Vendor Description
“The WAGO-I/O-SYSTEM is a flexible fieldbus-independent solution for decentralized automation tasks. With the relay, function and interface modules, as well as overvoltage protection, WAGO provides a suitable interface for any application.”
Source: http://global.wago.com/en/products/product-catalog/components-automation/overview/index.jsp
“The PFC family of controllers offers advanced compact, computing power for PLC programming and process visualization. Programmable in accordance with IEC 61131-3 600, PFC controllers feature a 600 MHz ARM Cortex A8 processor that offers high speed processing and support of 64 bit variables.”
Business Recommendation
Because of the use in industrial and safety-critical environments the patch has to be applied as soon as it is available. We explicitly point out to all users in this sector that this device series in the mentioned device series with firmware 02.07.07(10) should not be connected directly to the internet (or even act as gateway) since it is very likely that an attacker can compromise the whole network via such an device.
SEC Consult recommends not to use this product in a production environment until a thorough security review has been performed by security professionals.
Vulnerability Overview / Description
The “plclinux_rt” service accepts different unauthenticated actions.
This vulnerability contains the architectural security problems described by Reid Wightman. The SDK of “plclinux_rt” is written by the same vendor (3S). Therefore, the file commands of “Digital Bond’s 3S CODESYS Tools”, created around 2012 are applicable.
(See https://ics-cert.us-cert.gov/advisories/ICSA-13-011-01)
The CODESYS command-line is protected with login credentials, that’s why the shell of the mentioned tools does not provide root access out of the box. But after some investigation it was clear that there are further functions which are reachable without using the command-line and without any authentication.
These functions in “plclinux_rt” can be triggered by sending the correct TCP payload on the bound port (by default 2455).
Some of the triggerable functions are:
- Arbitrary file read/write/delete (also covered by “Digital Bond’s Tools”)
- Step over a function in the currently executed PLC program
- Cycle step any function in the currently executed PLC program
- Delete the current variable list of the currently executed PLC program
- And more functions…
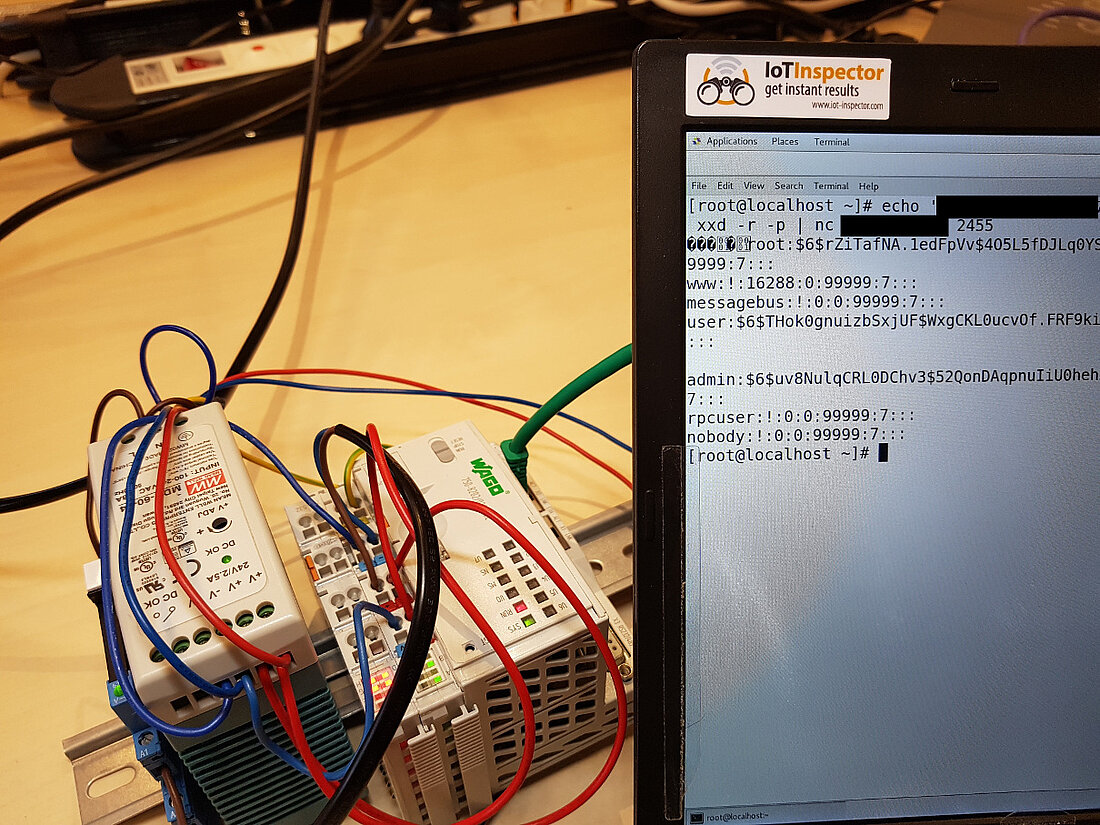
Since SSH is activated by default, an unauthenticated attacker can rewrite “/etc/shadow” and gain root privileges easily via these attack vectors!
1) Critical Improper Authentication / Design Issue
Files can be fetched, written and deleted. Running tasks on the PLC can be restarted, stepped and crashed. An attacker can therefore replace the password hash in the shadow file. A memory corruption (and potential reverse-shell) is also possible via arbitrary TCP packets. There are potentially more commands which can be triggered, but this was not covered by the short security crash test.
Proof Of Concept
As there is no patch available yet, the detailed proof of concept information has been removed from this advisory.
1) Critical Improper Authentication / Design Issue
Two payloads are specified here as proof of concept for file manipulation. Four payloads for live program manipulation are also listed.
File read and delete without any authentication.
Read “/etc/shadow”:
echo '[PoC removed]' | xxd -r -p | nc <PLC-IP> <Port>