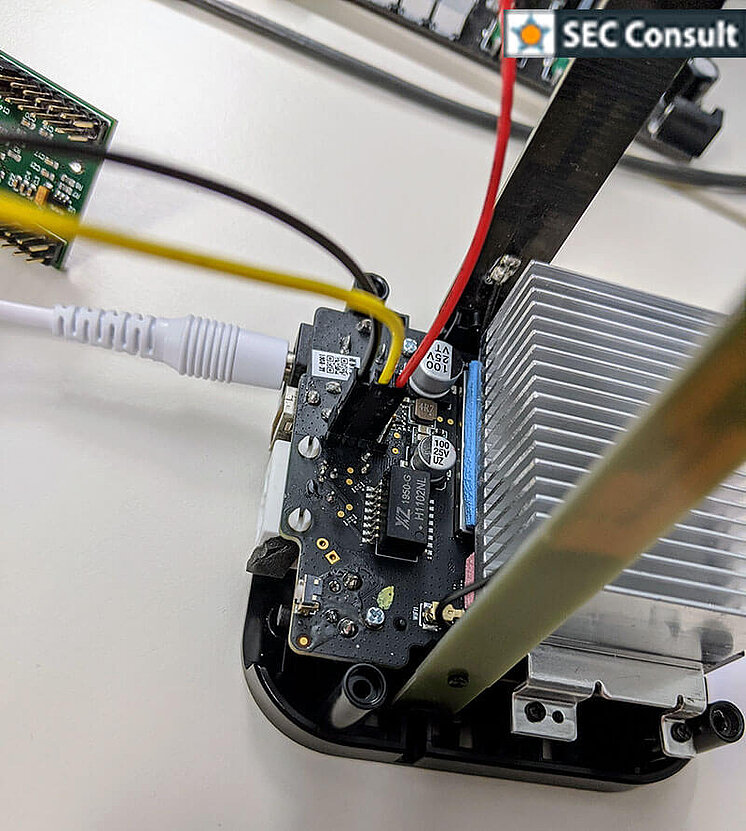
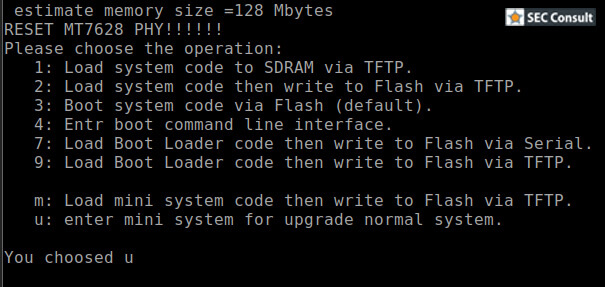
As visible above, this references a "WPAPSK1" NVRAM entry loaded as "pass" variable. This closes the deal. The previously found WPAPSK1 key from the config file (seemingly stored in NVRAM) is indeed the actual password for the shell login of the operating system. So with the username "eufycamera" and the password "Zjk0YTA3" it is possible to log into the operating system of the Homebase devices via UART and explore it further. If the WPAPSK1 entry was empty, the password Anker39#* would be used. As mentioned above, because of time constraints, no further research could be conducted to identify other security vulnerabilities in the devices.
Conclusion
Now, in 2022 we took another short look at the system. A lot has happened since we last researched the device.
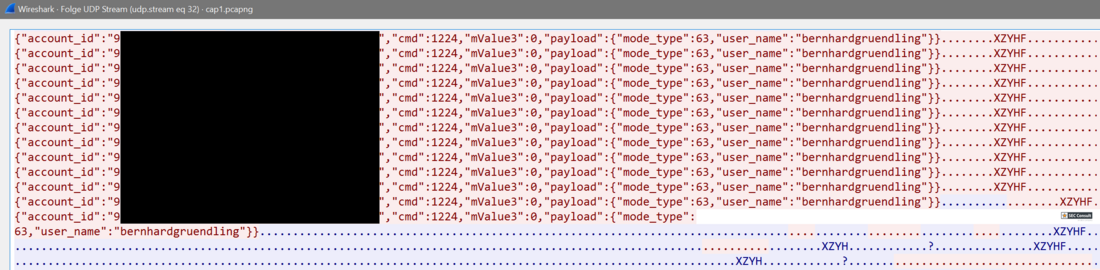
Anker/eufyCam had their first severe security incident where attackers were able to look into other users' camera feeds. After this, a series of CVEs related to Eufy was published by Talos Intelligence and Anker made affirmations to improve the security to prevent something similar from happening again. Looking at the device traffic now, it seems that indeed a lot of improvements were made. The commands are not transmitted unencrypted anymore, and the account identifier and usernames are also encrypted in transit now. This is pleasant news and shows that incidents and community research can really make a difference.
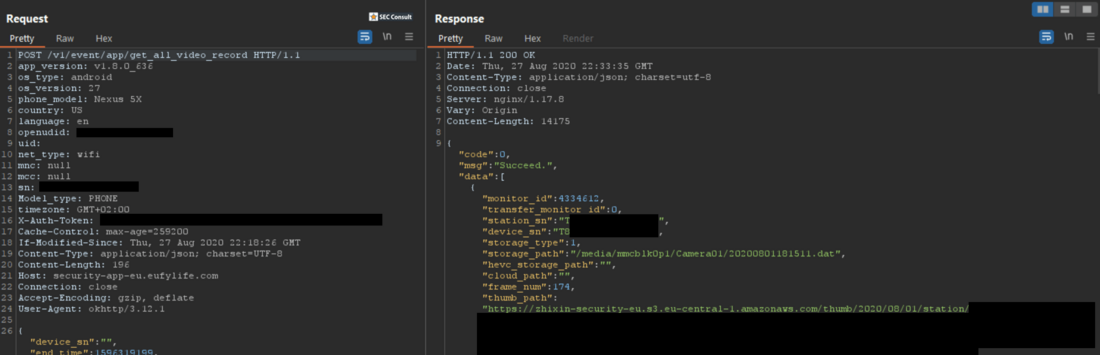
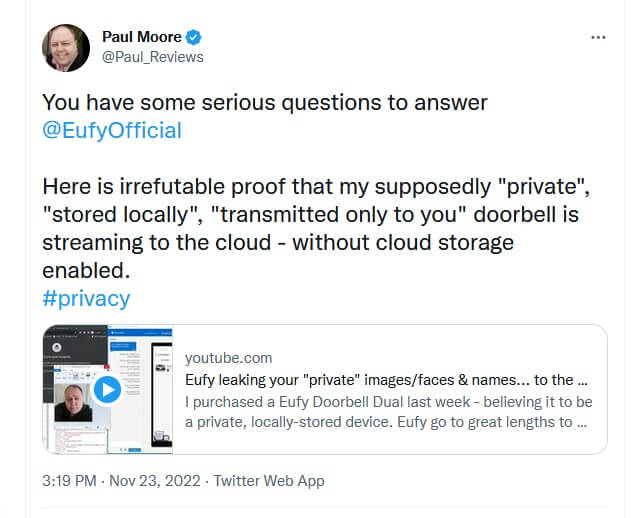
But sadly, thumbnails of all recorded images still seem to be transferred into AWS, so the device does not fit our requirements for privacy. With this blog post we want to foster further community research which may lead to further interesting findings like the following research SEC Consult has published in the past:
SEC Consult highly recommends to perform a thorough security and privacy review of the Anker eufyCam products by security professionals to identify and resolve potential further security issues.