Methods
As with most investigations, we had a lot of data at our hands. To reduce the amount of data to focus on, we took the following approaches:
First, we identified the install date of the machine and used information from the file system timeline to identify files that came from the install and files that were added or modified later. The latter category was then prioritized in the investigation.
One has to be aware that this method is vulnerable to timestomping attacks. Furthermore, older Solaris systems use a UFS filesystem, which has no birth timestamp to work with.
Second, we hashed configuration files and stacked the hashes (on a system itself as well as between systems). This allowed to reduce the number of files to investigate, as only one copy of a file per hash needed to be checked. The approach also highlighted files that had their default content modified.
Data Sources / Forensic Artifacts
Following are important data sources / forensic artifacts which we utilized for this aspect of the investigation.
System Install data
While this is not a proper artifact, it is nonetheless an important information to collect for a machine.
Depending on the Solaris version, one can identify its installation date with at least one of the following ways:
Init-based Services
Solaris still includes the traditional “init” system for running services. While this is deprecated for the modern Solaris versions, it is still available and usable.
The script files belonging to such services are stored in the directory /etc/init/.
Inetd-based Services
Solaris also includes the “inetd” system for running services on demand. While this is deprecated for the modern Solaris versions, it is still available and usable.
The configuration file, showing which commands are run for which sockets, is stored at /etc/inetd.conf or /etc/inet/inetd.conf.
On modern Solaris versions (checked for Solaris 11.4), this configuration has no active entries by default.
RC-based Services
Solaris also offers the “run command” system for running services based on the “run level” of the system. While this is deprecated for the modern Solaris versions, it is still available and usable.
The script files for the different “run levels” are stored in following directories:
- /etc/rc0.d/
- /etc/rc1.d/
- /etc/rc2.d/
- /etc/rc3.d/
- /etc/rcS.d/
Our practical experience showed that some duplication of scripts between different run levels can be expected.
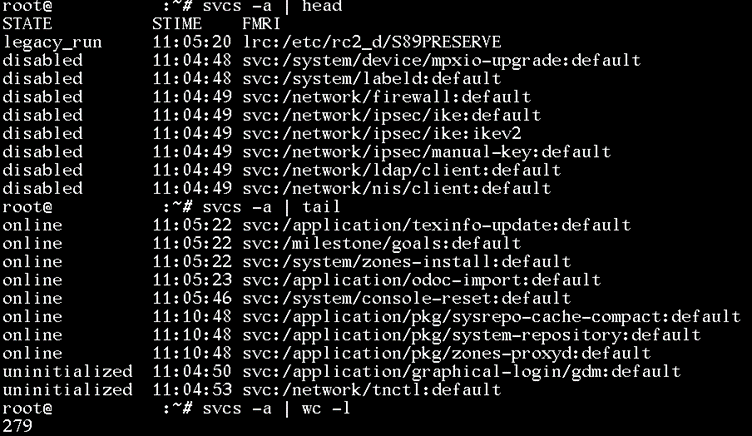
SMF-based Services
Service Management Framework (SMF) is the currently default way of running services on Solaris. It came into use with Solaris 10 and is meant to replace the other systems.
Services are defined using XML files. These are normally stored under /lib/svc/manifest/ and /var/svc/manifest/. Each service definition states the executions for the service, the dependencies as well as environment settings. A service definition can directly define the commands to run for the service or reference a script file. These elements can be quickly found by filtering the configuration file for the string “exec=”. Service script files are normally stored under /lib/svc/method/.
For each service, a separate log file is kept under /var/svc/log/. This log shows service-specific messages, including when the service was started and stopped.
On a live system, the services can be enumerated using “svcs -a”. This will show running services, disabled services as well as services started through legacy systems. It also shows the start time of running services.