Vendor description
"TightGate-Pro is a ReCoB system. ReCoBS stands for Remote-Controlled Browser System, literally translated 'remote-controlled web browser'. TightGate-Pro physically separates the web browser execution environment from the workstation. The system thus shields the internal network from the Internet and reliably and preventively prevents attacks via the web browser. TightGate-Pro is the strongest dedicated ReCoBS, because only physical outsourcing on a hardened system permanently withstands attacks. Local virtualisations, sandboxing systems or micro-virtualisations do not offer effective protection. TightGate-Pro is used in public authorities, financial institutions, industrial companies and critical infrastructures – in short, everywhere where “safe surfing on the Internet” is indispensable at the workplace and internal infrastructures must be reliably protected. TightGate-Pro is BSI-certified according to EAL3+."
Source: https://www.m-privacy.de/en/tightgate-pro-safe-surfing/
Business recommendation
The vendor provides a patch which should be installed immediately.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
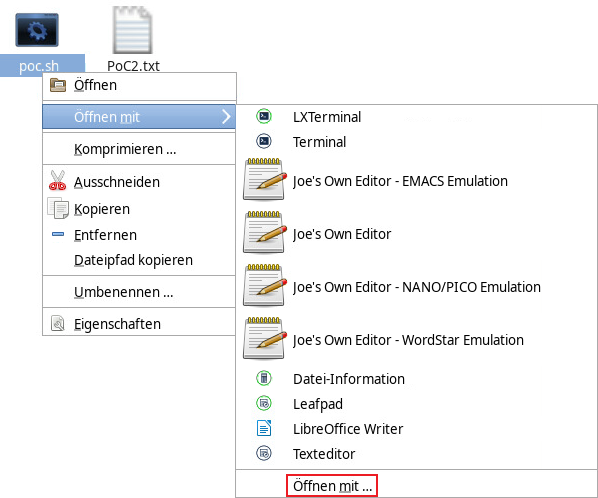
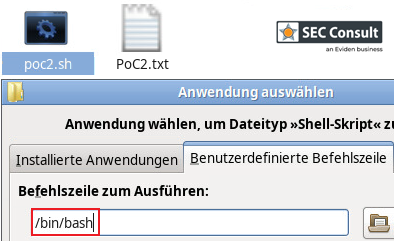
1) Code Execution
Execution of single commands and scripts is possible with the privileges of the current user. Code execution is possible with any file type on the server and no specific permissions need to be set for the utilized file.
Vendor response (translated):
"It is intended behavior to execute arbitrary bash scripts. It is not possible to execute arbitrary programs and libraries. There is no privilege escalation possible with this vulnerability."
We can confirm that it was not possible to escalate privileges during our test.
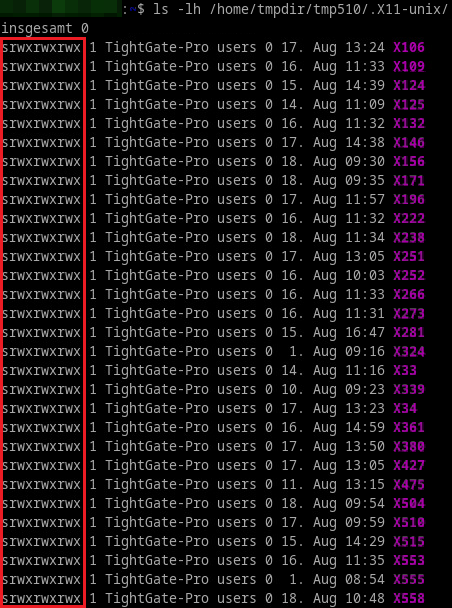
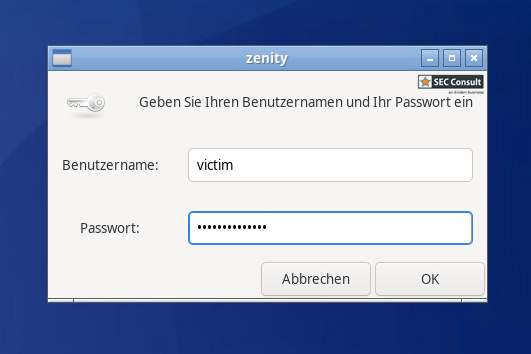
2) Access to all Desktops (CVE-2023-47250)
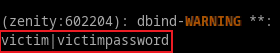
Multiple users are connecting to the same TightGate-Pro server, resulting in one instance of the X11 window system. Due to insecure permissions of the X11 sockets it is possible for any user to open arbitrary windows on the desktop of other users for phishing attacks or installing a keylogger directly.
Vendor response (translated):
"We acknowledge this issue as a important vulnerability. A fix with full RSBAC-Jail-Separation and changed Linux-Filesystem permissions is currently available in the "Prestable" packages:
- mprivacy-tools_2.0.406g
- tightgatevnc_4.1.2~1
- rsbac-policy-tgpro_2.0.159
These can be applied by the admin user "update". The updates will be provided automatically as Hotfix around 2023-10-24."
3) File Transfer by Abusing the Print function (CVE-2023-47251)
TightGate-Pro allows printing PDF documents on the host system. Documents are transferred to the host, printed and deleted afterwards. An attacker is able to control the path of the transferred file and to prevent the automatic deletion of the file.
Vendor response (translated):
"This is not a severe finding but we already fixed it. The fixes are available in the packages:
- mprivacy-tools_2.0.406g
- tightgatevnc_4.1.2~1
Now the .spool directly is always scanned for malicious data and the VNC- client does not transfer files which contain path symbols (e.g. ../)."
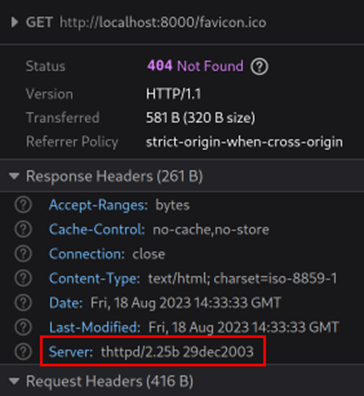
4) Outdated Update Server
Based on disclosed version numbers the update server is running outdated software with known vulnerabilities. The criticality of this issue depends on the exploitability of these issues.
Vendor response (translated):
"The old version of thttpd is already known. This is not seen as security-relevant. The access to the updateserver requires a previous registration of a customer-provided SSH key, which is only available to administrators on the TightGate-Pro instance. thttpd is isolated on the updateserver and can only *read* files. Even if an attacker can write malicious updatepackages, these are still secured by a cryptographic signature and would not be installed on TightGate-Pro instances. We will eventually replace thttpd with lighthttpd which is still supported."