Conclusio
As ASICs are very specific solutions, it is not very likely that someone would manage to reverse engineer such a part without having access to scientific equipment like electron microscopes, wet-etching and so on. The fact that big vendors manufacture a lot of PCBs for their engineers and production, constitutes a potentially weak channel as information can be leaked. In some cases, these parts are even thrown away without further consideration or are sold to a local retailer. For these PLCs, PCBs with debug ports sometimes even end up in an online-shop on the Internet.
A week prior to the publication of this blogpost the following statement from Siemens reached us: The boards purchased by SEC Consult were not development boards but previously used or refurbished boards from Siemens devices. Siemens does not see a supply chain leak. Since the PLCs were apparently used in an older series of PLCs, our initial assumption of a supply-chain leak does not hold.
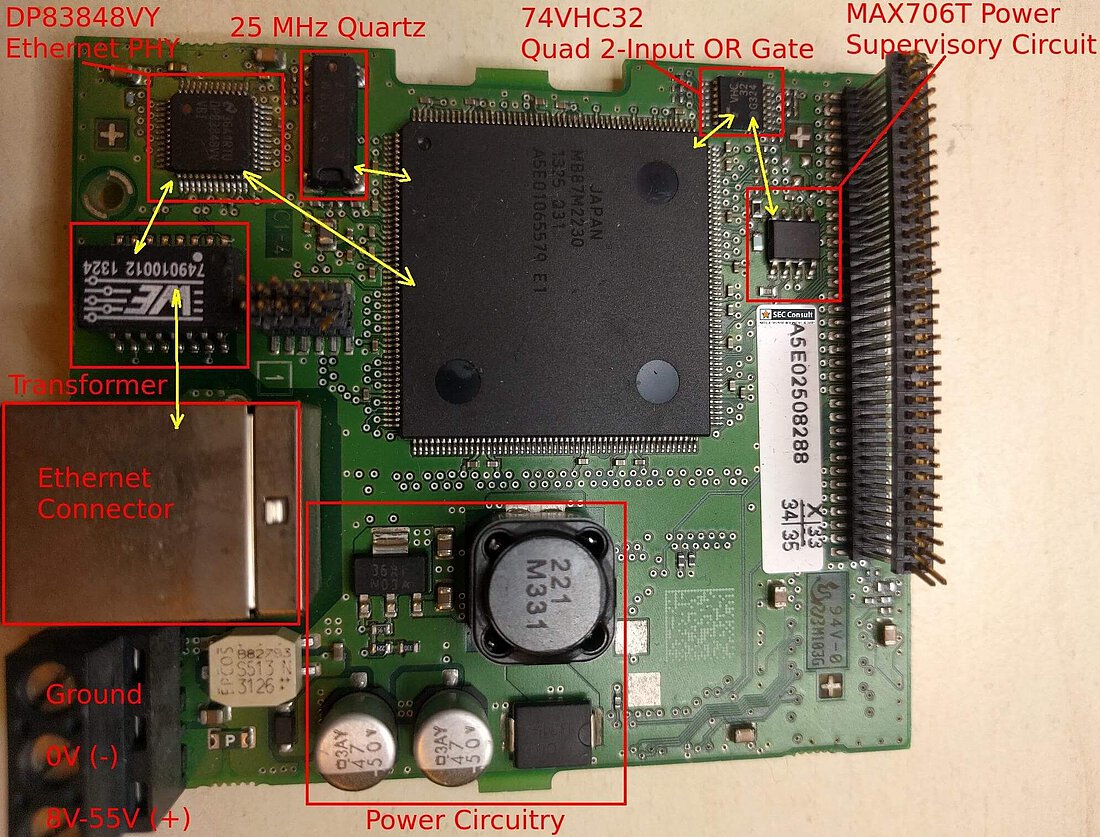
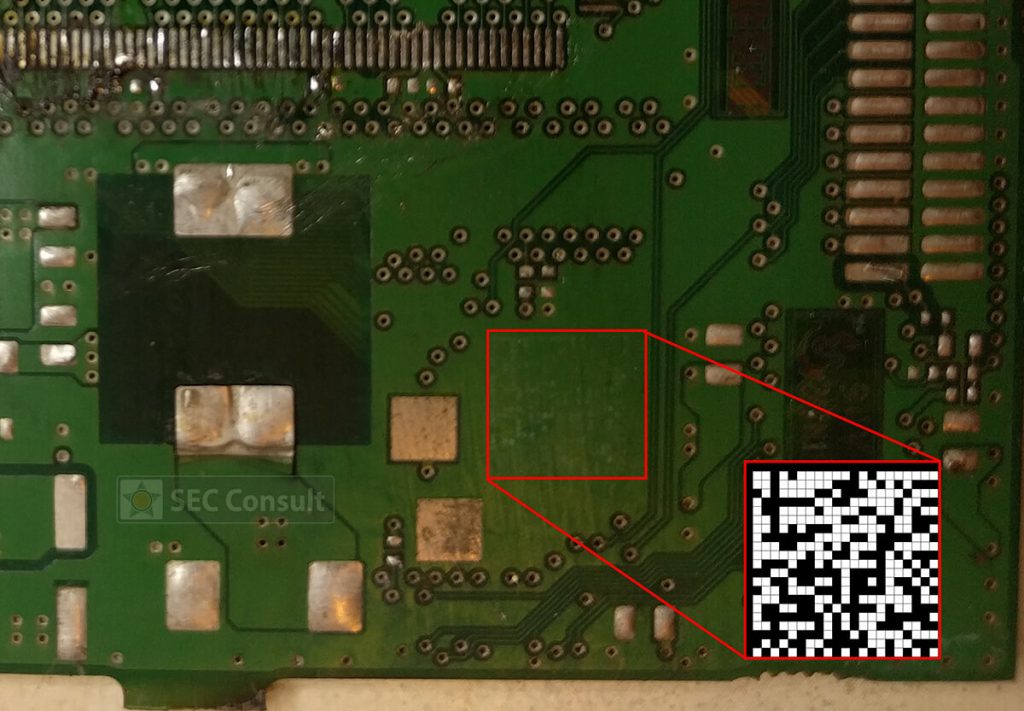
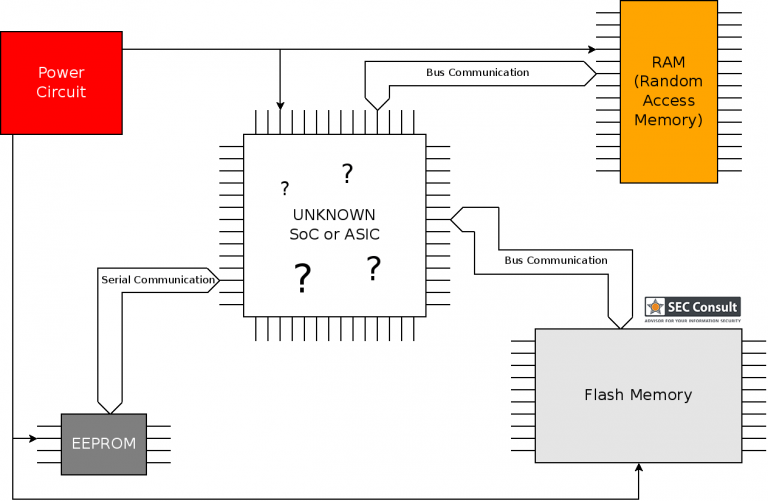
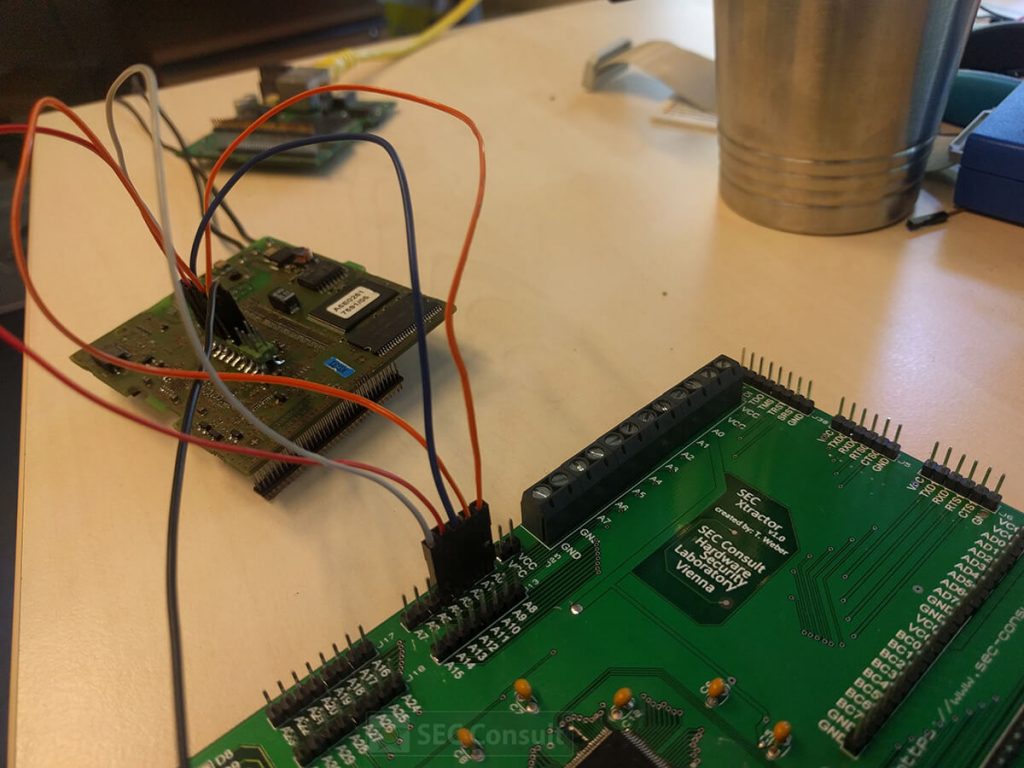
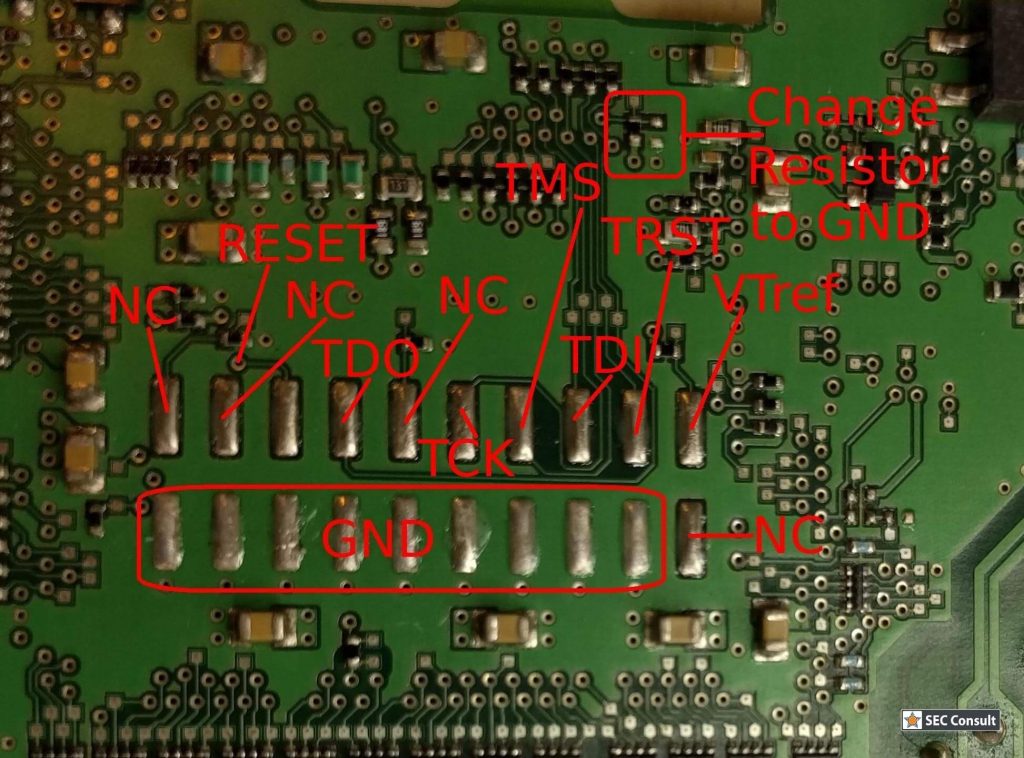
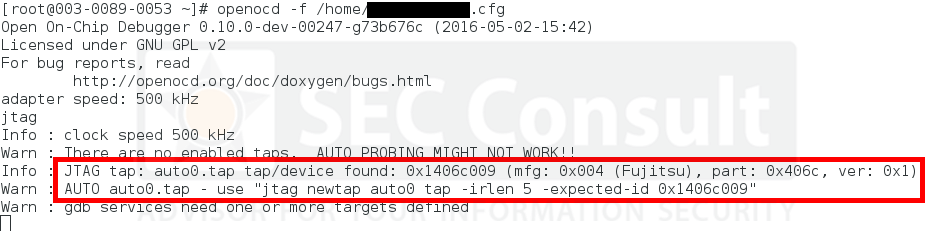
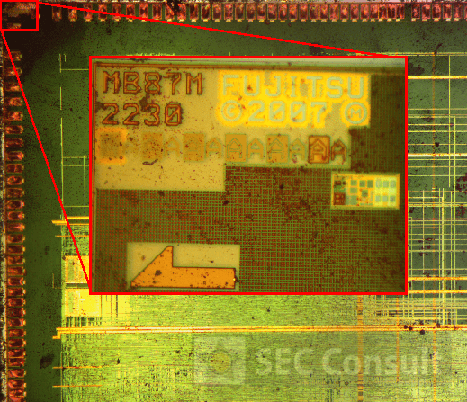
