Description
The web interface of Honeywell MB-Secure was prone to command injection in the ping interface. By abusig the IP address field or the interface field a command could be injected since the parameters were not filtered.
Vendor description
"The MB-Secure is a high level security solution that offers more than just security for buildings. Thanks to its Touch & Go function, many building functions can be managed easily. [...] Our MB Secure alarm control panels set a new standard. It provides all the power, capacity and versatility needed to meet virtually any installation requirement from a single platform. [...] MB-Secure combines hardware, firmware, licensing and future security in one platform. Forward-looking technology allows the configuration to be tailored to just a few users or large integrated systems."
Source: https://www.security.honeywell.de/en/news/mb-secure/
Business recommendation
The vendor provides a patch which should be installed immediately. SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
1) Authenticated Command Injection (CVE-2025-2605) The MB-Secure device provides a web interface for configuration which is enabled by default.
An authenticated attacker in the web GUI is able to execute any OS command by abusing the ping functionality at /si/ping. Roles which don't show the ping interface in the GUI can still reach and exploit this interface by directly opening the URL.
By putting a semicolon and the desired command followed by another semicolon into the interface field and pressing the "Ping" button, the command gets executed on OS level. The OS commands are executed with the permissions of the "root" user hence an attacker can completely compromise the device.
Proof of concept:
1) Authenticated Command Injection (CVE-2025-2605)
The affected lua file implements the ping function and executes it directly in the OS via the popen command without filtering or sanitizing the arguments.
Excerpt from nginx/lua/test/conf_panel_services.lua:
[...]
elseif ngx.var.arg_cmd == "ping" then
local host = ngx.var.arg_host
local intf = ngx.var.arg_interface or "eth0"
local wait = ngx.var.arg_wait or 1
local pingCnt = ngx.var.arg_count or 3
local repeations = ngx.var.arg_repeations or 3
local cmd
local response
if not host then
response = "No host"
else
cmd = "ping -W "..wait.." -c "..repeations.." -I "..intf.." "..host
Excerpt from linuxCommand(cmd, ms, cb) function:
[...]
local handler = io.popen(cmd)
[...]
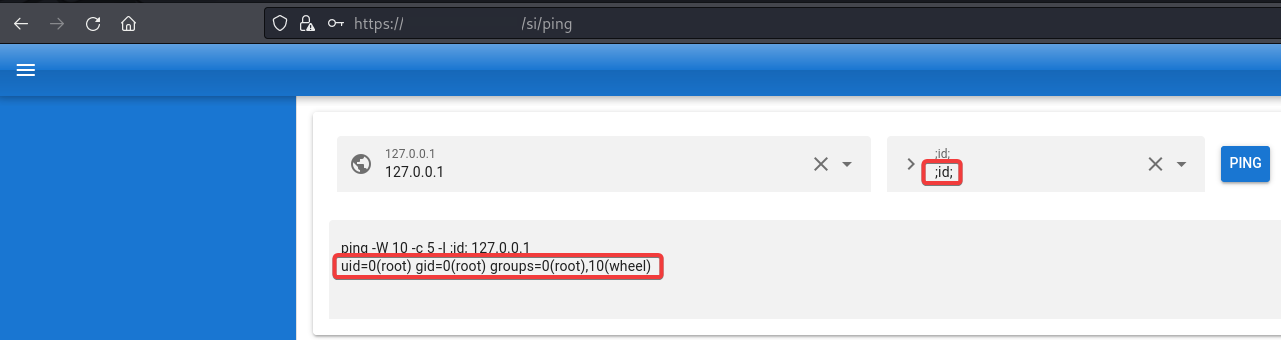
This allows an authenticated attacker to browse to the /si/ping path, insert the desired command together with semicolons to break up the ping command on OS level and execute the command.
The "id" command has been executed as a proof of concept and shows that the commands are executed with permissions of the "root" user, see figure 1:
Vulnerable / tested versions
Secure versions from V11.04 and prior to V12.53, MB-Secure PRO versions from V01.06 and prior to V03.09