Management summary
Multiple vulnerabilities have been identified in the NesterSoft WorkTime employee monitoring software. An unauthenticated attacker is able to exploit an OS command injection vulnerability to completely take over the WorkTime server. A missing authorization check allows an attacker to reset the database configuration. Furthermore, an SQL injection vulnerability can be exploited in the admin interface with minimal permissions in order to read data from the database. In addition, a reflected cross-site scripting (XSS) vulnerability was identified.
A local attacker can exploit the update behavior of the WorkTime monitoring daemon to escalate privileges on the system to NT Authority\SYSTEM.
Vendor description
"WorkTime is a green employee monitoring software with a primary focus on monitoring employees' productivity. It is a non-invasive, transparent, safe, and socially responsible technology. WorkTime offers a safe replacement for every invasive function."
Source: https://www.worktime.com/employee-monitoring
Business recommendation
The vendor did not respond to our communication attempts anymore. It is currently unclear, whether a patch is available. Please contact the vendor to request a patch for the identified critical security issues.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
1) Unauthenticated OS Command Injection (CVE-2025-15559)
An unauthenticated attacker can inject OS commands when calling a server API endpoint. This allows an attacker to execute arbitrary commands on the WorkTime server as NT Authority\SYSTEM with the highest privileges. Attackers are able to access or manipulate sensitive data and take over the whole server.
2) SQL Injection (MSSQL/Firebird Backend) (CVE-2025-15560)
An authenticated attacker with minimal permissions can exploit a SQL injection in a WorkTime server API endpoint to inject SQL queries. If the Firebird backend is used, attackers are able to retrieve all data from the database backend. If the MSSQL backend is used the attacker can execute arbitrary SQL statements on the database backend and gain access to sensitive data.
3) Local Privilege Escalation (CVE-2025-15561)
An attacker can exploit the update behavior of the WorkTime monitoring daemon to elevate privileges on the local system to NT Authority\SYSTEM.
4) Reflected Cross-Site Scripting (XSS) (CVE-2025-15562)
A server API endpoint reflects received data into the HTML response without applying proper encoding or filtering. This allows an attacker to execute arbitrary JavaScript in the victim's browser if the victim opens a URL prepared by the attacker.
5) Broken Access Control results in Denial of Service (CVE-2025-15563)
Any unauthenticated user can reset the WorkTime on-prem database configuration by sending a specific HTTP request to the WorkTime server. No authorization check is applied here.
Proof of concept
1) Unauthenticated OS Command Injection (CVE-2025-15559)
The server API call to generate and download the WorkTime client from the WorkTime server is vulnerable against OS command injection in the “guid” parameter. For this proof of concept the following OS command is injected:
whoami > C:\secwashereThe HTTP request is shown below
< PoC removed >The injected command is executed on the server as NT Authority\SYSTEM:
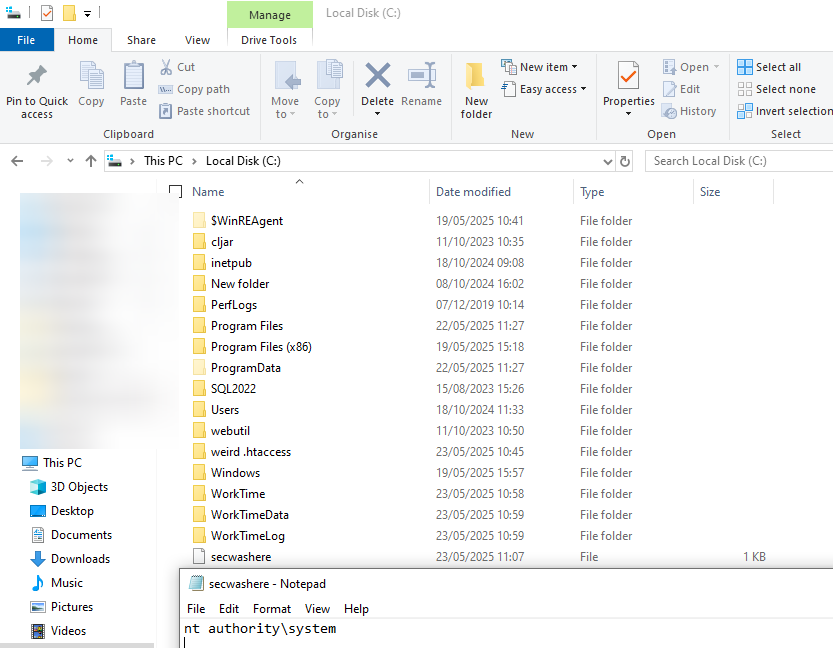
Command injection output
2) SQL Injection (MSSQL/Firebird Backend) (CVE-2025-15560)
The following authenticated "widget" API endpoint is vulnerable. Minimal permissions are required to access the server endpoint.
POST /api/widget HTTP/1.1
Host: <server_hostname>:8080
Content-Type: multipart/form-data; boundary=---------------------------295635091325610060643320064167
Content-Length: [...]
-----------------------------295635091325610060643320064167
< removed >
-----------------------------295635091325610060643320064167--Note that the request requires a token value in the request body. Any user that has access to the WorkTime server in any role has access to a valid token. The three parameters employee, computer and department are injectable. If the Firebird database backend is configured, the injection can be exploited using the following sqlmap command:
< PoC removed >If the MSSQL backend is used the following sqlmap command can be used with the request from above:
< PoC removed >Depending on the used MSSQL database user and the database configuration the injection can also be exploited to execute OS commands on the server.
