The SEC Consult Vulnerability Lab identified a sandbox breakout vulnerability in multiple Konica Minolta bizhub MFP printers end of 2019, that could be exploited via physical access to a printer's touchscreen terminal. An attacker is able to get full read and write access to the printer's operating system and stored data as root. This can be used to manipulate and compromise the printer and its users in many ways. Konica Minolta reacted in an exemplary manner and fixed the vulnerabilities immediately at the beginning of 2020. They also kept the updates coming continuously during our responsible disclosure. Due to the large number of affected devices (hundreds of thousands of devices according to the vendor) and the need to apply the firmware update manually by service technicians, the process took quite some time, especially during the COVID-19 pandemic with multiple lockdowns hindering the technicians to go on-site.
This blog post describes the vulnerabilities and patches, a practical example of the attack as well as a word about the responsible disclosure timeline. Furthermore, a technical security advisory has been published as well containing the affected models and fixed firmware versions.
A Different Approach to Printer Pentesting
The classic way
For years a large amount of printer vulnerabilities has been published regularly. Most of those vulnerabilities are found in one of the following parts of the printer:
The networking features and protocols exposed by the printers
Printer Services
Printer Software and Drivers
(Web) Applications running on the printers themselves
Very good research concerning classic printer vulnerabilities can be found at the following locations:
https://www.blackhat.com/presentations/bh-asia-02/bh-asia-02-fx.pdf
https://www.nds.ruhr-uni-bochum.de/media/ei/arbeiten/2017/01/30/exploiting-printers.pdf
https://gsec.hitb.org/sg2019/sessions/why-you-should-fear-your-mundane-office-equipment/ → Very nice talk - we have been there personally
http://i.blackhat.com/USA21/Wednesday-Handouts/us-21-Diving-Into-Spooler-Discovering-Lpe-And-Rce-Vulnerabilities-In-Windows-Printer.pdf → PrintNightmare vulnerabilities
A different route
