Management summary
The iMonitor EAM employee monitoring software is affected by multiple vulnerabilities, such as unencrypted and unauthenticated communication, which allows an attacker to read or manipulate sensitive data. Furthermore, a system service agent allows local privilege escalation and the EAM server uses weak default credentials for administrative access.
Vendor description
"iMonitor EAM combines user activity monitoring, behavior analytics and productivity tools in a single console, Prevent insider threats and increase productivity". […] "Centralized Employee Monitoring Solution: iMonitor EAM is a centralized employee monitoring solution which able to monitor 1000+ client computers with 1 server. [...]"
Source: https://www.imonitorsoft.com/employee-monitoring-software.html
Business recommendation
The vendor was unresponsive and did not answer to our communication attempts. Therefore, a patch is not available for these security issues. End users of this product should contact the vendor and demand a patch.
SEC Consult highly recommends performing a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
1) Unencrypted and Unauthenticated Communication (CVE-2025-10540)
The traffic between the EAM client agent and the EAM server, as well as between the EAM monitor management software and the server is transmitted in plain text. This means that neither the confidentiality nor the integrity of the transmitted data is protected from an attacker with access to network traffic.
As the software captures and transmits highly sensitive data such as keylogger history (which may include personally identifiable information, passwords, and other sensitive data) this poses a considerable business risk. Furthermore, an attacker can modify the command and control traffic to issue arbitrary commands to agents, including commands to run arbitrary applications on the agent machine.
2) Local Privilege Escalation (CVE-2025-10541)
An attacker can exploit a built-in update mechanism of the agent component eamusbsrv64.exe to elevate privileges on the local system to NT Authority\SYSTEM.
3) Insecure Default Credentials (CVE-2025-10542)
After installing the EAM server, access to the monitor management software is protected using the insecure default credentials with username 'admin' and a very weak three-digit password. These default credentials are also listed in the EAM monitor management software connection dialog for convenience. An attacker can use these default credentials to connect to the server and perform arbitrary actions on all agents in case the administrator does not change the password.
Proof of concept
1) Unencrypted and Unauthenticated Communication (CVE-2025-10540)
The communication between the EAM client agent and the EAM server can be observed using common package capturing tools such as Wireshark. The following screenshot shows that the observed traffic is unencrypted and contains sensitive data, such as passwords captured using the keylogger functionality: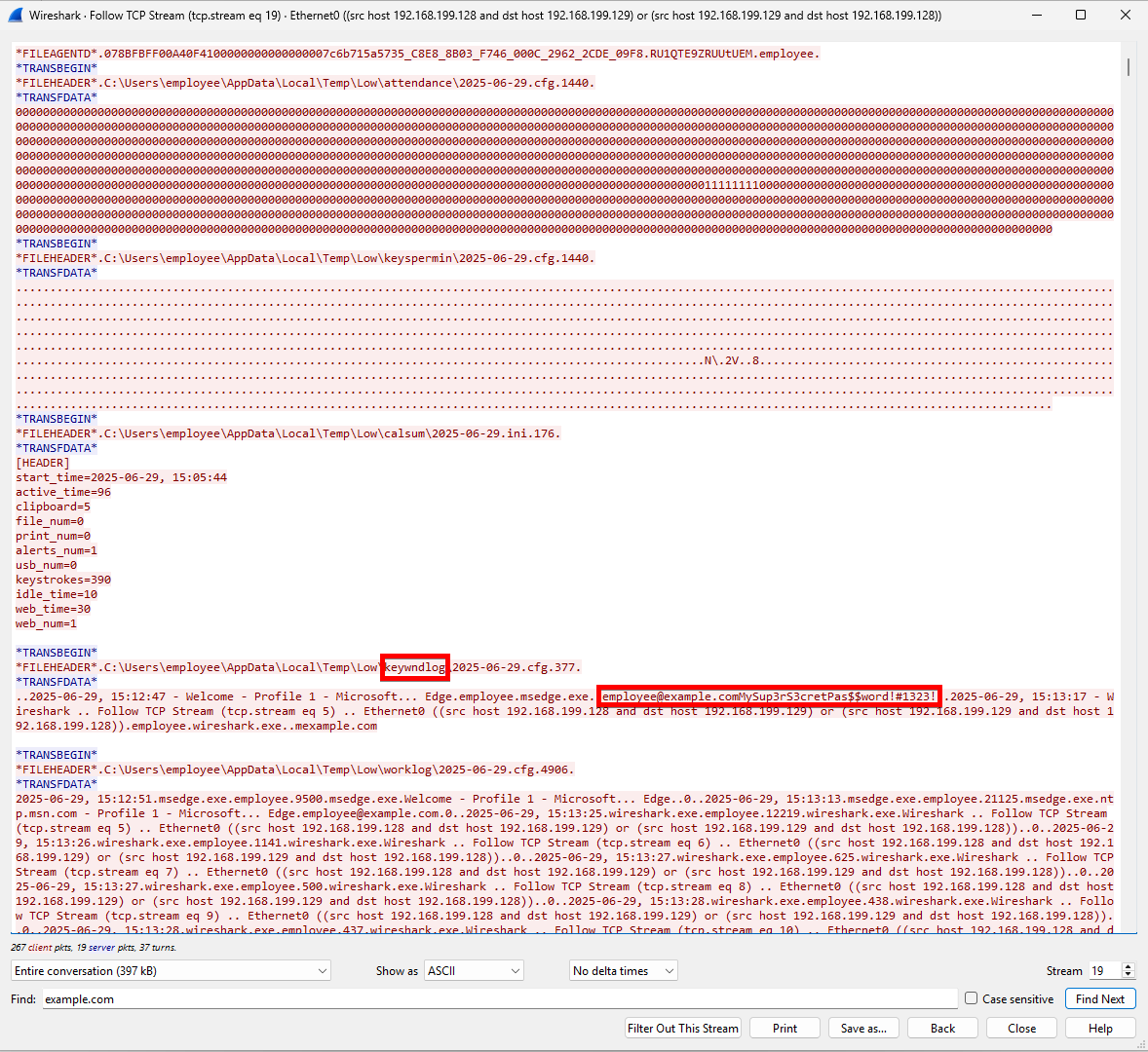
Figure 1: Plaintext protocol, wireshark
