IoT and Embedded Systems Security
SEC Consult offers a full spectrum of security assessments, be it hardware, firmware, apps or IoT cloud platforms. Our experienced experts check all sorts of IoT devices as well as IoT ecosystems and embedded systems for vulnerabilities and security gaps.
Detecting vulnerabilities before they are exploited
Dedicated Hardware Labs
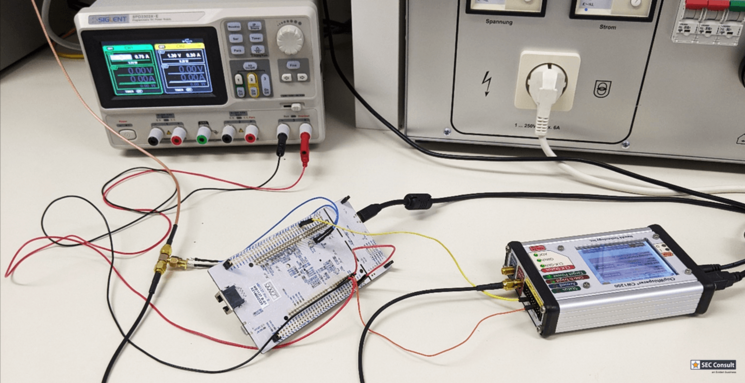
IoT devices and ecosystems carry security risks on several levels – hardware, firmware, network and cloud security, applications… SEC Consult operates dedicated laboratories with advanced technical capabilities to conduct hardware reverse engineering and security analysis. Our security experts can use this environment to reverse engineer hardware, find interfaces (UART, JTAG, I2C, etc.) and exploit hardware vulnerabilities.
Security for Systems in all Shapes and Sizes
Our assessments cover all kinds of IoT devices and embedded systems ranging from automotive, aviation, industrial control systems (ICS/SCADA), medical devices, enterprise systems, telco equipment (e.g. CPEs), consumer electronics, banking (e.g. ATM, POS), physical security, access control, surveillance – whatever it may be, SEC Consult meets your needs.
Years of Experience
SEC Consult experts offer their advanced knowledge in IoT security as well as a strong background in electrical engineering and hardware and software engineering. Time and again our in-house research leads to the publication of advisories and presentations at the industry’s leading conferences like for example BlackHat, Hack in the Box, Chaos Communication Congress, and more.
Devices, Cloud, Apps, APIs, and more!
We offer a full spectrum of security assessments and not only test devices but also whole IoT ecosystem. You can count on the experience of our experts in screening constrained devices (e.g. non-TCP devices operating via Bluetooth, ZigBee, etc.), gateways, devices and cloud APIs, mobile apps, etc.
Compliance
SEC Consult ensures compliance with industry standards and follows a custom-tailored approach, whether you are a service provider, device vendor or corporate end user. So you will be able to provide secure products and services to your clients.

IoT and Embedded System Security Assessments help you…
- protecting your network,
- building a secure IoT ecosystem,
- ensuring compliance with industry standards,
- enabling fact-based decision making.
IoT and Embedded System Security by SEC Consult
IoT and Embedded System Security by SEC Consult reveals vulnerabilities before they are exploited. Our assessment levels range from customers who want to get a first overview over their IoT/embedded system security up to customers with an already high maturity level. Our specialists conduct highly sophisticated attacks using manual methods and offer state-of-the-art hardening recommendations for you in accordance with the maturity level of your systems.
IoT devices are used in all kinds of companies in all kinds of shapes or forms. Vulnerabilities in those devices are constantly exploited by attackers to access confidential data, inject dormant malware or gain access to networks. Assessing IoT Security in time will help you to protect your IoT ecosystem and prevent you unintentionally adding vulnerabilities.
SEC Consult experts have a long-standing experience in assessing the compliance of IoT devices with industry standards. They know all about ETSI EN 303 645, ENISA Baseline Security Recommendations for IoT, NISTIR 8259 IEC 62443 or OWASP TOP 10 IoT 2018 and enable you to provide secure products and services for your clients.
Are you a service provider, device vendor or corporate end user? Regardless of your role, our specialists enable you to make educated choices on new IoT purchases by measuring the risk connected to IoT related services.
Working Hand in Hand
In ideal circumstances these both assessments work hand in hand:
Hardware Security Assessment (“Hardware Hacking”)
- Our specialists try to compromise the hardware of IoT devices with an attacker’s mindset.
- The approach involves identification of hardware parts, interfaces, and identification of vulnerabilities using hardware reverse engineering techniques in a lab environment.
- This so called “hardware hacking”enables debugging of firmware at runtime and lays the groundwork for in depth firmware and application security exploitation and binary exploitation.
Firmware/Application Security Assessment
- In this case SEC Consult experts also act with an attacker’s mindset. Here they attempt to compromise the firmware and/or software of IoT devices.
- The strategy involves identification of network services, analyzing the firmware security and identification of vulnerabilities while using web and binary exploitation as well as software reverse engineering techniques.
- Therefore our specialists can identify vulnerabilities in the device OS, web interfaces and other interfaces.
Supported by Automation
- SEC Consult works with experienced partners in IoT projects.
- Our specialists can provide a quick overview of your security posture because typical vulnerabilities can easily be detected.
- As our client you benefit from a scalable solution for automated analysis of the firmware of embedded devices.