What needs to be achieved?
The aim is to identify weaknesses, shortcomings and gaps in digital operational resilience, to assess readiness to deal with ICT-related incidents, and to take prompt corrective action.
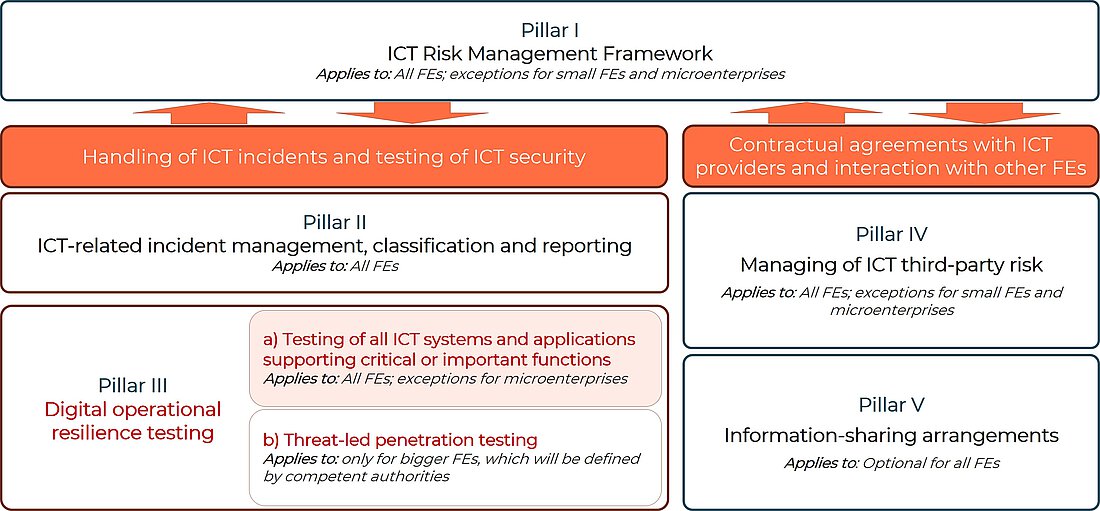
What is in the scope?
DORA narrows the scope of security testing to “ICT systems and applications supporting critical or important functions” (Art 24(6) DORA).
According to DORA, a function is considered "critical and important" if its disruption could materially affect the financial performance, stability and continuity of a financial institution's services and operations. Similarly, if any disruption, malfunction or interruption of that function would materially affect ongoing compliance with the conditions and obligations of its authorisation and other regulatory requirements under applicable financial services legislation (Art 3(22) DORA).
Determining which specific applications and functions support critical or important operations is a decision left to the financial institution.
To identify the applications within the testing scope, the principle of proportionality is applied. The size and overall risk profile, and the nature, scale and complexity of the services, activities and operations of the financial entity, needs to be taken into account (Art 4(1) DORA).
It's evident that the risk profile and complexity of services vary greatly between microenterprises and international banks.
Consequently, the testing plan for one financial institution may differ significantly from another's.
However, it is also a good exercise to examine which applications and systems are integrated into the ICT-network. Which applications should remain, which ones should be uninstalled. And which ones have been forgotten over the years, but are still running in the system. And nobody is keeping an eye on their security. The latter poses a considerable security risk.
How to fulfill the requirement?
The security tests of all ICT systems and applications supporting critical or important functions needs to be conducted at least once in a year. According to the principle of proportionality, the financial entities can select their own methods. As examples of appropriate test, the legislator provides following:
- Vulnerability assessments and -scans: These involve identifying and evaluating weaknesses or vulnerabilities in systems, often through automated scanning tools or manual reviews.
- Open-source analyses: This involves scrutinizing open-source software components to uncover any potential security vulnerabilities or licensing concerns.
- Network security assessments: This entails assessing the security measures and configurations within a network infrastructure to identify vulnerabilities and potential risks.
- Gap analyses: These involve comparing existing security measures against established standards or best practices to identify areas requiring improvement or where deficiencies exist.
- Physical security reviews: This involves evaluating the effectiveness of physical security measures in safeguarding assets, facilities, or sensitive information.
- Questionnaires and scanning software solutions: Questionnaires aim to gather information about various security aspects of a software application, including security policies, configuration settings and access controls. Whereas software solution scans perform automated scans to uncover security gaps, vulnerabilities or misconfigurations in an application.
- Source code reviews, when feasible: This refers to the examination of software application source code to identify potential security vulnerabilities or coding errors, where possible.
- Scenario-based tests: These involve simulating various scenarios or attacks to assess the preparedness and response capabilities of security measures or personnel.
- Compatibility testing: This entails evaluating how well a system, application, or device interacts with other systems, software, or environments.
- Performance testing: This involves assessing the performance, speed, and responsiveness of systems, applications, or networks under different conditions or loads.
- End-to-end testing: This refers to evaluating the entire system or process from start to finish to ensure all components function together as intended and securely.
- Penetration testing: This involves conducting controlled simulated attacks by ethical hackers to identify vulnerabilities and weaknesses in systems, networks, or applications, with the aim of bolstering security defenses.
Consequentially, the depth and the type of the application and system testing can vary considerably. This will depend on the risk profile of the respective financial entity, but also from the technology in scope. For example, hardware test and web application test, request a completely different approach.
It is important to emphasize that the goal must be achieved. However, the approach to reaching this objective varies from one financial entity to another.
How can we support?
Security testing – may it be of software, firmware or hardware – is our daily business since 2002. We have highly professional consultants, who have specific knowledge in various technologies.
We are confident that we can support you with the best advice by setting up an appropriate testing plan and by conducting the tests. This ensures not only compliance with DORA requirements but also strengthens your ICT network against cyber threats.