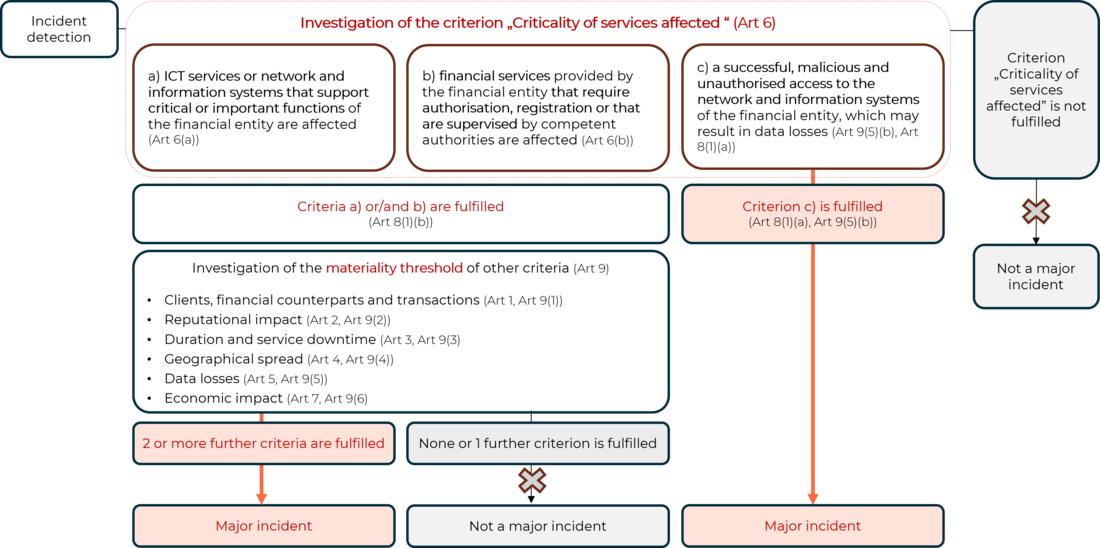
Pillar III - Digital operational resilience testing programme
The Chapter IV of DORA regulates the requirements for digital operational resilience testing. DORA outlines two primary forms of assessments:
Digital Operational Testing Programme
In other words, security testing of all ICT systems and applications that support critical or important functions at least once in a year.
DORA narrows the scope of security testing to “ICT systems and applications supporting critical or important functions” (Art 24(6) DORA).
For the security testing, DORA provides an exemplary list of testing methods: vulnerability assessments and scans, open-source analyses, network security assessments, gap analyses, physical security reviews, questionnaires and scanning software solutions, source code reviews where feasible, scenario-based tests, compatibility testing, performance testing, end-to-end testing and penetration testing.
DORA requires these tests to be carried out once a year. This means that the financial institution should develop a test plan for one year. The analysis of which applications and systems fall within the scope must be renewed regularly, as the ICT-network changes over time. In other words, the test plan and scope may vary from year to year.
TLPT
Advanced testing of ICT tools, systems and processes based on threat-led penetration testing (TLPT) every three years.
TLPT will be mandatory for selected financial entities only. These will be informed by the respective competent authority.
The scope of TLPT encompasses several or all critical or important functions of a financial entity, and it shall be performed on live production systems supporting such function.
In its core, TLPT is based on the TIBER framework, but includes advanced requirements. Such as the mandatory purple team testing as part of the project. Also the organizational structure of participants is slightly different. As of today, TIBER is implemented in many EU member states with their own country-specific guidance. How much the existing requirements differ from TLPT, varies between the EU member states.
In general, the TLPT procedure is as follows: