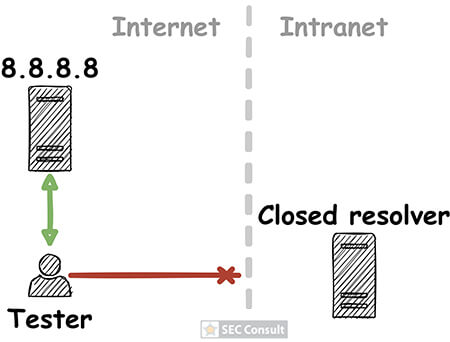
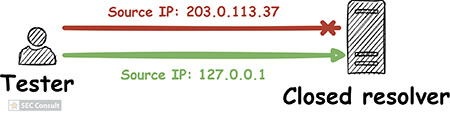
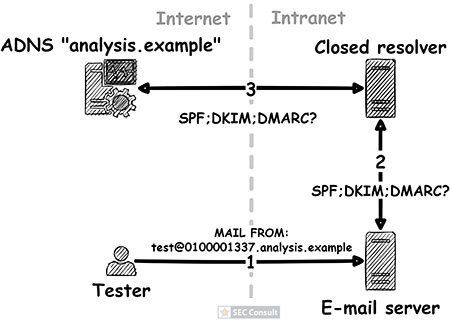
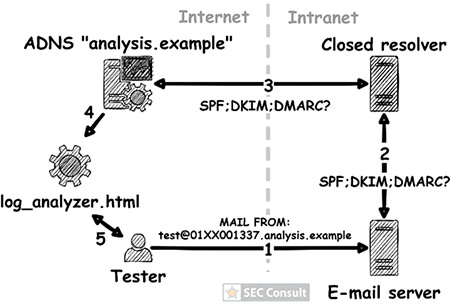
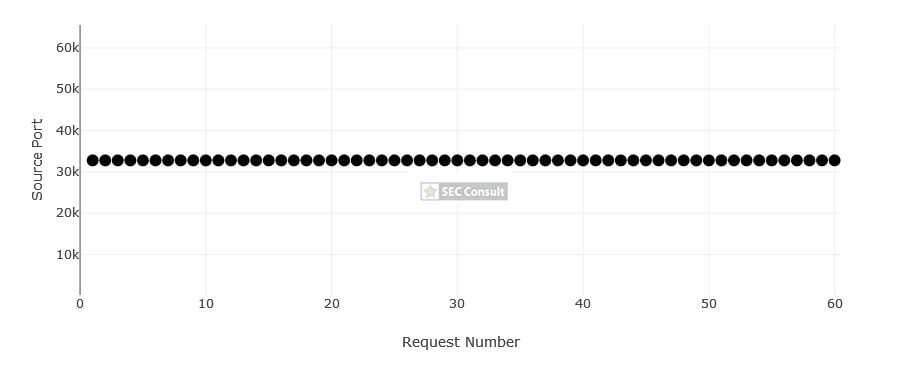
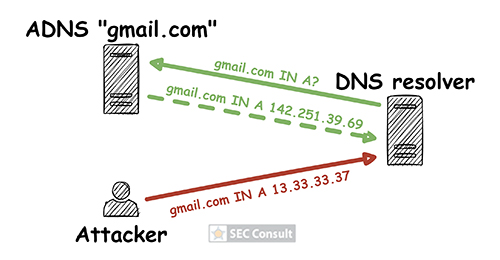
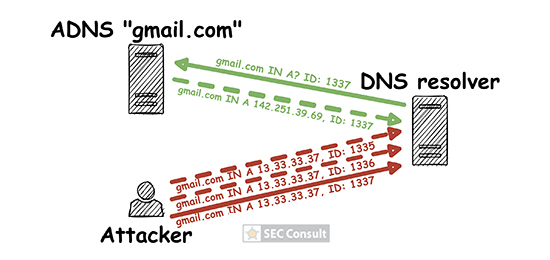
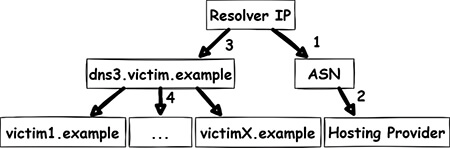
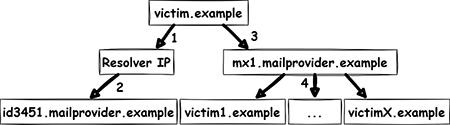
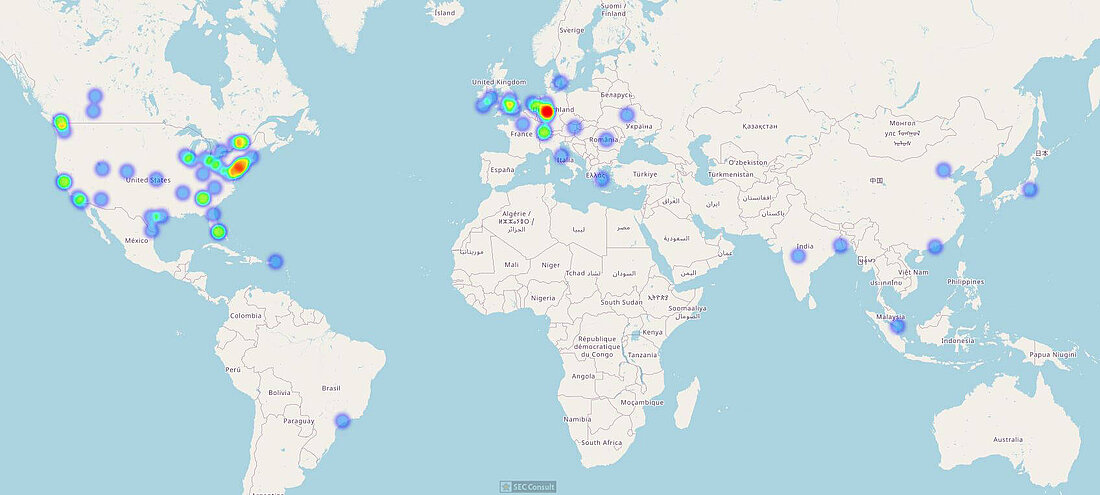
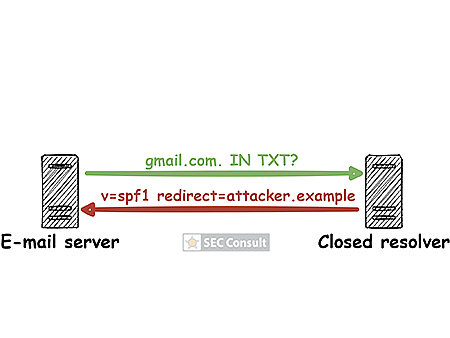
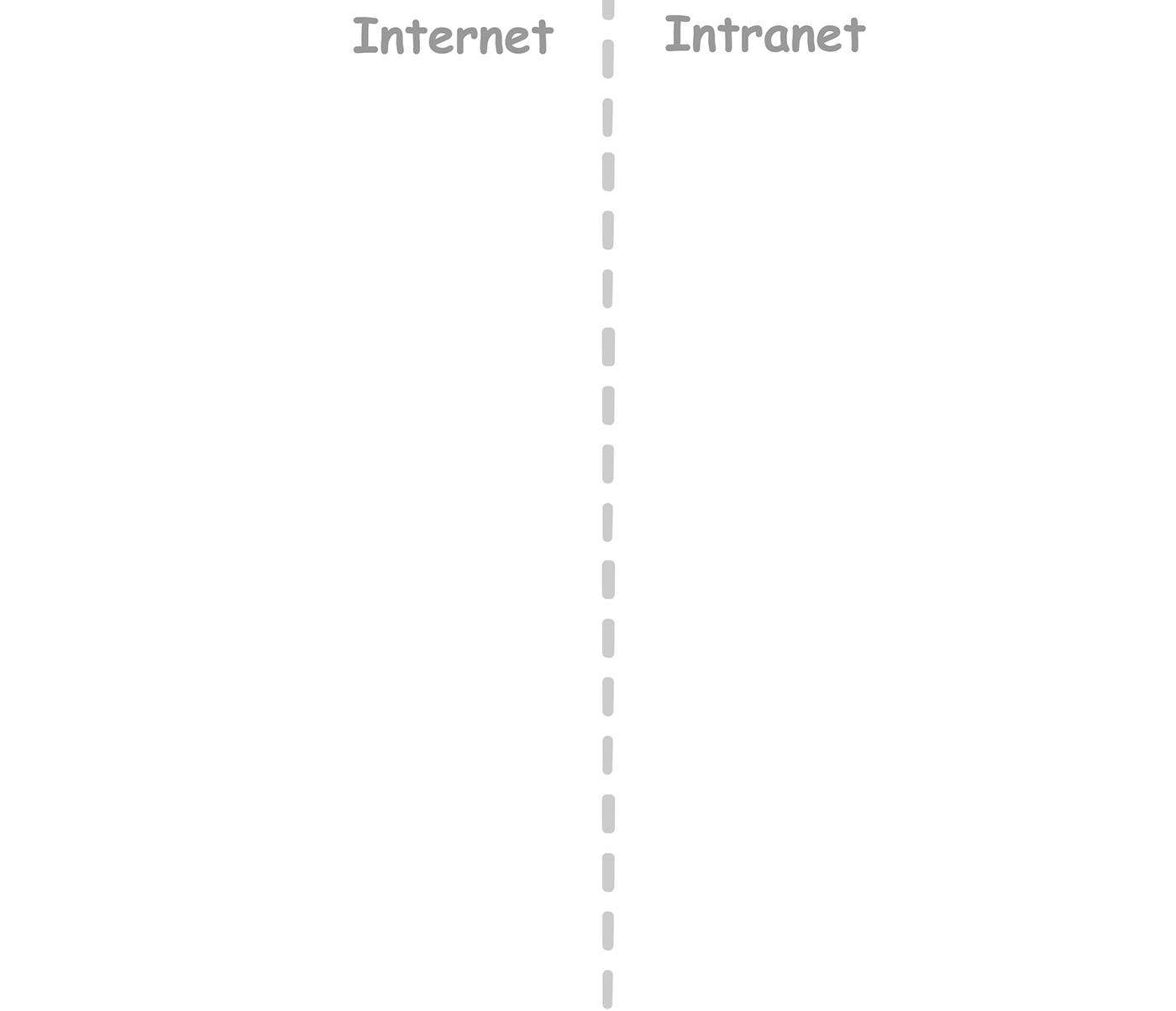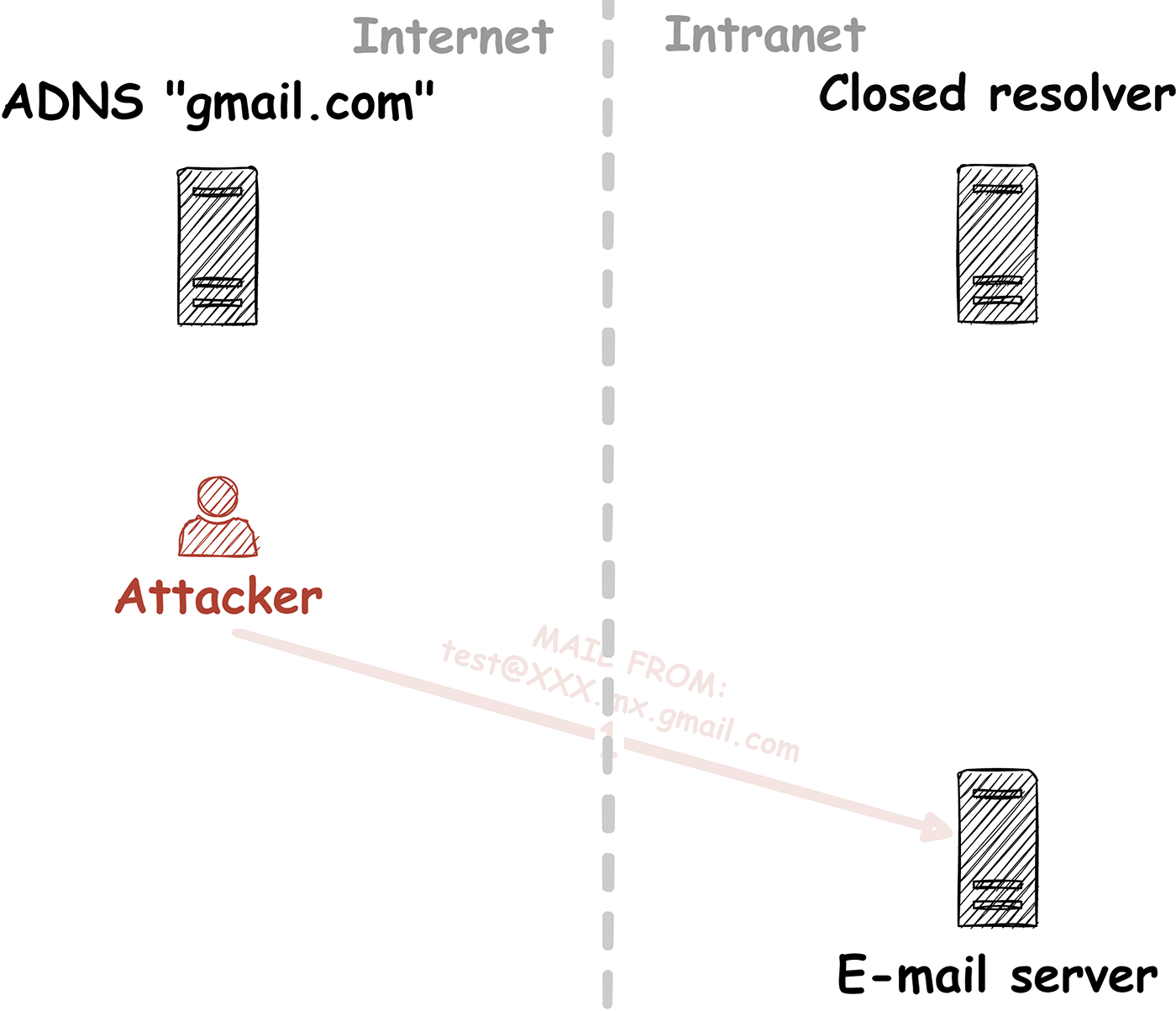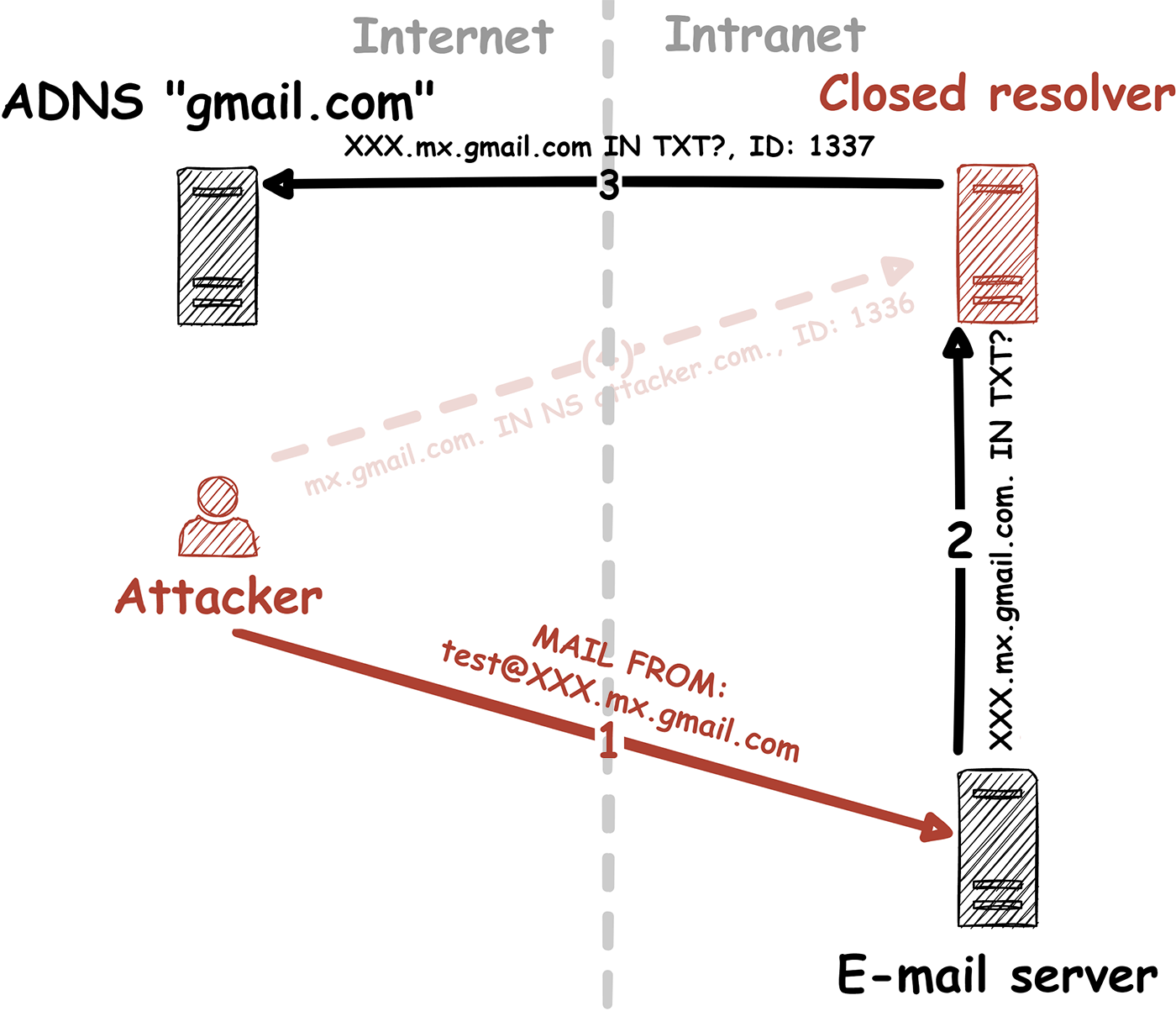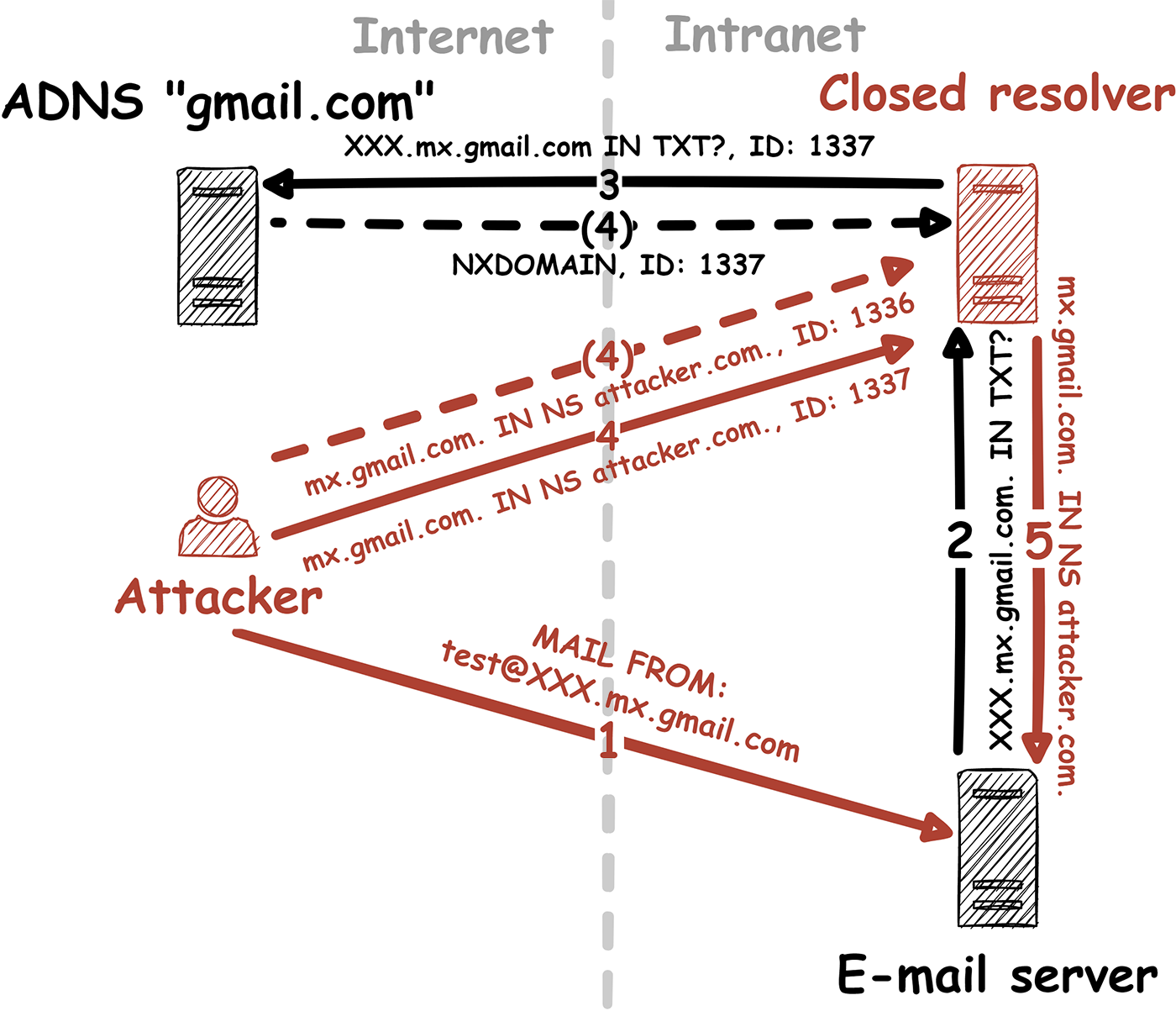
