Vendor description
"We are a global leader in office and production print technology and related solutions, with a large and growing presence in Digital and IT Services. Having redefined the workplace experience for more than 100 years, our differentiated business and technology offerings are empowering client success today by addressing the productivity challenges of a hybrid workplace and distributed workforce."
Source: investors.xerox.com
Business recommendation
SEC Consult recommends Xerox customers to install the latest updates and review the vendor's security note XRX24-015 for further information.
Also make sure to have patches from previous security notes installed, such as XRX23-020. SEC Consult has re-identified some critical 0-days (unauthenticated RCE, partial authentication bypass) that were already patched but not clearly communicated in the previous security notes.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
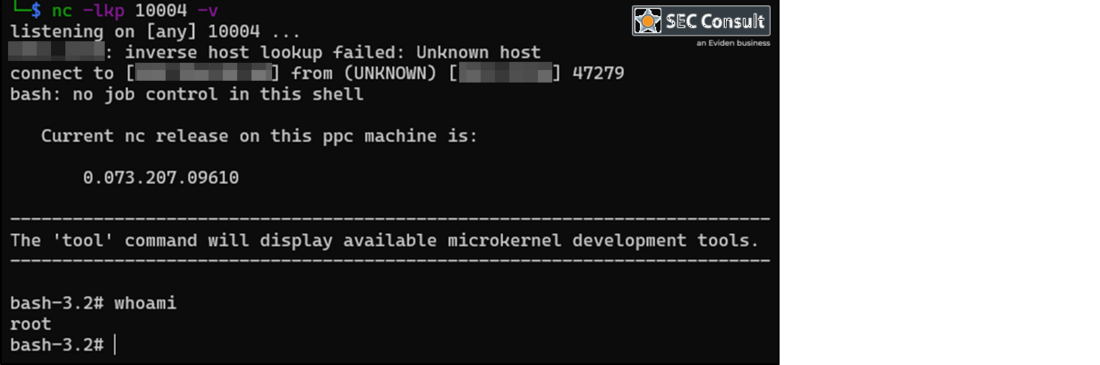
1) Authenticated Remote Code Execution (RCE) (CVE-2024-6333)
An attacker authenticated as a user with administrative access to the web interface of a range of affected Xerox printers can exploit a remote code execution vulnerability (RCE) as root user. It allows an attacker to execute commands directly on the operating system of the printer with root permissions. Consequently, the target Xerox printer can be fully compromised.
Proof of concept
1) Authenticated Remote Code Execution (RCE) (CVE-2024-6333)
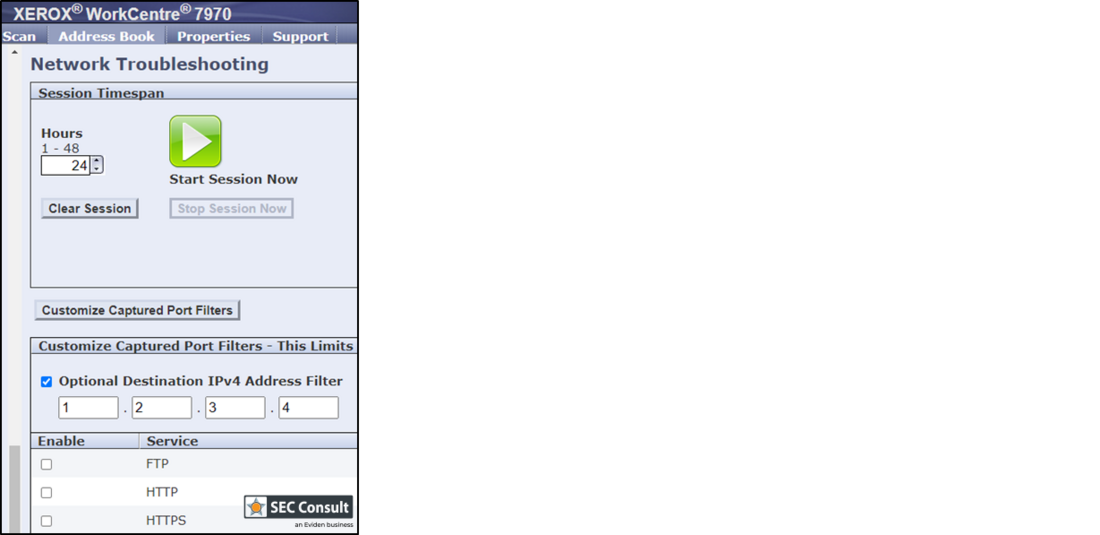
The "Network Troubleshooting" menu enables administrators to configure and run network troubleshooting based on the tcpdump tool. The web interface allows to apply custom filters like an IPv4 address as well as specific network services, as seen in the image (figure 1) below.