In this article, we will discuss user privacy issues that our team has recently discovered in two independent e-signature solutions, which have been fixed by now. In the past we also discovered vulnerabilities related to e-signature, for example, a high risk vulnerability in the central e-government services portal allowed user impersonation.
Typical Usage Scenarios
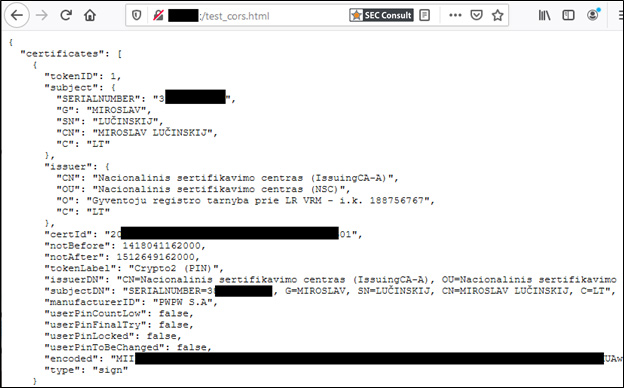
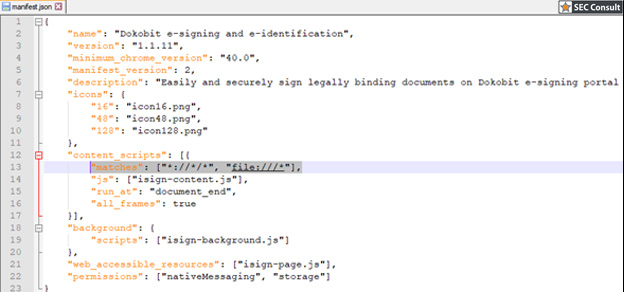
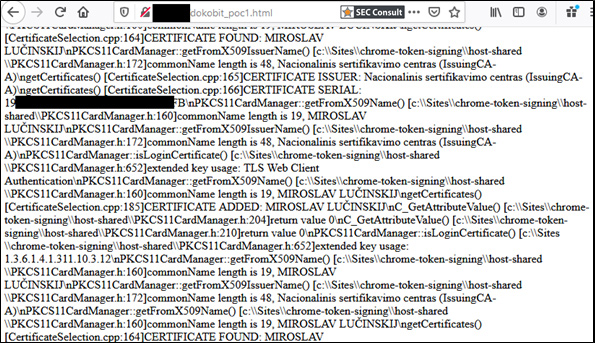
With document signing, Lithuanian e-signature users have the choice between a few alternatives for storing public/private keys and certificates. We will use standalone government ID cards as an example. The approach described in this article should however be valid for other types of smart cards and USB tokens, except for the mobile signature option. It is worth mentioning that upon insertion of an e-signature media, only the qualified digital certificate, and not the private key, is accessible without the PIN code. This certificate contains the NAME, the SURNAME, and the PERSON CODE of the owner of the certificate. Also, in case of regular use of a smartcard/token, chances are it will remain in the card reader of the computer. Why bother disconnecting it, one may ask?
Example 1 – GoSign misconfiguration
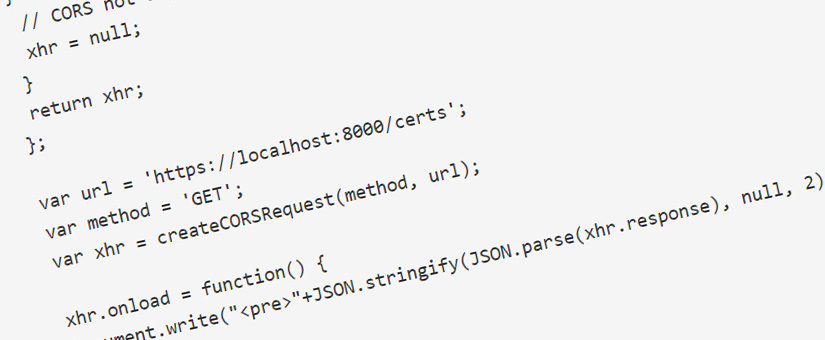
Before exploring the first example, let’s recall what Cross-Origin Resource Sharing (CORS) is. CORS is a mechanism that enables web browsers to perform cross-domain requests using the XMLHttpRequest API in a controlled manner. These cross-origin requests have an “Origin” header, which identifies the domain starting the request.