Vendor description
"frentix operates in the areas of e-learning, software development, multimedia and media production. Providing information and lasting impressions – we try to reconcile this goal in the area of tension between technology, usability and design." "The LMS OpenOlat is an internet-based learning platform for teaching, learning, assessment and communication, an LMS, a learning management system."
Source: https://www.openolat.com/unternehmen/
Business recommendation
The vendor provides a patch which should be installed immediately.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
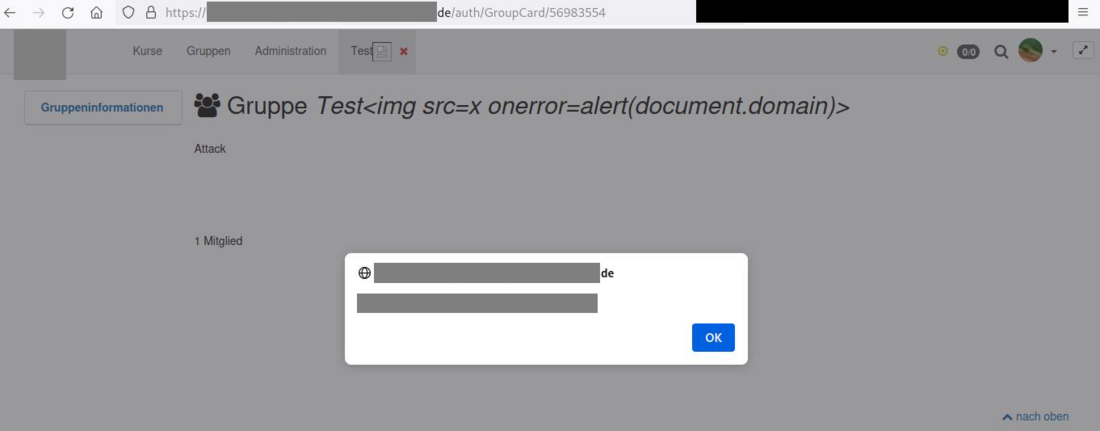
1) Multiple Stored Cross-Site-Scripting Vulnerabilities (CVE-2024-25973)
Insufficient filtering and sanitization of user input leads to the creation of groups, courses and other resources that contain XSS payloads. This allows an attacker to execute JavaScript code with the permissions of the victim in the context of the user's browser.
2) Privilege escalation via XSS due to insecure CSP
If the content security policy is not set securely and there is content on the same page that can be manipulated by the attacker, a privilege escalation can take place.
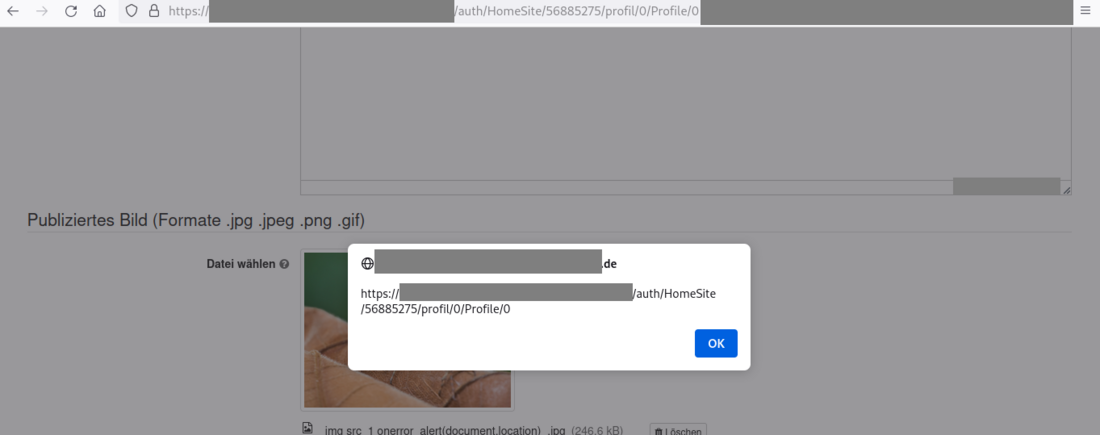
3) Stored Cross-Site-Scripting within the Media Center (CVE-2024-25974)
Insufficient filtering and sanitization of malicious files uploaded by a user leads to stored resources within the Media Center that could contain XSS payloads. This allows an attacker to execute JavaScript code with the permissions of the victim in the context of the user's browser.
Proof of concept
1) Multiple Stored Cross-Site-Scripting Vulnerabilities (CVE-2024-25973)
Various XSS issues have been found in different functions of OpenOLAT. The following examples show different attack scenarios.
Example 1 - Stored Cross-Site-Scripting within Coursenames
Due to insufficient filtering and sanitization of user input, an attacker with rights to create or edit groups can create a course with a name that contains an XSS payload. When a user edits this course the name including the payload is displayed and executed. Furthermore, the XSS payload is executed when editing the course via the course-editor, within the course-editor's "layout" tab inside the preview. This also happens multiple times at multiple locations during the publishing workflow.
The following payload was used as coursename:
<img src=x onerror=alert('from\u0020subcat\u0020title')>