Management Summary
Multiple vulnerabilities allow an attacker to take over the EfficientLab WorkExaminer Professional server from within an internal company network. Among code execution on the server as NT Authority\SYSTEM, the attacker gets access to all monitored data such as screenshots or keystrokes. An attacker can also exploit missing server-side authentication checks to get unauthenticated administrative access to the WorkExaminer Professional server and therefore the server configuration and data. In addition, all data between console, monitoring client and server is transmitted unencrypted. An attacker with access to the wire can therefore monitor all transmitted sensitive data.
Update 2025-10-27: The vendor informed us that they no longer support Work Examiner Professional/Standard and they are recommeding customers to switch to Controlio.
Vendor description
"Work Examiner Professional is a solution that will help you to perform a qualitative analysis of the usage of worktime and find the points where the efficiency of the personnel increases. Work Examiner Professional every manager will know how the employees' time is spent. Thus, the system shows the bottom-up pattern of the usage of the company's time on all the necessary control levels (division->section->department)."
Source: https://www.workexaminer.com/products/professional.html
Business recommendation
The vendor responded to the submission of our security vulnerabilities by stating that they are not within the scope of their bug bounty program. After telling them that we do not care about the bug bounty but a fix for the issues, we did not receive any further response.
Hence, there is no fix available for the identified security issues and we assume that this product is unmaintained. We urge customers to contact EfficientLab regarding the issues and a potential solution, such as using another product.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
1) Usage of Hardcoded FTP Credentials (FTP Access and RCE) (CVE-2025-10639)
An unauthenticated attacker with network access to port 12304 of the WorkExaminer server can use weak hardcoded credentials to login to the WorkExaminer FTP server and use the access to modify or read data, log files and gain remote code execution as NT Authority\SYSTEM on the server.
2) Missing Server-Side Authentication Checks (CVE-2025-10640)
An unauthenticated attacker with access to port 12306 of the WorkExaminer server can exploit missing server-side authentication checks to bypass the login prompt in the WorkExaminer Professional console to gain administrative access to the WorkExaminer server and therefore all monitoring data. This includes monitored screenshots and keystrokes of all users!
3) Unencrypted Communications (CVE-2025-10641)
All WorkExaminer Professional traffic between monitoring client, console and server is transmitted as plain text. This allows an attacker with access to the network to read the transmitted sensitive data. An attacker can also freely modify the data on the wire.
Proof of concept
1) Usage of Hardcoded FTP Credentials (FTP Access and RCE) (CVE-2025-10639)
The WorkExaminer Professional server installation comes with an FTP server that is used to receive the client logs. Weak hardcoded credentials can be used to access the FTP server on port 12304 via the network.
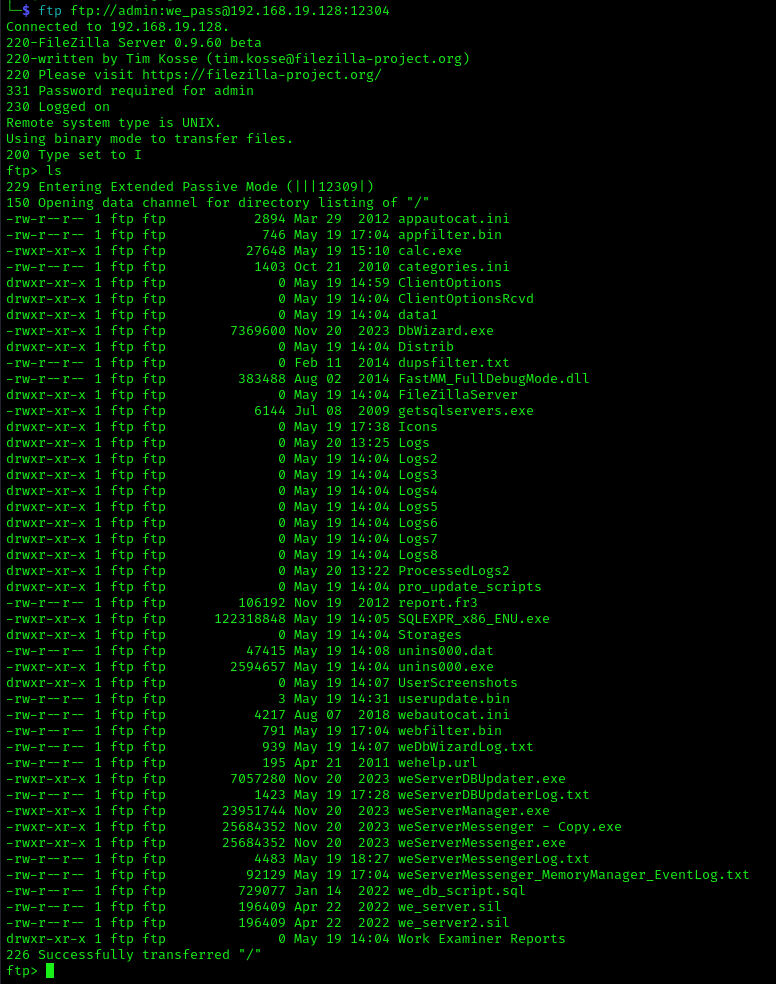
Figure 1: Access to FTP server with sensitive data
The attacker can then proceed to modify data or read any of the data stored in the WorkExaminer installation directory (e.g. "C:\Program File (x86)\Work Examiner Professional Server"). In addition it is possible to rename and overwrite one of the WorkExaminer service binaries to gain code execution on the WorkExaminer server as NT Authority\SYSTEM.