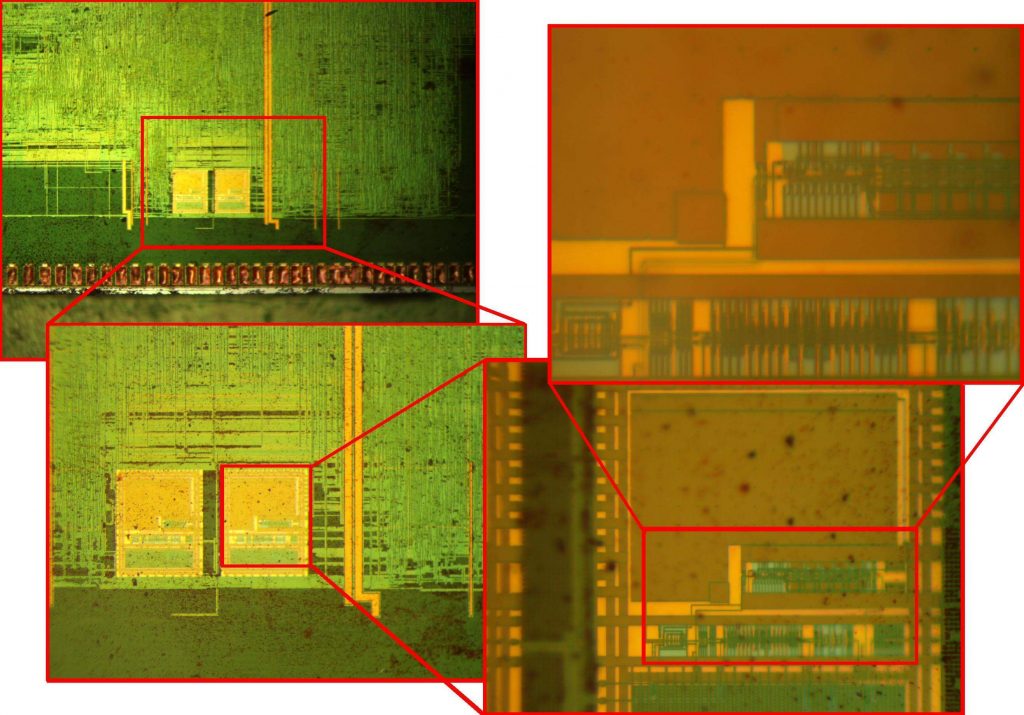
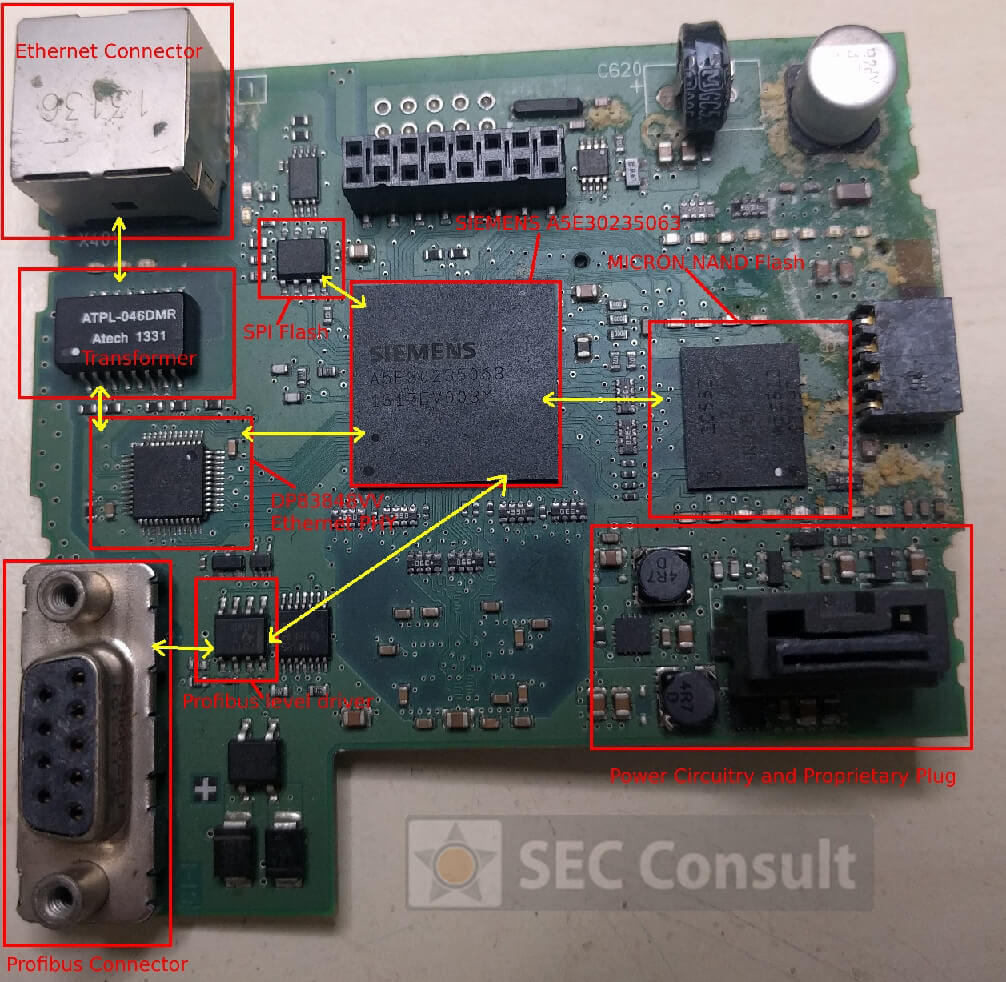
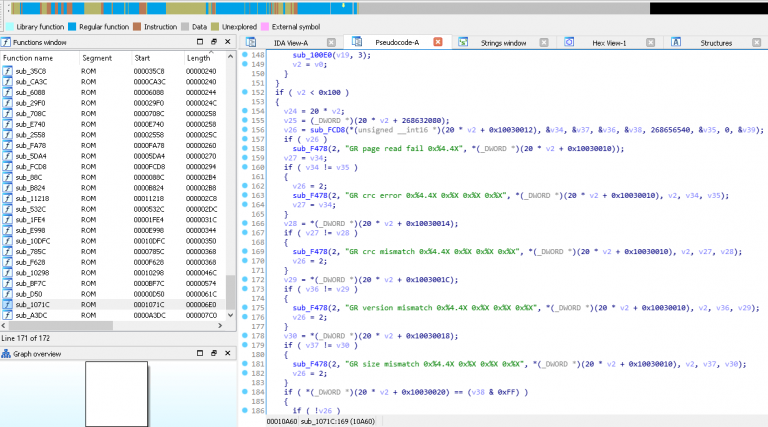
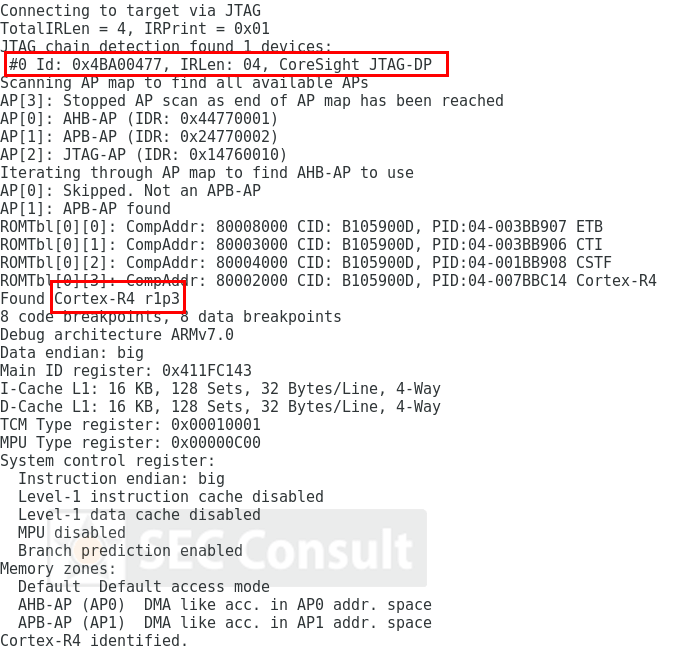
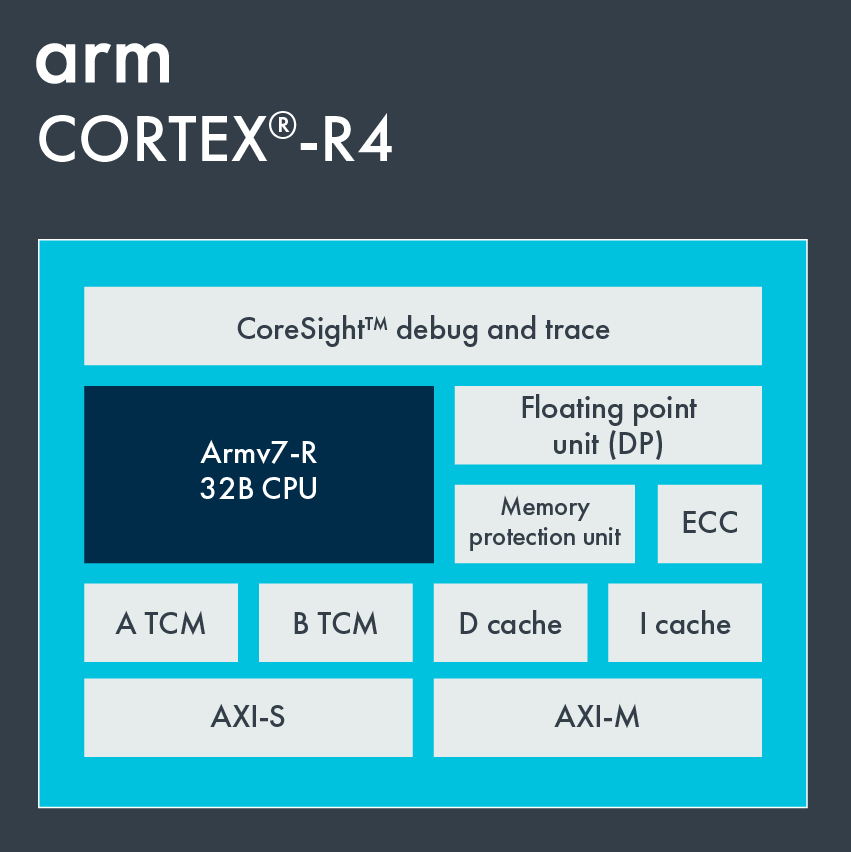
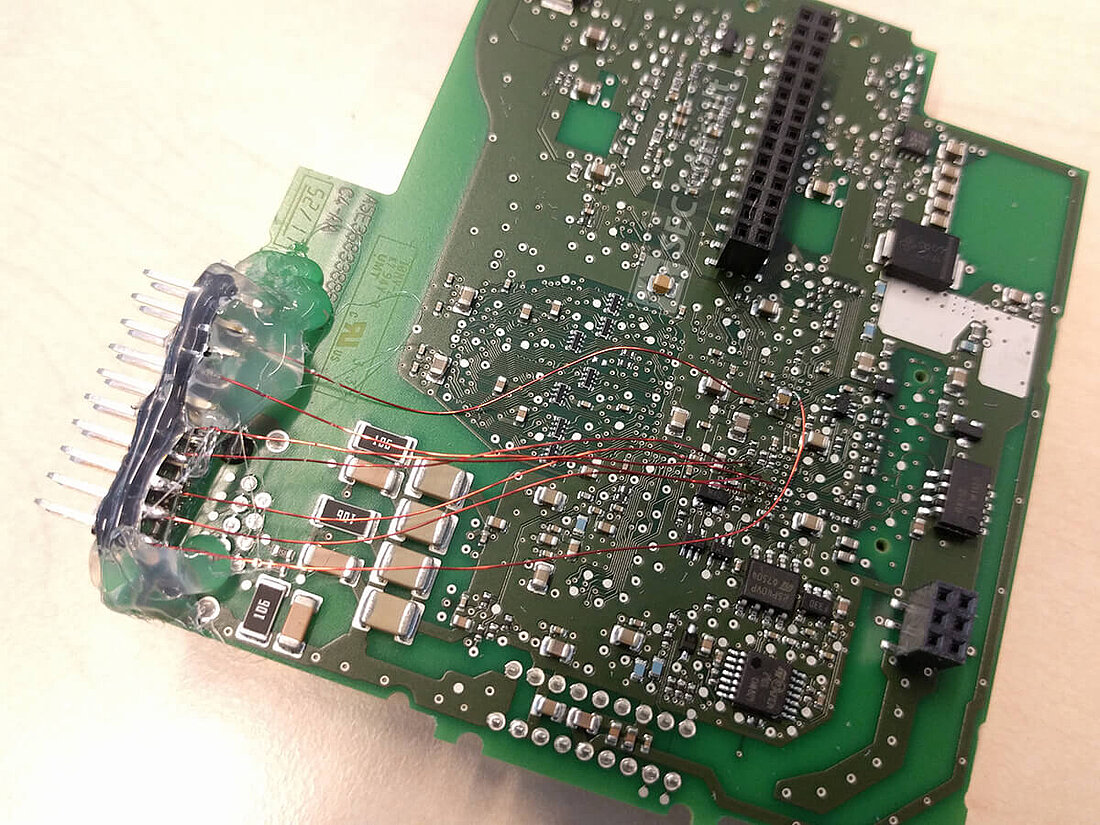
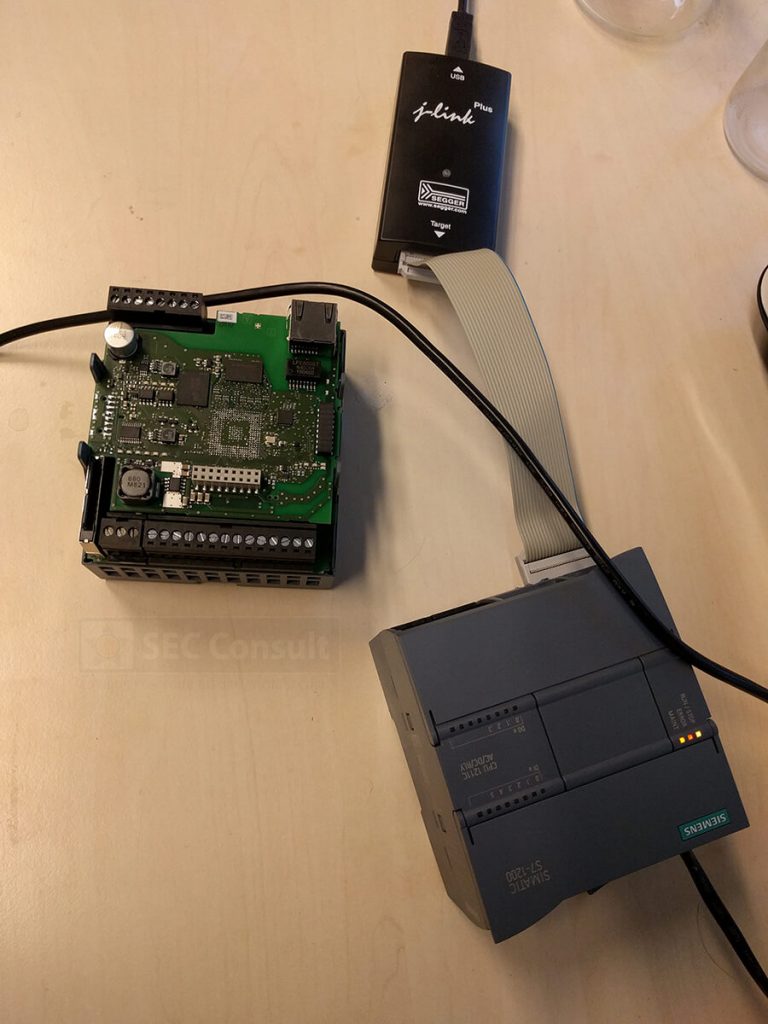
However, with few considerations and a structured approach it was indeed possible to reverse-engineer such boards. Finding