We tried to go a different route and focused on "the printer" itself. In the end it is just another computer with a housing fit to fulfill its purpose - in this case putting ink on paper. On most modern office printers you can find one or multiple of the following elements:
A screen, or even a touchscreen
Multiple inputs like keyboards, trackballs, touchscreens
Multiple ports like USB, RJ-45, serial interfaces, etc.
RFID readers for authentication
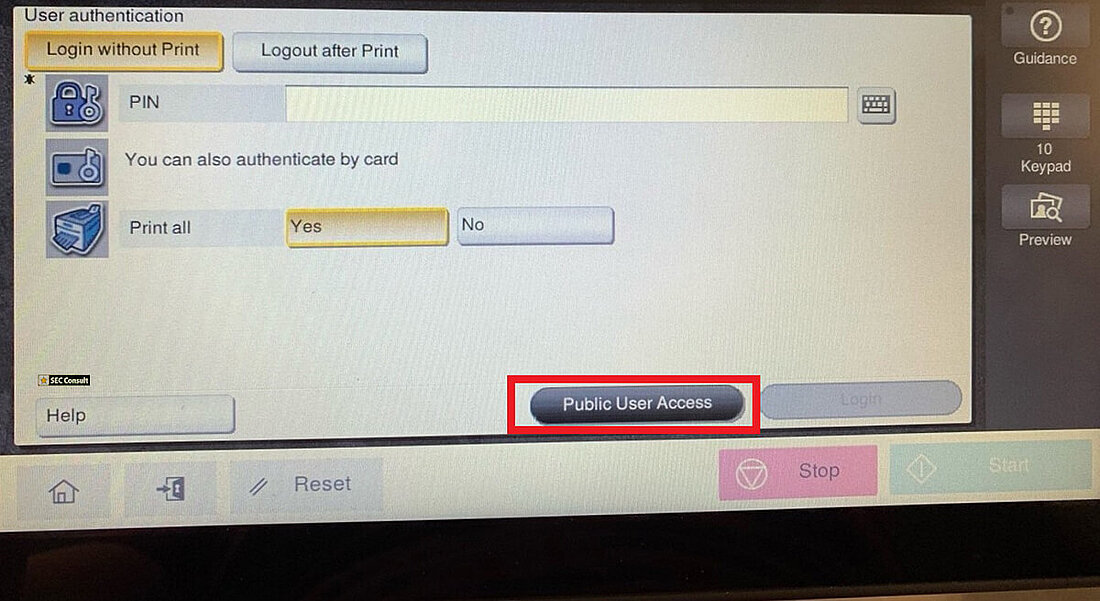
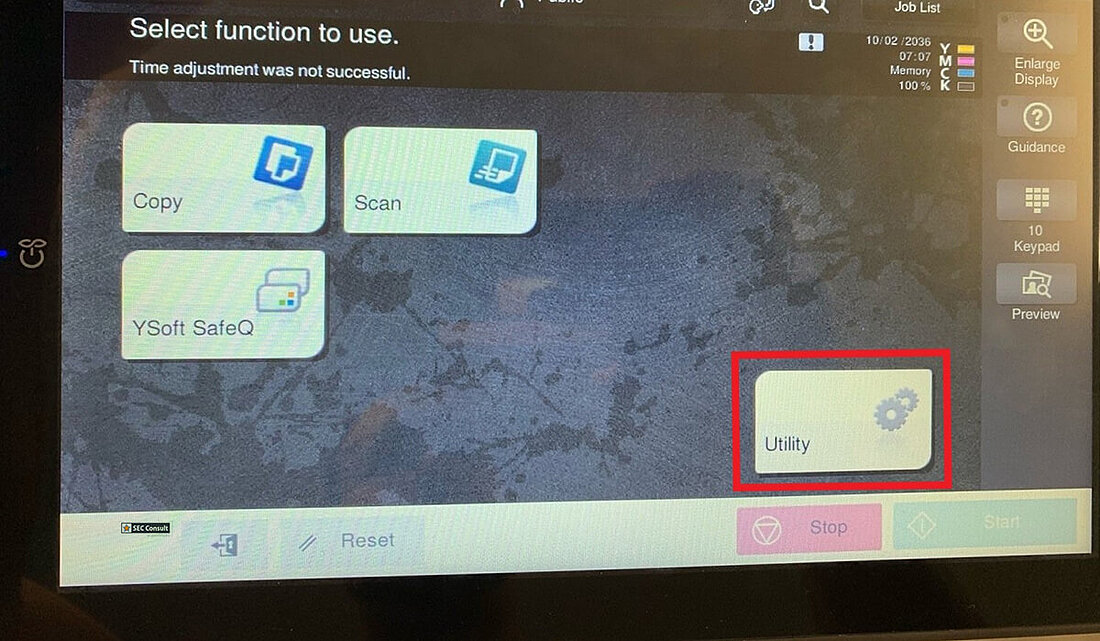
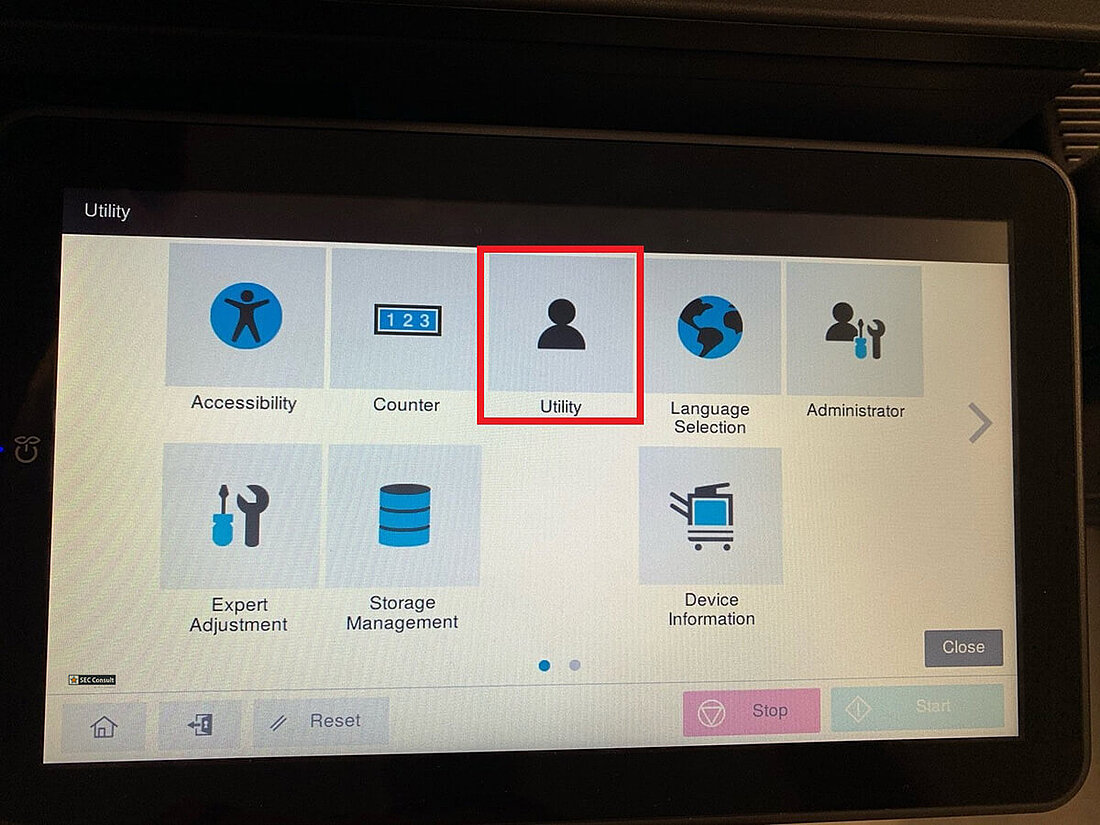
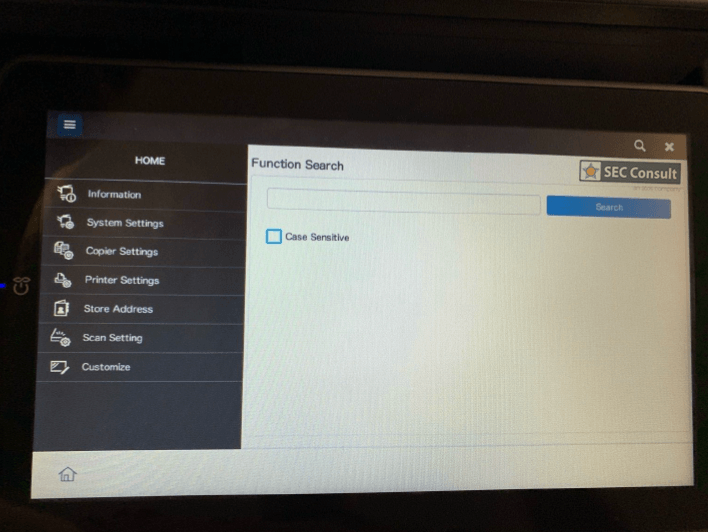
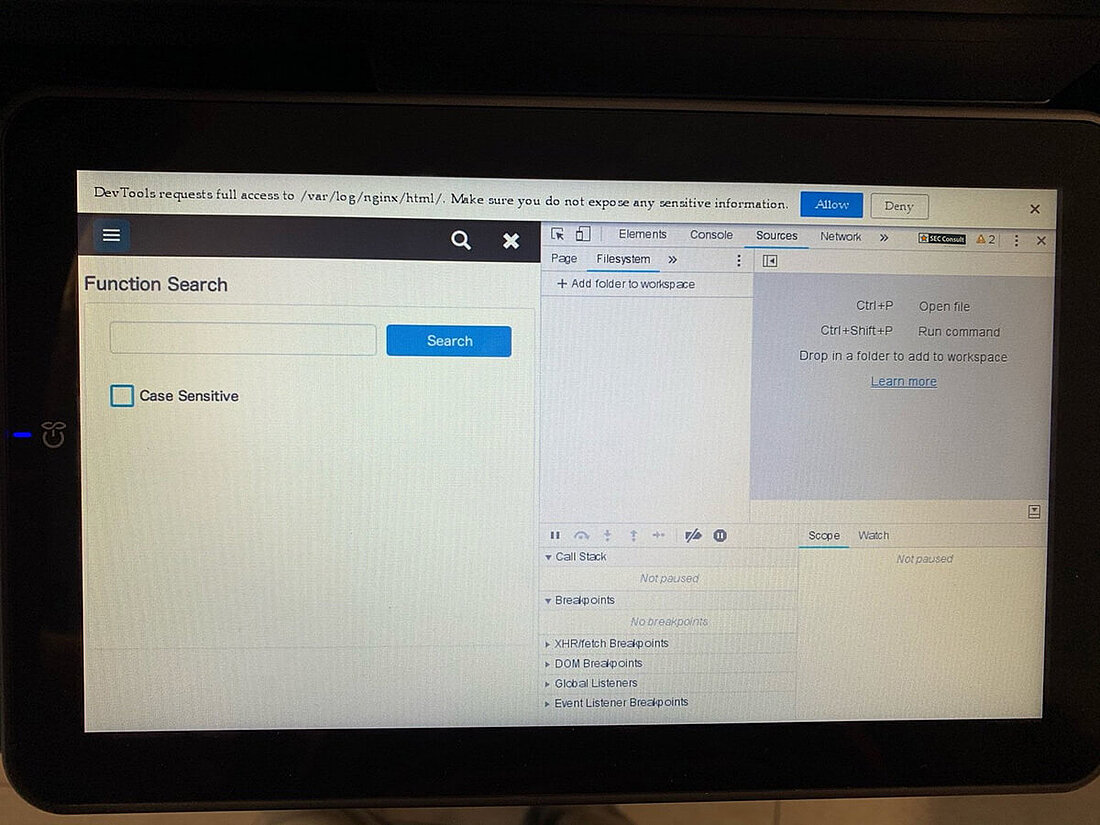
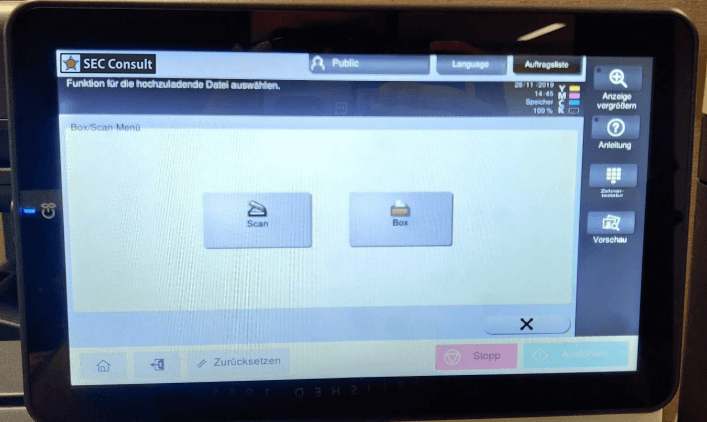
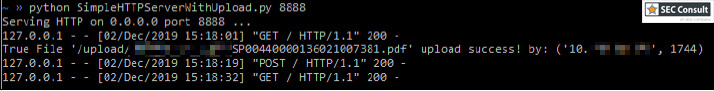
Most printers also have in common that they use their display to show some kind of application running in full screen on top of a Unixoid operating system that is, or should be locked down completely. This part is what we refer from now on as the printer sandbox. All scenarios that we tested were done as an unauthenticated user with physical access to the printer's touchscreen.
