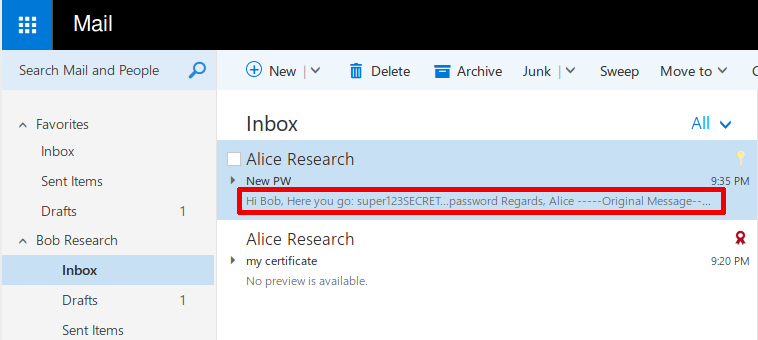
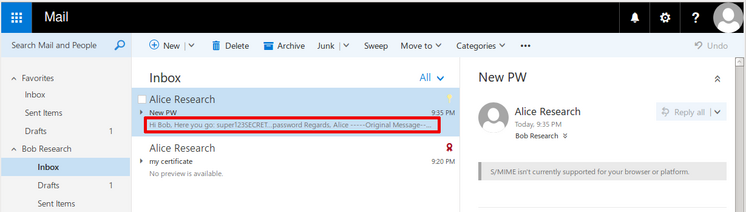
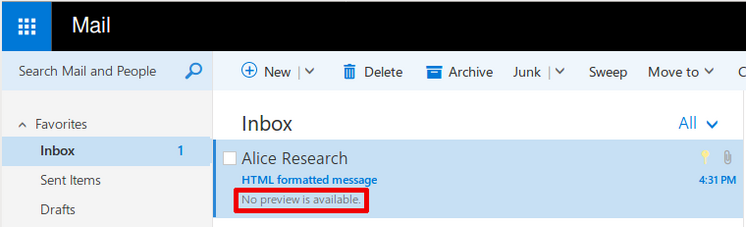
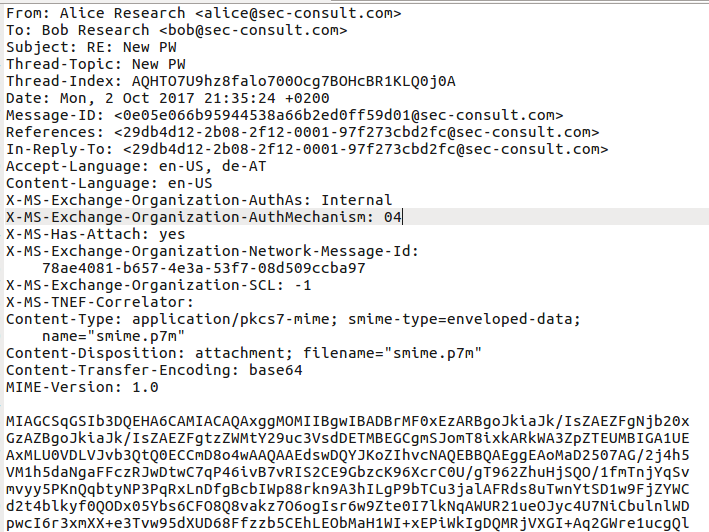
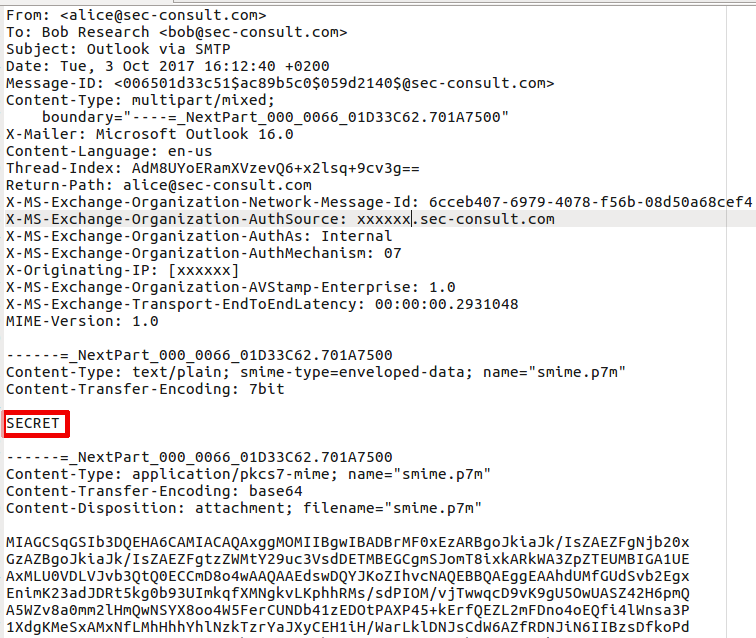
This has been a rather unusual vulnerability discovery. Unlike other cases we kind of stumbled upon the first indications of this vulnerability by pure coincidence (we did not search for Outlook vulnerabilities). We knew something was seriously wrong when we noticed that the contents of S/MIME encrypted mails were shown in Outlook Web Access (OWA).