The communication between the EAM monitor management software and the server is also unencrypted. Sensitive data such as the EAM monitor password and all data captured from the agents (which may include personally identifiable information, passwords, and other sensitive data) can be found in the plain text traffic, as the following screenshot shows: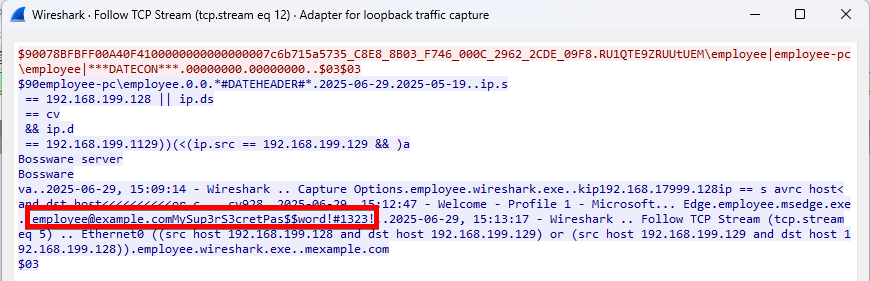
Figure 2: Captured plaintext credentials
2) Local Privilege Escalation (CVE-2025-10541)
The EAM agent installs a system service the runs the agent component eamusbsrv64.exe as NT Authority\SYSTEM. This executable contains an update mechanism to update the agent from files stored in path 'C:\sysupdate'. As any user can create this directory and write to it, this mechanism can be abused by a local attacker for privilege escalation.
When eamusbsrv64.exe is started, which happens automatically at system startup, it tests if the file 'C:\sysupdate\finish.txt' exists. If that file exists, all other files in that directory are moved to the EAM installation directory at 'C:\Windows\System\sys\syscon'. It is possible for an attacker to leverage this for arbitrary code exection by writing a DLL file with malicous code that will be loaded by eamusbsrv64.exe, for example wtsapi32.dll. The following proof-of-concept C code was used to create the DLL:
[ PoC removed ]The code can be compiled to a DLL using the following command:
x86_64-w64-mingw32-gcc malicious-dll.c -shared -o wtsapi32.dllTo prepare the exploit, the malicious wtsapi32.dll needs to be copied to 'C:\sysupdate\wtsapi32.dll'. Furthermore, the empty file 'C:\sysupdate\finish.txt' needs to be created. The following screenshot shows the prepared exploit state: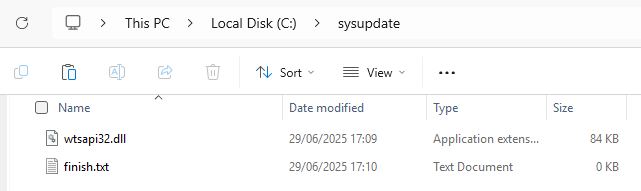
Figure 3: Sysupdate contents
To run the exploit, the eamusbsrv64.exe service must be restarted, which can be accomplished by restarting the computer. After the restart, the ‘C:\sysupdate’ directory is empty again, and the exploit has succeeded. The proof-of-concept file 'C:\sec-consult-poc.txt' is now present and demonstrates that the exploit runs with NT Authority\SYSTEM privileges, as the following screenshot shows: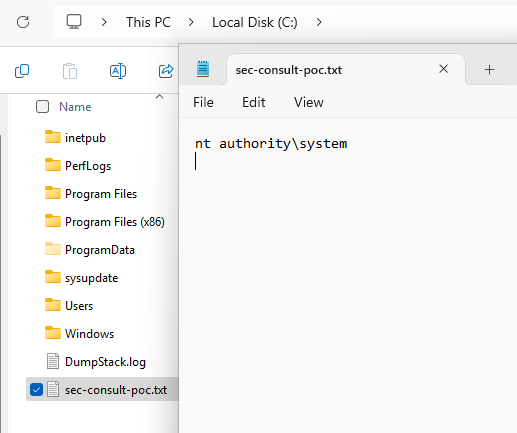
Figure 4: PoC result, execution as NT Authority\SYSTEM
3) Insecure Default Credentials (CVE-2025-10542)
After installing the EAM server, access to the monitor management software is protected using the insecure default credentials with username 'admin' and password '000'. These default credentials are also listed in the EAM monitor management software connection dialog for convenience, as the screenshot below shows. An attacker can use these default credentials to connect to the server and perform arbitrary actions on all agents in case the administrator does not change the password.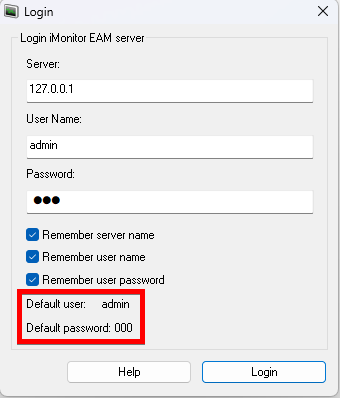
Figure 5: Default credentials shown in login form
Vulnerable / tested versions
The following version has been tested which was the latest available trial version at the time of the test:
- iMonitor EAM 9.6394