Vendor description
"Omada Identity is a modern, enterprise-ready IGA solution that is deployed on-premises, giving you full control over your data and security. Our solution is easy to use, highly customizable, and gives you complete visibility into your environment without having to write a single line of code but is completely customizable to address any requirement. With built-in automation features, Omada Identity can help you streamline your workflows, improve efficiency, and strengthen your security posture."
Source: https://omadaidentity.com/products/omada-identity/
Business recommendation
Upgrade to version v15U1 or install hotfix #309 for v14.14.
SEC Consult highly recommends to perform a thorough security review of the product conducted by security professionals to identify and resolve potential further security issues.
Vulnerability overview/description
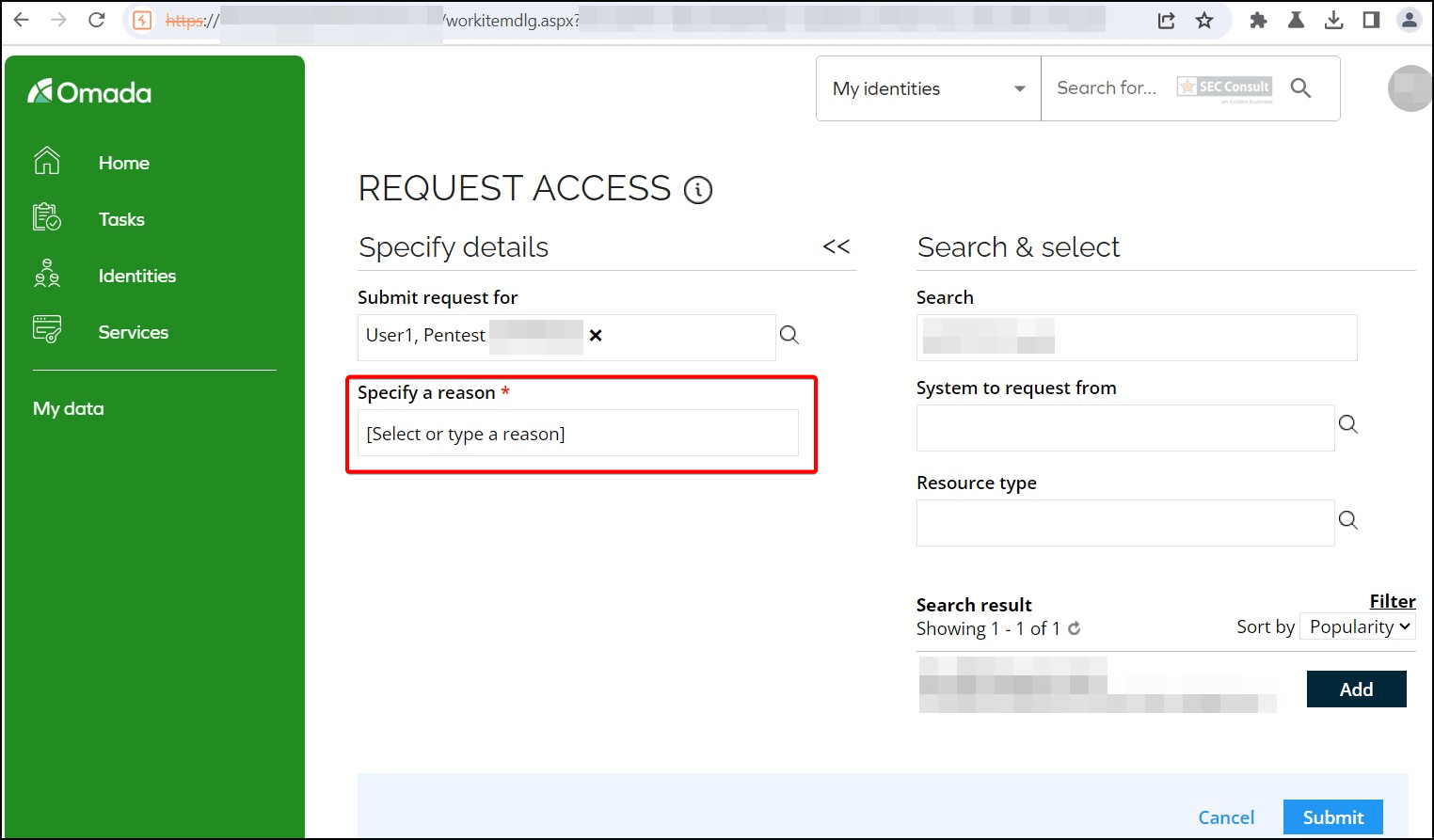
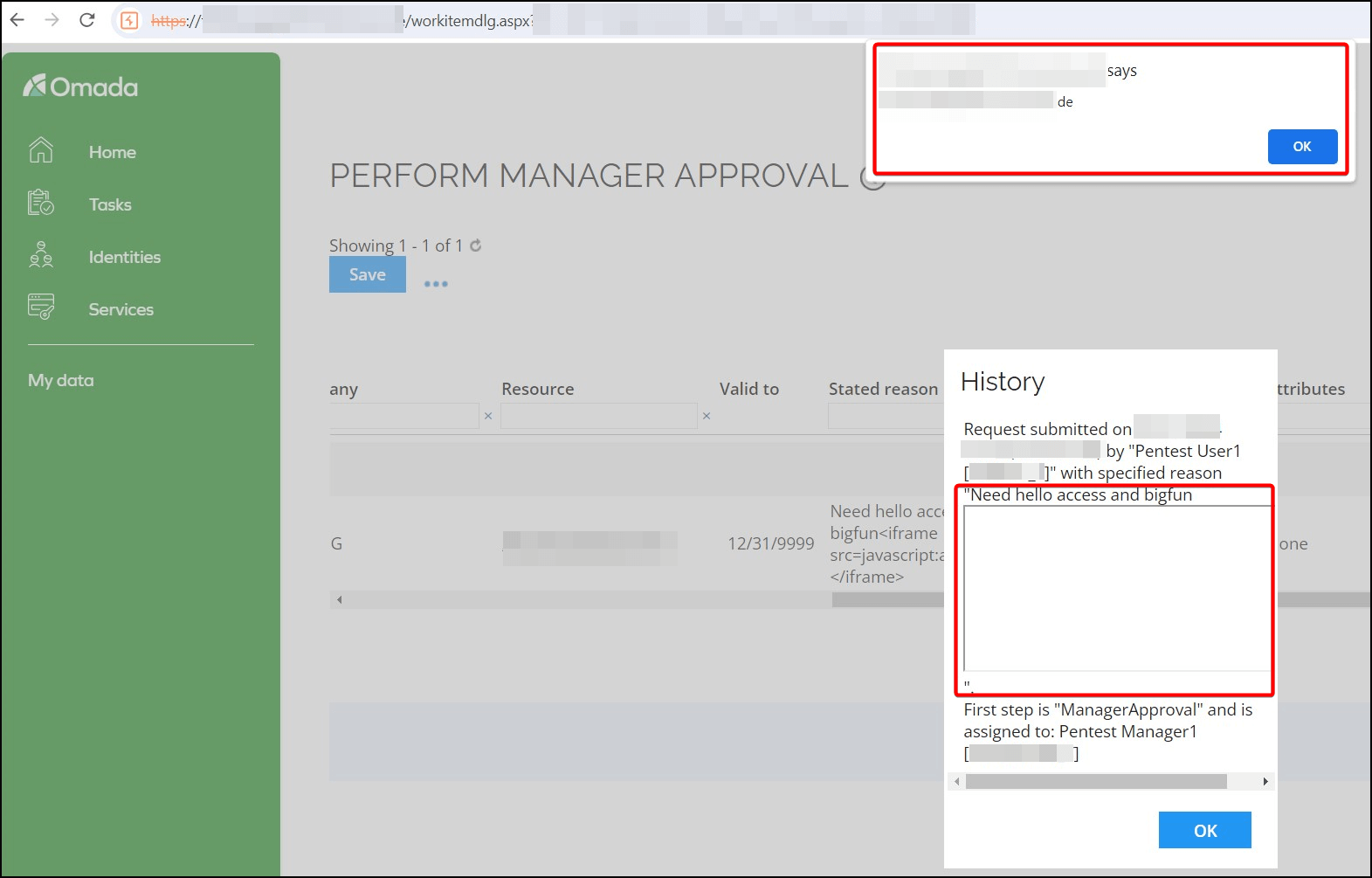
1) Stored Cross-Site Scripting (CVE-2024-52951)
An authenticated user can inject JavaScript in the "Request Reason". The injected JavaScript code will be executed if another user looks at the "History" of this access request. An attacker can then execute arbitrary JavaScript in the browser of other users which could for example be used for phishing attacks.