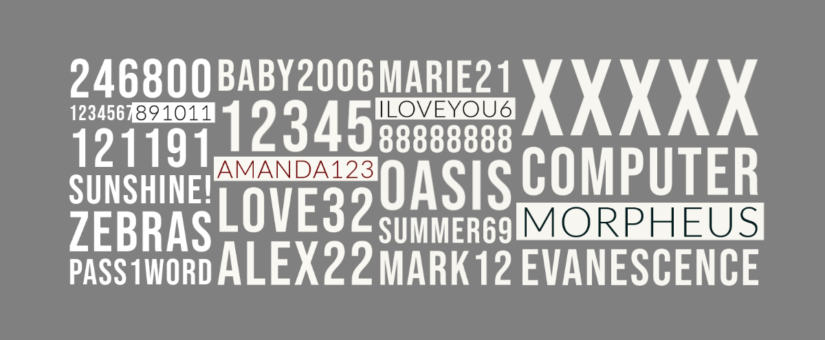Essentially identity protection by password is a failing concept as passwords get re-used very often as more and more services require user identification – even for newspapers! FIDO2 is a project by the FIDO Alliance and the World Wide Web Consortium (W3C) to substantially enhance the security of web application authentication. FIDO2 offers a comprehensive solution to this problem as it is
- more convenient: a single push of a button or a fingerprint read
- more secure: identity theft becomes a relic of the past and
- there is no need for a central identity provider (like Google, Facebook, etc) that the world has to trust.
Especially in times, where the need for working from home becomes essential for businesses around the globe more companies are using cloud-based services like Google Docs or Microsoft Office 365. In this case, Identity protection is highly relevant as there is no networking border (like firewalls or physical networks) that serves as an additional layer for data theft/manipulation in case of identity theft.
2-Factor Authentication (2FA) can help to keep companies to stay secure, with 2FA it is harder for an attacker to steal accounts, even if the attacker knows the password. Still, some 2FA solutions like the typical mobile Authenticator apps (or Tokens) which usually implement TOTP are still vulnerable to phishing.
In contrast to that FIDO2 gives companies and users a highly secure option for a passwordless login or 2FA – both have very few realistic attack vectors. One would be stealing a physical device or compromising the security of the client – but as a decent security advisor, we would also like to mention other attack options. FIDO2 is also a quite cost-effective solution as most mobile phones (all Android 7 and Apple mobiles) as well as all modern Windows PCs (TPM ready) or OSX PCs come already with integrated FIDO2 capabilities; USB FIDO2 keys are on the market for as little as €10.
The following guide gives administrators and users the required settings to enable FIDO2 protection – but is by far no complete FIDO2 Explanation.
1.1. Microsoft/Ad Account Protection
With the public preview of Azure AD, FIDO2 security keys can now be used to enhance the security of AD accounts. FIDO2 Keys can be used for passwordless login or in combination with 2FA (called Multi-Factor Authentication – MFA – in this context) it brings user authentication into Microsoft services to new heights. Meanwhile, it is easy to configure for admins as well as the end-user.
The FIDO2 and MFA are easy to configure and supports Azure AD as well as Hybrid-joined AD accounts.
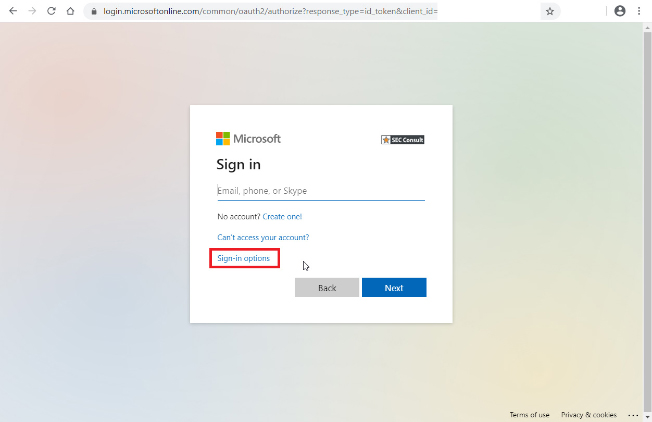
To enable FIDO2 Keys support and enhance the security with MFA the following steps are needed.
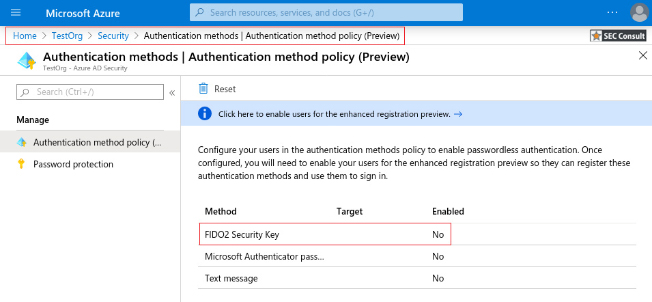
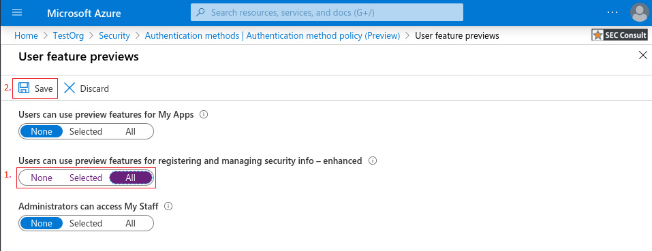
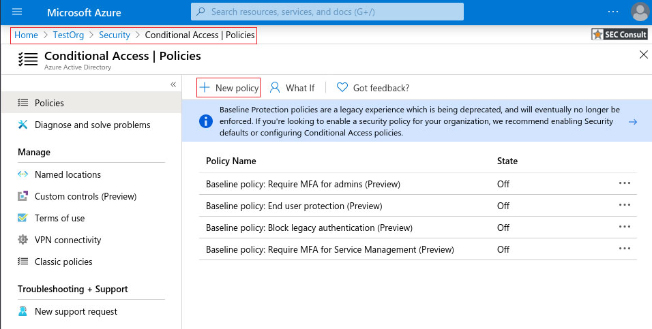
2. Browse to Azure Active Directory > Security > Authentication methods.
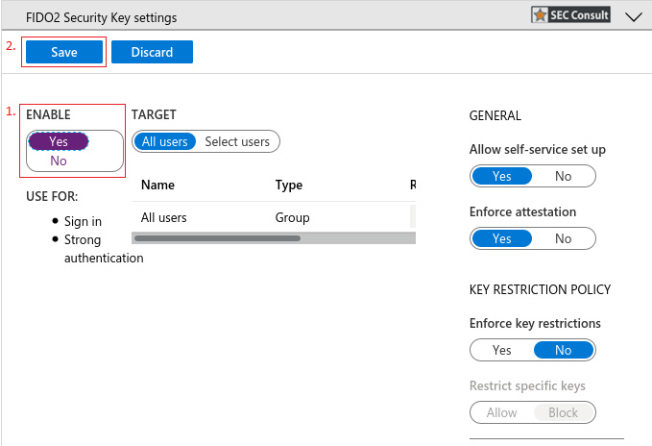
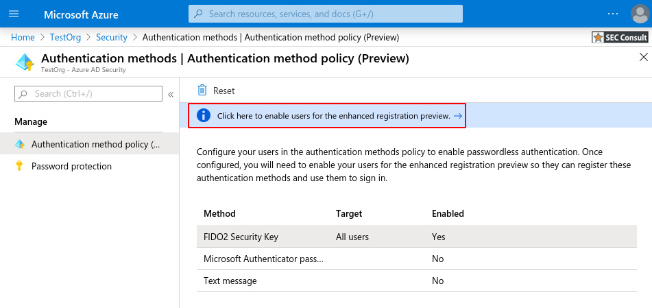
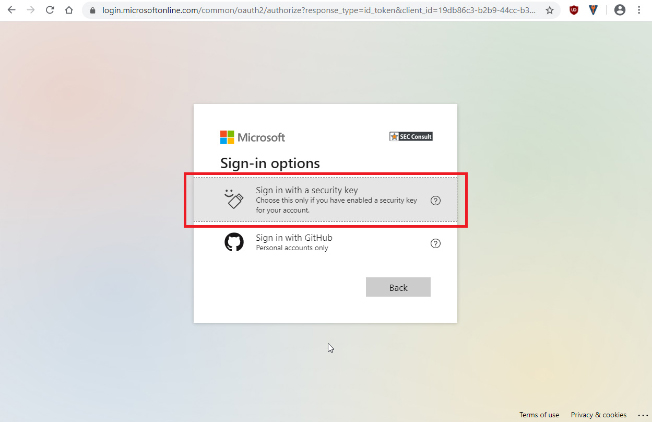
3. Select “FIDO2 Security Key”
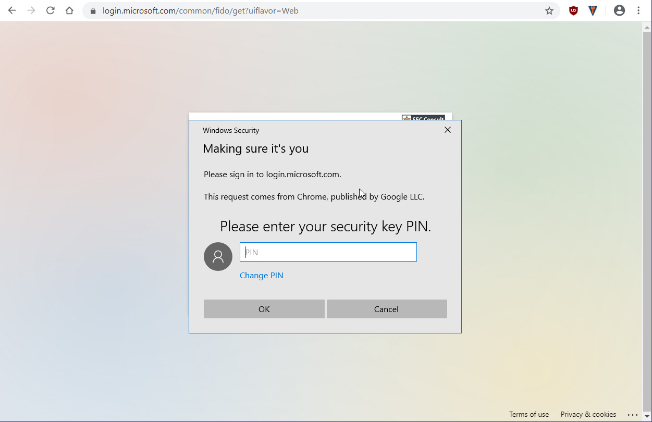
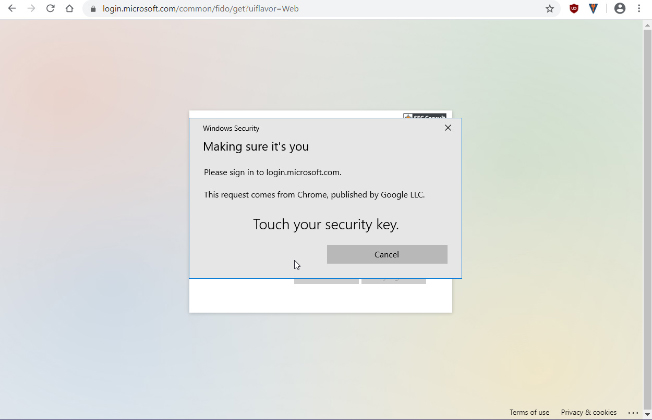
3. Enter PIN of key (or use fingerprint/camera for other tokens) – this is called “user verification” in the FIDO domain
4. Touch your Key (user presence verification)
5. You are logged in – Please note you never entered a password or even a username!
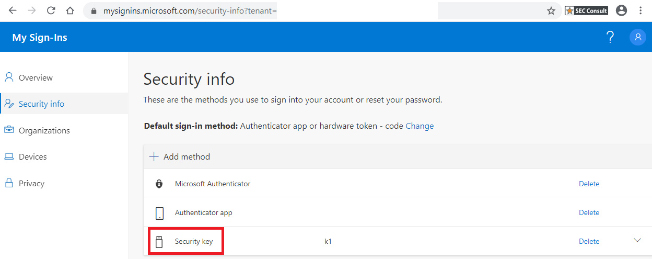
6. You can add further authenticators or keys.
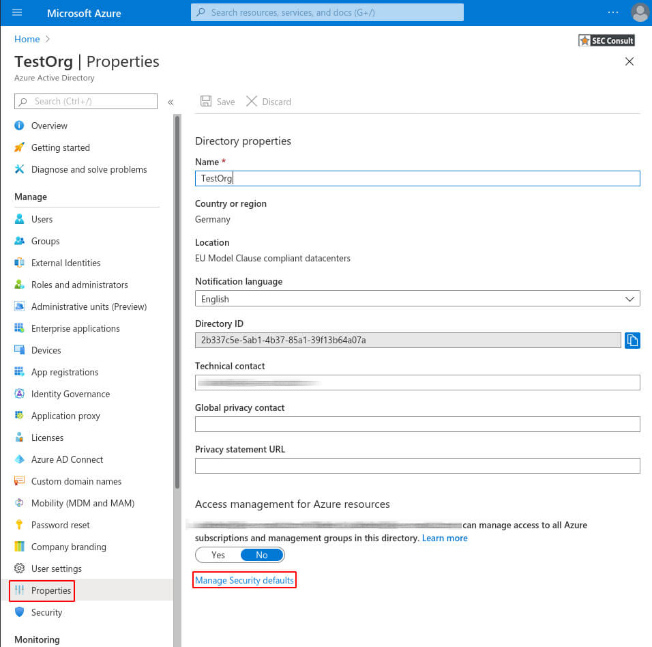
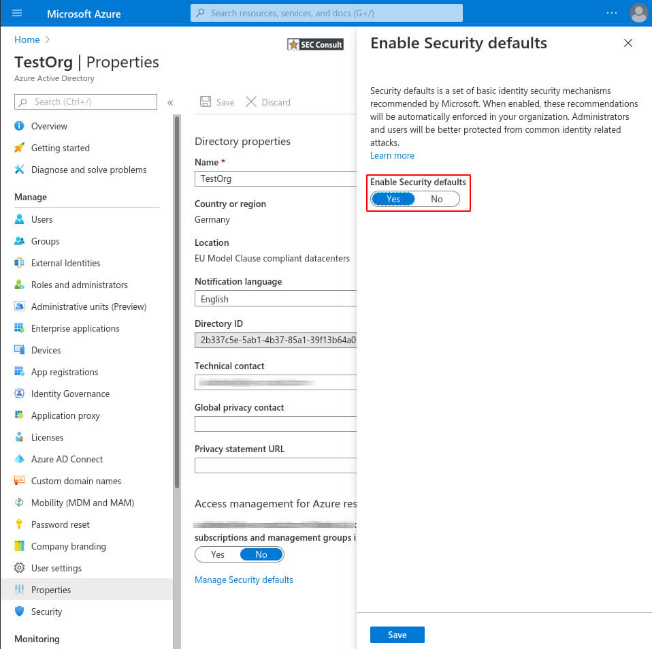
3. Enable the Security defaults and save the changes
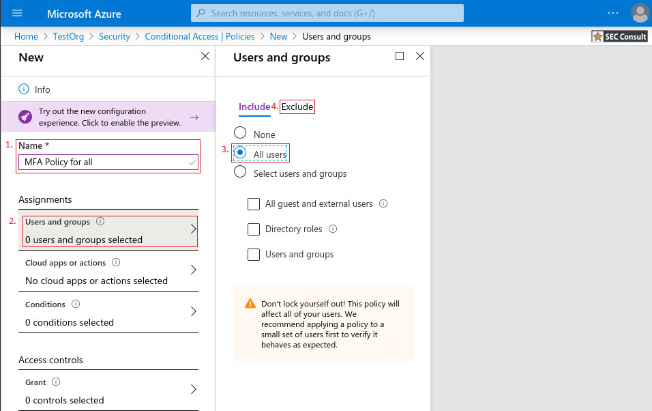
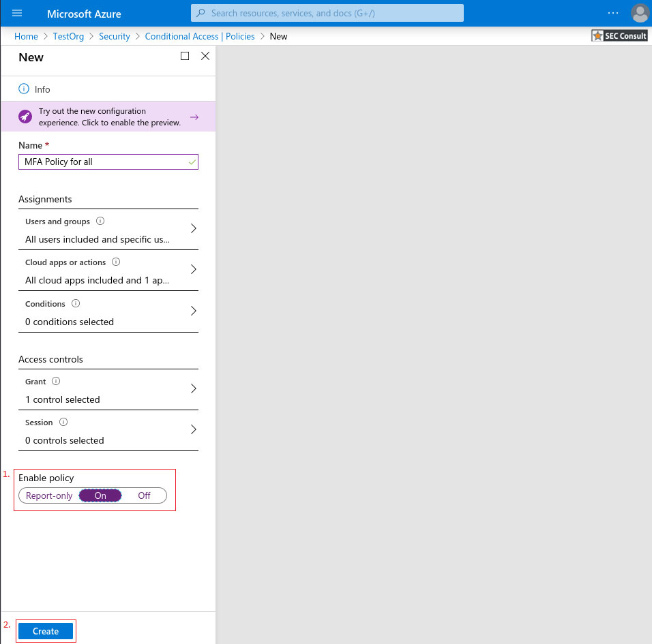
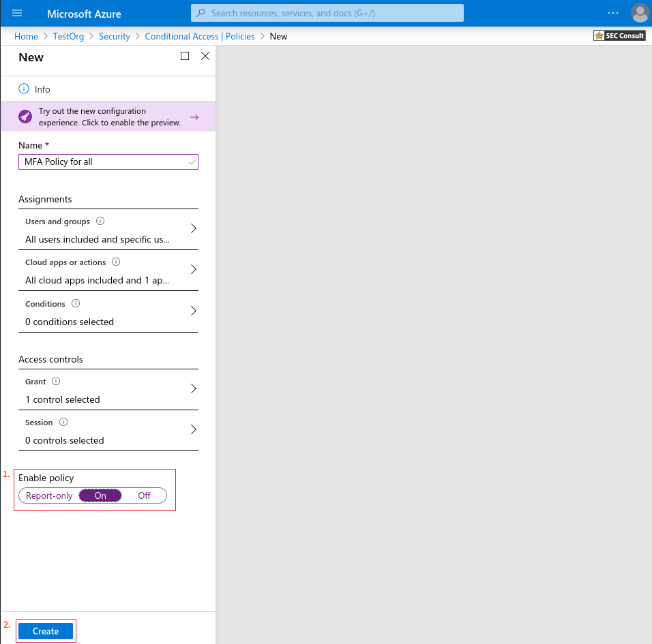
3. Give your policy a meaningful name.
a. Under Assignments, select Users and groups
