Visual Signature Spoofing in PDFs
research
The Portable Document Format, better known as PDF, is one of the most widely used formats for the exchange of digital documents. In 1999, support for digital signatures was added to PDF files with version 1.3.
Forged signatures exist roughly as long as signatures themselves, it is no surprise that since their introduction there have already been multiple successful attacks against the implementation of digital signatures in PDFs (e.g., see https://www.pdf-insecurity.org/).
Most previous attacks exploit vulnerable PDF applications so that they display invalid signatures as valid. However, what if we instead choose a different target: the user who views the document and must decide whether it is properly signed.
Since 1999, the number of features available in PDF has grown significantly. Nowadays, PDFs embed multimedia content, offer submittable forms, and even provide scripting capabilities using JavaScript.
The question we ask is: Can we trick a user into believing an unsigned PDF is signed, using only the features defined in the PDF specification?

Visual Signature Spoofing is an attack technique in which an attacker attempts to imitate the appearance of a PDF application for signed documents. When a signed PDF is opened, multiple Signature Indicators are displayed in PDF applications informing the user that the currently opened PDF contains a trusted signature. Using these signature indicators, a user can make an informed decision about whether a document is signed and to be trusted. Visual Signature Spoofing undermines these trust assumptions by mimicking the behavior and appearance of real signature indicators.
Typical Signature Indicators in PDF Applications
During our research, we identified four types of User Interface (UI) elements that serve as signature indicators. To imitate these signature indicators, we first have to observe their typical behavior in the application.
Signature Graphic
The signature graphic is the visual representation of the signature in the PDF itself. It is often clickable to show further information about the signature, such as the signing date and the signee. The signature graphic is embedded in the PDF page and moves when the PDF is scrolled or zoomed.
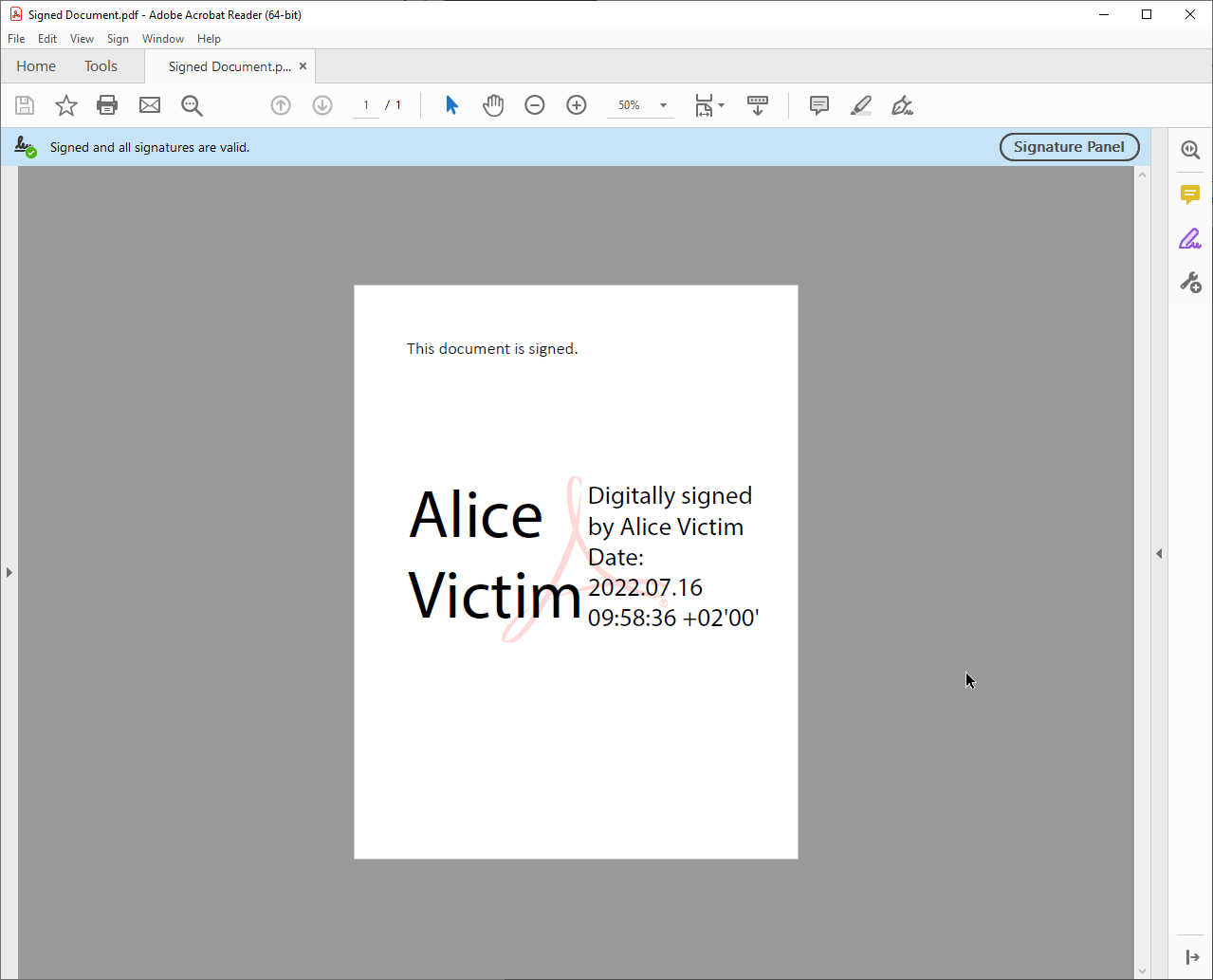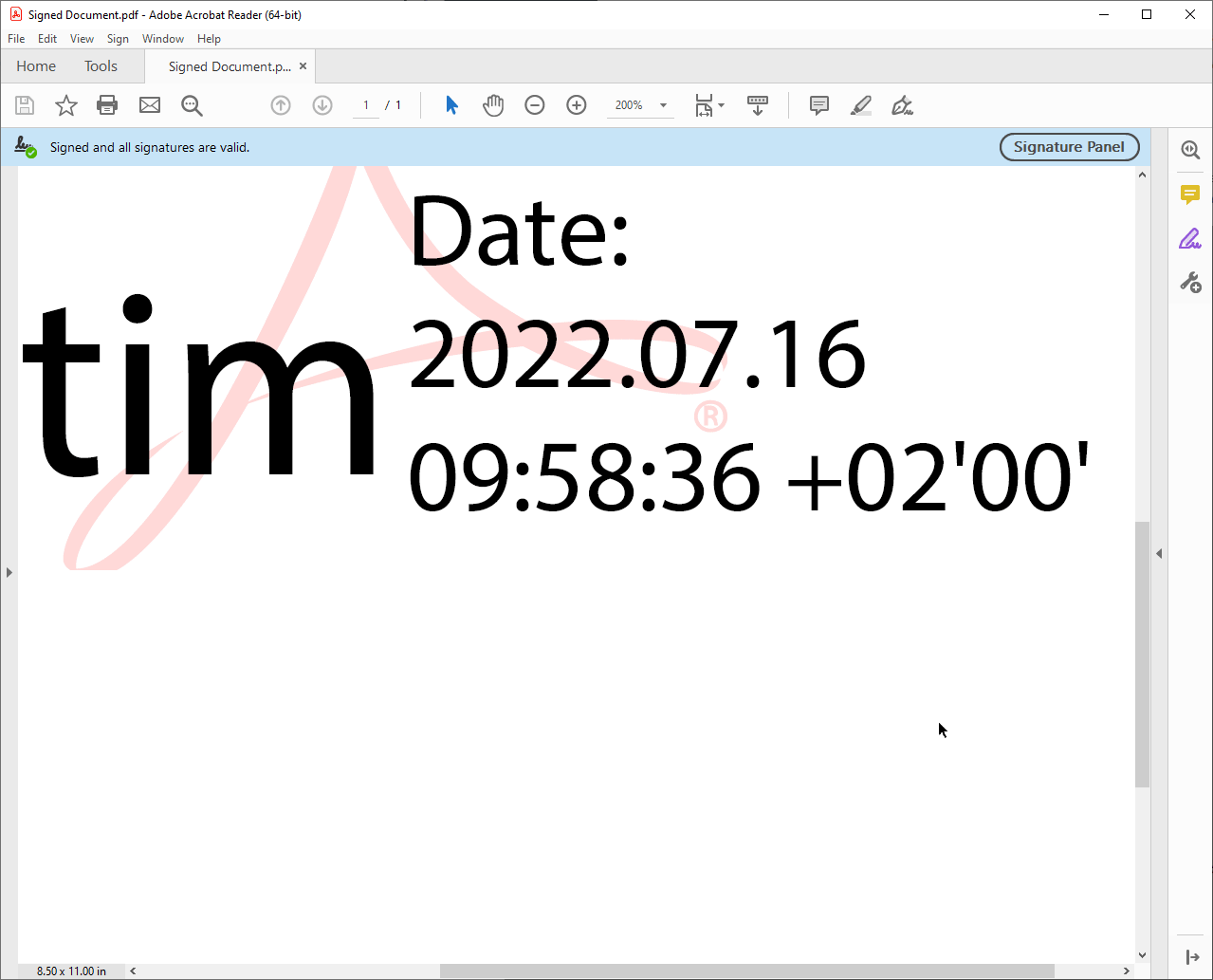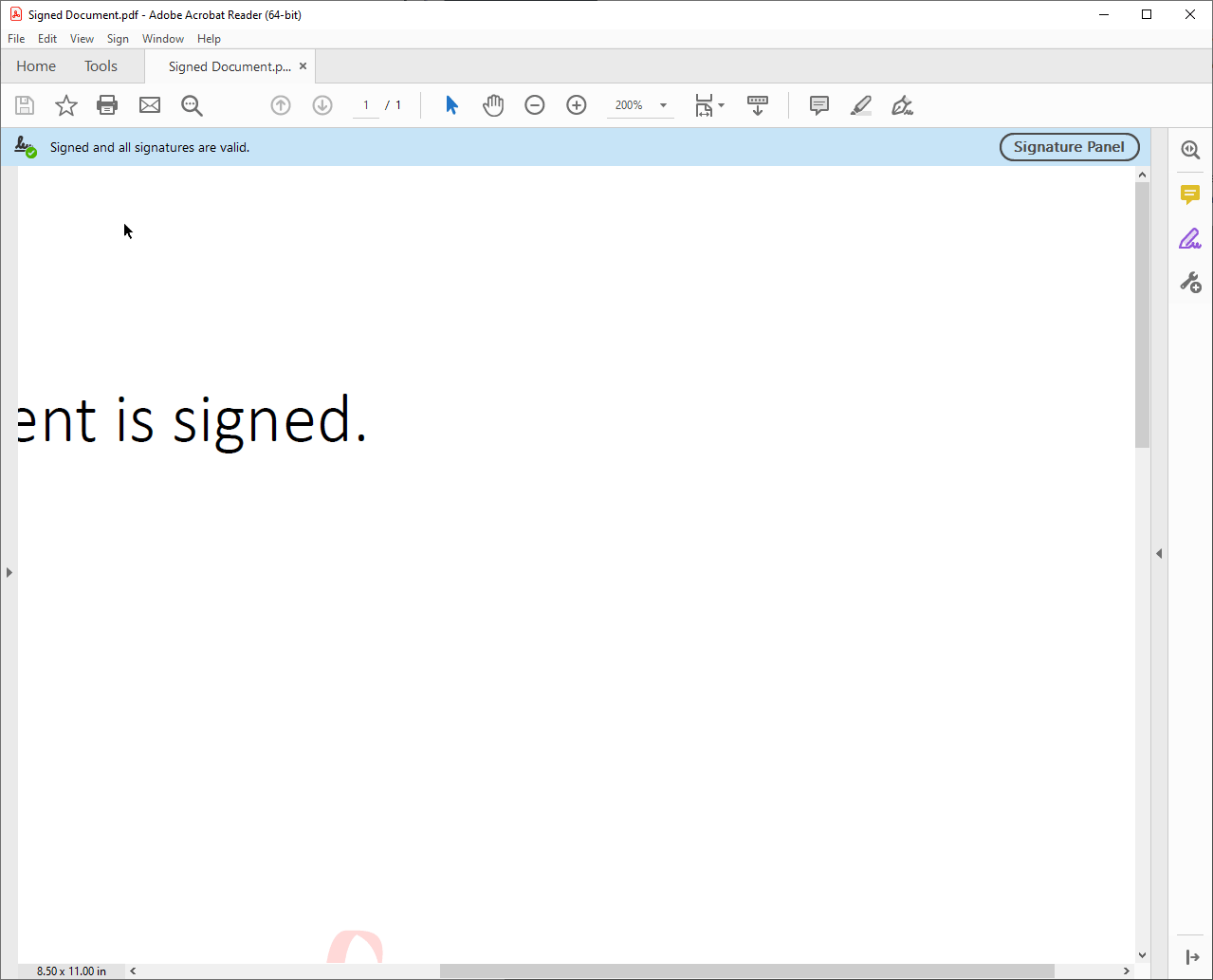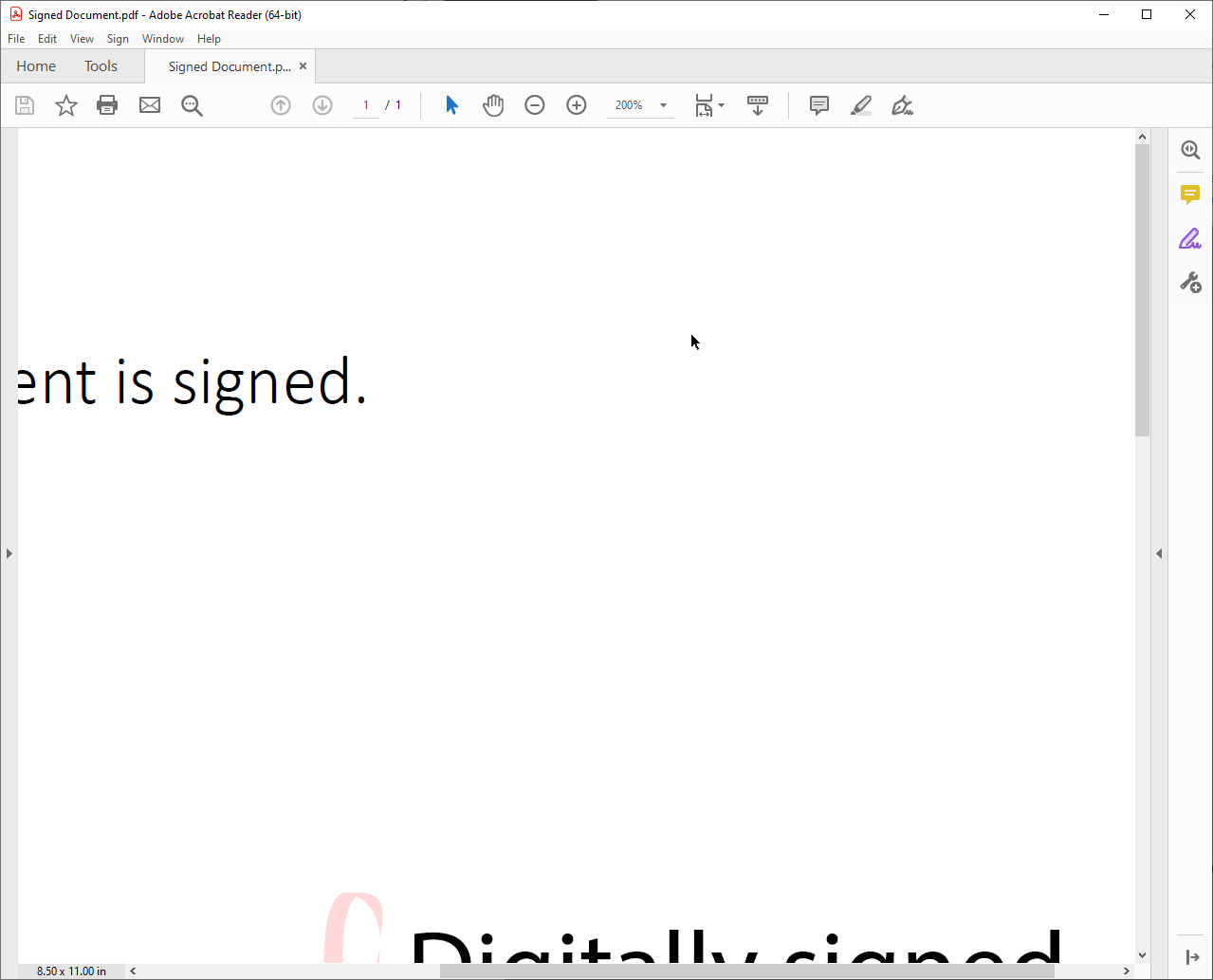
Signature Bar
Many PDF applications display a banner, typically at the top of the document viewport, which shows basic information about the validity of the signature and warns the user when verification problems occur. After the signature graphic itself, this signature bar is the most prominent signature indicator in PDF applications. Since the signature bar is part of the application UI, it remains unchanged when the user zooms and scrolls.
