Data Security And Compliance In The Home-Office
dataprotection
In The Beginning Was Data Security
It is already estimated that in the future up to 25% of data security breaches will occur outside the corporate infrastructure.[1] It is particularly alarming that employees are often unaware of regulations and measures for the secure handling of company data at home. Many companies do not even have corresponding regulations for telework.
Suitable security concepts in the form of appropriate guidelines, processes and technical protective measures for the processing of their sensitive company data are therefore highly recommended.
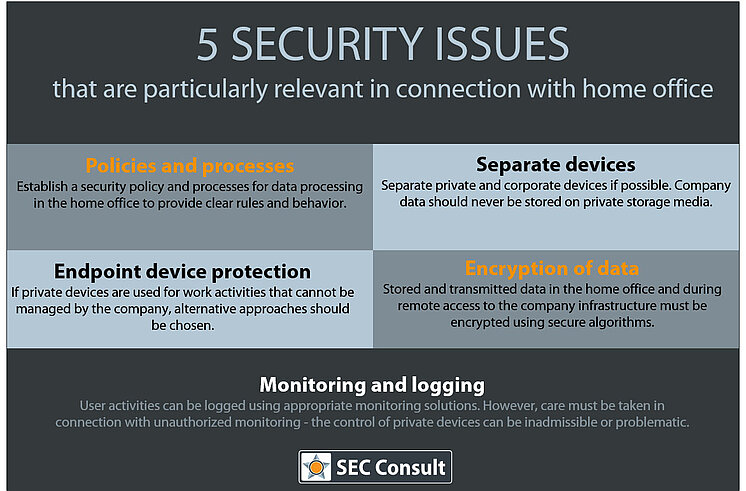
These security issues are particularly relevant in connection with teleworking:
- Policies and processes: The company should establish a security policy and processes for data processing in the home office that provide clear rules and behavior.
- Encryption of data: Stored and transmitted data in the home office and during remote access to the company infrastructure must be encrypted using secure algorithms.
- Endpoint device protection: If private devices are used for work activities that cannot be managed by the company, alternative approaches should be chosen (e.g. recommendations to individual employees on how to protect private devices).
- Separation of private and corporate devices: Private and corporate devices should be separated if possible. Company data should never be stored on private storage media. Ensure that company devices are protected from unsecure or malware-infected employee home devices.
- Monitoring and logging: User activities can be logged using appropriate monitoring solutions. However, care must be taken in connection with unauthorized monitoring – the control of private devices can be inadmissible or problematic.
Safety Standards As A Helpful Basic Framework
The selection of sensible protective measures is often complicated and lengthy. It is therefore advisable to orientate oneself on recognized safety standards. These include, for example, ISO/IEC 27001 and 27002, NIST CSF or even basic IT protection from the BSI.
A recognized security standard is particularly helpful in providing a framework of measures. This counteracts the danger of a confusing, inefficient, ineffective and costly implementation of individual measures that do not achieve the desired result. It ensures that the security controls in the company are both effective and economical.
The Compliance Issue
As with all other activities, in connection with work performed in the home office, it must be ensured that legal, contractual and internal data protection regulations are demonstrably complied with. To this end, many companies have already launched several data protection initiatives over the last few years, including the establishment of entire data protection management systems. In most cases, these are very much geared to conventional business operations. Compliance issues in the area of teleworking are hardly considered.
Here you will find an overview of relevant aspects to be considered:
- Examination / adjustment of data protection contracts with regard to new work situation
- Order processing
- Common responsibilities
- SLAs
- Updating existing records of home office operations
- List of processing activities
- Internal security guidelines
- Privacy policy/notice
- Adaptation of the risk assessment
- Include home office activities in privacy impact and risk assessments
Pragmatically Solve Implementation Control
Companies must ensure that the implemented technical and organizational data security measures are effective and are adhered to. This is a challenge even in the normal working day, which is made even more difficult by the shift to the home office.
An effective control of the employee is only possible to a very limited extent. After all, how do you want to check whether the company’s security standards are being maintained within the private home network in a private apartment?
The definition of appropriate and effectively enforceable control rights should be solved pragmatically. Existing data security concepts must take the risks associated with teleworking sufficiently into account and provide for appropriate protective measures. It is important to provide targeted support to employees at all levels of the company to ensure effective compliance.
More home office tips for employees and managers can be found in this blog article: IT security in the home office – what should be considered?
[1] https://www.watchguard.com/wgrd-resource-center/predictions-2020