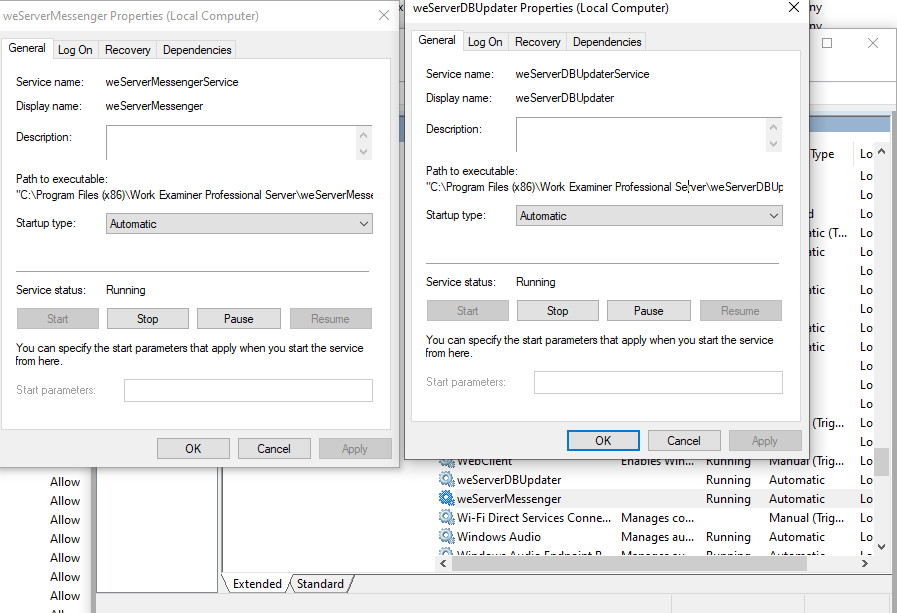
Figure 2: Service binaries
A Windows firewall exception is automatically created during the installation.
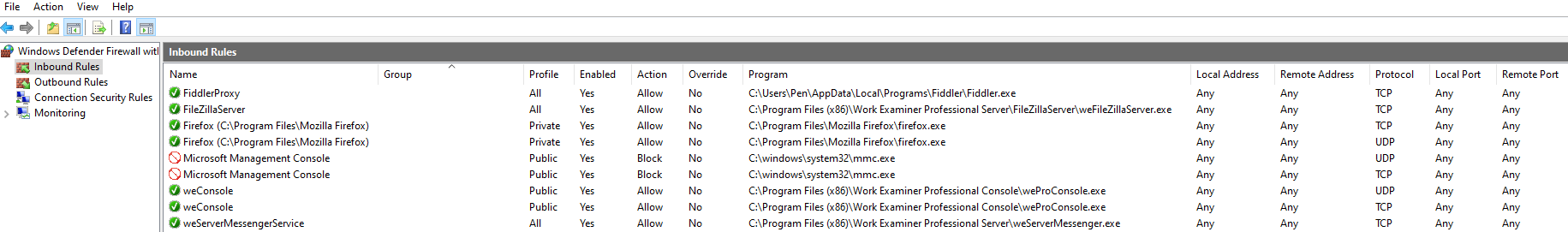
Figure 3: Firewall exception
2) Missing Server-Side Authentication Checks (CVE-2025-10640)
The WorkExaminer Professional console is used for administrative access to the server. Before access to the console is granted administrators must login. Internally a custom protocol is used to call a respective stored procedure on the MSSQL database. For general authentication the following procedure is called with the entered login name and password:
PROCEDURE [dbo].[we_Logins_AuthenticateSqlLogin]
@LoginName nvarchar(256),
@Password nvarchar(128),
@Result int OUTPUT
BEGIN
IF NOT EXISTS (SELECT LoginName FROM we_Logins WHERE @LoginName = LoginName)
RETURN (-1)
DECLARE @PasswordHash varbinary(128)
SELECT @PasswordHash = PasswordHash FROM we_Logins WHERE @LoginName = LoginName
SELECT @Result = PWDCOMPARE(@Password, @PasswordHash)
ENDHowever the return value of the call is not validated on the server-side. Instead it is only validated client-side. A quick authentication bypass can therefore be achieved by toggling the return value in the server response, when entering wrong credentials. For this proof of concept the global admin account "admin" was used.