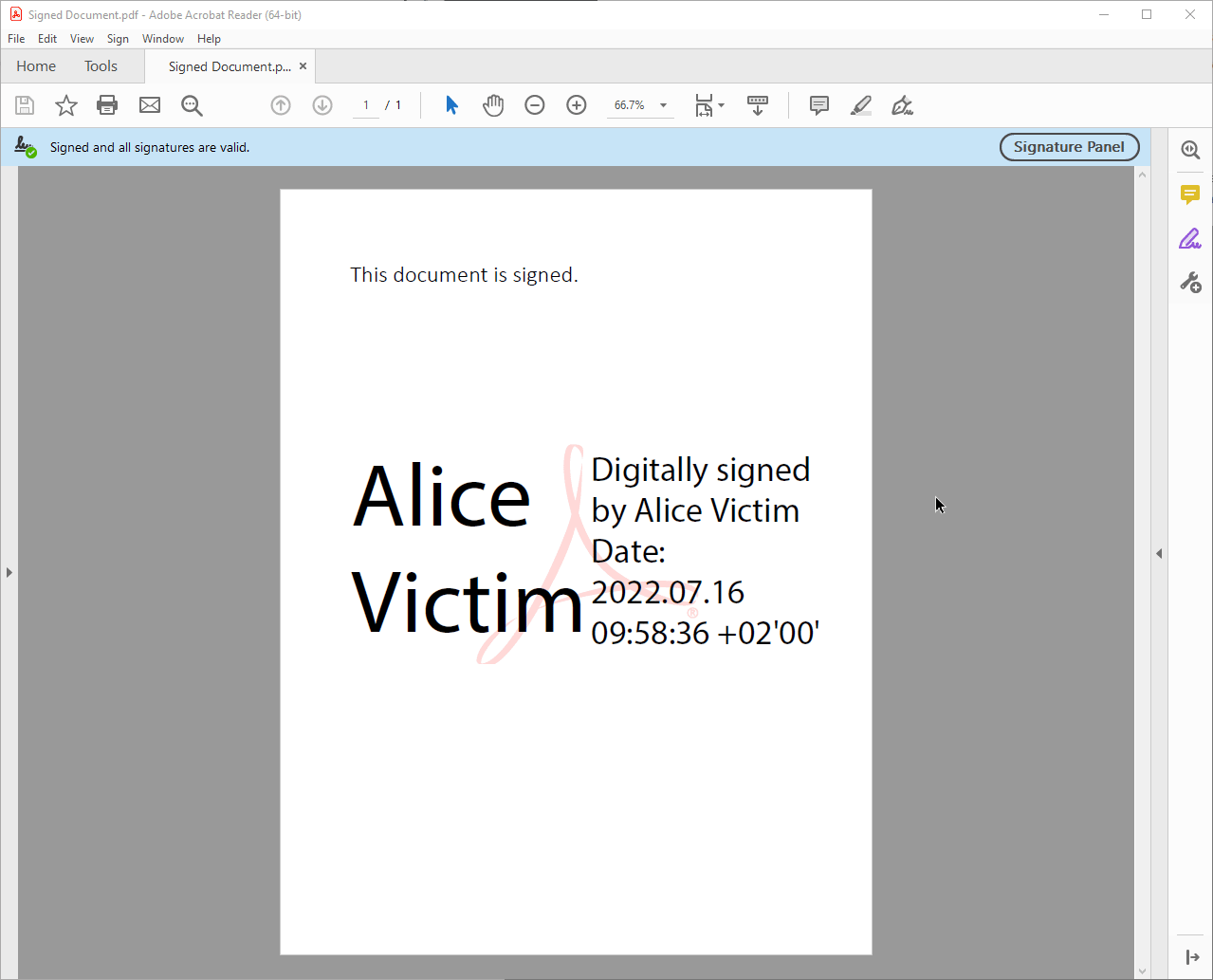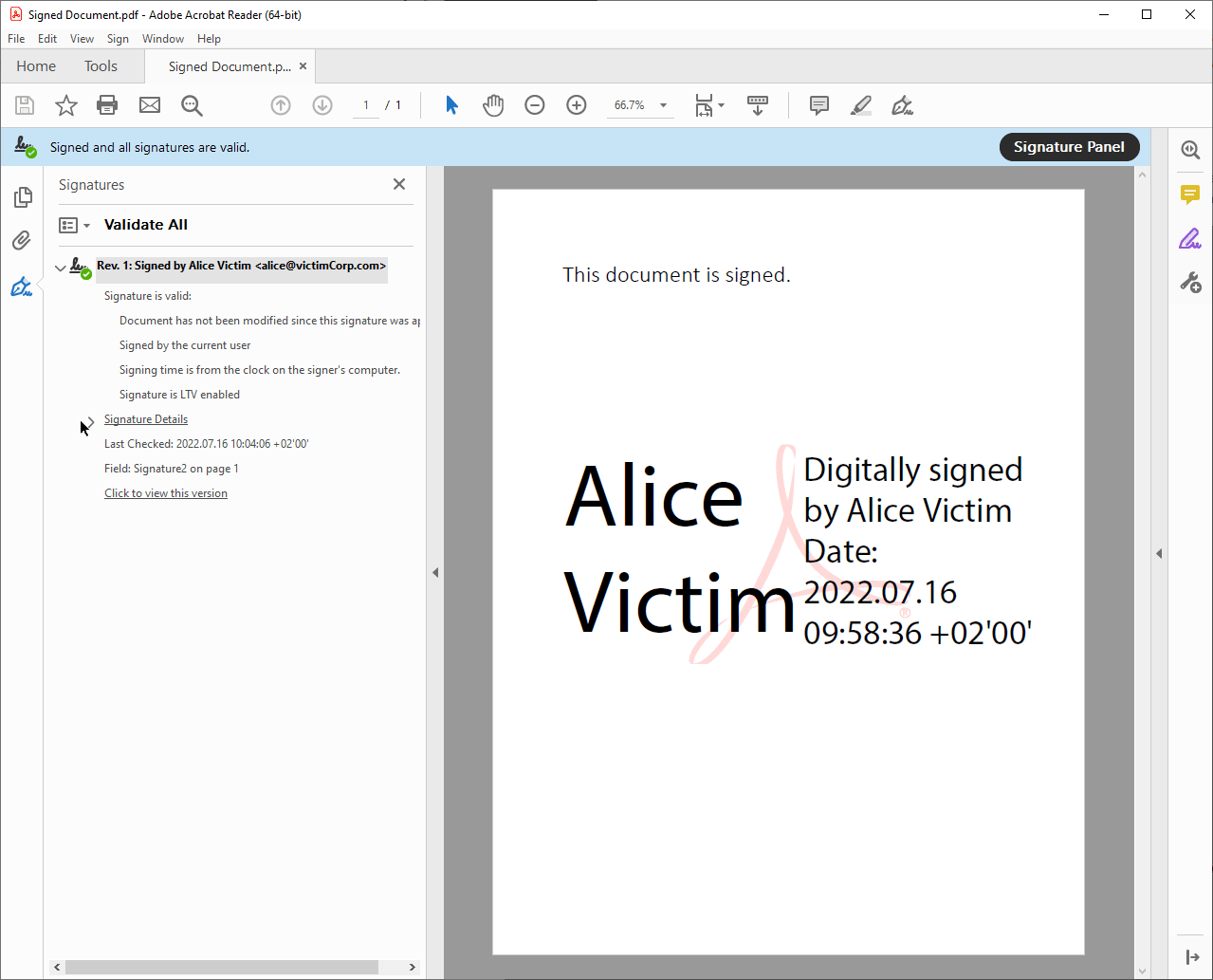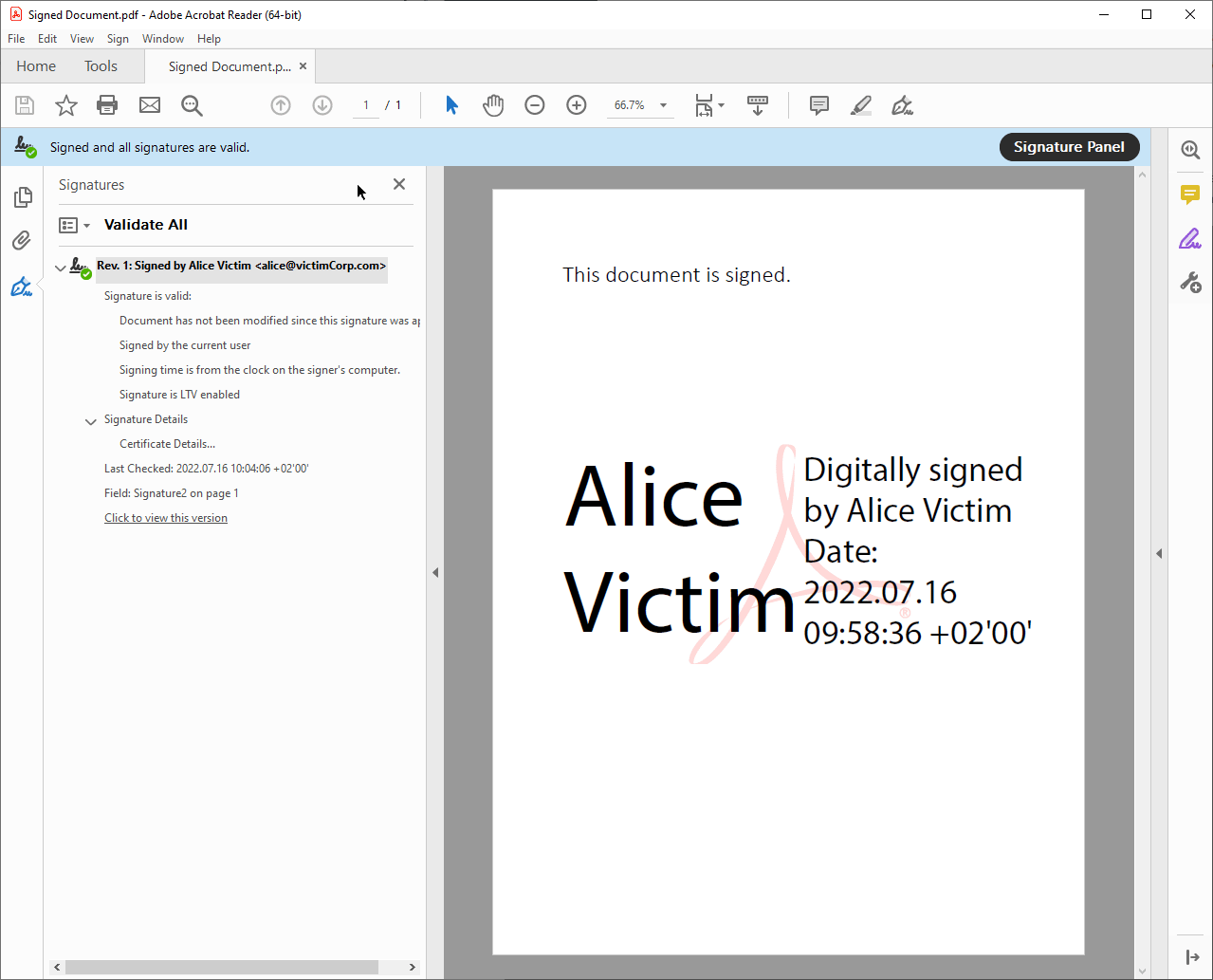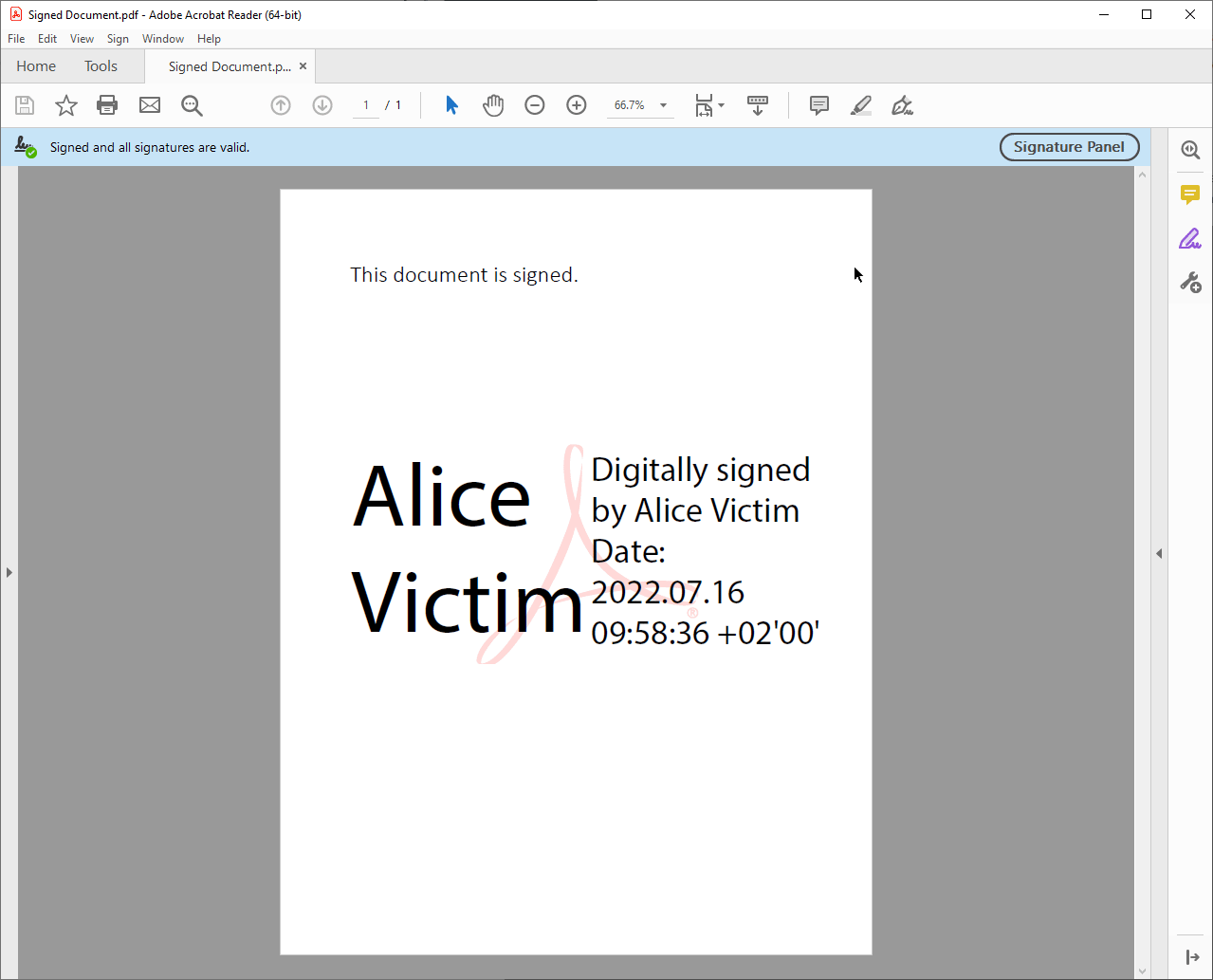
Signature Panel
The signature panel is often located at the side of the document viewport and shows basic information like the verification status and signer of the PDF. It can be opened and closed by the user and, like the signature bar, does not change position or size when a user zooms or scrolls.