3) Local Privilege Escalation (CVE-2025-15561)
To exploit the vulnerability, the attacker must first create an executable that should be executed with elevated privileges. For this proof of concept the following C code was used.
< PoC removed >It is required to add versioning information during the linking process. Otherwise WorkTime will not execute the created binary. Any resource file can be used:
1 VERSIONINFO
FILEVERSION 1,0,0,0
PRODUCTVERSION 1,0,0,0
FILEFLAGSMASK 0x3f
FILEFLAGS 0x0
FILEOS 0x40004
FILETYPE 0x1
FILESUBTYPE 0x0
BEGIN
BLOCK "StringFileInfo"
BEGIN
BLOCK "040904b0" // Language and code page
BEGIN
VALUE "CompanyName", "Your Company"
VALUE "FileDescription", "Your Application Description"
VALUE "FileVersion", "1.0.0.0"
VALUE "InternalName", "YourApp"
VALUE "OriginalFilename", "YourApp.exe"
VALUE "ProductName", "Your Product"
VALUE "ProductVersion", "1.0.0.0"
END
END
BLOCK "VarFileInfo"
BEGIN
VALUE "Translation", 0x409, 1200
ENDCompile the PoC code
$ x86_64-w64-mingw32-windres resource.rc -o resource.o
$ x86_64-w64-mingw32-gcc exec.c resource.oThe resulting executable must now be renamed to WTWatch.exe and be dropped in C:\ProgramData\wta\ClientExe.
The folder is writable by Everyone:
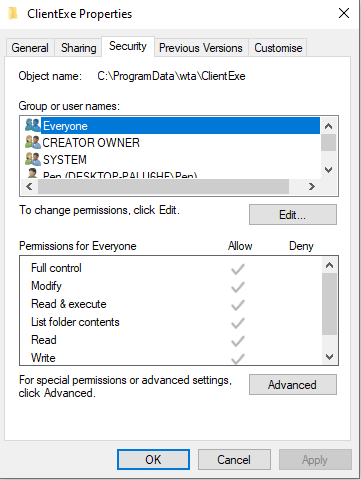
Folder permissions
After dropping the executable, it is executed by the WorkTime monitoring daemon as NT Authority\SYSTEM:
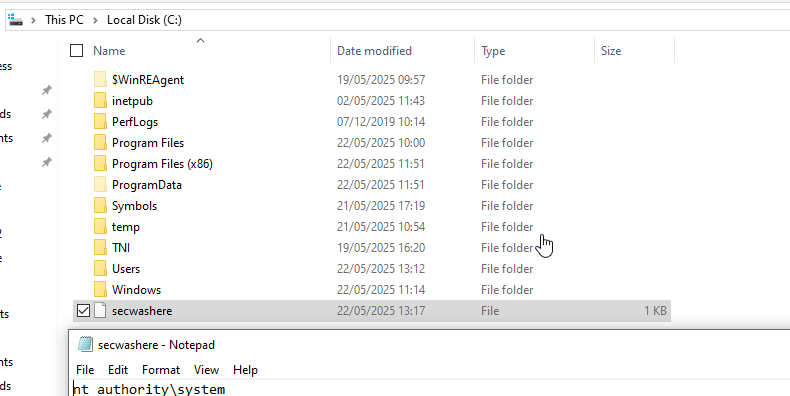
Privilege escalation
4) Reflected Cross-Site Scripting (XSS) (CVE-2025-15562)
As a proof of concept the following JavaScript payload was used:
alert(document.location)The type parameter in the POST body is reflected back into the HTML response
POST /report/internet/urls HTTP/1.1
Host: <server_hostname>:8079
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Cookie: PHPSESSID=[...]; aup_accept=accept
type="><script>alert(document.cookie)</script>The injected payload is reflected back into the HTTP response without proper encoding or filtering and the payload is executed:
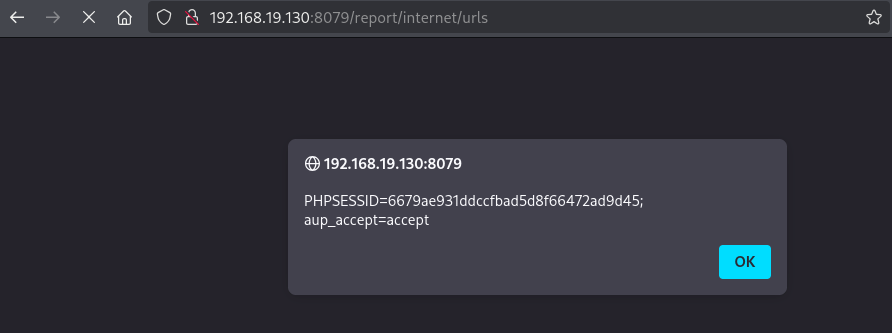
Cross Site Scripting
5) Broken Access Control results in Denial of Service (CVE-2025-15563)
An unauthenticated attacker can access the following URL to reset the server's configured database.
< PoC URL removed >If the attacker presses the displayed button the browser sends the following unauthenticated HTTP request which resets the database configuration:
< Poc removed >Vulnerable / tested versions
The following version has been tested which was the latest version available at the time of the test:
- WorkTime v11.8.8