By analyzing closed DNS resolvers on the Internet, we found numerous ISPs and hosting providers that are vulnerable to trivial Kaminsky attacks. This allows an attacker to manipulate the DNS name resolution of thousands of systems. As a consequence, e-mail redirections, account takeovers and even the compromise of entire systems may be possible. Closed DNS resolvers all across the world are affected.
This blog post describes the core problem of our research and how to find vulnerabilities in closed DNS resolvers. Furthermore, open-source tools such as the DNS Analysis Server, are introduced and provided. Lastly, we're showing how to take over a fully patched WordPress instance in a proof-of-concept exploit!
- Does this affect me?
- How can I protect myself?
- Should I be on the lookout for DNS vulnerabilities?
The Q&A section at the bottom of this article covers these and many more questions.
The Core Problem
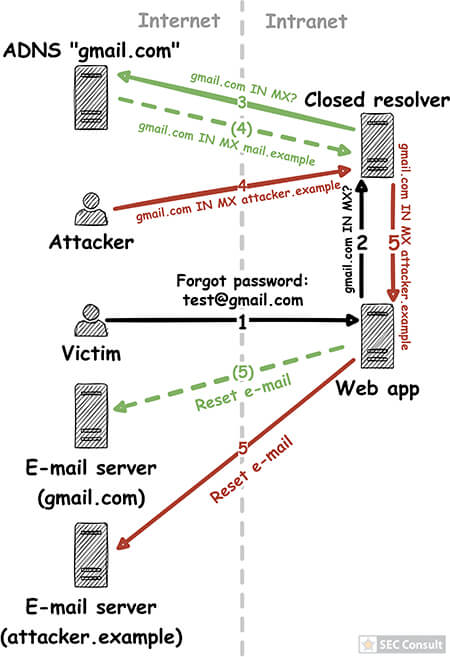
In our blog post “Forgot password? Taking over user accounts Kaminsky style” we showed how an attacker can take over user accounts of a web application by manipulating the DNS name resolution. Furthermore, we went into detail on how to find vulnerabilities in DNS setups of web applications and the fact that such vulnerabilities exist, even today. However, we didn’t tackle the core problem!