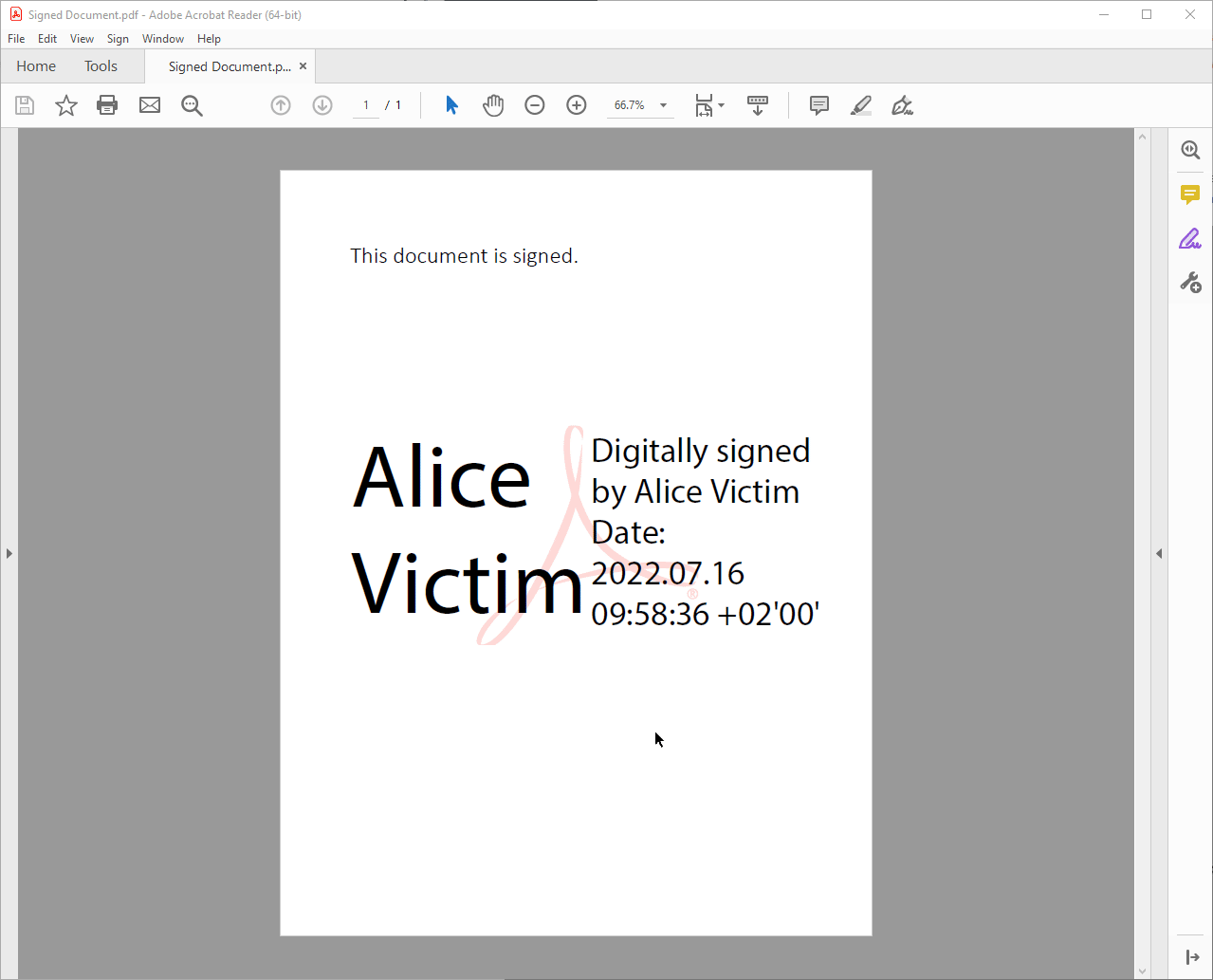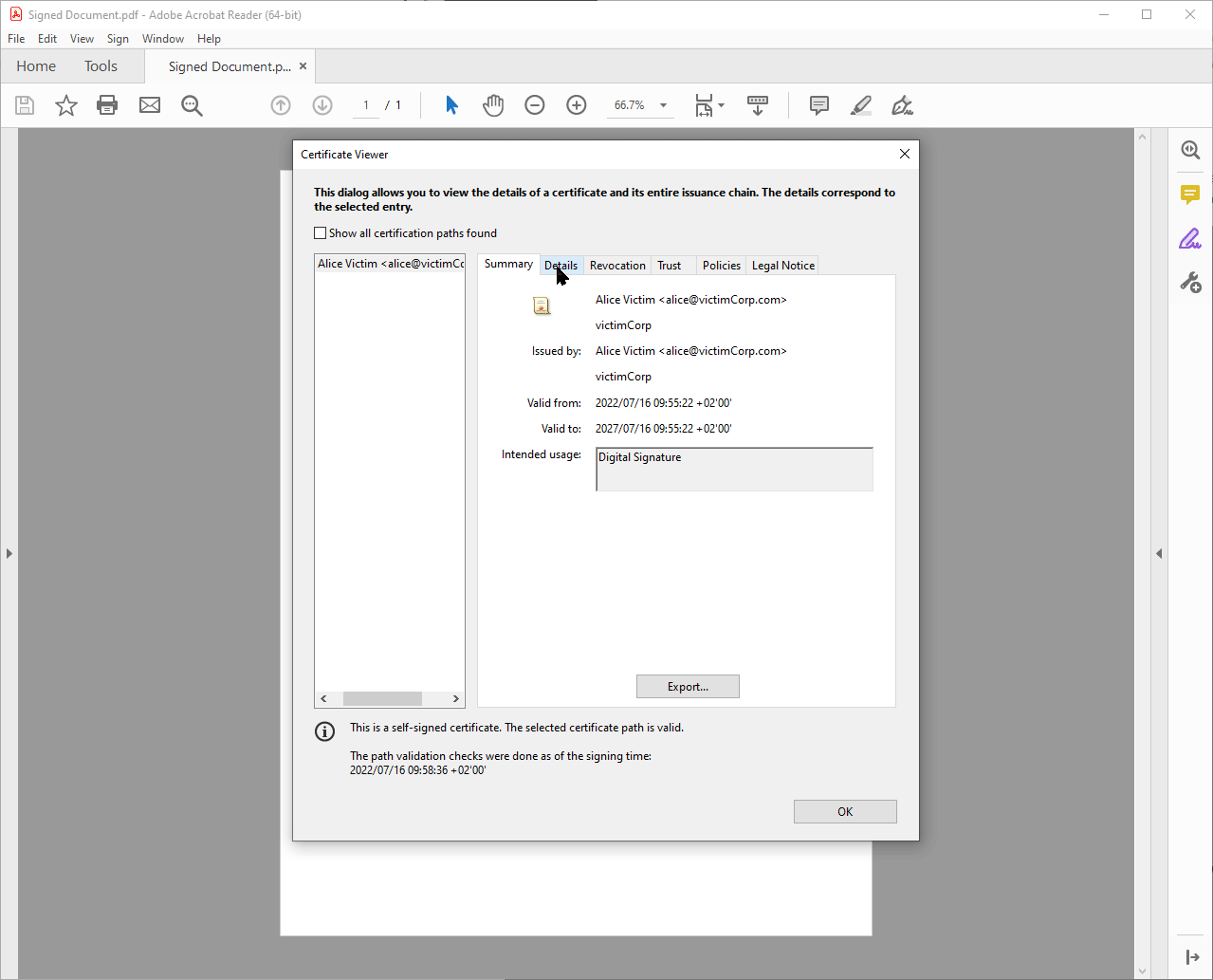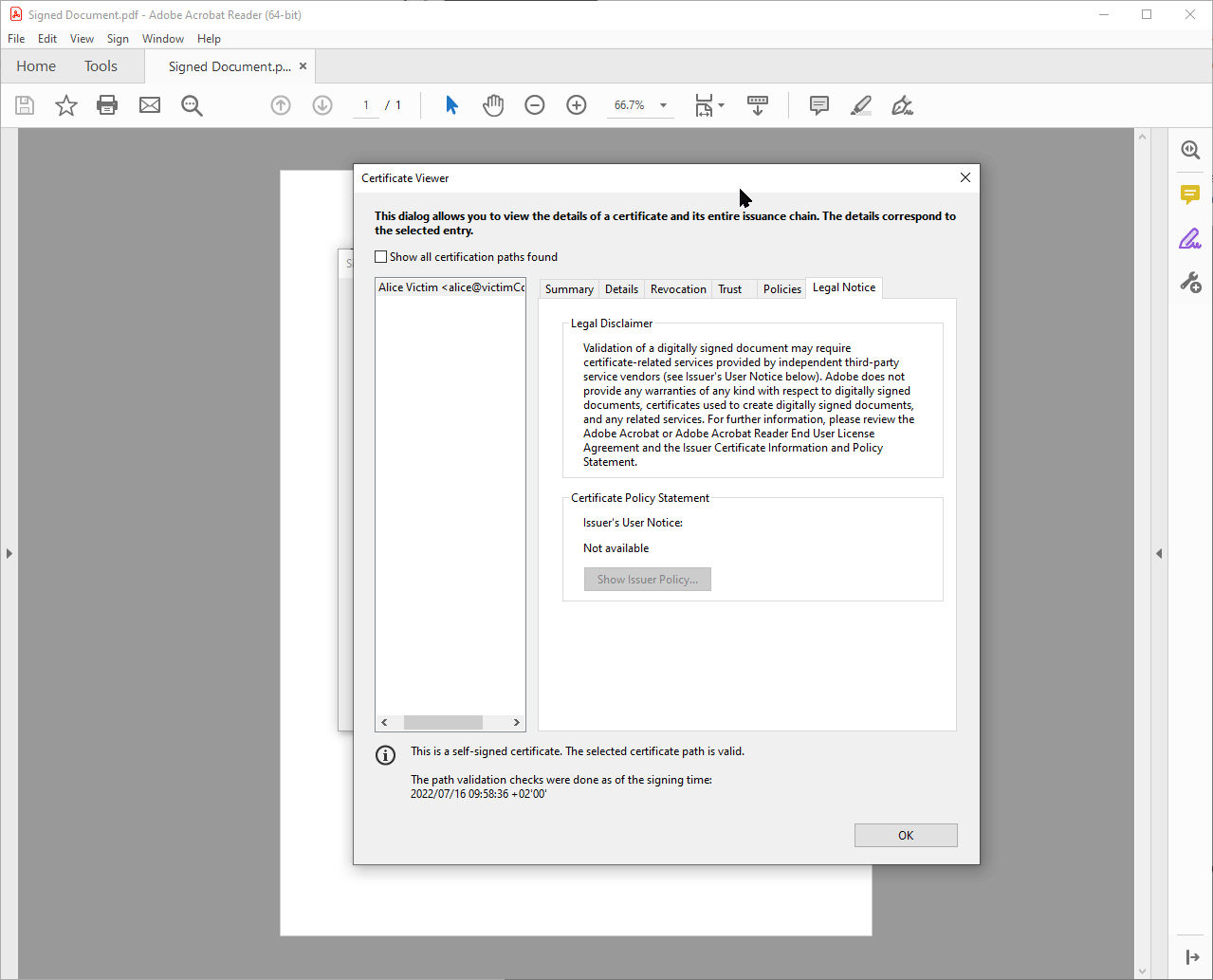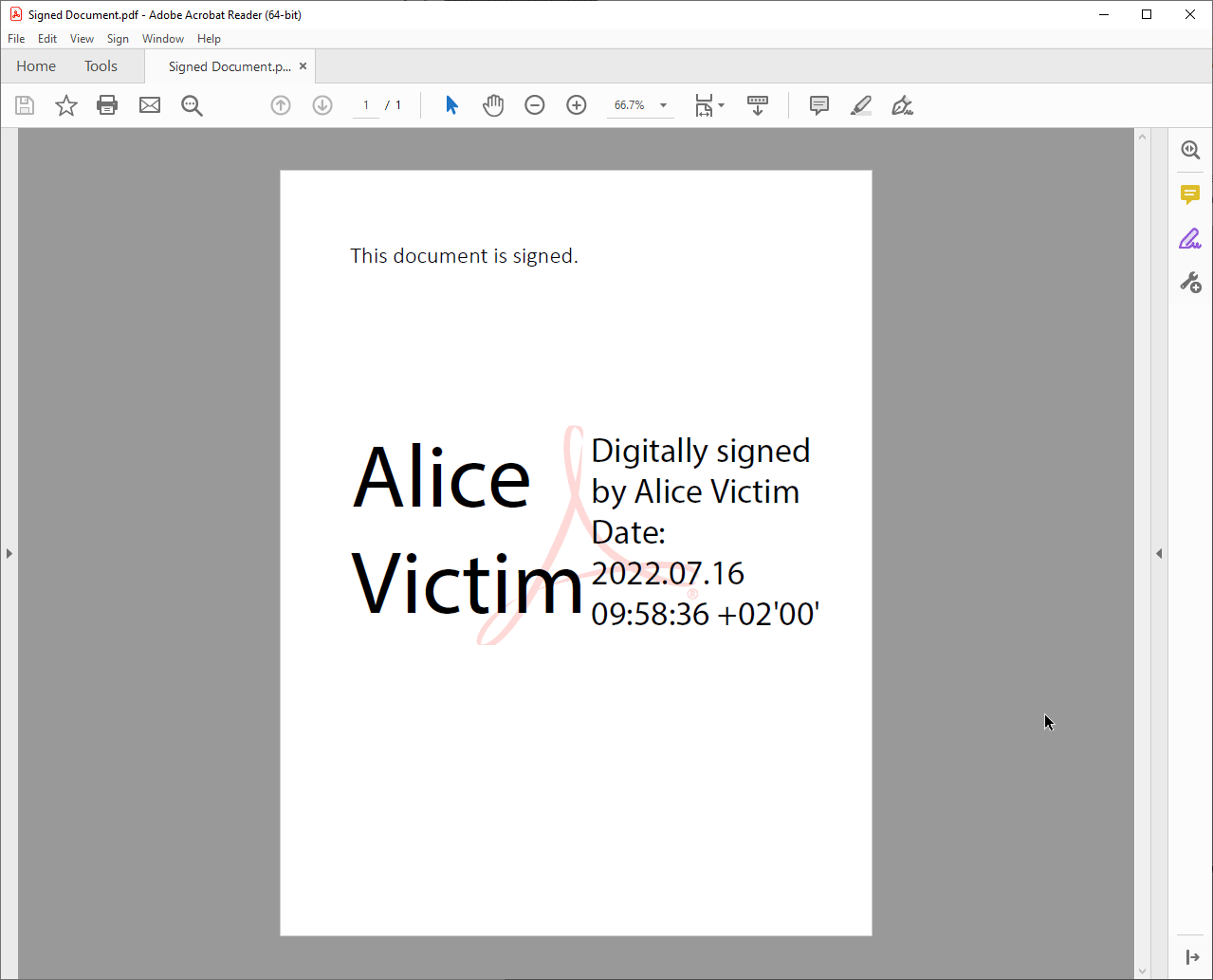
Windows
More specific information about the signature, e.g., details about the signature certificate, is displayed in pop-up windows. These windows can be opened in various places, such as by clicking the signature graphic. The appearance and behavior are partially dependent on settings of the operating systems such as the operating system color scheme. These windows can be moved by the user.
Visual Signature Spoofing Techniques
Next, we identified PDF features to imitate the signature indicator behavior. The following requirements need to be fulfilled for a convincing spoof:
The PDF objects must be movable for a correct positioning in the viewport.
The PDF objects must be interactive. Most interactions occur when a user clicks something. Additional interactions occur when a user hovers over an UI element with the cursor.
We must be able to freely choose the appearance of the PDF objects.
We should be able to hide PDF objects.
A combination of JavaScript and Widget Annotations was successful in fulfilling these requirements. Widget annotations are the visual representation of a form element, i.e., a simple button. Furthermore, widget annotations have multiple triggers for actions, e.g., when a page is opened, or when the user moves the mouse over the annotation.
Since version 1.3, PDFs support the execution of JavaScript as an action. JavaScript supports a wide range of features, some of which allow us to move and hide Widget Annotations.
By combining Widget Annotations with JavaScript, we can create a convincing spoof using the following strategy:
For each interactive UI element, e.g., a button or image, a new widget annotation is added. We set the appearance of the widget annotation to fit to the spoofed UI element. We also add a hidden widget annotation which starts a JavaScript script that continually positions the widget annotations correctly in the viewport. When a widget annotation is clicked, we hide or show other widget annotations, to imitate opening and closing other signature indicators.
Attack scenario
Alice and Bob use digital signatures in PDFs and trust each other's signature. The attacker Eve tries to create a PDF that imitates Alice's signature against Bob. The visual signature spoof is successful if the PDF does not contain a signature but convinces Bob that it is signed.
We assume that Bob only opens the document, reads it, verifies the signature by interacting with the signature indicators and closes it. Zooming and scrolling is also allowed.
This means that the goodness of a spoof depends only on how well the signature indicators in the PDF application can be spoofed.