b. Under Include, select All users
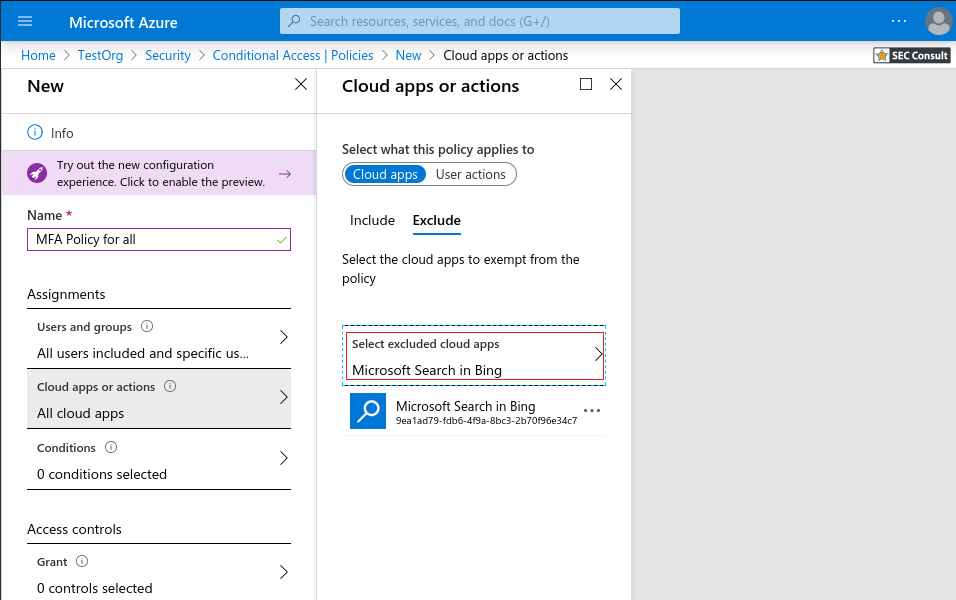
5. Under Cloud apps or actions > Include, select All cloud apps
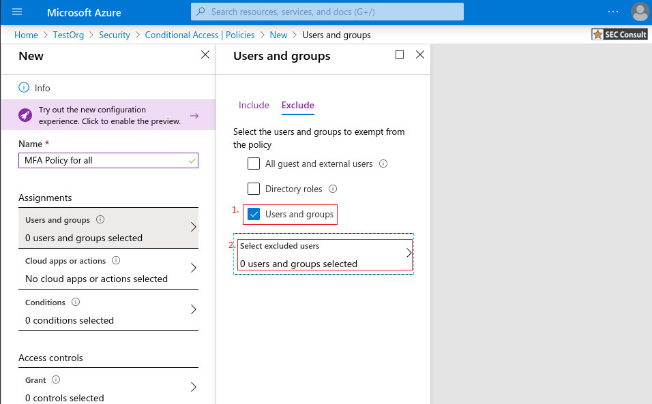
a. Under Exclude, select any applications that do not require multi-factor authentication.
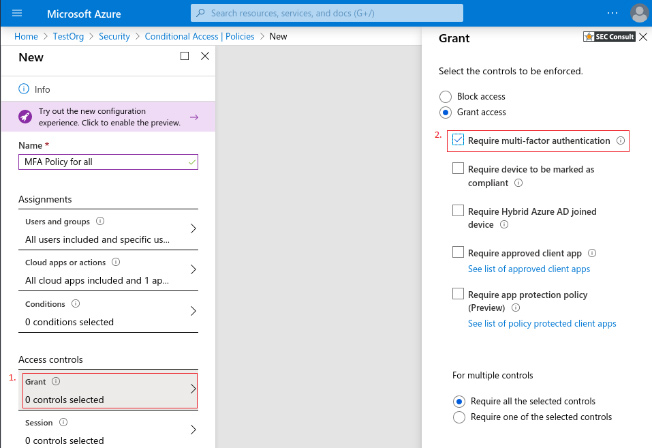
6. Under Access controls > Grant, select Grant access, Require multi-factor authentication, and choose Select
MFA Licensing – https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-licensing
Security Defaults – https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults
Conditional Access: Require MFA for all users – https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-all-users-mfa
Setting up the required Microsoft Azure configuration options to get FIDO2 based two factor authentications (2FA) up and running is only one of many ways to increase your IT security. If you are interested in web application penetration testing in general, you might also like the this article about pen testing an its benefits: Pentesting: Benefits, Legal Compliance and Costs.