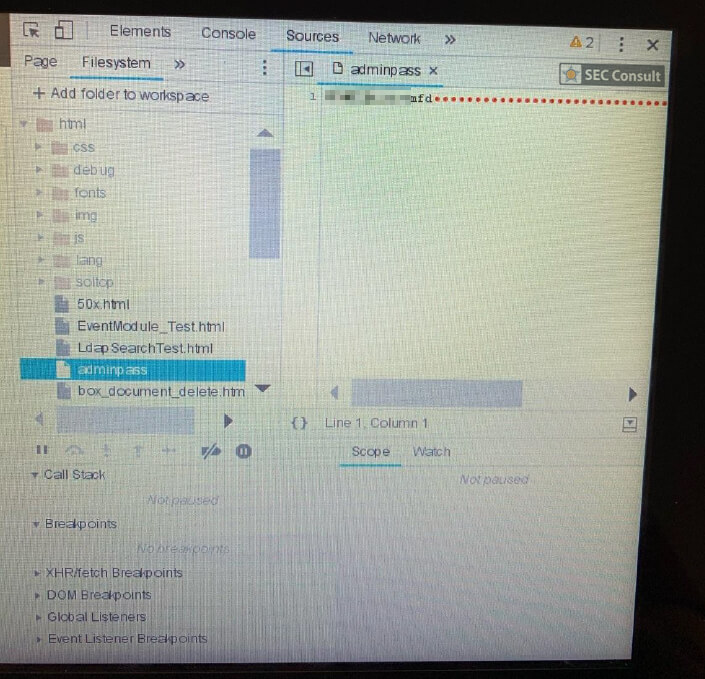
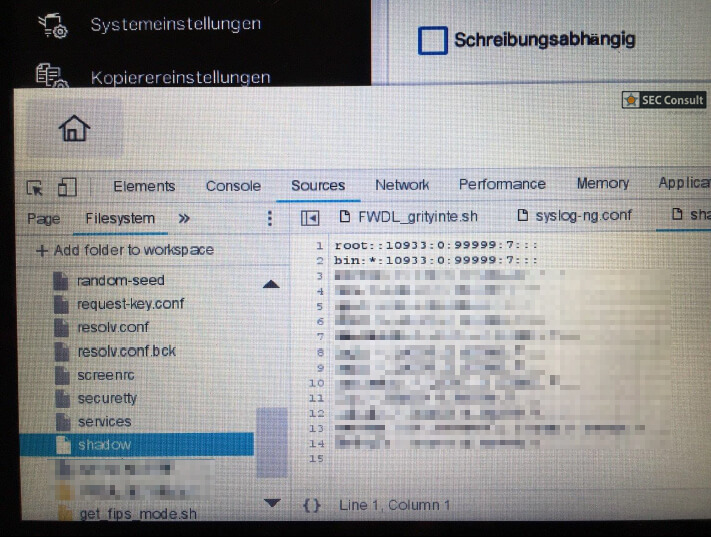
We observed that by opening certain applications and/or settings via the terminal, it was possible to observe a slight change in the look and feel of the user interface itself. It was quickly determined that this was the result of context change, meaning that the applications running are not solely based on the proprietary application only. After attaching a keyboard to one of the multiple USB ports of the printer and pressing specific key combinations, it was possible to determine that some application parts are running an ordinary Chromium browser in "kiosk mode", which can be escaped easily. This allows an attacker to get full access to the underlying printer's operating- and file system, including configuration files, passwords in clear text, proprietary scripts and many more. Access to all those files was easily possible as chrome was running as root.