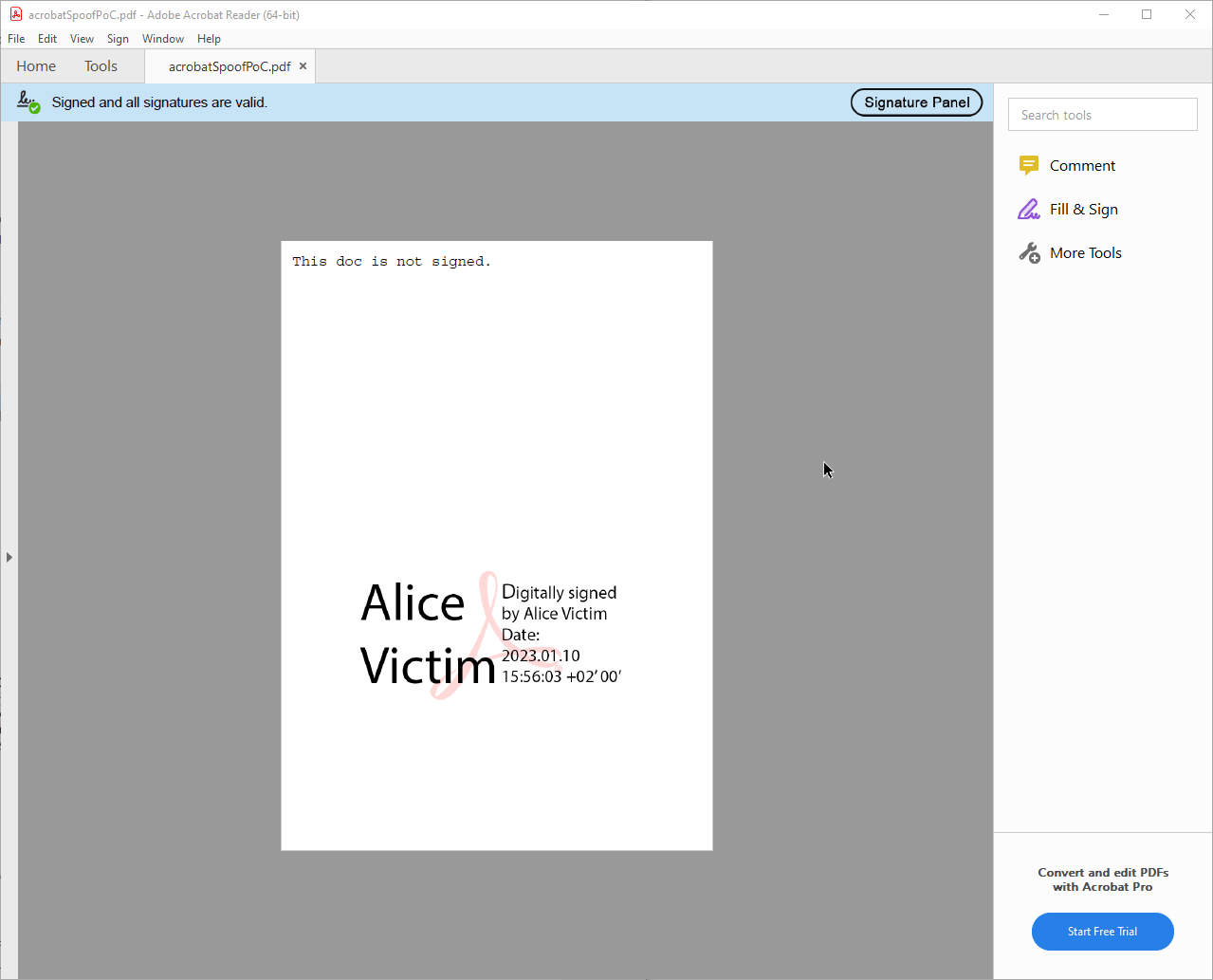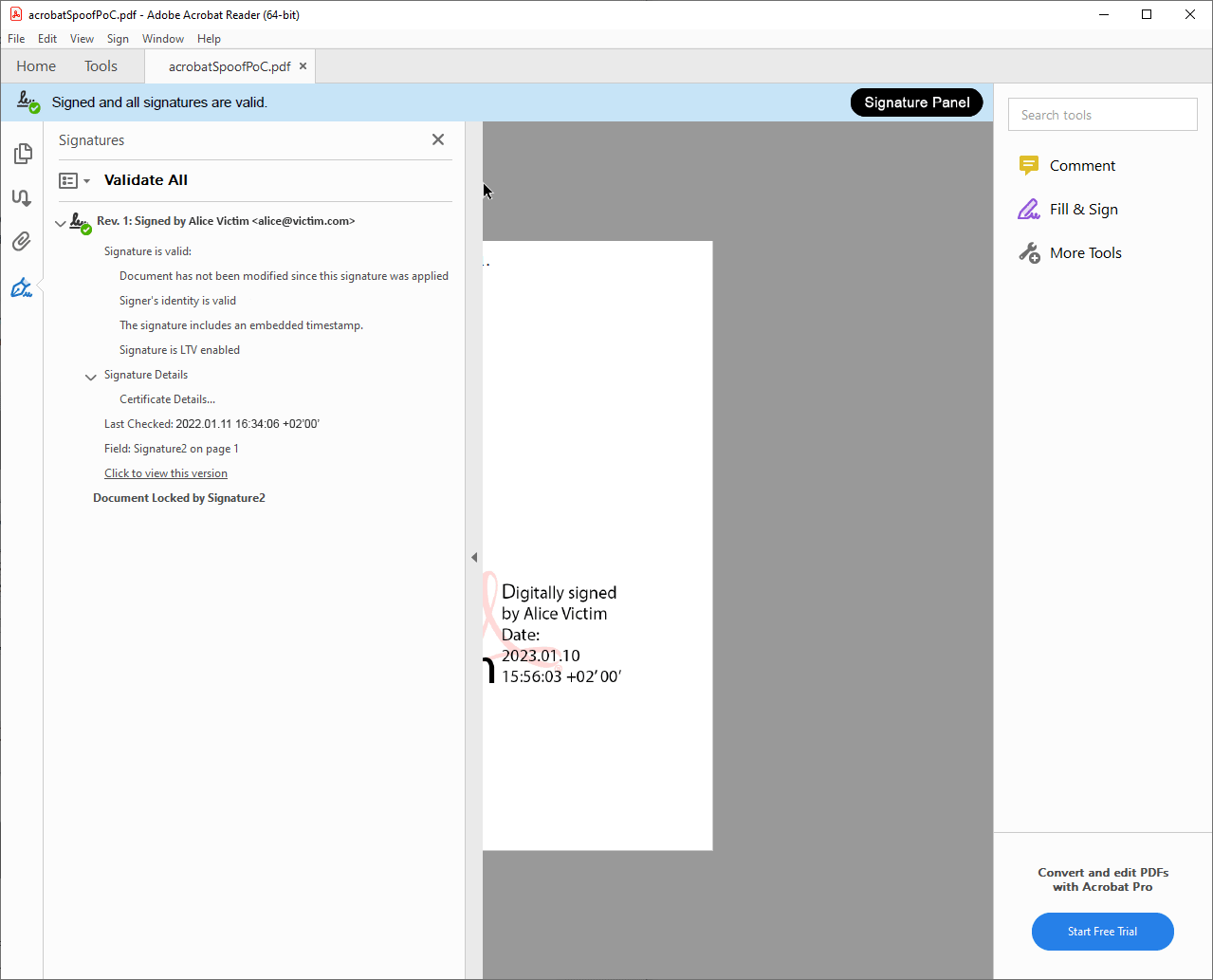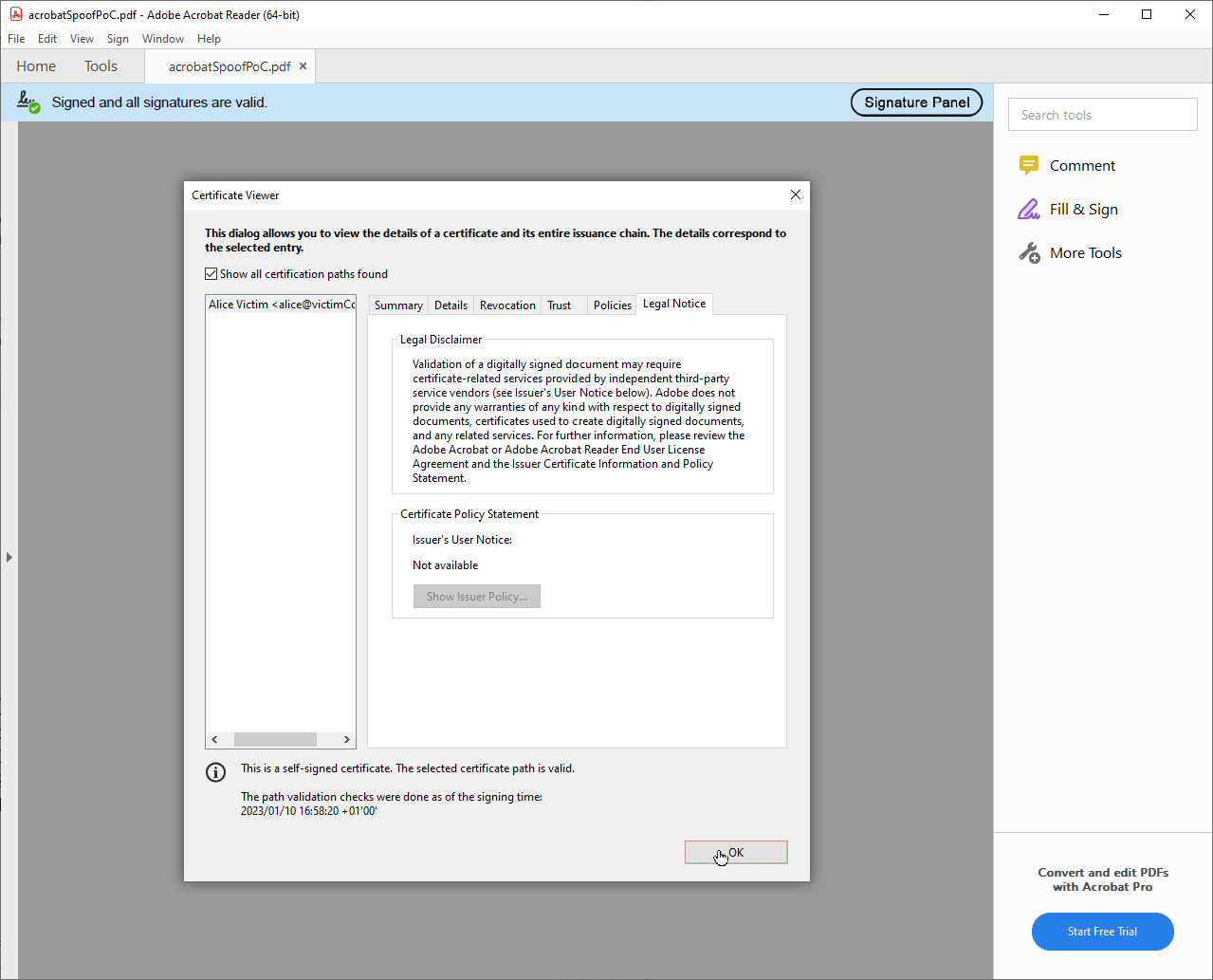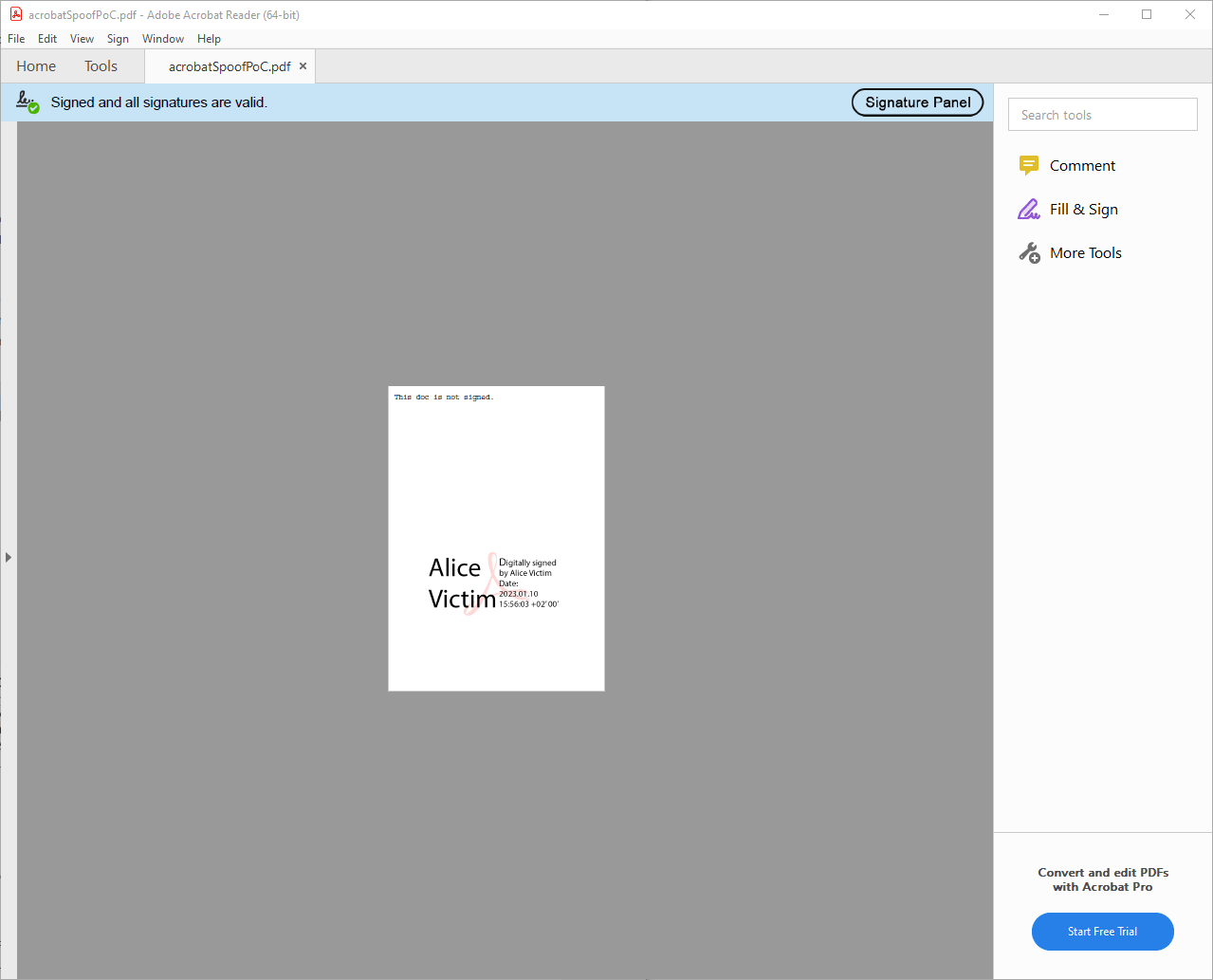
Furthermore, we assume that the attacker Eve has the following capabilities when creating the spoof:
Eve cannot sign a PDF with a signature that is trusted by Bob.
Eve knows what Alice's signature visually looks like.
Eve knows basic information about the PDF application and OS that Bob uses.
The delivery method of the PDF is out of the scope of this research, so we assume that Eve can deliver the PDF to Bob without raising suspicion.
Results
We evaluated the feasibility of Visual Signature Spoofing by creating spoofs for three commonly used PDF applications:
Adobe Acrobat Reader DC
Foxit Reader
Okular
All PDFs were evaluated on Windows 10.
Due to the reliance on JavaScript, a convincing spoof could only be created for Adobe Acrobat Reader DC. The other evaluated PDF applications did not implement the necessary JavaScript functions to control the position of the widget annotations, so a convincing spoof for these was not possible. It is important to note that JavaScript is enabled by default in Acrobat Reader DC.
In Acrobat Reader DC, we were able to position the widget annotations that make up the spoofed signature indicator freely in the viewport. Furthermore, we could move the widget annotations to react when the user scrolls or zooms. We were also able to hide or show annotations to imitate the user opening other signature indicators, e.g., a window. Overall, we were able to convincingly spoof the signature graphic, signature bar, signature panel, and to a lesser extent, popup windows.
There is some remaining behavior which we were not able to spoof in any PDF application during this research, for example:
We were not able to retrieve information about the OS color scheme. This means that the color of the spoofed windows might not fit the real accent color. We therefore chose a neutral color like white for the windows.
We could not imitate the dragging of UI elements. This means that scrollbars are not functional, and that windows cannot be moved. As a remediation we suggest adding an error sound when the user tries to drag a UI element to imitate a problem in the application. This can be achieved with the JavaScript function "app.beep()".
All spoofed signature indicators react with significant lag to the user zooming or scrolling.
These limitations show that visual signature spoofing is unlikely to succeed under scrutiny. Additionally, the creation of a visual signature spoof is time consuming since it must be custom-made.
