The devices we have looked at include Internet gateways, routers, modems, IP cameras, VoIP phones, etc. We have specifically analyzed cryptographic keys (public keys, private keys, certificates) in firmware images. The most common use of these static keys is:
- SSH Host keys (keys required for operating a SSH server)
- X.509 Certificates used for HTTPS (default server certificate for web based management)
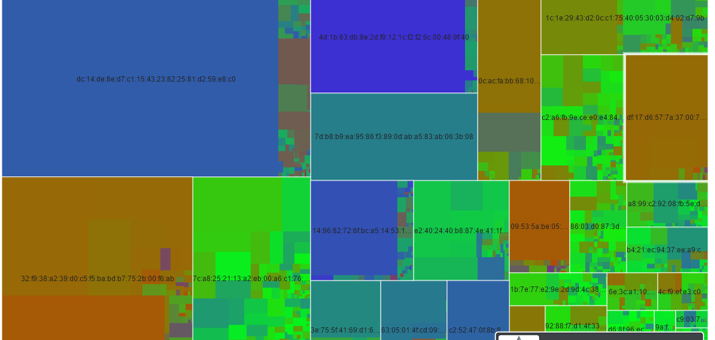
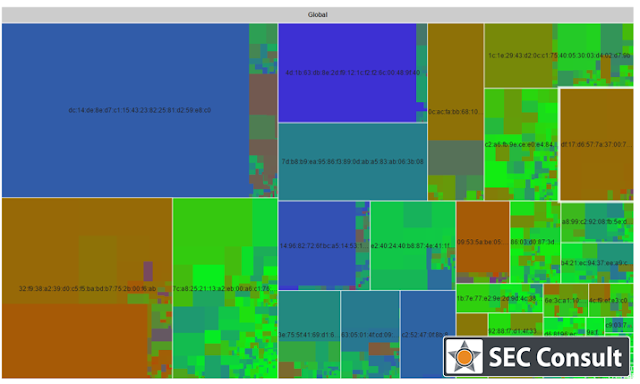
In total we have found more than 580 unique private keys distributed over all the analysed devices. Correlation via the modulus allows us to find matching certificates.
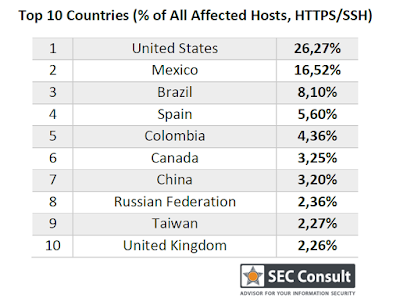
We have correlated our data with data from Internet-wide scans (Scans.io and Censys.io) and found that our data set (580 unique keys) contains:
- the private keys for more than 9% of all HTTPS hosts on the web (~150 server certificates, used by 3.2 million hosts)
- the private keys for more than 6% of all SSH hosts on the web (~80 SSH host keys used by 0.9 million hosts)
So in total at least 230 out of 580 keys are actively used. Other research has pointed out the extent of this problem (Heninger, Nadia, et al. “Mining Your Ps and Qs: Detection of Widespread Weak Keys in Network Devices“, Durumeric, Zakir, et al. “Analysis of the HTTPS certificate ecosystem“). However using our approach, an attribution at a vendor/product level is now possible. Plus the private keys have now been obtained.