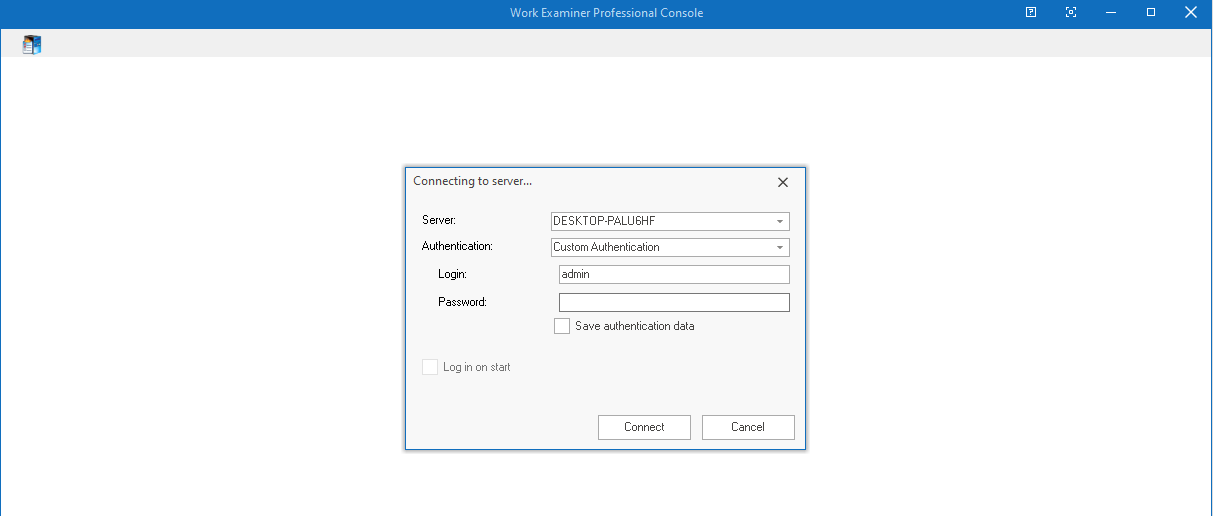
Figure 4: Login window
The highlighted byte in the server response is set from 0 to 1.
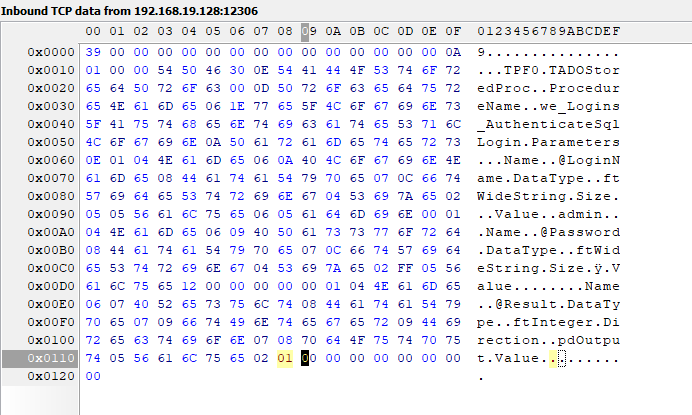
Figure 5: Server response toggle
The client now assumes that the authentication has succeeded and access is granted:
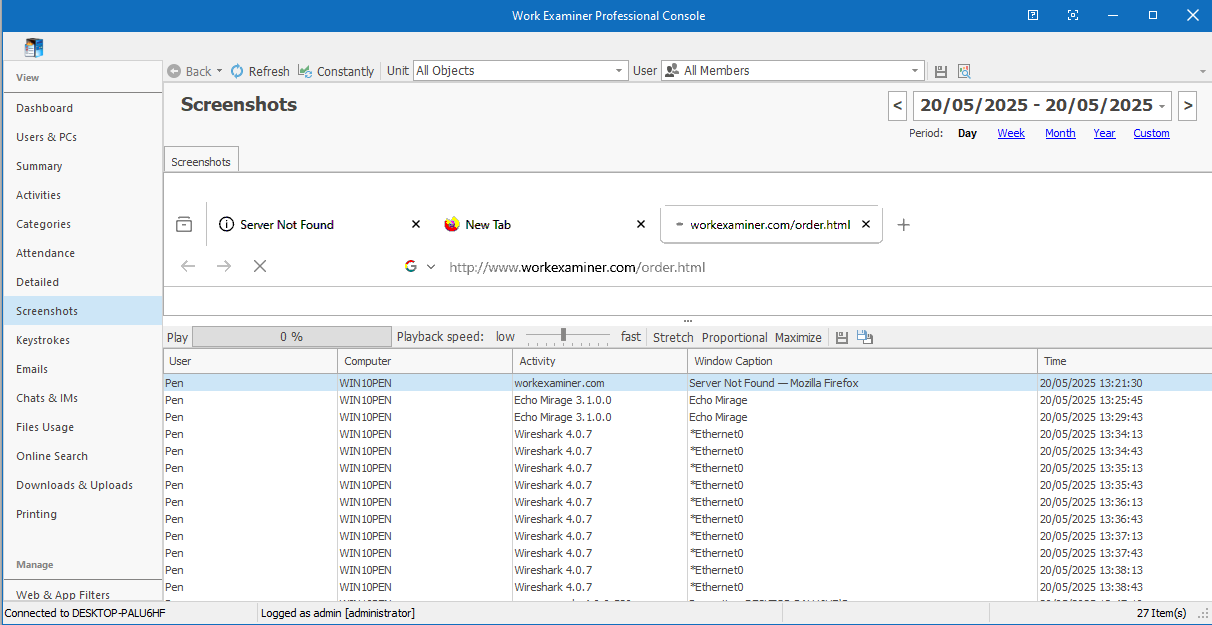
Figure 6: Login bypassed, logged in as admin
It is also possible to completely patch the login from the client. This can easily be achieved by replacing the selected instructions with nops:
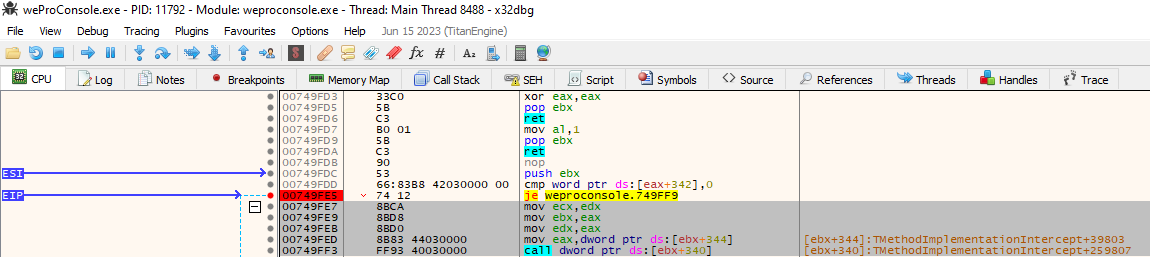
Figure 7: Debugger output
The modified client bypasses the login regardless of the entered password. If AD authentication is chosen during the login, the following procedure is called:
PROCEDURE [dbo].[we_Logins_GetLoginByName]
@LoginName nvarchar(256)
BEGIN
SELECT
LoginId,
LoginName,
Reports,
Menus,
AuthenticationType,
IsAdmin
FROM dbo.we_Logins
WHERE @LoginName = LoginName
ENDIn this case the return value must be replaced with the respective expected values.
3) Unencrypted Communications (CVE-2025-10641)
The monitoring clients transmit their data to the server using the unencrypted FTP. Clients connect to the FTP server on port 12304 and transmit the data unencrypted:
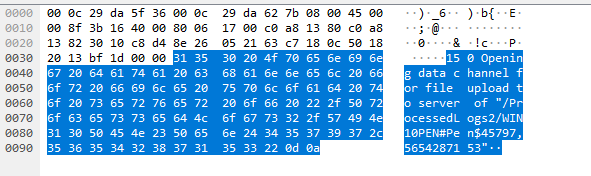
Figure 8: Unencrypted FTP communication
In addition, all traffic between the console client and the server at port 12306 is unencrypted. The following screenshot shows keystrokes that are retrieved via
the console:

Figure 9: Unencrypted console
Vulnerable / tested versions
The following version has been tested which was the latest version available at the time of the test:
- WorkExaminer Professional 4.0.0.52001