Vendor Description
“From the start, the Fortinet vision has been to deliver broad, truly integrated, high-performance security across the IT infrastructure. We provide top-rated network and content security, as well as secure access products that share intelligence and work together to form a cooperative fabric. Our unique security fabric combines Security Processors, an intuitive operating system, and applied threat intelligence to give you proven security, exceptional performance, and better visibility and control–while providing easier administration.”
Source: https://www.fortinet.com/corporate/about-us/about-us.html
Business Recommendation
The patched FortiClient versions should be installed immediately as the VPN credentials could be decrypted by an attacker.
Vulnerability Overview/ Description
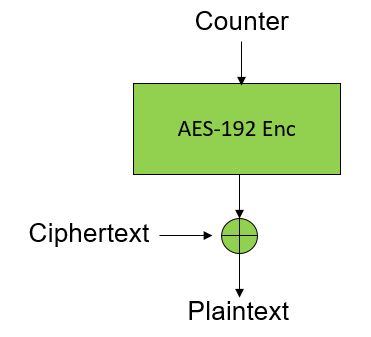
FortiClient stores the VPN authentication credentials in a configuration file (on Linux or Mac OSX) or in registry (on Windows). The credentials are encrypted but can still be recovered since the decryption key is hardcoded in the program and the same on all installations. Above all, the aforementioned storage is world readable, which actually lays the foundation for the credential recovery.
Proof Of Concept
1) Hardcoded key
The hardcoded key can be disclosed on the Linux version by issuing the following command:
$ strings forticlientsslvpn |grep "fc_1A"
fc_1A2Brown3Fox4Jumped5Over6A7Lazy8Dog
The same decryption key can be found in the Windows and Mac OSX binary.
2) Overly permissive access control
The read access of the configuration file is set for “others” too, making the file world-readable. On Mac OSX, the file can be found under
/Library/Application Support/Fortinet/FortiClient/conf/vpn.plist
while the same dataset is stored in the registry key
HKLM\SOFTWARE\WOW6432Node\Fortinet\FortiClient\Sslvpn\Tunnels
on Windows, which is world-readable for all users as well.
$ ls -l /home/user/.fctsslvpnhistory
-rw-rw-rw- 1 root root 1227 Aug 23 12:26 .fctsslvpnhistory
$ cat /home/user/.fctsslvpnhistory
...
profile=demo
p12passwdenc=Enc 420d2ee65abded897a69c50f4995397969f1c1f949055d8e51
path=
passwordenc=Enc 420d2ee65abded897a69c50f49956909f61e3e549873cdfecf12bafdfa7b78f789a17ba1a5a6c9eb1803
user=li
port=443
server=server.com
...
Combining the two issues, an attacker can steal the password of any user who has a FortiClient profile on the system. In an enterprise environment, where employees usually log onto VPN server with their domain credentials, a vicious employee can extensively harvest the credentials of colleagues by logging onto the workstation where the credentials have been stored. Hence an attacker might steal credentials of any user in the domain and gain access to their user account (e.g. emails, other private data).
SEC Consult developed a proof of concept tool which takes as input the encrypted string, and prints the decrypted hexdecimal bytes followed by the recovered password. For now, this tool will not be released to give users more time to patch.
$ kr 420d2ee65abded897a69c50f49956909f61e3e549873cdfecf12bafdfa7b78f789a17ba1a5a6c9eb1803
0x50 0x61 0x73 0x73 0x77 0x6f 0x72 0x64
0x52 0x65 0x63 0x6f 0x76 0x65 0x72 0x65
0x64 0x00
PasswordRecovered
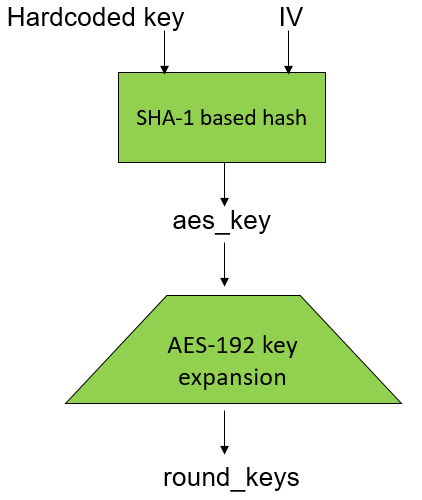
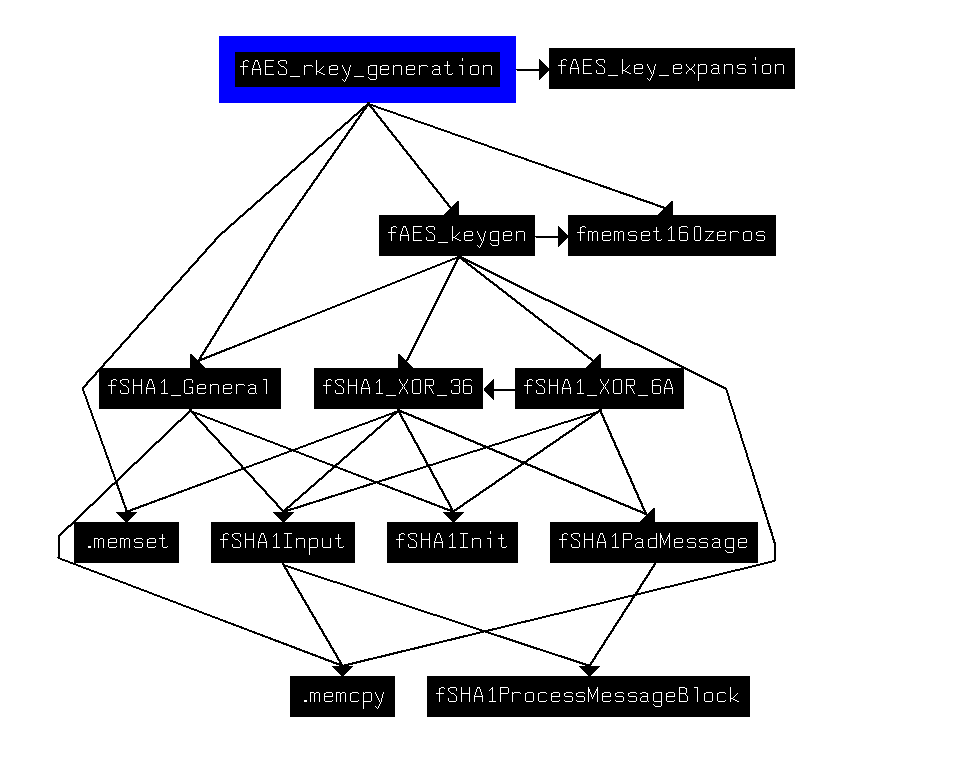
The key generation module is based on a modified SHA-1 hash function, where the hardcoded key and IV flow in and the 24 bytes AES key comes out, what is followed by the AES-192 key expansion routine: