Debunking Cloud Security Myths: Clearing Misconceptions That Risk Your Business
cloud news
However, both of these myths involve sometimes fatal misconceptions that affect the security of a company in the cloud. In the following, we will take a closer look at these two statements and myths and categorize them.
- The provider takes care of data security in the cloud!
- My cloud security scanner finds all vulnerabilities, so I don't need a cloud penetration test!
Let's start with the most frequently heard statement, which can have a huge impact on the security of an organization's data.
"The provider takes care of the security of the data in the cloud!"
One of the most common misconceptions about services in the cloud is that the cloud provider takes care of security. However, this is not true, as the cloud provider only takes care of security in one specific area. Depending on the cloud provider and product chosen, an organization's IT no longer has to worry about issues such as patch management or network security, but they are not completely without responsibility. A shared responsibility model has been introduced in cloud computing to define which organization is responsible for the security of certain areas.
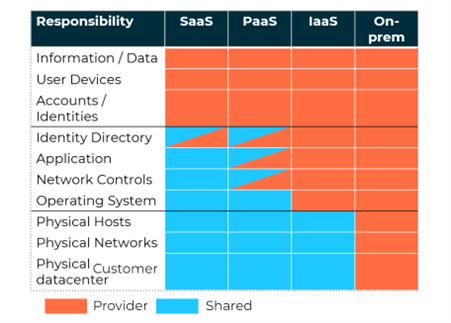
Shared responsibility model
The shared responsibility model for cloud services, such as Azure, describes the division of responsibilities between the cloud provider and the customer. The image below shows a generalized version of the shared responsibility model. As can be seen here, there are areas that the cloud provider's customer must always take care of. These are, for example, roles and user concepts and data security. This quickly shows that it is not possible to simply hand over responsibility for security to the cloud provider, as responsibility always remains with the customer. This also means that they should ensure that the resources they have configured are configured securely, which would be possible with a cloud penetration test, for example.
Infrastructure as a Service
Infrastructure as a Service (IaaS for short) is a widely used service with many cloud providers. This includes, for example, virtual machines that are hosted in the cloud. With virtual machines in particular, it quickly becomes clear that the cloud provider's customer has to take care of many security-related issues. As the customer selects the operating system and all software for a virtual machine and installs it themselves, they are also responsible for its secure operation. This includes topics such as the configuration of a local firewall, patch management of the software or the configuration of remote maintenance via SSH or RDP.
With IaaS, all of these and many other points must be carried out and managed by the cloud provider's customer. Security should therefore be taken into account when using services such as IaaS. Furthermore, the implementation of a cloud penetration test should also be evaluated here.
Software as a Service
Software as a Service (SaaS for short) is also a widely used service, but it offers the customer significantly fewer options for influencing security. Probably the best-known SaaS solution is M365 and therefore also its user management Entra ID. This in particular is an essential part of each of our cloud penetration tests and M365 security assessments as there are many opportunities to allow vulnerabilities in this infrastructure via insecurely configured authorizations or roles.
Overall, the shared responsibility model in particular shows that the above statement is a clear myth and that every customer of a cloud provider must make an essential contribution to the security of the data in the cloud and that this should be checked regularly.
"My cloud security scanner finds all vulnerabilities, so I don't need a cloud penetration test!"
Cloud security scanners are automated tools for identifying common misconfigurations. These can increase the security of an organization if their results are used effectively. Nevertheless, there is also a widespread misconception here: “My cloud security scanner finds all vulnerabilities, so I don't need a cloud penetration test.”. Cloud security scanners scan configurations, analyze access rights and check for generally known vulnerabilities, such as “deny of wallet”. This makes it easy to uncover the “low-hanging fruit” of vulnerabilities in the cloud infrastructure.
However, these scanners are only as good as the rules according to which they work. They are based on predefined signatures and pattern recognition. This means that they can only find vulnerabilities that are already known and for which a signature exists. New, complex or customer-specific attack scenarios therefore remain undetected. Furthermore, cloud penetration tests are carried out by our experienced security consultants, who not only check known vulnerabilities, but also specifically try to combine vulnerabilities and misconfigurations. This can result in vulnerabilities that a conventional scanner can no longer detect. However, these are often the really critical vulnerabilities that enable the security consultant and attackers to gain higher administrative authorizations.
The above statement must therefore also be dismissed as a myth. Security in the cloud requires a multi-layered approach in which cloud security is only one part of the solution. These can regularly search for vulnerabilities, but offer no guarantee of complete security. Only through regular penetration tests can companies ensure that their cloud infrastructure is actually secure - even against complex attack methods.