Still, visual signature spoofing might work in other attack scenarios, such as targeted social engineering attacks (e.g., CEO fraud). The spoof is much more convincing when the attacker is in control of the PDF application, and merely shows it to the victim without letting them interact with it. For example, an attacker might show the receptionist a contract “signed” by the CEO, to gain entry to the facility.
Conclusion
Visual Signature Spoofing was partially successful in forging signed documents.
Due to the limited support of JavaScript in the other PDF applications, it was only possible to create visual signature spoofs for Adobe Acrobat Reader DC. Other PDF applications may also become vulnerable in the future if they add support for the necessary JavaScript functions. Manufacturers of PDF applications should always consider that adding more functionality also gives a malicious actor more tools in attacking users.
Additionally, PDF applications should clearly separate the PDF content from the applications UI elements, especially if they are security relevant. For example, the signature bar could be moved to the top of the application, so that spoofing the signature bar would require a spoof of all the other UI elements between it and the viewport.
The easiest way to detect visual signature spoofing is to view the PDF with JavaScript disabled in the application settings. The spoofed signature indicators can no longer track user interactions and will not react properly. This exposes the spoof. Furthermore, users can look out for suspicious behavior, like increased lag, not draggable UI elements, or unusual visual contrasts. Finally, users may open a PDF in different PDF reader applications.
We attempted to contact the affected vendor Adobe through their PSIRT multiple times since mid February 2023, but never received a response.
Try it Yourself
The best way to get a feel for visual signature spoofing is to interact with it yourself. We provide a proof-of-concept spoof for Adobe Acrobat Reader DC. The spoof was tested in Adobe Acrobat Reader DC, version 2022.003.20314, on Windows 10 set to light mode. Please also make sure that JavaScript was not disabled in the application settings.
You can download the proof-of-concept here.
This research was conducted by Tobias Friese during his bachelor thesis.
In 2021, he joined SEC Consult as an intern, and continued working as an associate security consultant.
The blogpost was edited and published with the help of the SEC Consult Vulnerability Lab.

