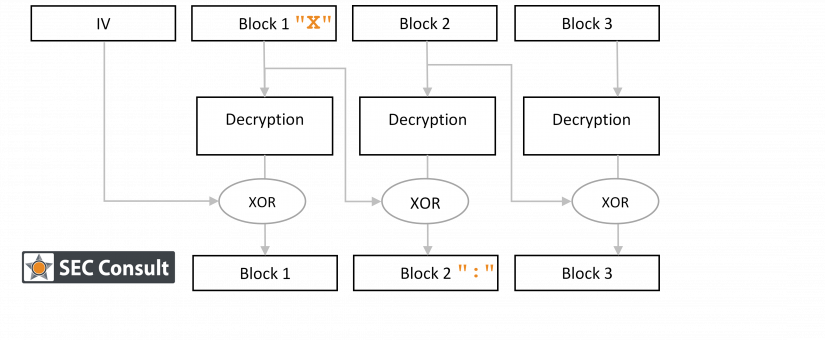
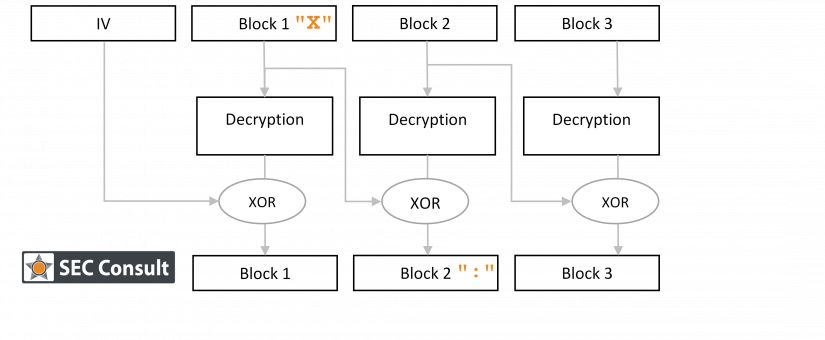
This Java library was susceptible to two attacks that could potentially allow an attacker to bypass some of the OSCI-Transport protocol’s core security promises.
Since its introduction in 2001, the OSCI-Transport protocol has been adopted by many German government agencies to allow them to securely exchange data over untrusted networks (e.g. the Internet). The OSCI-Transport protocol provides integrity, authenticity, confidentiality and non-repudiation for all data exchanged. The OSCI-Transport Library is a free implementation of this protocol and is distributed by KoSIT.
Back in 2017 SEC Consult identified several vulnerabilities in this library. When we had a short look at the code in September 2018 again, two other vulnerabilities could be identified, which are described in this blog post. These vulnerabilities allow an attacker to bypass the security layers that are designed to protect a message’s metadata (request and response signature and request and response encryption).
Therefore, when all security measures provided by OSCI-Transport are activated, the impact of these vulnerabilities is limited. However, the impact is critical if e.g. content signature and content encryption are not active. As we have very little insight into how the OSCI-Transport protocol is used in practice, it is not possible to reasonably estimate the real-life impact of these vulnerabilities. Setting the practical applicability aside, the technical details of these vulnerabilities are rather interesting and are being shared with you now.
SEC Consult did not conduct a full security audit and can therefore not make any statement regarding the overall security of the library or its security mechanisms.
OSCI-Transport Overview
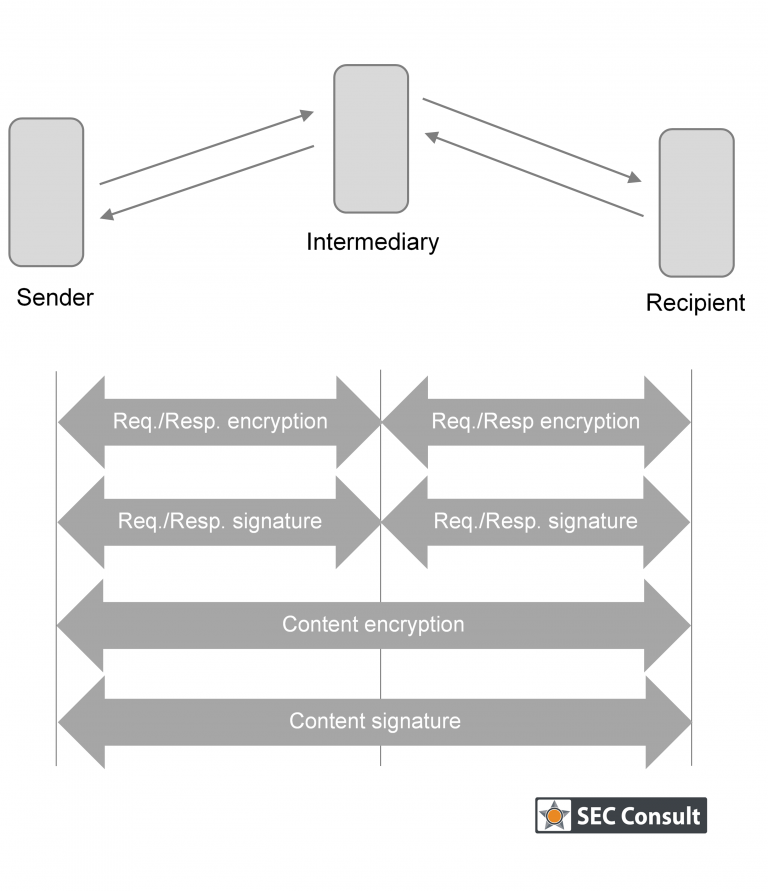
OSCI-Transport is an XML-based data exchange protocol that requires an Intermediary to route communication between a Sender and a Recipient. The main security features of OSCI-Transport are:
- The content signature provides authenticity for the payload data that is exchanged.
- The content encryption provides confidentiality for the payload. As the Intermediary cannot decrypt the payload, OSCI-Transport provides end-to-end encryption.
- The request and response signature provides authenticity for the data that is exchanged between a Sender and the Intermediary or between the Recipient and the Intermediary.
- The request and response encryption provides confidentiality for the communication to and from the Intermediary.
All of these security mechanisms are optional – the communication partners have to agree on which mechanisms to use.
When sending data, the Sender has to initiate a connection to the Intermediary (e.g. over HTTP) and send the OSCI-Transport XML message. For receiving data, two scenarios are defined: in the active recipient scenario, the recipient initiates a connection to check for a message while in the passive recipient scenario, the Intermediary initiates the connection as soon as a new message is available.