The Basics: S/MIME
S/MIME is an IETF standard for end-to-end encryption and signing of mails. Most popular mail clients, including Microsoft Outlook, Mozilla Thunderbird, Apple Mail, and the Mail Clients on Apple iOS and Samsung Knox devices, support S/MIME. Along with similar technologies like PGP/GPG, it is used by security/privacy conscious individuals and organizations to protect the mail communication. To use S/MIME the mail client has to be configured, this includes installing a personal certificate and exchanging certificates with communication partners.
In an environment where mail servers or network hops between sender and recipient are compromised, S/MIME will still protect the mail’s body against unauthorized access (confidentiality) and manipulation (integrity, authenticity).
The Vulnerability
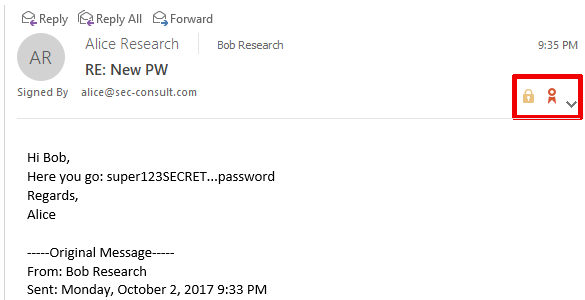
There is a bug in Outlook that causes S/MIME encrypted mails to be send in encrypted and unencrypted form (within one single mail) to your mail server (and the recipient’s mail server and client and any intermediate mail servers). The impact is that a supposedly S/MIME encrypted mail can be read without the private keys of the recipient. This results in total loss of security properties provided by S/MIME encryption.
In the sender’s “Sent Items” folder, there is no indication of the problem whatsoever. The message is displayed in Outlook as if it was properly encrypted.
To trigger the vulnerability, no active involvement by an attacker is required. An attacker might remain completely passive.
Note: This vulnerability affects mails where Outlook is used as the sender and has no impact on incoming S/MIME encrypted mails – where Outlook acts as the recipient. This is about mail body S/MIME encryption not transport level security (TLS).
Affected Mails and Scope
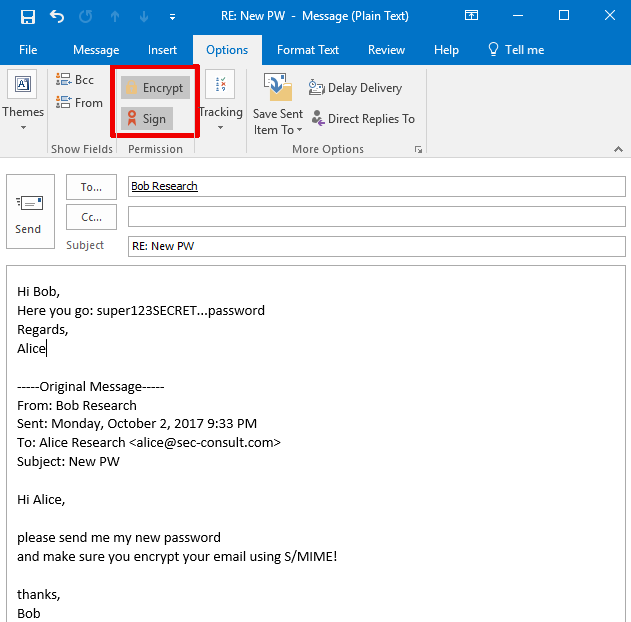
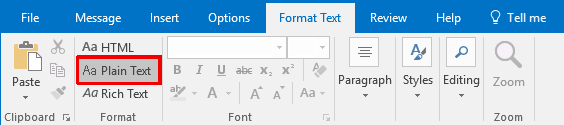
We observed this vulnerability only triggers with mails that are formatted in “Plain Text”. Microsoft confirmed this observation.
Speaking about “Plain Text” formatting in the context of encryption might be confusing, the screenshots below will clarify it. Outlook formats mails in “Plain Text” by default when replying to “Plain Text” formatted mails.
When composing a new mail “HTML” is the default format (unless the default has been changed). We did not observe any negative impact on attachments, Microsoft shares this observation.
The scope of this vulnerability differs depending on the used transport protocol:
a) Outlook with Exchange (impact limited to first hop)
The plaintext leaks one hop only (to the sender’s MTA) and to the recipients mailbox if the recipient and sender are in the same domain. When sending mails to external recipients Exchange seems to remove the plaintext part from the message.
b) Outlook using SMTP (impact on the entire mail path)
The plaintext leaks to all mailservers along the path and the recipient.
We do not have information regarding how the vulnerability manifests in Office 365, Outlook.com, etc.