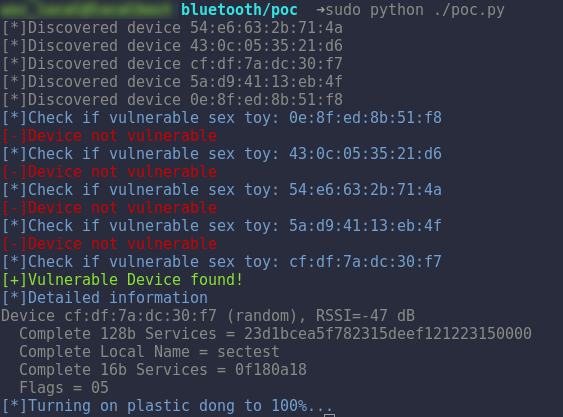
The Bluetooth SIG highly recommends to use Bluetooth LE 4.2 for obvious reasons. The “panty buster” product is currently using Bluetooth LE 4.0 (for compatibility reasons), although it would be capable of using Bluetooth 4.2 hardware wise. Besides the version in use, the second very important parameter is the key exchange. The key exchange is called pairing method. The different pairing methods are explained in the following paragraph.
Bluetooth Key Exchange aka “Pairing”
Passkey
The passkey pairing method is one of the most used methods. A key, which is set on the initiator side must be entered on the device, which should be paired. This method can be very insecure, because a lot of devices use the default passkey 0000 or 1234.
Pin-comparison
This method is used, when there is no input available (e.g. Pairing a device, without any buttons/keyboards). A 6-digit pin is presented at the initiator of the connection and the device itself. If the pins match on both devices a connection gets established.
Out-of-Band Pairing
Out of band pairing can be used by devices, which support for example NFC, where the NFC protocol is used to exchange the temporary key (TK).
Just Works
As the name already suggests it just works, unfortunately simplicity often leads to insecurities. In this case the TK is set to 0x00. This allows an attacker to decrypt the whole communication and even replay packets.
No Pairing
The last method is to use no pairing at all. This is the method Vibratissimo is currently using.
The pairing method depends on the following parameters:
- Display values
- Display with binary input (yes/no)
- Keyboard
- No input/output
- Keyboard/Display available
It’s quite obvious that some pairing methods can’t be used with sex toys. The reason for that is that there is no screen, keyboard or any input at all. One of the secure ways would be to use OOB pairing, or implement some kind of pairing button as it is used for other sex toys. No pairing is definitely not a good option, because the devices can be controlled basically by everyone within Bluetooth range.
The Swinger Club Problem
During one of the multiple calls with CERT-Bund, the manufacturer, the software developers and the hardware developers an interesting discussion arose. The hardware manufacturer stated, that they are aware of the problem that there is no authentication (aka “No Pairing”) in place and moreover that this is a desired property of the sex toy. The reason for this is, that there is a user group who wants to be controlled by random individuals without asking beforehand: Swingers. According to the vendor, visitors of swinger clubs like to have this feature.
We think that this user group, which is aware of that feature would be rather small and the bigger part of the users may not be aware of the fact that anyone could turn on their sex toys remotely. This fact is also confirmed by multiple other vulnerabilities of the exact same nature from other manufactures:
As a hotfix the hardware manufacturer already implemented a more secure pairing method in a new firmware version. The user has to send the device to Amor Gummiwaren GmbH to get the firmware updated as there are no ways to perform this remotely. Password protected pairing is already included in new devices but not enabled per default. From an IT Security point-of-view this feature should be an opt-out feature and not an opt-in feature.