out the debug-port of a custom chip was the first hurdle to overcome in order to debug and reprogram a chip. It became clear that one would gain full control over the device, in the end.
This means for the potential attackers:
- Hardware backdoors could be installed on the PCB of the Siemens PLC.
- All application programs on the PLC could be modified during run-time.
- A PLC-persistent malware could be designed.
- Since the NAND flash of the S7-1200v4 is write-able, it could be possible to place a backdoor in the firmware at this memory segment without leaving any trace (more complicated but invisible).
As attackers with such capabilities tend not to disclose such details, we assume that they might have known them for a while and there is the possibility that such PLCs could carry backdoors.
Better news for the security analysts:
- A security researcher which has access to the pinout is able to search for firmware vulnerabilities on these devices.
- Memory forensics, searching for backdoors, malware and other changes in the code of this PLC are possible too.
- Hardware backdoors are more easily detectable as they will be connected to all of the pins which are used to debug the PLC.
In contrast to Bloomberg’s article “The Big Hack” which describes an IC of the size of an RF balun (RF conditioner), a general backdoor at that level will be hidden in firmware or a small hardware module (as big as a coin) at least. It is easier to hide such sophisticated chips in packages of other chips or even between the PCB layers instead of giving them a separate package.
This research was done by Thomas Weber on behalf of SEC Consult Vulnerability Lab