The focus of this blog post is the question of which digital business continuity testing requirements are applicable to cloud environments under the DORA regulation.
Unlocking Cloud Security: Insights from the DORA Framework
cloud DORA
Cloud security is considered in DORA from two angles:
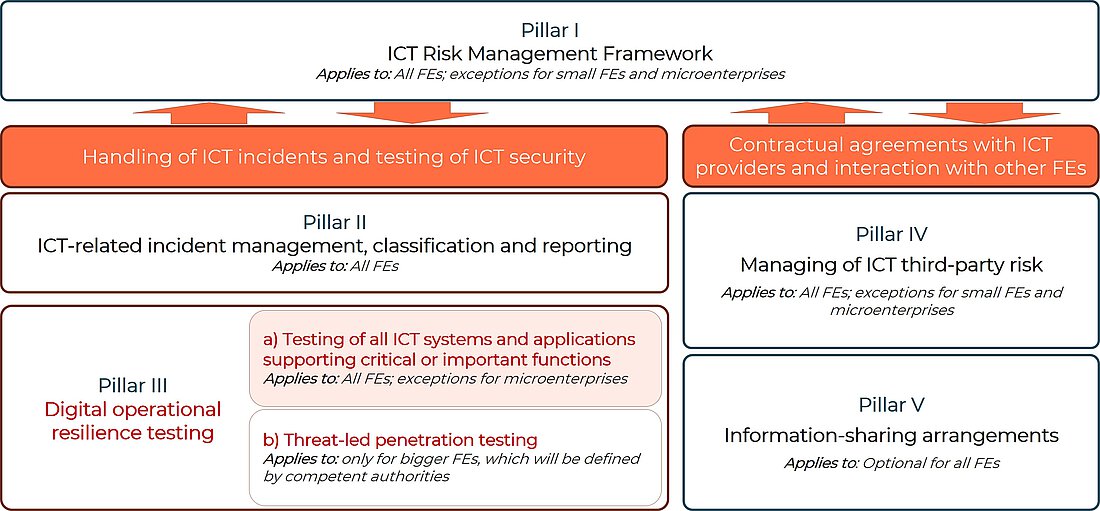
- Testing the digital operational resilience of a financial organisation (Art. 24 and 25 DORA) (shown in Figure 1 under Focus III a)).
This requirement stipulates that all ICT systems and applications that support critical or important functions must be tested regularly. This means that every company must examine and, if necessary, test its infrastructure in the cloud.
- ICT risk management of critical third-party ICT providers (Art. 31-44 DORA) (shown in Figure 1 under Focus IV).
Cloud providers such as Microsoft Azure, Google Cloud Project or AWS fall into this category due to their importance for the European financial market.
This means that there are two levels of criticality in DORA:
- Critical or important function - critical to the operations of a financial organisation
- Critical third-party ICT service provider - systemic in nature for the stability of the European financial market.
Firstly, every company within the scope of DORA that operates critical or important functions for business capability in the cloud, is obliged to test these for vulnerabilities. Such a test must be carried out annually for all critical or important applications. These requirements originate from Articles 24 and 25 of the DORA Regulation. Therefore, it is not the security of the cloud provider that is tested here, but rather an evaluation of how securely their implementation and configuration of the individual cloud components and authorisations has been carried out.
On the other hand, cloud providers such as Microsoft Azure, Google Cloud Project or AWS represent a critical ICT third-party service provider due to their important position for the European financial market. These requirements are regulated in Articles 31-44 of the DORA Regulation. This also means that these third-party service providers are audited by the European Union and are covered by the monitoring framework for critical third-party ICT service providers. In this procedure, the third-party service provider is audited as an organisation. For example, its ICT risk management framework, risk management processes, physical security, governance arrangements, ICT audits, etc.
What needs to be achieved?
The aim is to identify weaknesses, deficits and gaps in digital operational resilience, assess readiness for ICT-related incidents and take swift remedial action.
Cloud penetration test - operator or customer?
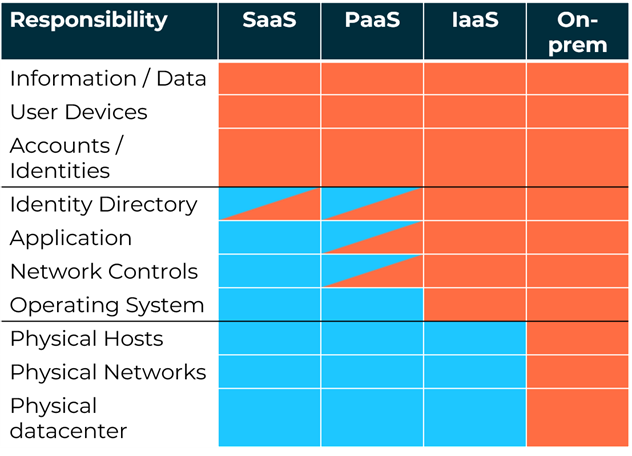
One of the first questions that every customer of a major cloud provider (AWS, Azure, GCP) will ask is: Who is responsible for the security of the data in the cloud? This is where the cloud providers' shared responsibility model comes into play. This clearly shows which aspects of security the provider is responsible for and which the customer is responsible for.
The cells marked in orange represent the topics that the customer must secure. Those in blue concern the cloud operators.
For example, as can be seen in the graphic above, no cloud provider takes responsibility for the correct implementation of access authorisations (identity and access management). The secure configuration of storage such as AWS S3 buckets is also the responsibility of the customer, which leads to many insecure public S3 storage and data leaks. It is therefore of great importance for companies affected by DORA to also evaluate whether critical functions for business operations are operated in their cloud infrastructure. If this is the case, these must be tested for vulnerabilities in the same way as other on-premise infrastructures.
Assumed Breach Scenario
Such a test for vulnerabilities in a cloud infrastructure can be carried out very effectively using an assumed breach cloud penetration test. Experienced cloud penetration testers check your implemented and utilised cloud infrastructure for vulnerabilities and misconfigurations. The manual combination of seemingly unimportant misconfigurations can lead to critical vulnerabilities that allow access to sensitive data.
In an Assuemed Breach Cloud Penetration Test, the lowest privileged user roles in the infrastructure to be tested are provided to the testers. This simulates the scenario of a successful phishing attack or a data leak and evaluates which authorisations and what damage an attacker can cause as a result. Penetration testers combine methods of reconnaissance with lateral movement and privilege escalation in order to spread further and further into the cloud infrastructure. In most cases, the combination of different vulnerabilities and misconfigurations makes it possible to escalate from a normal user up to an administrator of the entire infrastructure.
How can SEC Consult support you?
Security testing - be it of software, firmware or hardware - is our daily business. SEC Consult supports you in uncovering attack vectors in your cloud and container infrastructure. With our advanced exploits and extensive experience, we identify vulnerabilities, misconfigurations, privilege escalation opportunities, lateral movement between environments and even intrusions into your local infrastructure. Our experienced consultants can provide you with optimal support in drawing up a suitable test plan and carrying out the tests. This not only ensures compliance with DORA requirements, but also strengthens your ICT network against cyber threats.