially causing a blackout.
Attack Vectors on Charging Infrastructure
1. Physical Access
Charging stations, often installed in public areas, are susceptible to physical attacks. Simple tools like screwdrivers or lock-picking can grant unauthorized access. Security measures such as tamper contacts, video surveillance, or integration into a Security Operations Center (SOC) are often lacking. Once accessed, attackers can manipulate firmware, deploy hardware implants, or extract and alter credentials (e.g., for Wi-Fi, VPNs, and backends). Connected Ethernet cables and embedded SIM cards may also be exploited for advanced network attacks.
2. Network Access
Although most charging stations are not directly accessible via the internet, thousands of publicly available stations can still be found on platforms like Shodan or Censys due to misconfigurations. For charging stations within internal networks, attackers may resort to physical access to a station to infiltrate the network and access other devices. Vulnerabilities in cloud portals, operator backends, or remote support interfaces also provide potential attack pathways (see “Attacks on Backend and Cloud Systems”). Compromised backend systems are often used by attackers to gain initial access (MITRE ATT&CK „Initial Access“) and then move laterally within the operator’s or manufacturer’s infrastructure (MITRE ATT&CK „Lateral Movement“, „Privilege Escalation“).
The Importance of NIS2 and the Cyber Resilience Act for EV Charging
The NIS2 Directive and the EU Cyber Resilience Act introduce legal requirements for all stakeholders in public charging infrastructure.
NIS Directive: Operators of critical services must implement appropriate security measures. This includes "Operators of a recharging point that are responsible for the management and operation of a recharging point, which provides a recharging service to end users, including in the name and on behalf of a mobility service provider" (see NIS2 Directive Annex I, “Other Critical Sectors”). Supply chain security and operator infrastructure security play a critical role in this context.
EU Cyber Resilience Act: This legislation mandates security standards in product development and regular penetration testing to identify and address vulnerabilities early. Manufacturers of charging stations, software solution providers (Charge Point Management Software, Energy Management, Billing & Payment, etc.), and potentially cloud service operators for charging infrastructure management are affected.
Non-compliance can lead to severe legal and financial consequences, including sales bans on affected products, fines, and personal liability for executives (managers and board members).
Did you know…?
Key Requirements of the EU Cyber Resilience Act (Annex I):
- Regular Security Assessments: Effective testing such as penetration tests, source code reviews, and red teaming must be conducted continuously.
- Compliance with Core Security Requirements: This includes secure default configurations, access protection through authentication, tamper resistance, input validation, and system hardening.
- Cybersecurity in Development Process: Security must be integrated throughout the product development process.
- Software Bill of Materials (SBOM): A detailed inventory of all software components and their versions must be documented.
- Security Updates: Updates to fix vulnerabilities must be provided promptly, free of charge, and include detailed information on their impact.
- Coordinated Vulnerability Disclosure (CVD) Process: Manufacturers must offer a clear point of contact for vulnerability reporting and implement a responsible disclosure process.
Measures to Improve Cybersecurity of Public Charging Infrastructure
To secure charging infrastructure, operators and manufacturers should implement the following measures:
- Comprehensive Penetration Testing: Regular pentests on charging station products to identify vulnerabilities. These tests should cover hardware, software, and firmware components to ensure holistic security. Both physical access (attackers at the station) and network access should be assessed. Tests should identify susceptibility to typical embedded system vulnerabilities, such as missing secure boot, lack of flash memory encryption, JTAG/SWD attacks, backdoor accounts, command injections, or buffer overflows.
- Pentests for Backend and Cloud Components: Thorough testing of OCPP servers, remote support/admin tools, backends for mobile apps, and billing portals to ensure sensitive customer and billing data are protected and systems are not an entry point for attack.
- Network Pentests: Comprehensive testing of network infrastructure, including charging station connectivity via M2M cellular or VPN, network segmentation, and firewalls. Particularly revealing are “assumed breach” tests that explore how attackers might spread further within the network if a charging station is already compromised. This identifies vulnerabilities in other charging stations stations, unprotected backend services, or administrative interfaces.
- Gap Analysis for NIS2 and Cyber Resilience Act: Identify and address gaps in compliance with NIS2 and Cyber Resilience Act requirements
Given the rising cyber threats to charging infrastructure, it is critical for operators and manufacturers to act proactively. Penetration tests, network and backend analyses, and regular compliance reviews provide a strong foundation for ensuring charging infrastructure security and strengthening user trust in e-mobility.
SEC Consult supports operators and manufacturers with professional penetration testing for IT infrastructures and software products, a specialized hardware lab in Vienna for embedded system pentesting, a comprehensive consulting portfolio for NIS2 and the Cyber Resilience Act, and tailored advisory services (Secure Coding Training, Threat Modeling, Secure Software Development in line with OWASP SAMM, IEC 62443, etc.).