SEC Consult tested hardware writeblockers in preparation for incident response case work (Wiebetech USB 3.1, Wiebetech Forensic Ultradock, Logicube Portable, Tableau TK8u/T8u USB 3.0 Forensic Bridge). We noticed that two of our writeblockers are behaving differently than expected, namely Wiebetech USB 3.1 and Wiebetech Forensic Ultradock (SATA).
Note: apparently the companies CRU, Wiebetech and Digistor merged, but the writeblocker is still labelled "WiebeTech", so we kept this name in this article.
This research was conducted by Dr. Michael Denzel with the support of Veronika Svientik (working student).
Wiebetech USB 3.1
The Wiebetech USB writeblocker has some issues with virtual machines. The official usage is also only allowed with physical machines (and no virtual machines). Our tests using virtual machines resulted in the writeblocker not working at all and writes to the data device were forwarded, corrupting the attached data medium. While officially not allowed, this behaviour is unexpected for digital forensic investigators.
Furthermore, even in write-block-mode on a physical machine the writeblocker is caching writes. Especially in digital forensic investigations this can lead to seemingly incorrect results when taking hashes before and after investigations (consider that e.g. Windows is writing metadata to System Volume Information automatically). These changes are not written to the connected data device but are displayed.
Figure 1 and 2 show screenshots of such a behaviour. A USB stick was connected without writeblocker to the computer and a file 2025-06-04_Testfile.txt was created with the content "Test". The hash of this file is displayed in Figure 1. The USB stick was then disconnected from the computer and properly connected via the Wiebetech USB writeblocker. The hash was calculated and matched the hash in Figure 1. Afterwards the file was opened, edited and saved - all while the USB stick was still connected via the writeblocker. This succeeds without error (other writeblockers will reject the "save" command). When calculating the hash of the file again, a different hash is shown (see Figure 2). When disconnecting the USB stick and reconnecting it, the file and the hash revert to the original state, showing that the modifications were only cached by the writeblocker.
While this behaviour is not incorrect per se, it can lead to forensic tools not working properly. It is state of the art to check the hashes of entire data mediums before and after an investigation, to prove that the investigation did not corrupt any files. If Windows was changing metadata in the background automatically, these changes would be cached by the Wiebetech USB writeblocker, and the hashes from before and after the investigation would not match. Digital forensic investigators should be aware of this behaviour and take further steps to validate hashes.
Additionally, the Wiebetech USB writeblocker required a special driver to function. A lot of other writeblockers do not require special drivers, so this behaviour is unexpected.
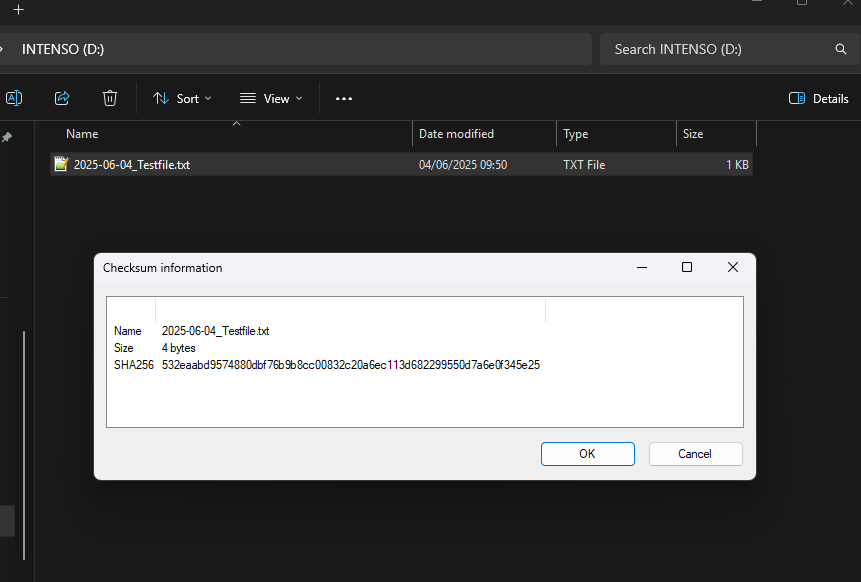
Figure 1: Screenshot of the initially created file with SHA256 hash (without Writeblocker)
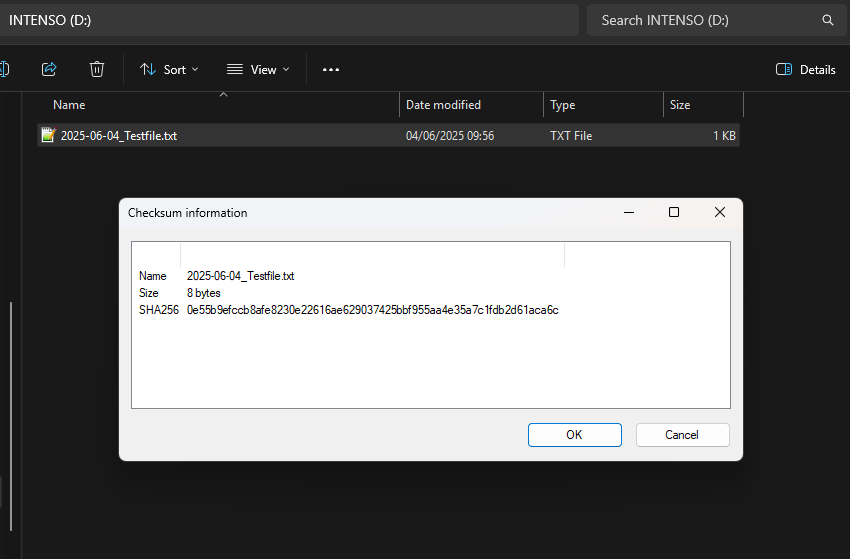
Figure 2: Screenshot of the same file incl. SHA256 hash, connected via writeblocker and file modified while connected with writeblocker
Wiebetech Forensic Ultradock (SATA)
Unlike the USB writeblocker, the Wiebetech Forensic Ultradock did not have issues with virtual machines. However, this writeblocker also caches writes which might lead to unintended results. It did not require an additional driver to function.
Other Writeblockers
The Logicube Portable and the Tableau TK8u USB 3.0 Forensic Bridge worked as expected in our tests. All writes to connected data devices were blocked, there was no caching of writes and no issues with virtual machines. The writeblockers worked seamingless without additional drivers.
Conclusion
When working with Wiebetech writeblockers, digital forensic investigators should take special care and read the manual carefully. These writeblockers work differently than the familiar writeblockers of other brands.
Furthermore, our research shows the importance of preparing forensic investigations and testing your tools (software & hardware).
