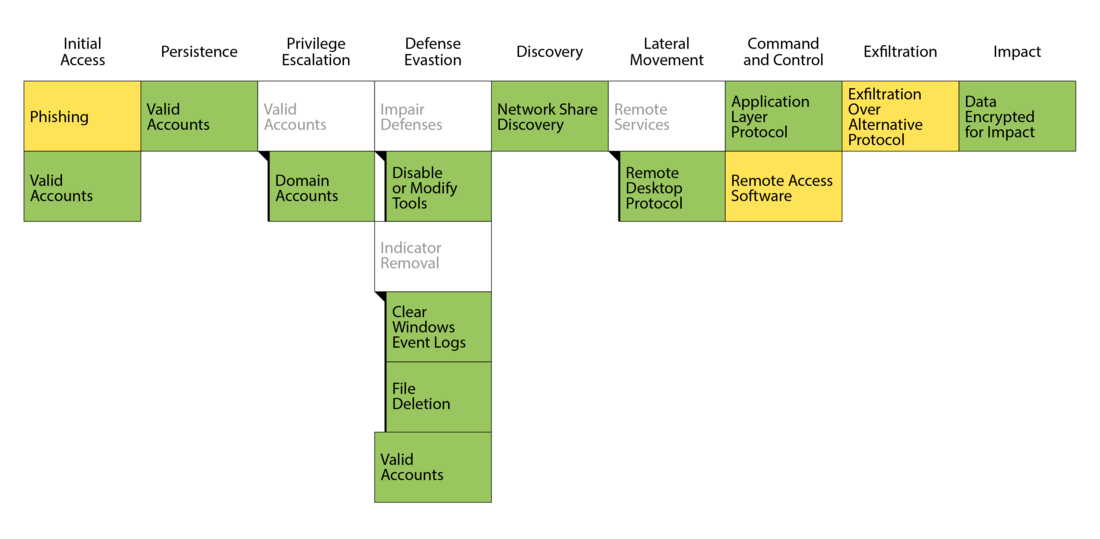
Phishing (T1566)
Due to the defense evasion steps taken by the attacker and the generally sparse data available, the initial access vector in this specific case could not be conclusively identified.
Noticeable however is that the company was successfully attacked with phishing e-mails multiple times six months and twelve months before this case. Those infections lead to malware execution, including AgentTesla and QakBot. Such malware could have been used to steal credentials. A clear connection to the ransomware case could not be established, but it is possible that credentials acquired back then were used to initiate the intrusion into the network.
Valid Accounts (T1078) & Valid Accounts: Domain Accounts (T1078.002)
We saw the attacker use valid credentials extensively. Valid credentials stolen at some point prior to the attack were likely the key to the network. It enabled the attacker to move quietly through the network, execute malware, and eventually exfiltrate data.
At a point in time that could not be identified, the attacker managed to compromise a domain admin account. That account was then almost exclusively used for all attacker actions.
Impair Defenses: Disable or Modify Tools (T1562.001)
The attacker was seen deactivating the Windows Defender Real-Time Protection on a workstation before deploying his tooling. This was not done immediately after connecting to the workstation, but rather after some local reconnaissance using legitimate tools and exploration of accessible data were already done.
With Windows Defender - the only line of endpoint defence - out of the way, the attacker could act without hinderance on the devices. The attacker was observed using PCHunter64.exe and PowerTool64.exe on multiple server systems. Based on official documentation for both tools, they are similar in function as Process Explorer. Though it remained undetermined what the attacker used these tools for, it is probable that the attacker employed them to deactivate security measures on the affected systems.
Indicator Removal: File Deletion (T1070.004)
The attacker appeared to be aware of the traces he left behind. He stored and executed all his tools from the directory C:\PerfLogs, which he ultimately cleared of all its content, effectively removing all executables and their outputs to evade analysis.
Indicator Removal: Clear Windows Event Logs (T1070.001)
Showing awareness of the value of Windows Event Logs in investigating his actions, the attacker promptly deleted all event logs on a system using PowerShell after completing the encryption process with the ransomware. Following command was used:
powershell $logs = Get-WinEvent -ListLog * | Where-Object {$_.RecordCount} | Select-Object -ExpandProperty LogName ;
ForEach ( $l in $logs | Sort | Get-Unique ) {[System.Diagnostics.Eventing.Reader.EventLogSession]::GlobalSession.ClearLog($l)}