Vendor description
(Translated) "Elefant is the KBV-certified practice software from HASOMED, specializing in the needs of psychological psychotherapists, child and adolescent psychotherapists and medical psychotherapists. The software is ideal for individual and group practices, private accountants, medical care centers and training institutes in the fields of behavioral therapy, psychoanalysis, depth psychology -based psychotherapy and systemic therapy."
Source: https://hasomed.de/produkte/elefant/
Business recommendation
The vendor provides a patch which should be installed immediately.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
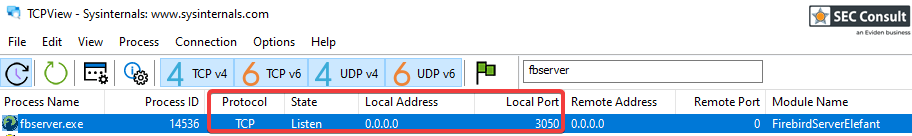
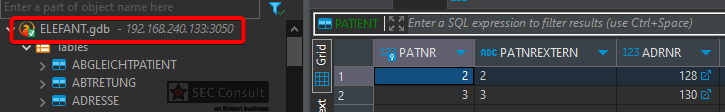
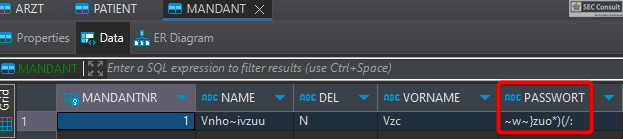
1) Unprotected Exposed Firebird Database (CVE-2024-50588)
An unauthenticated attacker with access to the local network of the medical office can use known default credentials to gain remote DBA access to the Elefant Firebird database. The data in the database includes patient data and login credentials among other sensitive data. In addition, this enables an attacker to create and overwrite arbitrary files on the server filesystem with the rights of the Firebird database ("NT AUTHORITY\SYSTEM").
2) Unprotected FHIR API (CVE-2024-50589)
An unauthenticated attacker with access to the local network of the medical office can query an unprotected Fast Healthcare Interoperability Resources (FHIR) API to get access to sensitive electronic health records (EHR).
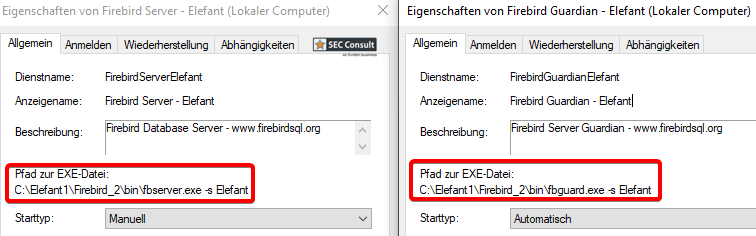
3) Local Privilege Escalation via Weak Service Binary Permissions (CVE-2024-50590)
An attacker with local access the to medical office computer can escalate his Windows user privileges to "NT AUTHORITY\SYSTEM" by overwriting one of two Elefant service binaries with weak permissions.
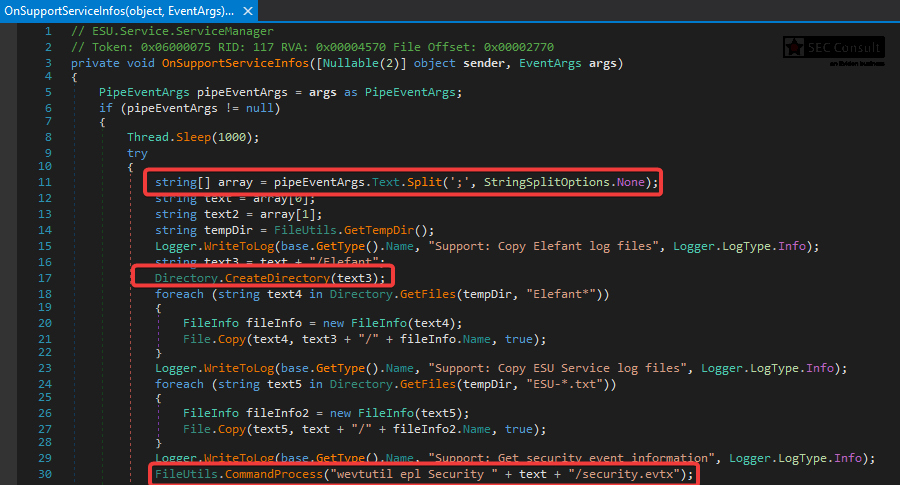
4) Local Privilege Escalation via Command Injection (CVE-2024-50591)
An attacker with local access the to medical office computer can escalate his Windows user privileges to "NT AUTHORITY\SYSTEM" by exploiting a command injection vulnerability in the Elefant Update Service. The command injection can be exploited by communicating with the Elefant Update Service which is running as "SYSTEM" via Windows Named Pipes.
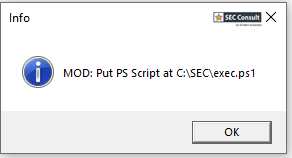
5) Local Privilege Escalation via Race Condition (CVE-2024-50592)
An attacker with local access the to medical office computer can escalate his Windows user privileges to "NT AUTHORITY\SYSTEM" by exploiting a race condition in the Elefant Update Service during the repair or update process.
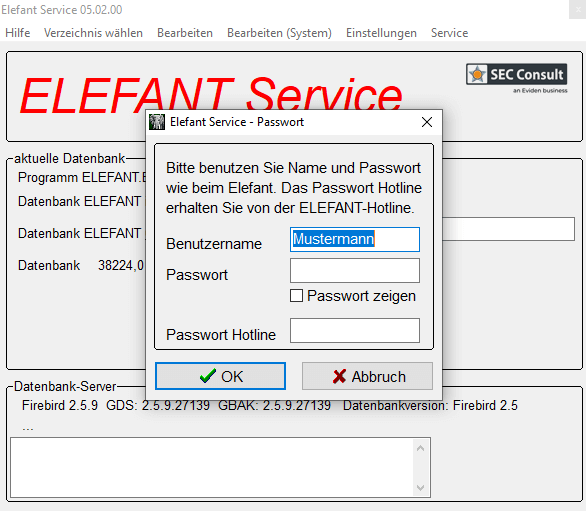
6) Hardcoded Service Password (CVE-2024-50593)
An attacker with local access to the medical office computer can access restricted functions of the Elefant Service tool by using a hard-coded "Hotline" password.